Contents:
SYN flood is a type of denial-of-service (DoS) attack in which a threat actor floods a server with several requests, but doesn’t acknowledge back the connection, leaving it half-opened, usually with the purpose of consuming server resources, which leads to denying other users access to that server.
In this article, we’ll explore how a SYN flood attack works, why it’s so dangerous, how to spot its signs, and what measures you can take to prevent it from taking over your system. Let’s begin!
How Does SYN Flood Work?
SYN flood is one the most common attacks on Transmission Control Protocol/Internet Protocol (TCP/IP) and it works by exploiting a vulnerability in the way TCP/IP handles incoming connection requests. But before getting into further details, let’s first have a closer look at how a “normal” TCP/IP connection works.
Normal TCP Connection
Under normal circumstances, establishing a TCP connection involves three steps, also known as “the TCP three-way handshake”:
- In order to establish a connection, the client first sends a SYN (synchronize) packet to the server (the packet is the basic unit of data that is transmitted through a network).
- In order to acknowledge the communication, the server responds to the original packet with a SYN/ACK (synchronize/acknowledge) packet.
- Finally, the client returns an ACK packet to the server to acknowledge receipt of the packet. The TCP connection is open and ready to send and receive data when this packet sending and receiving sequence is completed.
SYN Flood Connection
In the case of a SYN flood attack, the dynamic of the connection changes, remaining “half-open”. Here’s how it happens:
- First, the attacker sends a large number of SYN (synchronize) packets to a target server, with a fake source IP address.
- The server responds, as in the case of a normal connection, to each SYN packet by sending a SYN-ACK (acknowledgment) packet back to the supposed source, waiting for a final ACK packet to complete the three-way handshake and establish a connection.
- However, since the source IP address is fake, the ACK packet is never received, leaving the server with a large number of half-open connections that consume resources and ultimately overload the system, causing a denial of service.
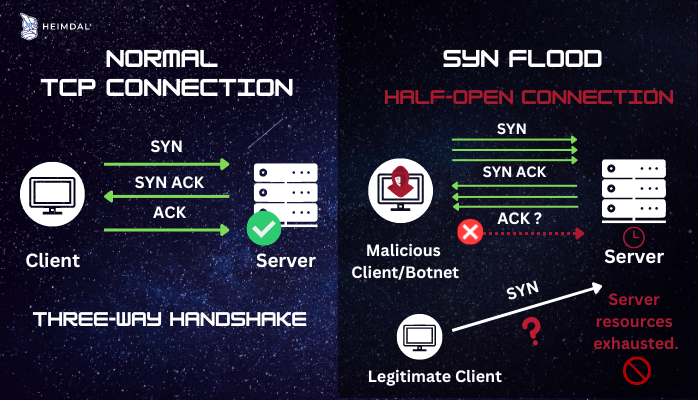
Normal TCP Connection Vs. SYN Flood.
SYN Flood Attack Types
Direct Attack – In this case, the attacker makes no attempt to hide their IP address. And since they are using a single source device that has a legitimate IP address, it is very likely that the source of the attack will be found and shut down (by simply blocking the IP address).
Spoofed Attack – The malicious client spoofs the IP address on each SYN packet it sends to the server. This makes it look like the packets are coming from a trusted server. Spoofing makes it hard to track down the packets and stop the attack.
Distributed attack – In a DDoS attack, the client employs a botnet that distributes the source of malicious packets across numerous machines. The sources are authentic, but the attack’s distributed nature is challenging to mitigate.
For an additional layer of obfuscation, the attacker may have each distributed device fake the IP addresses from which it delivers packets. However, when employing a large botnet like the Mirai botnet, for example, an attacker is less likely to worry about hiding the IP address of the compromised device.
Why Are SYN Flood Attacks Dangerous?
SYN flood attacks are dangerous because they can cause a denial of service, rendering a target server or network unavailable to legitimate users. The attack causes the target to allocate resources for half-open connections that will never be completed. This can lead to a rapid consumption of resources, such as memory, CPU, and network bandwidth, resulting in the target becoming unavailable.
Additionally, SYN flood attacks can be launched from a large number of sources, either by a single attacker using multiple computers or by a group of attackers using a network of infected computers (a botnet). This makes it difficult for the target to defend against the attack, as it is overwhelmed by a large volume of incoming traffic from multiple sources.
This type of attacks can cause significant disruption and financial damage to businesses, organizations, and individuals that rely on the target server or network.
SYN Flood Targets
SYN flood attacks can target any server that relies on the Transmission Control Protocol (TCP) for communication. This includes servers that provide various online services, such as web servers, email servers, database servers, and application servers.
In addition to these, SYN floods can also target infrastructure servers, such as firewalls, routers, and load balancers, as well as cloud-based servers and virtual private servers (VPS). Essentially, any server that handles incoming TCP connections is at risk of being targeted by a SYN flood attack.
The specific type of server targeted by a SYN flood attack will depend on the attacker’s motives and objectives. Some attackers may target web servers to cause a denial of service, rendering the target website unavailable.
Others may target email servers to disrupt communication or steal sensitive information. In some cases, attackers may target infrastructure servers to launch more sophisticated attacks, such as man-in-the-middle attacks or data theft.
SYN Flood Example
Mirai Botnet, used SYN flood, among other ‘flooding’ techniques, to compromise over 600,000 Internet of Things (IoT) devices and launch one of the most damaging DDoS attacks in history against high-profile targets, including KrebsOnSecurity, a well-known internet security blog, Lonestar cell – a popular telecom operator in Liberia and Dyn – a broadly used DNS provider.
Other very major service providers that used Dyn’s services, including Sony Playstation servers, Amazon, GitHub, Netflix, PayPal, Reddit, and Twitter, were also adversely affected as a result of the DDoS on Dyn.
If you want to learn more about Mirai Botnet, my colleague Vladimir analyzed its attack strategy, in detail, in a dedicated piece: A Technical Analysis of the Mirai Botnet Phenomenon.
Signs of a SYN Flood
- High network traffic: A sudden and sustained increase in network traffic can indicate a SYN flood attack, as the attacker is sending a large number of SYN packets to the target server.
- Unresponsive servers: A server that becomes unresponsive or slow to respond to requests is a potential indicator of a SYN flood attack, as the server is being overwhelmed by incoming SYN packets.
- Increased CPU usage: High CPU usage on a server can indicate that the server is being overwhelmed by incoming SYN packets, as the server is working to process the large number of incoming connections.
- Network connectivity problems: A server or network that becomes unavailable or experiences connectivity problems is a potential indicator of a SYN flood attack, as the server is being overwhelmed by incoming SYN packets and is unable to process incoming requests.
- Increased error rates: An increase in the number of errors or timeouts from a server can indicate a SYN flood attack, as the server is being overwhelmed by incoming SYN packets and is unable to process incoming requests.
How to Prevent a SYN Flood?
There are several ways that you can protect your network against a SYN flood attack:
- Firewall configuration: Configure firewalls to limit incoming traffic and block incoming connections from suspicious or known malicious IP addresses.
- Use SYN cookies: SYN cookies are a special type of cookie that is used to track SYN requests. When a server receives a SYN request, it will send back a SYN cookie to the client. The client must then return the cookie in order for the connection to be completed. This helps to ensure that only legitimate clients are able to connect to the server.
- Network segmentation: Segment the network into smaller, more secure sub-networks to limit the potential damage from a SYN flood attack.
- Load balancing: Use load balancing techniques to distribute incoming traffic across multiple servers, reducing the risk of a single server being overwhelmed by a SYN flood.
- Implement traffic filtering techniques, such as rate limiting. By limiting the number of incoming connections from a single IP address incoming traffic, you can help to prevent your server from being overwhelmed by too many requests at once.
- Network visibility: Monitor network traffic to detect SYN flood attacks in real-time, allowing administrators to quickly respond and take appropriate action.
- Network security devices: Use network security devices, such as intrusion detection systems (IDS) and intrusion prevention systems (IPS), to detect and prevent SYN flood attacks.
- Software and system updates: Keep software and systems up-to-date to ensure that vulnerabilities are patched and that the latest security measures are in place.

Heimdal® Patch & Asset Management Software
- Schedule updates at your convenience;
- See any software assets in inventory;
- Global deployment and LAN P2P;
- And much more than we can fit in here...
How Can Heimdal® Help?
Because prevention is always better than cure, you should consider an intrusion prevention system that can help you detect threats before getting a chance to damage your systems. Our Heimdal DNS Security – Network offers unique threat hunting and visibility across the entire network. Protection from A to Z, independent of the device or operating system. Hybrid DNS enables you to secure traffic locally on any DNS server, without rerouting to our resolvers, making it perfect for both on-premises and cloud-based systems.
Regain your peace of mind with an all-encompassing solution for your entire business ecosystem. Protect and maintain BYODs, IoTs, and all other devices connected to your organization’s network.
Heimdal® DNS Security Solution
Wrapping Up
SYN flood attacks can be a serious threat to the security of your network. With the right protection, however, you can keep these malicious attempts from compromising your data and causing major damage.
Implementing an intrusion detection system along with proper firewalling policies should help you protect your organization against SYN flooding attacks.
Additionally, it is important that you stay up-to-date on any new threats as they arise so that you can take steps to ensure your network remains safe and secure.
If you are concerned about the risk of SYN Flood or DDoS attacks in general, contact sales.inquiries@heimdalsecurity.com to talk about more in-depth ways to protect your organization.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








