Contents:
Managing privileged access to internal resources is a challenge for organizations worldwide. If left unaddressed, it could lead to data breaches, downtime, and financial loss.
Statistics show that 80% of data breaches seem to be caused by misuse of privileged account access (Forrester study).
For this article, I chose the term “privilege overreach” to describe the phenomenon of giving users too much access to a system, without considering the security implications.
So, what exactly is privilege overreach? Why is it risky, and what can it lead to in terms of consequences? Most importantly, how can privileged access management tools help organizations mitigate this “lurking” security threat?
What is Privilege Overreach?
The term privilege overreach refers to the excessive privileges granted to users, often without realizing the potential security risks associated with this practice.
This could happen due to a variety of reasons, the most common ones being lack of access control policies and tools, the job role complexity that makes access rights hard to define, legacy systems with inherited privileges, fear of disruption, etc. Let’s analyze them a bit more in-depth:
- Lack of access control policies
Without a well-defined access control policy, organizations may grant permissions in an ad hoc manner. This absence of clarity can result in users being given more access rights than they actually need.
Your access control policies should include controls that are used to restrict reading, writing, processing and transmitting of information, as well as the modification of information systems, applications, services, and communications configurations that provide access to your organization’s information.
Lorna Willard, Information Security Auditor
- Lack of a centralized access control mechanism
Without proper tools and processes to monitor and audit privilege usage, organizations might find it challenging to spot and address excessive privilege issues.
- Sticking to default settings or legacy systems
Many software applications and systems come with default user settings that grant broad access. If these defaults aren’t customized upon installation, users might unintentionally be given excessive privileges.
Older systems might not have the fine-grained access controls that modern systems do. As such, they can often grant broad privileges as a one-size-fits-all solution.
- Fear of workflow disruption
You might over-privilege users simply out of fear that restricting access could disrupt workflows or impede job functions.
- Gradually accumulating unnecessary privileges
Over time, as employees change roles or take on additional responsibilities, they might accumulate access rights without shedding the ones from their previous roles. This gradual increase in privileges, if unchecked, leads to excessive access, a process also known as privilege creep.
Deprovisioning is really important from a security standpoint because if we leave your access rights around when you’re no longer permitted to use them, we can end up with an exposure.
Jeff Crume, Cybersecurity Expert
- Complexity of some job roles
In larger organizations, complex job roles and responsibilities may make it challenging to define precisely what access each user needs. Read more about the separation of privilege in this article: Separation of Privilege (SoP) 101: Definition and Best Practices.
- Administrative convenience
Sometimes, for the sake of administrative convenience, system administrators might grant blanket privileges to groups of users, even if not all individuals within those groups require such broad access.
In fact, statistics show that 40% of organizations use the same security for privileged accounts as they do for standard accounts.
Why is privilege overreach so risky?
The first issue is that a user with a privileged account might abuse their position or make unintentional errors that can compromise an organization’s security. This is known as an insider threat.
You’ve seen Mr. Robot, right? If you give someone the same level of access to your network that Elliot from “Mr. Robot” has at Evil Corp, you’re just one bad decision away from serious trouble. Well-meaning access can easily turn into a major risk.
With additional privileges, a disgruntled employee has more avenues to exploit the organization:
- They can access, modify, or leak confidential information, sabotage systems, or perform other harmful actions.
- They might accidentally modify critical data, misconfigure systems, or unintentionally expose sensitive information.
According to Ponemon‘s 2022 Insider Threats Report, employee inadvertent or accidental behavior is the primary cause of 57% of data breaches involving an insider.
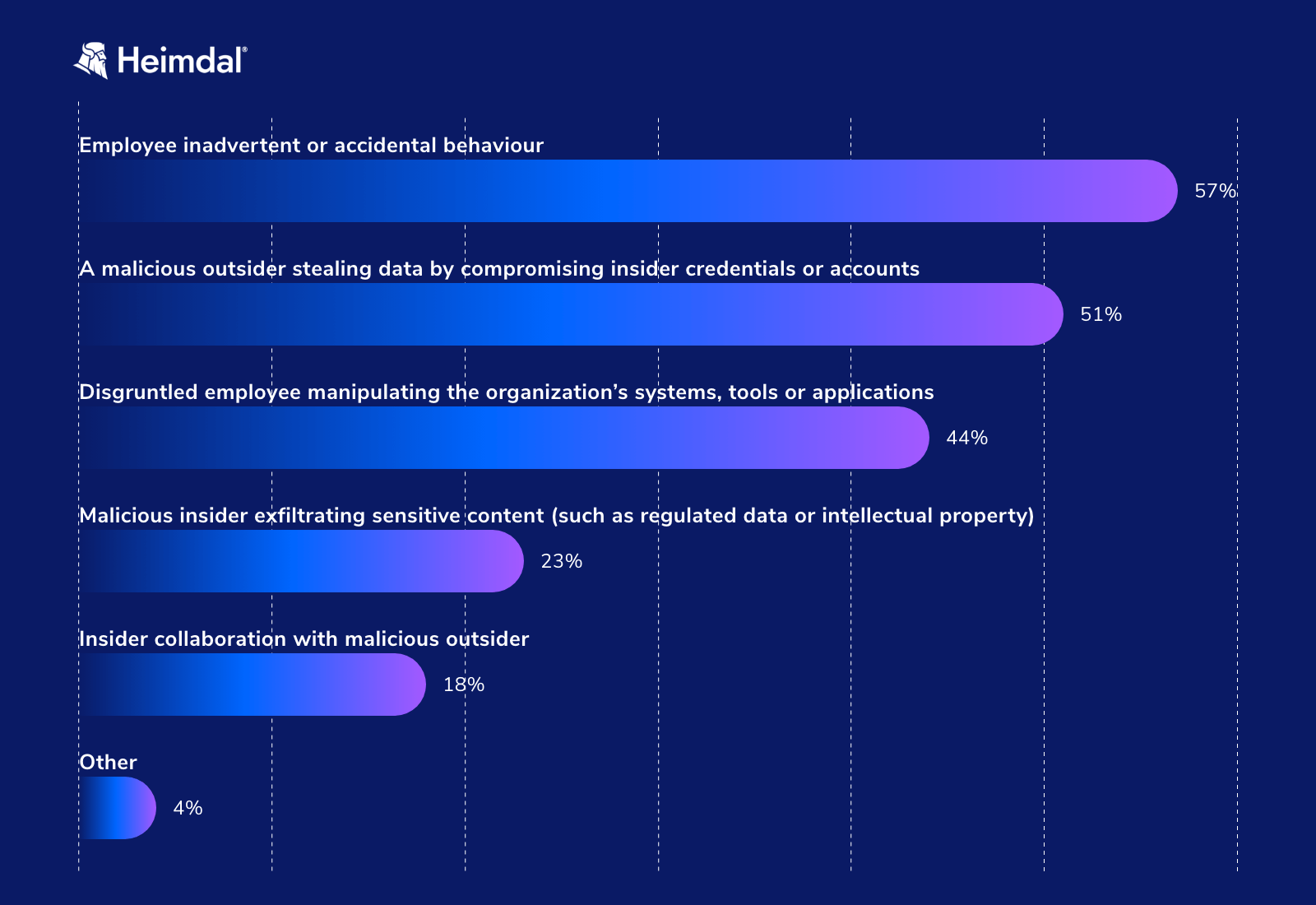
The cost of Insider Threats, Ponemon Institute
Secondly, if an attacker gains access to an end user’s account and that user has elevated permissions, the attacker will gain those same elevated permissions, providing the perfect opening for cybercriminals to move laterally across the network and begin their malicious activities.
This is known as a privilege escalation attack. Check out this article if you want to learn more about How to Prevent Privilege Escalation Attacks.
What are the consequences of privilege overreach?
Privilege overreach could open the door to data breaches, could lead to systems disruptions and operational downtime, and could result in compliance violations and hefty fines.
Let’s break down and analyze each one individually.
1. Data breaches
As we’ve discussed at the beginning of this article, 80% of data breaches seem to be caused by misuse of privileged account access.
When users have access to data or systems beyond what’s necessary for their roles, it creates opportunities for unauthorized access or misuse. This can lead to the exposure or theft of sensitive information, including customer data, intellectual property, and trade secrets.
The consequences of a data breach extend beyond immediate financial losses, as they can tarnish an organization’s reputation, erode trust, and result in legal liabilities, making it a top concern for CISOs and IT security teams.
Scenario 1 – The Insider Exploits Privilege Overreach
Pannacle Trust is a family bank. Sarah, the System Administrator, is drowning in complex user admin rights. She’s lost track and handed the new guy, Alex, access he doesn’t need, which will hurt her and the bank.
Alex gets into an argument with his boss on day one. Frustrated and armed with more access than he knows what to do with, Alex starts poking around in sensitive customer financial data.
He copies some of the data and shares it with external parties. It all looks like standard admin work until a routine security check uncovers the mess.
Now the bank is in hot water: informing numerous affected customers, undergoing regulatory investigations, and bracing for the sting of fines.
Scenario 2 – The Unwary Click and Privilege Trap
MediBrant is a private healthcare organization. Charlie, their meticulous System Administrator is swamped with managing a tangle of complex access permissions.
Despite his efforts to keep everything straight, some users, including Olivia, who manages patient records, end up with extra access they didn’t need.
One busy morning, Olivia gets this email, looks official — something about an ‘urgent’ file she needs to check. She clicks, downloads the file, and just like that, malware slips in and steals her credentials.
The attackers didn’t just break in; they waltzed in through Olivia’s over-privileged account, straight to confidential patient records. The intrusion stayed under wraps until an audit spotted the anomaly.
The institution is now facing the consequences of notifying affected patients, managing regulatory investigations, and addressing fines, all due to unintentional privilege escalation.
The moral of these two stories? Privilege overreach isn’t just a technical oversight, it’s a ticking time bomb for any institution. In the case of Pannacle Trust, it led to intentional internal misuse, while at MediBrant, it was the weak link that allowed external attackers to slip through.
2. Operational downtime
Excessive privileges can disrupt systems, causing downtime. Users with elevated access can make mistakes that affect system settings or data.
System administrators must manage and restore these systems, which is time-consuming and costly. System stability is vital, and privilege overreach can jeopardize it.
When it comes to high-privilege accounts, even the most well-organized ship can be flipped upside down in a matter of minutes, and sometimes even seconds. Malicious actors only need access to a single login to infect 10,000 machines with malware.
Andrei Hinodache, Cybersecurity Solutions Expert
3. Compliance and hefty fines
This one doesn’t need an explanation. The average cost of a data breach around the world in 2023 was USD 4.45 million, which is 15% more than the previous three years (IBM).
Many security regulations involve access control compliance, such as PCI, SOC2, GDPR, UL, HIPAA, NERC CIP, ISO 27001, and SSAE16.
What’s more, government institutions take more and more measures to reduce the allowable time for disclosing data breaches. Therefore, taking all possible precautions to prevent data breaches has transitioned from being a choice to a must.
How to prevent privilege overreach?
To prevent privilege overreach, it’s essential to blend strong access rules, timely access checks, proper user guidance, and the right tech tools. Ensuring security becomes more manageable with these in place.
We’ll be unpacking this topic further in future content, so stay tuned!
In the meantime, if you want to learn more about privileged access management, check out this video:
Combat privilege overreach with Heimdal®
Gartner predicts that, by 2024, a staggering 65% of enterprises leveraging privileged task automation could see savings of up to 40% in IT operations staff costs. This strategy will result in 70% fewer breaches, showing the significance of an automated PAM solution.
We’re firm believers in the power of automation and its capacity to solve the problem of privilege overreach, which is why we designed a powerful solution to help security teams address this issue.
Heimdal®’s Privilege Elevation and Delegation Management solution offers an unmatched level of control and flexibility to IT professionals, system administrators, and security teams in their quest to effectively manage user privileges.
With this solution, you can effortlessly elevate and delegate privileges based on user roles, ensuring that authorized individuals have precisely the access they need, all while reducing the risk of privilege misuse.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
If you liked this article, make sure you also read:
- What Is Privileged Access Management (PAM)?
- Privileged Access Management (PAM) Best Practices
- What Is the Principle of Least Privilege (POLP)?
- How to Prevent Privilege Escalation Attacks?
And our eBook: A Privileged Access Management Guide for Mid-Market and Lower Enterprise Organizations.
FAQs
What is excessive access?
Excessive access privileges occur when a user’s permissions exceed what their job requires. This over-privileging can pose security risks. Should an account have such excess, it’s important to promptly revoke these unneeded privileges to ensure security and compliance.
What is an over privileged user?
An over-privileged user is someone with more access rights than needed for their duties. Often, these users have network admin-level privileges when they only need local file or device access. This excess can pose security risks.
Why does excessive privilege cause security risk?
Excessive privileges pose a security risk firstly because employees with more access than needed might misuse it. Secondly, if a hacker breaches a user’s account with excess privileges, they too gain those excessive rights, amplifying the potential damage.
What are the 4 types of access control?
The four main access control types are Mandatory Access Control (MAC), Discretionary Access Control (DAC), Role-Based Access Control (RBAC), and Rule-Based Access Control (also known as RB-RBAC or RBAC). A fifth one is considered to be Attribute-Based Access Control (ABAC), sometimes referred to as Policy-Based Access Control (PBAC).
What are high privileged accounts?
High privileged accounts are those that offer elevated access and rights beyond standard user accounts. These can belong to employees, or be linked to external entities like contractors, vendors, auditors, or even to machines and applications requiring special access.
Which user is considered as the highest privileged user?
The root user in Unix/Linux systems, the administrator account in Windows environments, and the root user in macOS are considered the highest privileged users. These accounts have extensive access rights, allowing for tasks like software installation or configuration changes, and are often referred to as superuser accounts.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










