Contents:
Nowadays, cyber threats are more sophisticated and common than ever.
Companies face significant risks from breaches, ransomware, and other malicious activities, leading to financial loss, reputational damage, and operational disruptions. Strong incident response capabilities are now essential. Investing in top-tier incident response software is crucial. These tools offer comprehensive solutions for efficiently detecting, managing, and mitigating cyber incidents.
This guide presents the 12 best incident response software to help you protect your assets and ensure business continuity.
The 12 Best Incident Response Software On the Market
- Heimdal® XDR (+ MXDR)
- IBM Security QRadar
- Datadog Cloud SIEM
- Crowdstrike Falcon
- Cynet 360 AutoXDR
- KnowBe4 PhishER
- Mandiant Incident Response Services
- Rapid7 InsightIDR
- Cisco SecureX
- Splunk Enterprise Security
- AT&T AlienVault USM
- Kaspersky EDR Expert
1. Heimdal® XDR (+ MXDR)
The ultimate solution for your enterprise’s security needs is Heimdal® XDR. We know that precise monitoring and prompt response are crucial to keeping your endpoints, networks, emails, identities, and data safe from cyber threats. Our service combines essential tools and security expertise to provide comprehensive protection.
Whether you use Microsoft 365 or Google Workspace, Heimdal® XDR and MXDR services have you covered.
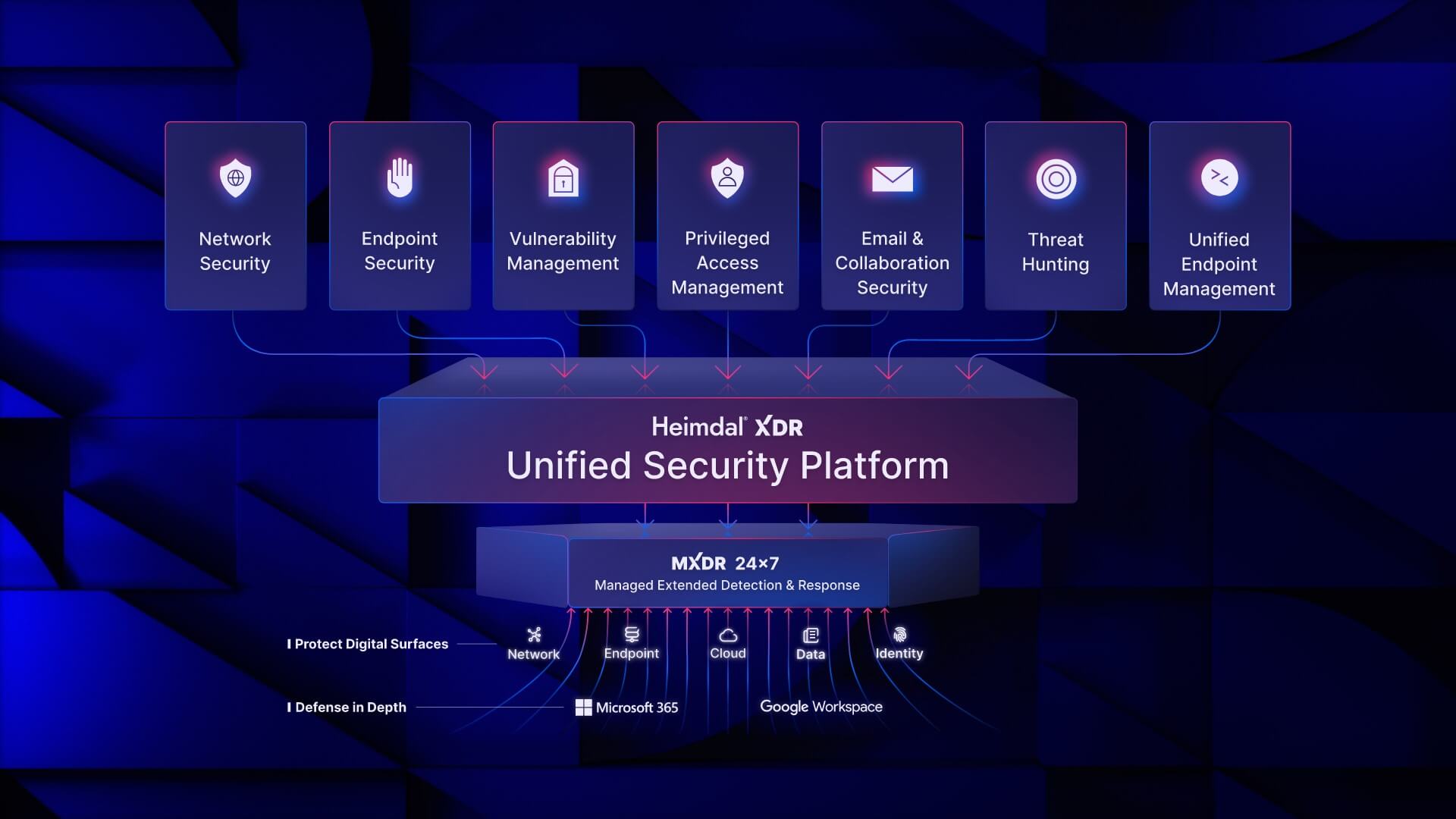
The MXDR department aims to protect clients and offer responsive support for security incidents, reducing costs through efficient security monitoring and management. Key services include continuous security monitoring, incident detection and response, proactive threat hunting, vulnerability management, and 24×7 client support.
To achieve these goals, the MXDR team uses advanced tools like a custom monitoring dashboard, Heimdal® Next-Gen AntiVirus, Heimdal® Ransomware Encryption Protection, and various log analysis tools. They work closely with other departments to ensure coordinated security and threat management.

The MXDR department addresses threats such as ransomware attacks and system vulnerabilities. Success is measured through KPIs like timely incident response and reduced client vulnerabilities. SOPs ensure consistent service delivery, and continuous improvement is achieved by monitoring trends and updating response processes.
MXDR team members have strong qualifications in cybersecurity, undergo regular training, and stay current with the latest threats and best practices. They follow a thorough incident response process, from detection to post-incident analysis, contributing to risk management and compliance.
The MXDR team prioritizes projects based on impact and urgency, employs proactive threat hunting, and ensures data privacy through strict policies. Customer satisfaction is regularly assessed to maintain high-quality service.
Committed to effective cybersecurity, the MXDR team continuously improves methods and stays updated with the latest threats, ensuring clients’ digital environments remain secure and compliant.
Here’s what professionals say about Heimdal® on Reddit:
I’ve gradually been moving all of my endpoints over to Heimdal®. Mainly just using the NGAV, Ransomware Encryption Protection, Patch Management and MXDR. I’ve had a very positive experience of both the software and the company.
Heimdal® are very responsive to suggestions and there’s lots planned in the roadmap.
I had a major concern with an endpoint and Andrei from Heimdal® reached out on a Saturday evening at 7pm GMT (or 9pm in Romania, where he is based) to help me out.
I bought via Brigantia in the UK and they have been very helpful with explaining how to set up the portal and I had a free session with Clelia from Heimdal® to further harden my settings. If you find the portal confusing, there’s lots of support available to help.
The CEO of Heimdal® is very open and approachable in webinars and will honestly answer any question put to him.
2. IBM Security QRadar
IBM Security QRadar SIEM is a scalable, appliance-based solution that collects and analyzes log and flow data from devices, endpoints, and applications, generating prioritized alerts to speed up incident analysis and remediation.
This solution supports IBM X-Force Threat Intelligence and third-party threat intelligence feeds via STIX and TAXI, enhancing threat detection. Additionally, integrated modules for risk and vulnerability management, forensics analysis, and incident response are available as options.
QRadar SIEM is available for both on-premises and cloud environments. Organizations considering enterprise SIEM products should gather additional information about IBM QRadar SIEM to determine if it meets their requirements.
I’m gonna be the outlier here and say qradar works fine for what it is. You have to pay a lot more for their fancy AI so I don’t use it, but for syslogs and parsing and rules and stuff honestly it gets the job done and isn’t that bad, I’m getting decent value out of it and not even fully utilizing the actual SIEM part (just need to dedicate more time). I’ve got a decent sized deployment and I guess since I’ve been using it for a long time I’m used to the search speeds, but I’ve got my indexes decent and my searches are specialized enough to only hit what they need.
I am also on prem though multiple sites and multiple processors.
Unlike what others have said I think their support is perfectly fine. I always get the South American support and can actually understand what they are saying and 9 times out of 10 once I’ve got a screen share with ssh my problem is solved on the first call.
Reddit Review of IBM Security QRadar
3. Datadog Cloud SIEM
Datadog Cloud SIEM stands out as a cutting-edge log management solution designed to facilitate seamless onboarding across teams. It offers an intuitive user experience aimed at enhancing threat detection and investigation within dynamic, cloud-scale environments.
Unlike traditional SIEM tools, Cloud SIEM is tailored to meet the unique challenges of public cloud environments, ensuring effective threat detection and investigation capabilities. With Cloud SIEM, users can analyze operational and security logs in real time, regardless of their volume, leveraging pre-built integrations and rules to detect and investigate threats efficiently.
By providing developers, security, and operations teams with a shared view of threats and observability data, Cloud SIEM enables faster collaboration and accelerates security investigations within a unified platform.
Datadog has the best in category dashboarding, and some really good AI/ML/buzzword algorithms coorelating data.
But, they have never released much toolset to help you understand why the bill is expensive, metrics that are not being queried, and what drives up custom metrics cardinality.
They also don’t ‘get’ ephemeral container design, which shows in custom metrics and host billing. You gotta urge and push for hour based billing on all their services or just a couple hours of extra capacity significantly increases your monthly bill.
Datadog really is great, but you cannot expect them to manage your data — they’ll just be happy to keep taking your money until you quit and move to another platform.
Reddit Review of Datadog Cloud SEIM
4. Crowdstrike Falcon
CrowdStrike specializes in cybersecurity, focusing on incident response and forensics to address various cyber threats.
The company offers a comprehensive range of solutions aimed at safeguarding clients’ networks from cyberattacks while enhancing productivity and efficiency.
These solutions include real-time threat detection to preemptively address potential issues, aiding organizations in mitigating attacks by blocking intrusions at their origins, and offering post-breach remediation services such as malware removal and forensic analysis.
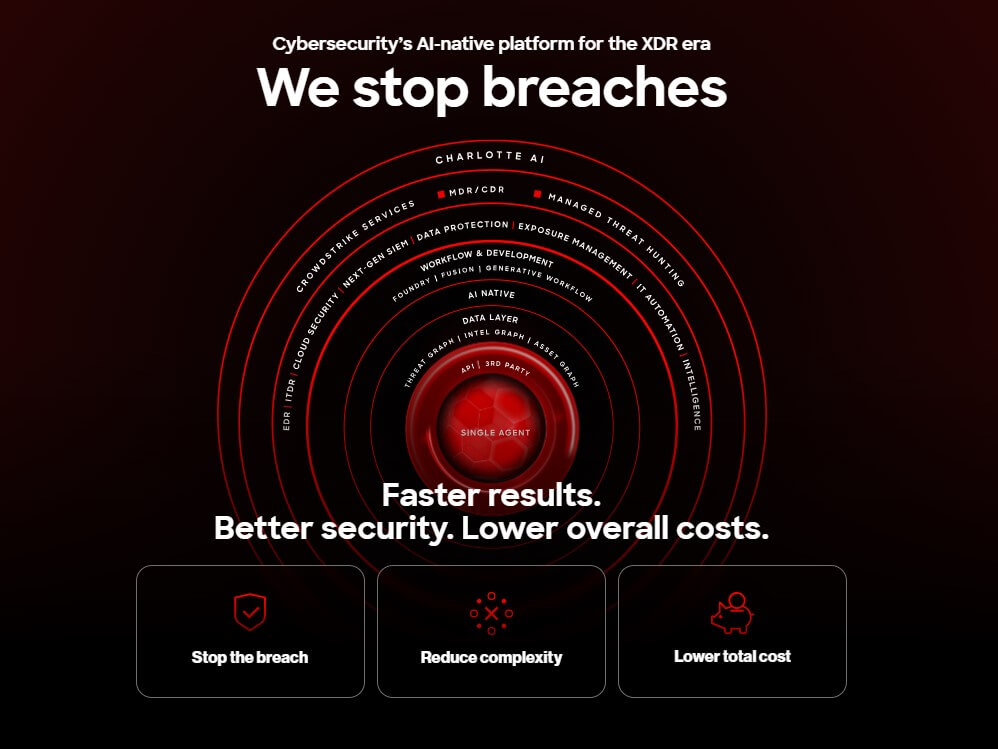
CrowdStrike also assists companies in recovering from data breaches by restoring lost data or encrypting sensitive information.
Moreover, they provide employee training to enhance defense against cyberattacks and offer consulting services on cybersecurity matters, including threat intelligence sharing among government agencies collaborating against existential threats posed by hackers.
Crowdstrike is by far my favorite tool in our toolset and has definitely saved our asses before. Easy to manage and highly effective. We don’t have their monitoring service. The Windows defender standard is basically impossible to manage at an Enterprise level. The product itself is effective but there is no great way to manually intervene or investigate.
Reddit Review of CrowdStrike
5. Cynet 360 AutoXDR
Cynet 360 AutoXDR Endpoint Protection Software stands as a holistic cybersecurity solution meticulously crafted to shield endpoints against sophisticated threats.
By harnessing advanced AI and machine learning algorithms, it swiftly identifies and responds to cyber threats in real-time, furnishing organizations with a proactive defense against malware, ransomware, and other malicious activities.
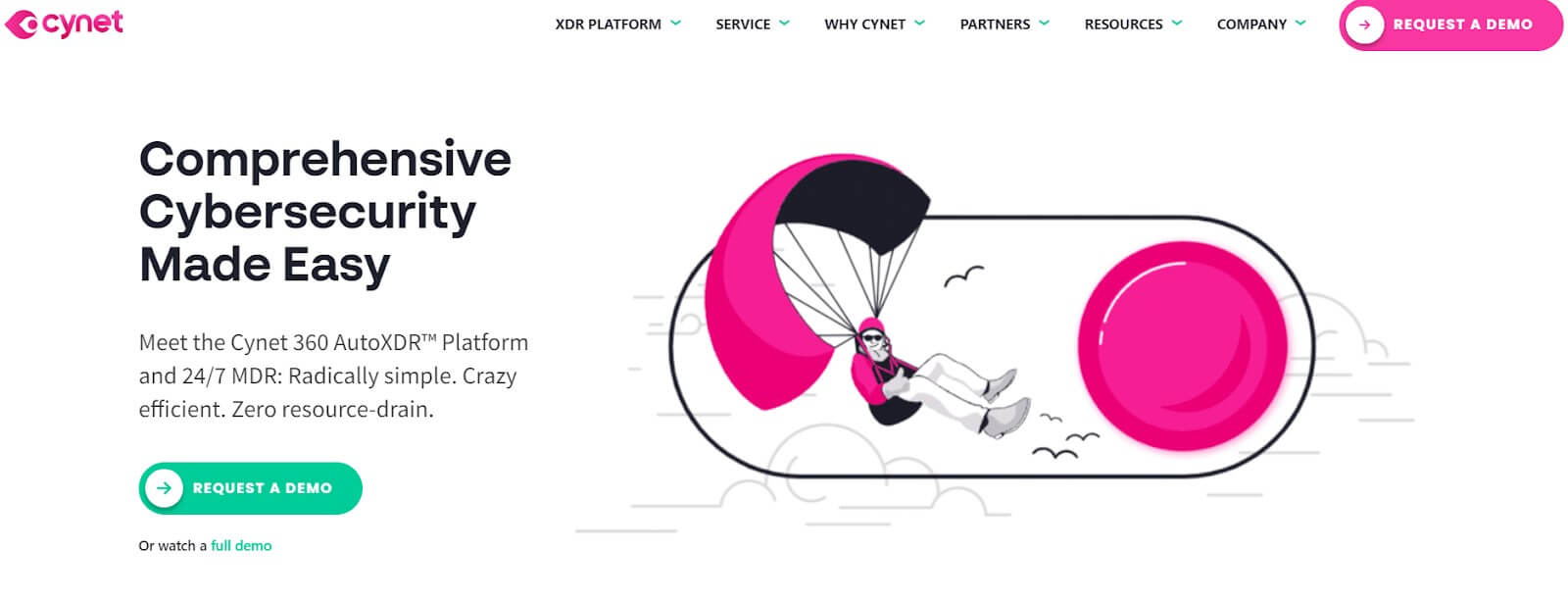
This software encompasses an array of features, including endpoint detection and response, threat hunting, and automated remediation, ensuring continuous monitoring and protection of endpoints.
With its user-friendly interface and seamless integration with existing security tools, Cynet 360 AutoXDR Endpoint Protection Software delivers a robust and efficient solution for safeguarding organizational endpoints from cyber threats.
We’ve been using them for about a year, the product is great, the MSP support, not so much. Our biggest gripes with the system is the licensing management, it’s clunky and confusing, and I believe it’s designed for MSP’s to lose track. You have to jump through hoops where other companies make license management very easy, like Sentinel or Huntress for example. We’ve brought this to the attention of the MSP TAM leader as a suggestion for future changes like other EDR/MDR companies do, only to find myself having to defend the issues we have with the system. They do not care to take suggestions or comments. They throw it back to you saying it’s already designed in the best way.
Reddit Review of Cynet 360 AutoXDR
6. KnowBe4 PhishER
PhishER plays a vital role in Cyber Security operations, serving as an intuitive Security Orchestration, Automation, and Response (SOAR) tool.
It streamlines threat response by automating the management of malicious email messages, enabling security teams to swiftly address high-risk threats.
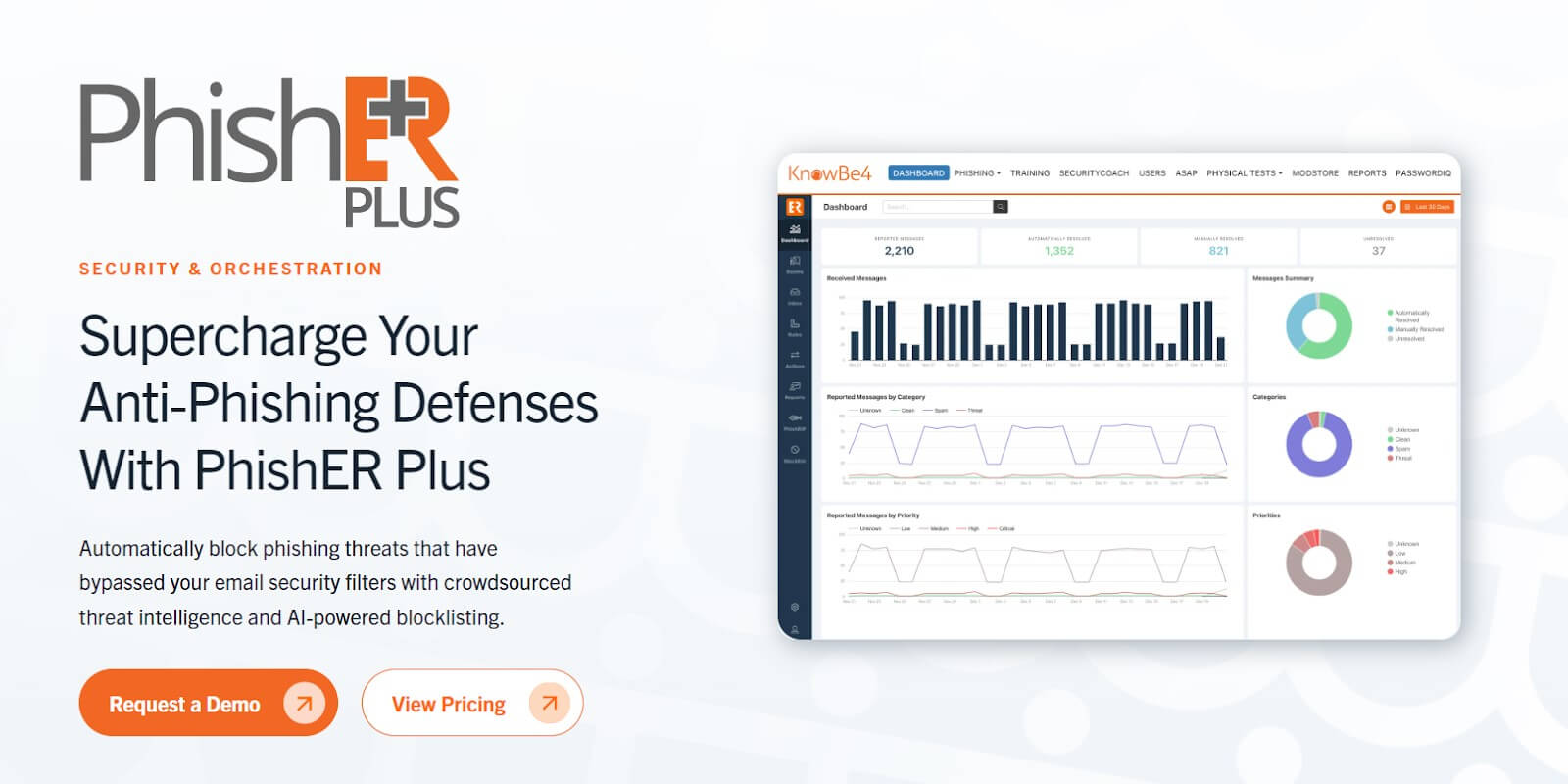
Additionally, PhishER efficiently handles a large volume of email threats simultaneously, ensuring comprehensive protection. It effectively automates the processing of the majority of reported emails, which are non-threats, optimizing workflow efficiency.
knowb4 is legit. roll it out to the company through 365 and have then report anything unusual and let me decide or block the domain. I’m proud to say the client I support had like 30 senders blocked and like 10-15 domains blocked. In less than 2 years I’ve blocked 500 senders and almost 300 domains. my staff is well trained thanks to kb4.
Reddit Review of KnowBe4 PhishER
7. Mandiant Incident Response Services
Mandiant’s incident responders possess extensive experience at the forefront of complex breaches globally, demonstrating a profound understanding of both established and emerging threat actors, alongside their evolving tactics, techniques, and procedures (TTPs).
Utilizing a blend of cloud and on-premise solutions, investigations commence promptly while addressing client data privacy concerns.
Mandiant incident responders promptly analyze network traffic and data from numerous endpoints within hours of engagement, supported by access to unparalleled threat intelligence from frontline attack research and other sources.
Acknowledging that comprehensive incident and breach response extends beyond technical aspects, support is extended to executive communication and crisis management, including legal, regulatory, and public relations considerations. Effective crisis management is crucial in mitigating reputational damage and legal liabilities.
Mandiant is the ghostbusters of incident response. They’re who you call. But they are costly, too.
Reddit Review of Mandiant
8. Rapid7 InsightIDR
Rapid7 InsightIDR serves as a cloud-based Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) solution, aiding IT security professionals in detecting and addressing security threats across hybrid environments.
Utilizing InsightIDR, data is collected and analyzed to proactively pinpoint potential security threats. Notable features include endpoint detection and response (EDR), AI-powered behavioral detections, vetted threat content, and advanced analytics.
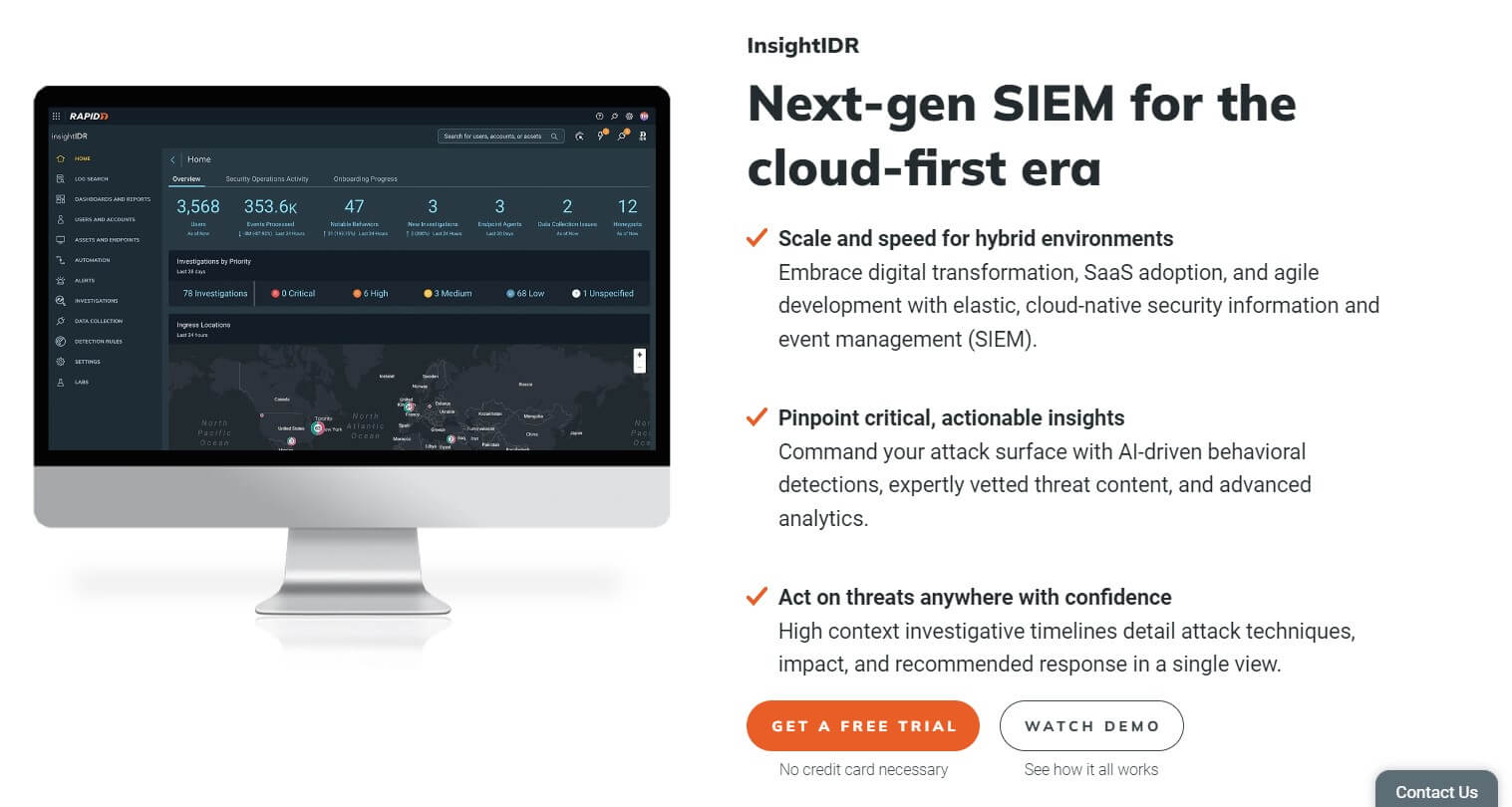
Moreover, InsightIDR offers streamlined one-click response and automation capabilities, doubling as a SOAR tool, and providing up to tier 3 SOC analysis.
Additionally, it boasts an XDR agent that bolsters Identity and Access Management (IAM) security for Active Directory users.
I am using Rapid7 IDR and their features have improved a lot. It depends on how you configured and how many sources you are adding… in combination with the Rules.
Reddit Review Rapid7 InsightIDR
9. Cisco SecureX
Cisco SecureX represents a cloud-native security suite that integrates threat intelligence, defensive measures, and response capabilities from both Cisco and third-party security and networking products.
Its purpose is to assist businesses in tackling security obstacles by establishing a seamlessly integrated ecosystem that facilitates the sharing of threat intelligence and coordinated response efforts.
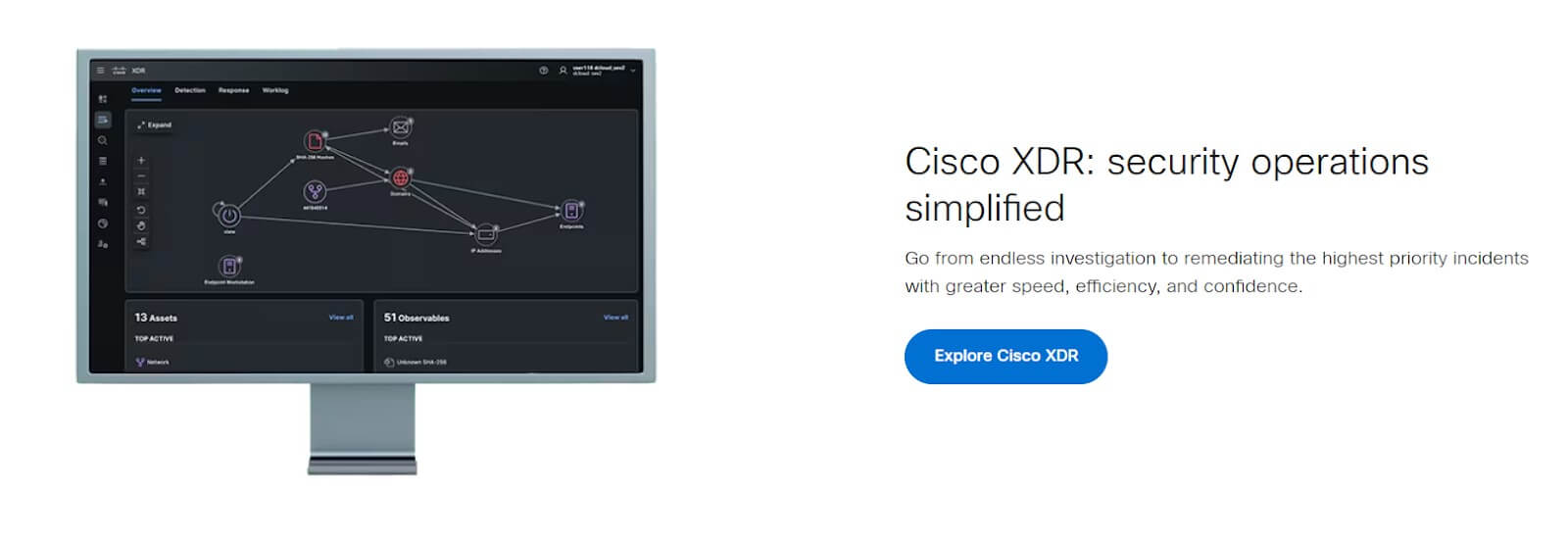
By unifying visibility, enabling automation, and fortifying security across networks, endpoints, cloud environments, and applications, SecureX equips users to detect, investigate, analyze, and respond to threats effectively, leveraging data aggregated from various products and sources.
Furthermore, SecureX ensures the enforcement of security policies throughout the entire distributed network, extending beyond a singular point in the data stream.
The power of secureX is the orchestration in my opinion. Our analysts use the secureX ribbon mostly which is being rolled out to more and more products.
Reddit Review of Cisco SecureX
10. Splunk Enterprise Security
At its core, Splunk Enterprise Security functions as a robust SIEM solution, empowering security personnel to swiftly address cybersecurity threats, streamline threat management processes, and safeguard organizations.
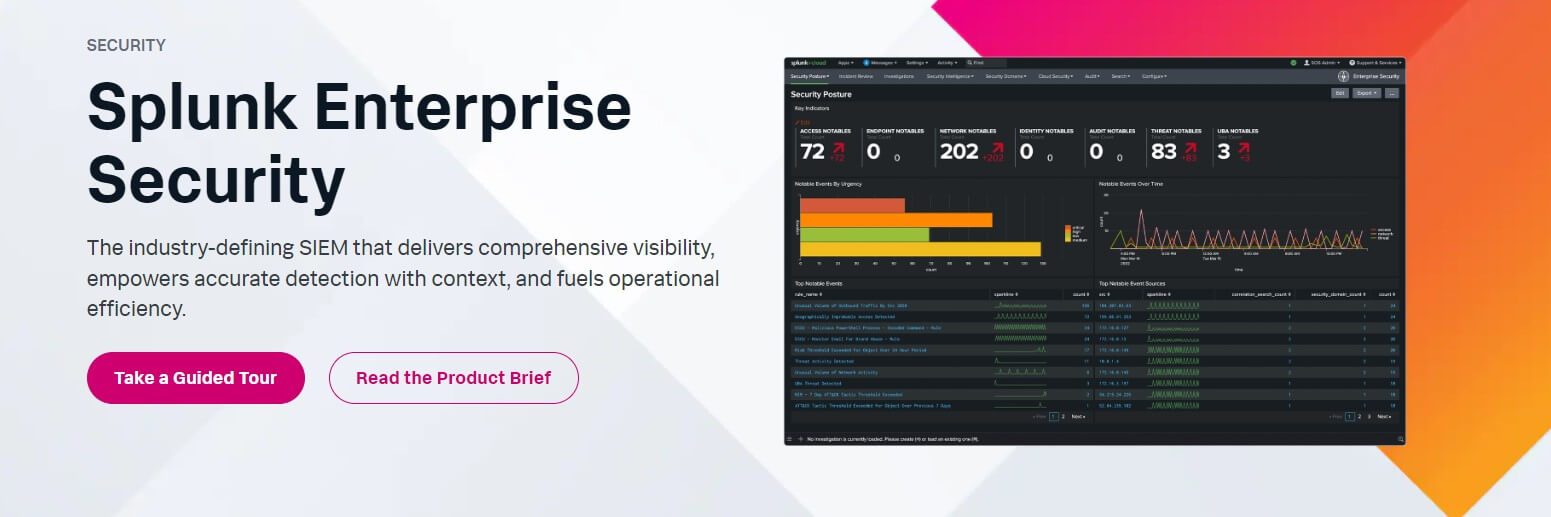
By leveraging data from various touchpoints, security professionals can attain a comprehensive understanding of security landscapes, facilitating informed decision-making. Splunk ES facilitates continuous monitoring, proactive incident response, efficient security operations, and executive-level assessment of business risks.
It can be deployed either as software alongside Splunk Enterprise or as a cloud-based solution in conjunction with Splunk Cloud.
I’ve always thought of myself as a Splunk fanboy and started to think maybe I’m just biased and maybe there is a better tool that is cheaper. So in my most recent position I sought to challenge that bias and we ended up not going with Splunk. One year later we are ripping it out and replacing it with Splunk.
I’ll preface this by saying it very much depends on the maturity of your security team, and what your team hopes to use the tool for and how much you intend to use and train yourself on the product.
Reddit Review of Splunk
11. AT&T AlienVault USM
AlienVault Unified Security Management (USM), a cloud-hosted offering from AT&T Cybersecurity, aids organizations in monitoring security across their networks and devices.
USM streamlines threat detection, incident response, and compliance management by consolidating these functions into a single platform, offering a unified view of alarms, vulnerabilities, and events.

Leveraging sensors, USM gathers and analyzes data from various sources across an organization’s attack surface, encompassing log data, packets, and other security-related information.
This data is transmitted to the USM Anywhere service, hosted within the secure AlienVault Secure Cloud. USM’s correlation engine automatically identifies and correlates behavioral patterns across diverse assets to detect potential security threats.
Additionally, log data is securely stored long-term in the AlienVault Secure Cloud, serving compliance and forensic purposes.
We are very unimpressed with their support, their product, and their deployment guides. All this after I advocated for AlienVault. I have implemented the OSSIM product for other customers a couple years ago and on my home test network (for education/experience). Product seems to be going downhill imo.
Reddit Review of AlienVault
12. Kaspersky EDR Expert
Kaspersky EDR Expert is an innovative EDR solution offering advanced endpoint protection, enhanced detection capabilities, and robust threat hunting and investigation features.
This sophisticated system is deployed by both SOC and IT operations teams for incident response purposes, allowing them to proactively hunt, prioritize, investigate, and mitigate complex threats and APT-like attacks.
Tons of settings for every little thing, if you like tweaking your AV this is your product. Seems pretty lightweight RAM-wise. I haven’t gotten around to testing its detection.
Reddit Review of Kaspersky EDR Expert
How Incident Response Software Benefits Organizations?
Let’s say a mid-sized e-commerce company detects unusual login activity on its website. Multiple failed login attempts from various IP addresses are flagged by their security monitoring system, suggesting a potential brute force attack.
In this case, their incident response steps would be:
- Identification: The security team confirms the suspicious activity and identifies it as a brute force attack attempt.
- Containment: To prevent further unauthorized access, the team temporarily blocks the suspicious IP addresses and enforces stricter login attempts limits.
- Eradication: They search for any malware or backdoors installed during the attack and remove them.
- Recovery: The team restores affected systems and ensures that all security patches are up-to-date. They also reset passwords for potentially compromised accounts.
After the incident is resolved, the team reviews the response to identify any gaps or weaknesses in their security protocols and updates their incident response plan accordingly.
And, this brings us to an important question that how an incident response platform would have benefited the company?
In this example, an incident response platform could have made the team’s job even easier. Such a platform would provide real-time alerts, automated containment measures, and detailed reporting tools. This would allow the team to respond faster and more efficiently, minimizing damage and reducing downtime even further.
So, that means the benefits of an incident response platform include:
- Speed: Rapid detection and response reduce the impact of incidents.
- Efficiency: Automated workflows and tools save time and resources.
- Accuracy: Centralized data and analysis improve decision-making.
- Compliance: Helps meet regulatory requirements by maintaining detailed records of incident handling.
- Preparedness: Provides structured procedures and plans for various types of incidents.
Conclusions
The 12 best incident response software solutions highlighted in this guide offer comprehensive solutions for detecting, managing, and mitigating cyber incidents efficiently.
Among the best solutions available in 2026, Heimdal® XDR stands out as the ultimate choice for enterprise security needs.
With its comprehensive suite of tools and expertise, Heimdal® XDR ensures precise monitoring and swift response to cyber threats across endpoints, networks, emails, identities, and data.
Whether utilizing Microsoft 365 or Google Workspace, Heimdal® XDR provides unparalleled protection, enabling organizations to safeguard their assets and ensure business continuity.
Frequently Asked Questions (FAQs)
What Is Incident Response?
Incident response is the process of identifying, managing, and mitigating security breaches or cyber attacks to minimize damage and recover quickly.
What is incident management in software?
Incident management is the process used by IT teams to address disruptions and restore services to their operational state.
What is incident reporting software?
Incident reporting software simplifies the documentation and management of incidents within an organization. It enables users to report various incidents through a centralized platform, streamlining communication and resolution processes. Additionally, it may offer reporting and analytics features to identify trends and enhance incident response efforts.
What are the two types of incident reports?
There are primarily two types of incident reports: internal and external.
- Internal Incident Reports document incidents within the organization, helping improve processes, safety, and risk management.
- External Incident Reports, shared with stakeholders like regulators and partners, ensure compliance, transparency, and accountability.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











