Contents:
A DNS zone is a segment of the domain namespace. It works like an administrative area that enables more precise control over the domain namespace.
DNS zones contain DNS records. They hold name and IP address details for one or more DNS domain components.
Key takeaways:
- DNS zone transfer misconfigurations expose you to cyberattacks
- To keep safe from DNS zone transfer attacks, only allow trusted IP addresses to perform this process
- 91% of online threats use DNS. Use a DNS Security solution to secure your DNS
The Structure of DNS Zones
Below the DNS root domain, there is a hierarchical structure of subdomains that forms the Internet’s domain namespace. A DNS zone can start at a domain in the tree and can also widen onto subdomains allowing one entity to control many subdomains.
Every time subdomain space is registered or allocated, the registrant must keep up an administrative and technical infrastructure to handle zone management, including sub-delegation to lower-level domains. A DNS zone is a space that includes one or more subdomains and is designated for management.
However, you should not associate a DNS zone with a domain name or a single DNS server. This is a typical error because:
- a DNS zone can hold several subdomains
- several DNS zones can be located on the same server
As DNS zones are only used for control delegation, they don’t have to be physically isolated from one another.
DNS Zone Types
Primary zone
Primary zones read zone information directly from a host file and they can include a subzone, or child zone. Additionally, resource records like host, alias (CNAME), IPv4 address (A), IPv6 address (AAAA), or reverse mapping pointer (PTR) records may be contained by a primary zone.
Secondary zone
Secondary zones or “slave zones” are read-only copies of the primary zone and are kept on different servers. They can only retrieve updates from the primary zone, as they cannot process updates. Their role is to keep a complete copy of the zone for which they are secondaries.
Stub zone
Stub zones essentially transmit the name server (NS) records for those zones.
Forward zone
Forward zones route all requests to other servers for a specific zone.
What Is a DNS Zone Transfer?
A DNS zone transfer is a DNS transaction. It`s a communication method between a primary and a secondary server.
In the process, you transfer a copy of a section a.k.a. zone, of the DNS server database to another DNS server. IT administrators use the DNS zone transfer for distributing DNS databases across a group of DNS servers.
A zone transfer appears like a client-server transaction and uses the Transmission Control Protocol (TCP). You’ll need it in case you want to set up a new DNS server as a secondary DNS server. Zone transfers are frequently used to back up DNS files or to replicate DNS data across several DNS servers.
All DNS names and IP addresses a name server hosts will be provided in ASCII text. If the name server permits zone transfers, humans will be able to read the ASCII text.
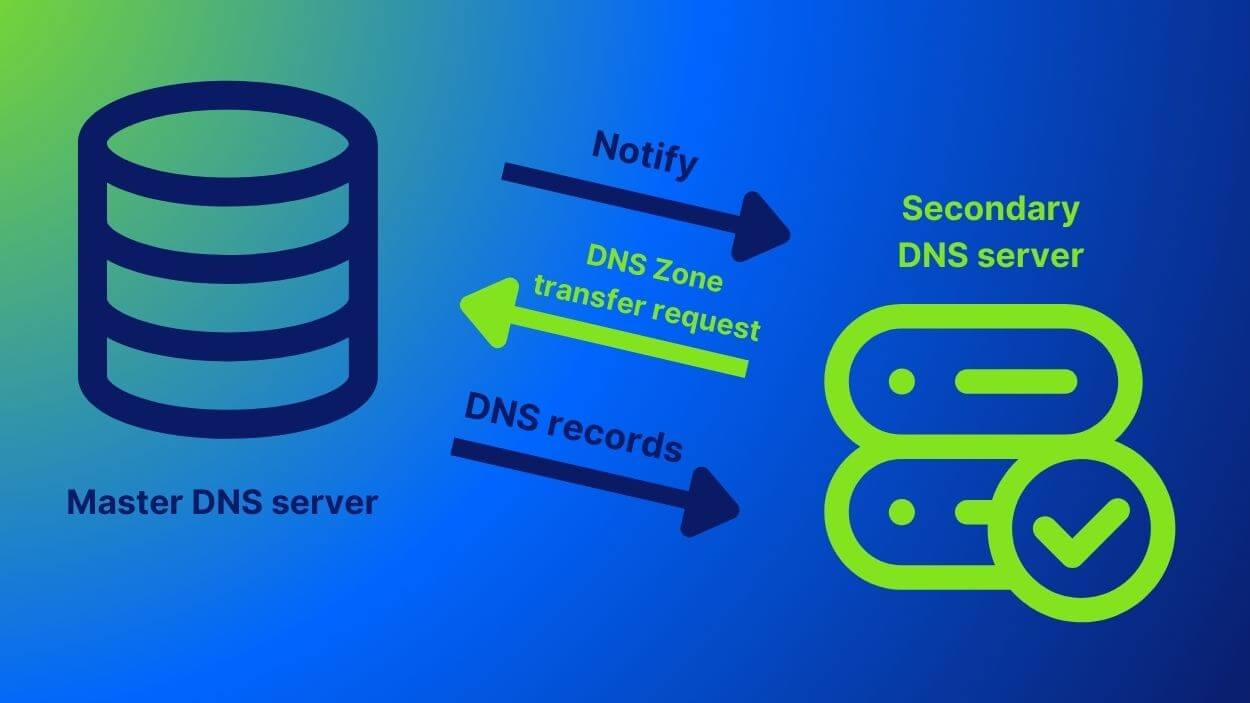
There are two main types of DNS zone transfer:
Authoritative DNS zone transfer (AXFR)
AXFR zone transfer is also called a full zone transfer. The process means that the Primary Server sends the whole zone file, with all the DNS records to the Secondary ones. AXFR allows you to keep all the secondary DNS servers up to date and makes easier adding new ones.
Incremental DNS zone transfer (IXFR)
The IXFR zone transfer, or partial zone transfer, only sends the latest changes from to the Secondary DNS servers. So, the process doesn’t copy the whole zone file. It works faster than AXFRs and you could use it if you only did minor changes, like adding some A records.
How Can a DNS Zone Transfer Attack Occur?
DNS zone transfer doesn’t request authentication. So, anyone pretending to be a client can query the DNS server for a copy of a zone.
Zone transfers replicate a domain’s database and send it from the primary server to the secondary server. Access to using zone transfer gives hackers visibility to all the DNS records.
Permitting externals to execute zone transfers on one of a domain’s DNS servers is a common DNS misconfiguration that puts sensitive data at risk. For the attackers, it’s like receiving a map of the network. That’s like helping them to plan the attack. That level of visibility over your network tells them where to redirect packets or how to launch a man-in-the-middle attack.
How to Prevent Malicious Zone Transfer
There are three ways to protect against malicious zone transfer:
- Completely disable the zone transfer option
- Create an exclusive list of trusted IPs that can perform a zone transfer
- Use TSIG keys (Transaction Signatures) to secure communication between DNS servers
Threat actors can learn a lot of information about their target networks and the hosts by observing the DNS. A poorly secured DNS can reveal sensitive data, like:
- intelligence on particular servers
- a server’s role in a specific IT structure
- data about what operating systems run across the network
- leaks of user names and IP addresses
How Can Heimdal Help Secure DNS
Heimdal DNS Security – Network offers you specialized threat hunting, complete network visibility, and A to Z protection, no matter the device or operating system you use. The Hybrid DNS module included in DNS Security – Network adds extensive filtering capabilities to any local DNS server. You can use it to secure DNS traffic in your internal networks without having to direct DNS queries to Heimdal’s TPN resolvers.
This DNS security solution offers 96% accuracy in detecting and predicting future attacks and protects you against APTs, data leaks, ransomware, and network malware.
You can use whatever DNS forwarder you like and benefit from the local DNS resolver’s ability to have a dynamic IP. Because of this, both on-premises and cloud-based DNS environments can benefit greatly from DNS Security – Network.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;
Wrapping Up
DNS zone transfer puts one more exploiting opportunity on the Internet’s infrastructure map and hackers will surely know how to make use of it. As you might already know, 91% of online threats leverage DNS, so securing your network at DNS-level is not just nice to have, it is mandatory, for keeping your system safe.
DNS zone FAQs
How is a DNS zone different from a domain?
A domain is a human-readable name that points to an IP address. Its role is to make using Internet easy for humans. A DNS zone is an administrative space within the DNS. It contains all the DNS records of a domain.
DNS zone transfer uses TCP or UDP?
The DNS uses both TCP and UDP. While DNS zone transfers use TCP port 53, DNS queries use UDP port 53. DNS zone transfers always happen through TCP to maintain consistency in the DNS Zone database.
How can hackers perform a DNS zone transfer attack?
Gaining access to a DNS server that allows zone transfers enables hackers to launch a DNS zone transfer attack and view all DNS records.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








