Contents:
The Conti Ransomware-as-a-Service had its golden era between 2020 and early 2022, with $180 Million earnings/ year. Their victims’ list included hundreds of businesses, hospitals, schools, emergency services, and the Costa Rican and Peruvian governments.
A few months after pledging their support for the Russian state in their war against Ukraine, the threat gang collapsed.
Key takeaways
- The Conti ransomware group was active between December 2019 – May 2022.
- In 2021 its recorded revenue was $180 million.
- The group targeted not only businesses, but also healthcare and educational institutions, emergency services, and governments worldwide.
- Rapid data encryption capabilities, double extortion, and paying affiliates a fixed wage set Conti apart from other ransomware groups.
- Conti used phishing, TrickBot, and BazarLoader Trojans for initial access.
- Announcing their support for Russia in the Ukraine war and an internal data leakage caused the disbandment of Conti.
- The Conti group disappeared only as a brand. Its members dispersed into other threat groups.
What is Conti Ransomware?
Conti was a Russia-based ransomware-as-a-service. It was known for:
- the speed with which it encrypted data and spreaded Conti ransomware to other systems
- being among the first threat groups that used double extortion techniques
- paying its affiliates a fixed wage, not a commission.
According to MITRE, researchers first observed it operating in December 2019. At first, it went under the Wizard Spider pseudonym. The threat actors used TrickBot to deploy Conti ransomware on their targets.
In early May 2022, the US government announced a reward of up to $10 million for information on the Conti ransomware gang.
Conti was a ransomware variant used to attack more than 900 victims worldwide, including victims in approximately 47 states, the District of Columbia, Puerto Rico, and approximately 31 foreign countries. According to the FBI, in 2021, Conti ransomware was used to attack more critical infrastructure victims than any other ransomware variant.
Source – The US Department of Justice, Office of Public Affairs
How did Conti Ransomware operate?
The group used phishing attacks to install the TrickBot and BazarLoader Trojans to obtain remote access to the infected machines.
The message they used pretended to come from a sender the victim trusted. They tricked the victim to download malicious document from Google Drive. Once they downloaded the document, a Bazaar backdoor malware also installed on the compromised device. The Backdoor connected the victim’s machine to Conti’s command-and-control C2.
Additionally, Conti used a multithreading method in order to spread fast, making it tough to stop.
Conti ransomware could also spread via Server Message Block (SMB). This is actually how they were able to encrypt data on other machines in a network.
After it infected a computer, Conti encrypted the data and exfiltrated it, so it can apply a two-step extortion scheme.
Double extortion ransomware is also known as pay-now-or-get-breached. Initially, the attackers exfiltrates large quantities of private information. Then they encrypt the victim’s files.
The scheme starts with a ransom demand in return for the decryption key. Once they get the money for decrypting the documents on the victim’s computer, they continue extortion. They threaten the victim to leak on the dark Web the sensitive data they have exfiltrated.
Usually, the hacker reveals on a dark forum a small amount of the encrypted data, with the threat of releasing additional material if the ransom is not paid.
Initial Access
Just like many other threat groups, Conti ransomware operators mainly used phishing techniques for gaining initial access. Social engineering and spear phishing campaigns were among their favorite methods to obtain credentials.
They also exploited vulnerable firewalls, exploited unpatched CVEs, and attacked internet-facing RDP (Remote Desktop Protocol) servers.
Privilege Escalation
After establishing network access, the attackers focused on gaining access to a domain admin account. To disable security tools and evade detection they used batch files. To move laterally inside the network, Conti used the Server Message Block port to spread to other computers.
They targeted any privileged accounts that would allow them to steal important information, including backups.
Succeeding in privilege escalation allowed the hackers to run their ransomware code.
Reconnaissance
In the reconnaissance phase, Conti ransomware group scanned the network for servers, endpoints, backups, sensitive data, apps, and protection software. They used popular port scanners like ‘Angry IP Scanner’ or ‘Advanced Port Scanner’ to compile a list of IP addresses.
Furthermore, they collected a list of server names to look for hints as to what they’re for. A Domain Controller, for example, is likely to be named DC1.
Getting the Credentials
Just like other ransomware groups, Conti used popular post-exploitation tools like Mimikatz, which dumps credentials from memory.
Backdoors
To obtain persistence inside the system and communicating with the Command-and-control center, Conti installed a backdoor.
Backdoors allow hackers to exfiltrate data and monitor network traffic to observe how the victim was recovering from the attack. Conti frequently used programs like AnyDesk and Cobalt Strike to help them with remote access and control. Tor proxies helped them hide their contact with the C&C server.
Data Harvesting
Before running the ransomware code, the attackers stole as much business-critical data as possible. They either exfiltrated data:
- towards their own server
- through email
- uploading it to one or more anonymous cloud storage containers
Ransomware Deployment
The actual ransomware attack happened once they have:
- exfiltrated as much data as possible
- deleted/encrypted any backups
- deactivated the necessary security measures
The Conti ransomware group used multi-threaded encryption. That enabled them to encrypt files quicker than any ransomware groups.
They used remote code execution to infect with ransomware as many servers and endpoints as possible. One of their methods was to infect a logon script in a Group Policy Object (GPO), which runs the code every time the computer starts up and joins the domain.
Activity Monitoring
The attackers used backdoors to monitor the way in which the victim reacts to the attack. They also kept an eye on emails to see how the victim plans to go forward with the rehabilitation process.
If the victim tried to recover their files in order to avoid paying the ransom, the attackers tried to initiate a second attack.
Conti Ransomware most famous attacks
JVCKenwood
JVCKenwood is a Japanese multinational electronics company headquartered in Yokohama, Japan that, among others, focuses on car and home electronics, wireless systems for the worldwide consumer electronics market.
The company is one of the victims that suffered a ransomware attack conducted by the Conti ransomware group.
Security specialists say that Conti has accessed and stolen almost 2TB of information belonging to JVCKenwood’s customers and suppliers.
The ransomware attackers asked for a ransom of $7M not to publish the stolen information and provide a decryptor.
The City of Tulsa
The threat actors deployed a ransomware attack on the City of Tulsa’s network. Tulsa’s infrastructure suffered from a major ransomware attack.
The attack had a massive impact as the city shut down its network to prevent the spread of malware.
This forced mitigation plan – shutting down the network – had however a significant impact on the residents. For a while, they were unable to access the online bill payments systems and other significant e-mail-based services.
All this time the City of Tulsa, Tulsa City Council, Tulsa Police, and Tulsa 311 appeared “down for maintenance”. In other words, the City had to shut down all of its systems and disrupt all online services.
Ireland’s Health Service
Ireland’s Health Service is Ireland’s publicly funded healthcare system.
The Conti ransomware attack forced the organization to shut down all of its IT systems.
The IT outage led to a massive disruption in the country’s healthcare infrastructure. Therefore, citizens had limited access to diagnostics and medical records. There were transcription errors due to handwritten notes, and slow response times to healthcare visits.
The Conti gang claimed to have had access to the HSE network for two weeks and allegedly have stolen 700 GB of unencrypted files. The compromised data included:
- patients’ and employees’ info
- contracts
- financial statements
- payroll, etc.
Conti said they would provide HSE with a decryptor and also delete the stolen data if the victim paid a ransom of $19,999,000.
The Costa Rican Government
Conti’s attack on the Costa Rican government’s network, in April 2022, was the ransomware gang’s way to say goodbye. The attack took 27 government agencies offline and made the authorities to declare a national emergency on May 8th. It took the Costa Rican state more than a month to completely recover.
At first the Conti ransomware group asked for $10 million. After the government refused to cooperate, the attackers doubled the price.
The fall of Conti Ransomware
In February 2022, soon after the war in Ukraine outburst, Conti declared their support for Russia. Researchers think this was the beginning of the end. 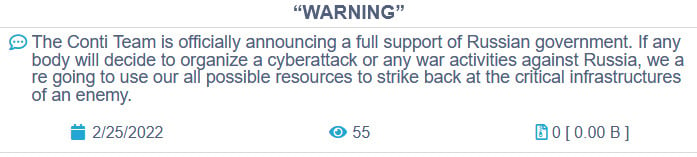
First, the “ContiLeaks” Twitter account leaked the group’s internal communication. There were 393 JSON files containing over 60,000 internal chats stolen from the Conti and Ryuk ransomware gang’s private, encrypted XMPP chat server.
Allegedly, it was a gang member of Ukrainian origins that published online Conti’s:
- chat messages
- salary structures
- the threat group’s day to day activities
- the group’s structure
- bitcoin addresses
- law enforcement evading methods
- the BazarBackdoor API
- photos of storage servers
The insider whistle-blower also leaked a password-protected ZIP containing the source code for the Conti ransomware encryptor, decryptor, and constructor.
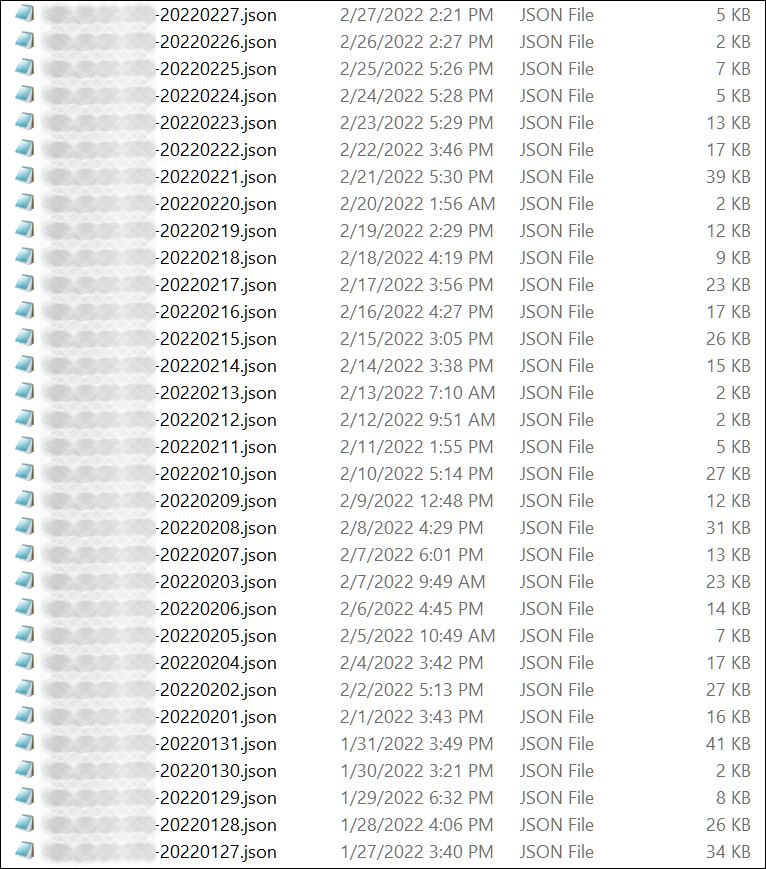
After a massive attack targeting the Costa Rica government, Conti closed down their website and ceased ransomware attacks. On May 19, Conti’s website and negotiations service went offline, along with its other public facing infrastructure. This put an end to Conti ransomware attacks.
Conti RaaS Rebranded
As security researchers expected, in the cybercrime land nothing goes to waste. Specialists say Conti only vanished as a brand. Its hackers spread to other threat groups, like BlackCat, Hive, Bazarcall Collective, or Karakurt. They changed their business model from a centralized to a network structure approach. At the moment, researchers say Conti reshaped into:
- Autonomous groups – Conti members infiltrated Karakurt, Black Basta and BlackByte. Those threat groups don’t practice encryption, but data exfiltration and extortion.
- Semi-autonomous groups – AlphV (BlackCat), HIVE, HelloKitty (FiveHands), and AvosLocker are other threat gangs that include ex-Conti members. BlackCat received a massive blow at the end of 2023, but the threat gang seems to have recovered its strength since then.
- Independent affiliates – Some prefer to work solo while continuing to be loyal to the organization.
Ransomware Prevention Measures
Here is a quick list to help you prevent ransomware attacks. You can check this article for a more detailed approach on ransomware prevention.
- Patch your operating systems, software, and firmware as soon as possible.
- Update passwords on a regular basis.
- Don’t reuse passwords for several accounts
- Protect your most sensitive data through end-to-end encryption
- Enable multi-factor authentication
- Deactivate any ports that you don’t use
- Educate your employees to identify phishing emails.
- Deploy cybersecurity solutions to cover as much attack vectors as possible

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Wrapping Up
With the right knowledge and proper practices, as well as a reliable suite of solutions, staying safe from data breaches can come easy.
As always, Heimdal™ Security can help you with the latter. Contact us at sales.inquiries@heimdalsecurity.com or book a demo to find out which of our company products suit your needs.
If you liked this article, follow us on LinkedIn, Twitter, YouTube, and Facebook to keep up to date with everything we post.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








