Contents:
New information about how the Conti ransomware group compromised the Costa Rica government has come to light, demonstrating the attack’s accuracy and how fast it moved from initial access to the final phase of encrypting machines.
The Conti ransomware organization only launched one more attack (Costa Rica) before switching to a different organizational structure that depends on numerous cells cooperating with other gangs.
Let’s Dig Deeper into the Attack on the Costa Rica Government
The Conti ransomware operation, which was initiated in 2020 to take the place of Ryuk, quickly gained notoriety after attacking targets in both the private and public sectors, including American local governments, educational institutions, and national healthcare systems. The highly destructive ransomware is believed to be the work of a Russia-based cybercriminal organization that goes by the alias Wizard Spider.
On April 11, 2022, the gang launched their final attack under the Conti name after obtaining initial access to the network of the Costa Rican government and conducting reconnaissance activity.
The steps taken by the Russia-based cybercrime group, from gaining initial access to stealing 672GB of data on April 15 and deploying the ransomware, are explained in a report published by cyber intelligence company Advanced Intelligence (AdvIntel).
According to BleepingComputer, the attacker entry point was a system belonging to Costa Rica’s Ministry of Finance, to which a group member called ‘MemberX’ managed to obtain access over a VPN connection utilizing hacked login information.
Advanced Intelligence CEO Vitali Kremez claims that the impacted credentials were collected due to the malware that has been deployed on the initial machine hacked on the user network.
As per the report put together by the AdvIntel security experts, over 10 Cobalt Strike beacon sessions were installed in the early phases of the cyberattack.
The infection followed a typical attack flow wherein the adversaries gained access from the compromised VPN log by installing a crypted form of Cobalt Strike inside the Costa Rica sub-network.
After gaining local network domain administrator access, the threat actor utilized the Nltest command-line tool to enumerate domain trust relationships.
The cyber intelligence firm provides detailed information on the ransomware gang’s activity on the Costa Rica government network, including the specific commands used at each stage.
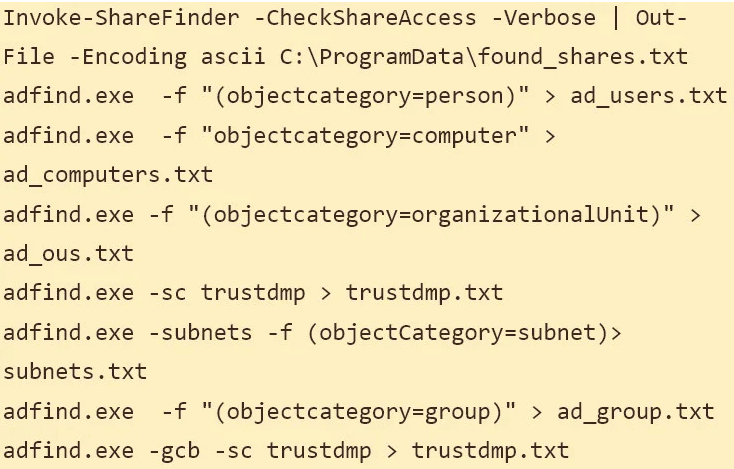
The experts said that the fileshare output was then downloaded to a local device by MemberX using the Cobalt Strike backdoor channel. The hacker gained access to administrative shares, where they uploaded a Cobalt Strike DLL beacon and used the remote file execution tool PsExec to run it.
The researchers also state that Conti developers used the open-source, credential-dumping application Mimikatz to carry out a DCSync and Zerologon attack that granted them access to all the hosts on Costa Rica’s interconnected networks.
In order to ensure that they wouldn’t lose access in the event that security specialists find the Cobalt Strike beacons, the attacker installed the Atera remote access tool on machines with less user activity where they had administrator rights.
The adversaries pinged the whole network and re-scanned the network domain trusts, leveraging enterprise administrator credentials with ShareFinder and compiling a list of all corporate assets and databases available under their new elevated privileges.
Due to the use of the Rclone open source, multi-threaded, command line computer program, which can handle files on various cloud storage services, data theft was possible. This was used by the Conti ransomware gang to upload files to the MEGA file hosting service.
Bye, Bye, Conti!
A note on the Conti leak website suggests that the initial ransom demand was $10 million, but when Costa Rica declared that it was not paying it, it was raised to $20 million. Nevertheless, according to AdvIntel, messages between Conti members revealed that the price was significantly lower than $1 million.
In response to attacks by the Conti ransomware organization on numerous government bodies, Costa Rican President Rodrigo Chaves declared a national emergency on May 8th. Some of the impacted institutions restarted activity in early June.
About a week later, the creators of Conti ransomware began to wind down the business by taking some of the infrastructure offline and declaring that the brand doesn’t exist anymore.
Everything came to an end at the end of June when the ransomware gang decided to take down the data leak site and all the websites used to negotiate ransoms with victims.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










