Contents:
There’s been a lot of talk about the Angler exploit kit lately, but, for most people, the warnings don’t strike a chord. And they’re definitely not to blame.
Not everyone has the time to Google “Angler exploit kit” and read 4-5 articles to understand what it’s about. And the fact that most articles on the subject are technical analyses doesn’t really help.
So we set out to create the ultimate guide to Angler exploit kit for non-technical people, an article that explains the basics:
- What exploit kits are
- Why Angler stands out among exploit kits
- Its top capabilities
- How Angler spreads
- What your antivirus can(‘t) do about Angler
- Recent developments in Angler’s activity
- How to keep your system safe from Angler
- A list of technical analyses for those who want to dive deeper in the subject.
But why do I need to know this stuff?
Fair question. The answer is simple enough: because you’re a target as well.
As you’ll see, you don’t need to be rich, famous, in politics or sports to become a cyber crime victim. All you have to do is have an Internet connection and use it. That’s all it takes, sadly.
But it doesn’t mean you’re defenseless. Au contraire, the fact that you’re reading this is already making you smarter and more aware than cyber criminals want you to be. So keep scrolling and give them an unexpected surprise.
1. What is an exploit kit?
Let’s start with the basics.
It is basically a piece of code engineered for malicious purposes. What it does is open a channel that cyber criminals can use to communicate with your system and feed it codes which include different types of commands.
As you’ll see, exploit kits are big business in the cyber criminal world. Here’s where it all started:
The first recorded exploit kit attack could be traced back in 2006, which used the WebAttacker kit.
This was the first exploit kit found in the Russian underground market. It came with technical support and was sold for US$20.
Source: Evolution of Exploit Kits by Trend Micro
The exploit kit is engineered by the attacker to perform at least 3 core actions:
- To scan your system for vulnerabilities
- To exploit the vulnerabilities it discovers by downloading malicious code into your system
- To execute malicious code on your system which basically means that it is able to install malware on your device.
The exploit kit usually targets browsers or other programs that a website can invoke through any of your browsers (Adobe Reader, Java Runtime Environment, Adobe Flash Player, etc.).
Exploit kits include a set of commands that can make a system behave abnormally. They can be used to disrupt the activity in software, hardware and anything else that is electronic.
But remember: it doesn’t mean that, if your system is infected, you can figure out that it’s happening on your own.
If we could see these infections with the naked eye, it would be much easier to stop them. But that ship has sailed sometime in the ‘90s and it’s not that simple anymore.
Example:
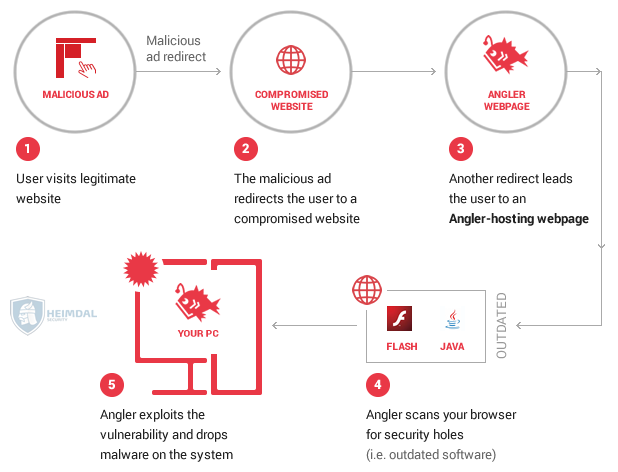
You click on a Google search result looking for more information on a GoPro camera. You end up on a blog that offers a review, so you browse around, but close it afterwards.
While you’re on the website, here’s how an infection can happen in less than a second:
- The attackers redirect your browser to a malicious website that hosts an exploit kit (this is called a drive-by attack)
- The exploit kit then proceeds to scan your browser to see if there are any security holes
- You may have not installed the latest Java updates (nod silently if you hate them too – you’re not alone)
- Since the Java plugin in your browser is vulnerable, the security hole in it could give the exploit kit a way into your system
- Here, the exploit kit can drop the payload, which is the part of malware which performs the malicious action
- The payload will then proceed to apply what is was programmed to do: collect your financial information (credit card details, online banking passwords and usernames, etc.), encrypt your data and ask for ransom or other actions, which we’ll present further on.
Shortly, this is how cyber criminals take advantage of the security holes in your system so they can infiltrate and carry out their attacks. They don’t require any input from you, as a user and the entire process is invisible. But, of course, there is more to this story.
You may have noticed that nowhere in this process have I mentioned the antivirus protection kicking in. There are 2 reasons for this:
- Unfortunately, not everyone has antivirus installed, which makes these users walking targets
- The most used exploit kits are so sophisticated that they manage to avoid being detected antivirus products. Keep reading to find out why.
There are certain exploit kits that have become infamous for their abilities. This is why they’re used to deliver some of the most sophisticated forms of malware.
What these exploit kits can do will make you want to follow some basic online security rules we’ve prepared for you at the end of this article. Just look at the surge in new exploit kits created in the past few years!
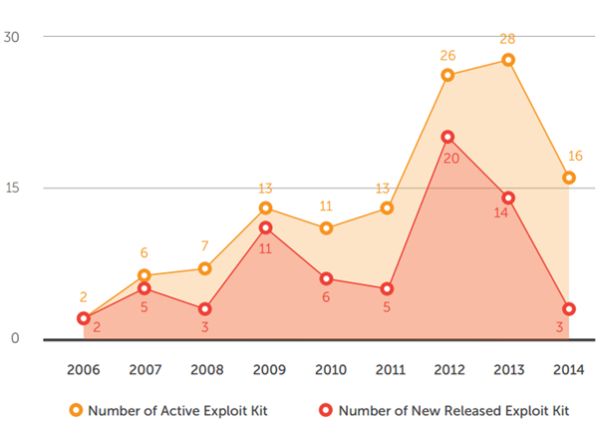
Source: Evolution of Exploit Kits by Trend Micro
2. Why does Angler stand out among exploit kits?
First identified in 2013, Angler is one of the most notorious exploit kits used in cyber attacks. In its short history, Angler has gained traction because of its special characteristics. It has spread ransomware, it’s been involved in malvertising and even in hacktivism campaigns.
In 2014, it was the second most used exploit kit according to the 2015 Trustwave Global Security Report. It accounted for 17% of infections, while Nuclear, the top used exploit kit, generated 23% of infections.
Since March 2015, Angler has become even more active. Our team at Heimdal Security, as well as many other researchers have observed the exploit kit in their analyses.
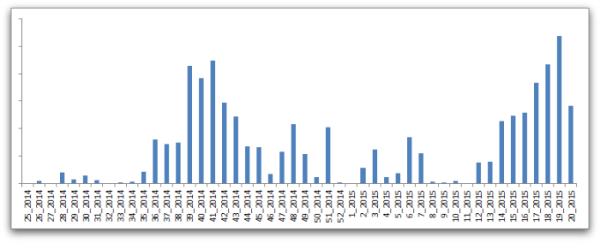
Source: Sophos’s “A closer look at the Angler exploit kit”
What’s more, according to Cisco’s Midyear Security Report, in 2015, Angler accounted for 40% of user penetration in the cyber attacks observed so far.
As you can clearly see, Angler dominates the exploit kit market at the moment and has been especially active in the past months.
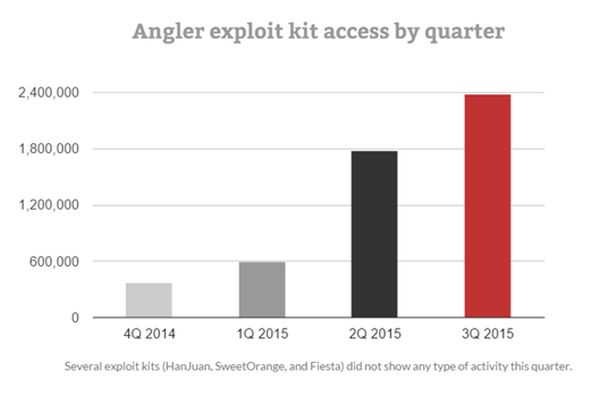
Source: Trend Micro, “Hazards Ahead: Current Vulnerabilities Prelude Impending Attacks”
But these Angler exploit kit statistics alone don’t paint the entire picture. What’s important is the set of factors that made Angler achieve such a wide distribution and high usage. News about Angler spreads like wildfire in the cyber security community because of what this exploit kit can do.
Angler continues to lead the exploit kit market in terms of overall sophistication and effectiveness.
3. The top capabilities of the Angler exploit kit
There are many reasons why Angler ranks so high among the cyber criminals’ preferences. We’ve tried to gather some of them here, without going too much into technical detail. For those who want to dive deeper into the subject, you can find a list of technical analyses at the end of the article.
So here’s what the infamous Angler exploit kit can do:
It can be easily used by attackers who lack deep technical knowledge.
Attackers who are not IT or security experts can purchase the exploit kit online. They don’t have to know how to create the kit themselves and they can still reap the benefits by using the kit.
Sometimes, exploit kits such as Angler even come with a user-friendly interface. This enables the attacker to track the evolution of the malware campaign and adjust the settings for more effective results.
I bet you didn’t think it was that easy…
It’s sold in cyber criminal circles and up for anyone to buy.
Cybercrime-as-a-service is not new, and we’ve been talking about it for a while. Exploit kits such as Angler are sold in cybercriminal circles, for a good price. Sophos speculates that there may even be a “pay-per-install” payment model, where attackers are charged by Angler creators only for the successful malware infections.
To make the exploit kit even more appealing, its creators even preload it with vulnerabilities, making the kit ready to be deployed.
It can be programmed to perform a vast number of actions.
Angler is a very versatile exploit kit. Cyber criminals can instruct the kit to:
- install malware (financial – Tinba, Vawtrak, ransomware – CryptoWall, Teslacrypt, Torrentlocker)
- collect confidential data (usernames, passwords, card details, etc.) and upload it to the servers they control
- or tie the infected system into a botnet (a “zombie army” of computers used to deliver additional attacks).
For example, here are the types of malware that Angler installed on vulnerable systems via drive-by attacks in April 2015:
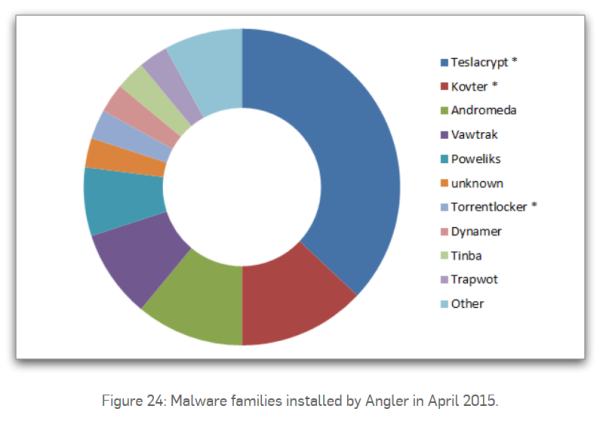
Source: Sophos, “A closer look at the Angler exploit kit”
It focuses on vulnerabilities in outdated software.
This factor alone is a huge reason why Angler is so successful in installing malware on users’ PCs.
How many times have you ignored an update from one of your apps or from your operating system?
We’ve all done it. Millions of Internet users still do it on a daily basis, because of a number of reasons which are not important right now.
What IS important is that Angler takes advantage of all these security holes in your system. And there are plenty to choose from!
As a cyber security specialist once said, cyber criminals only have to find one vulnerability, but we have to patch them all.
It integrates new vulnerabilities fast!
Angler’s popularity increased because its developers are able to add exploits for new vulnerabilities very quickly. When a Zero-Day vulnerability hits the market, Angler is among the first to integrate it, especially if we’re talking about Flash.
For example, here are the most common malware vectors identified by Cisco in the first half of 2015:
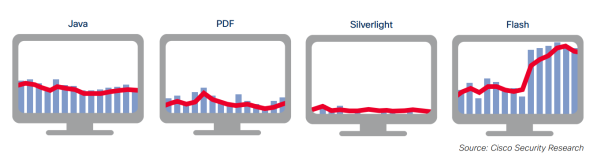
Source: Cisco 2015 Midyear Security Report
Flash already has one of the worst reputations in terms of software vulnerabilities. So of course that the team behind Angler looks at it first, because Flash offers so many security holes to exploit.
Because it’s so adaptive, creators can add new vulnerabilities to Angler as well as remove existing ones very fast. This makes it prime for purchase in cyber criminal circles.
It tries to evade detection at each stage of the infection.
Innovation is key for Angler and its development. Its creators seem to take this very seriously, because they constantly adapt their tactics to evade being detected by security products, especially antivirus.
Shortly, here’s how it’s done (it may get a bit technical here, but not too much):
To evade reputation filtering it switches hostnames and IP numbers rapidly, as well as using domain shadowing to piggyback on legitimate domains. To evade content detection, the components involved in Angler are dynamically generated for each potential victim, using a variety of encoding and encryption techniques. Finally, Angler uses obfuscation and anti-sandbox tricks to frustrate the collection and analysis of samples.
Source: Sophos, “A closer look at the Angler exploit kit”
The cyber criminals behind Angler thought of every little detail when engineering this exploit kit. This is why it takes so long to spot and why your antivirus can’t protect you from malware infections delivered by Angler.
Here’s more on the subject, below.
It can deliver “invisible” malware infections.
Angler is often used in drive-by attacks, which we discussed at the beginning of the article.
In both cases, the attack is not at all apparent. This is especially because the antivirus protection doesn’t kick in. That is why drive-by attacks are some of the worst and most Internet users have no idea they even exist or can happen.
What’s more, Angler can deliver “fileless” infections, which means that, throughout the process, not a single file will be downloaded by the attackers into your PC. Traditional antivirus products scan your files to detect malware infections. But if there’s no file to scan, then it just concludes that there’s no infection either.
Another factor that contributes to Angler’s success is that the encrypted payload it uses. The payload represents the attacker’s commands. In order for antivirus to block the infection, it has to first decrypt the payload. Then it has to analyze it, quarantine it and then delete it.
While antivirus struggles to do all that, the malware is installed onto the system and is already extracting information or doing what it was instructed to do.
This is why it can take up to a few days for your traditional antivirus product to warn you that there’s an infection in your system. By then, your data will already be in the hands of cyber criminals. Or encrypted and waiting for you to pay hundreds of dollars to decrypt it.
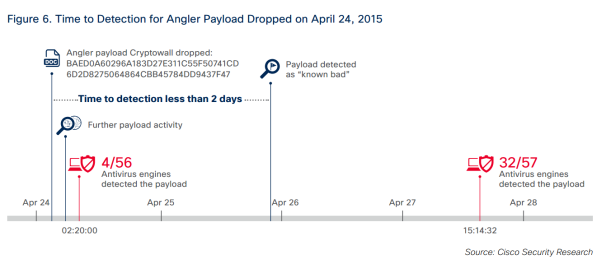
Source: Cisco 2015 Midyear Security Report
As this example from the 2015 Trustwave Global Security Report shows:
They [the Angler developers] even included a Zero Day of their own for Adobe Flash (CVE-2015-0313/CVE-2015-0311) that went undetected for two months.
Its distribution tactics make it difficult to block.
Cyber criminals know that the key to flying below the radar is to move fast.
Here’s how they manage to spread Angler and keep their identities anonymous at the same time:
- They look for web servers they can compromise.
- They basically hack into the websites hosted on those servers.
- Once they’re in control of the server, they create massive amounts of subdomains loaded with Angler
- They send victims through spam campaigns or malvertising campaigns to those subdomains, where they get infected with Angler.
- They continue to consolidate their infrastructure constantly (read more about Angler’s infrastructure).
The problem is that these subdomains are created in enormous volumes, they have a very short lifespan and they are random. Not having a pattern to follow or providing the time to be analyzed, these infection tactics are very difficult to block.
The kit [Angler] camouflages itself as legitimate web pages, making it difficult to block without inadvertently blocking other legitimate applications.
Source: 2015 Trustwave Global Security Report
For example, here are some numbers from Dridex campaigns which unfolded this year and were analyzed by Cisco.
- The malware campaign happens fast (9h), before traditional antivirus can react
- Multiple campaigns are delivered in this very short timeframe (850)
- The attackers use Microsoft macros to deliver the financial malware
- The attackers quickly morph campaign content such as user agents, attachments and referrers, and relaunch campaign.
Source: Cisco 2015 Midyear Security Report
And the cycle happens over and over again.
It uses hacked credentials from data breaches to spread further.
After all the data breaches that have made the news so many times over, millions of compromised credentials ended up on the dark web. These are for sale as well.
For example, if your email was involved in one of the recent breaches, it’s most likely up for sale on some dark web market. Along with your username, password and even card details. And there is a lot more information that cyber criminals can gather, based on these clues.
Of course, the cyber criminals behind Angler have made use of these credentials, especially compromised DNS records.
By using hacked credentials and DNS records, cyber criminals have managed to substantially increase their reach. At the same time, they also used this to cover their tracks and stay anonymous and avoided being discovered by law enforcement.
It uses believable, well-built landing pages to deliver the exploit.
Another essential factor that helps a malware campaign reach as many victims as possible is authenticity. If the web page the victims lands on seems legit, the user is more likely to browse around and click on things.
So attackers have made it their mission to create fake pages that look as real as possible. And with all the bad web design out there, it’s not even that difficult to blend in.
Cisco researchers suggest that the exploit kit’s authors may be relying on data science to
create computer-generated landing pages that resemble normal webpages and easily dupe users.
[…] Malvertising (malicious online advertising) is likely the key driver for a consistent stream of web traffic to these pages.
Source: Cisco 2015 Midyear Security Report
It’s known for being an effective malware infection vector.
While there are no definitive numbers to confirm this, word is that Angler has a very effective “conversion” rate.
This could be part of its success and a reason why so many attackers choose to use Angler in their campaigns. Of course, the others parts that contribute to this high usage are listed above.
As always, it’s a mix of elements that gets the job done. Unfortunately, this time it’s done at the detriment of Internet users around the world.
4. How does Angler spread?
Angler may be one of the most advanced exploit kits out there, but that’s not enough. In order for it to become the „most wanted”, it must be able to reach as many potential victims as possible.
So how do cyber criminals spread Angler to that Internet users like you and me get infected?
Attackers rely on 3 major tactics to reach as many PCs as they can:
- Malvertising
- Malicious iFrames
- Malicious code injection.
Malvertising is when cyber criminals use online advertising to distribute malware. They infiltrate content distribution networks that are in charge of deploying online advertisements on websites. The servers that work to do this are usually quite vulnerable, so it’s not a challenge for attackers to get in.
Once they’re in, they can infect all the banners in the network with malicious code, in this case, redirects that lead to Angler landing pages. So websites as big as The Huffington Post, Mashable or others could be endangering their visitors without knowing it.
By using malvertising, cyber criminals can reach huge numbers of Internet users at once. We’re talking millions!
And there’s another way that Angler can get into your system: iFrames. This is a way to insert content from another website on the website you’re visiting. So you could be reading an article on The New York Times and the page could host malicious content from another website. This type of malicious content will also redirect users to Angler exploit kit pages, where the infection will be triggered.
[Tweet “This guide about the Angler exploit kit explains this cyber threat so anyone can understand:”]Of course, there’s also the situation in which attackers choose to inject malicious code into various websites. This code will also feed traffic to the web pages creates to spread Angler and the consequent malware infections.
All these 3 tactics rely on leveraging the trust that visitors have in big websites. Cyber criminals also correlate this trust factor with the exploit kit’s ability to remain undetected while the infection takes place. It’s a dreadful combination that fools too many victims who are very often unaware that such dangers even exist.
5. Can antivirus protect me from Angler?
We’re sorry to say this, but no.
You may still think that antivirus protection is a solution for all your security problems, but it’s only a myth.
Traditional antivirus can’t provide 100% protection. No security solution can, that’s why you need multi-layered protection.
I’ve explained earlier why antivirus is mostly ineffective against the most advanced exploit kits. Their ability to avoid detection is uncanny.
That doesn’t mean you don’t need antivirus. In fact, it’s a basic security provision you have to make. But you need more than antivirus to keep your safe from Angler and similar exploit kits.
Here’s more proof:
One of the biggest reasons that Angler has been so pervasive and able to infect as many users is the lack of antivirus coverage. During the month of July Talos observed almost 3,000 unique hashes associated with exploits. That data was then queried against VirusTotal which found that only 6% of the hashes were in VirusTotal. Of that 6% the average detection was low, with usually less than ten AV engines detecting it.
Source: Cisco Talos, “Angler exposed”
6. Recent developments
Here’s a big recent improvement which shows that Angler is at the forefront of innovation in all exploit kit matters. At the beginning of December, our team at Heimdal Security spotted Angler distributing CryptoWall 4.0, the newest version of the infamous ransomware.
Angler creators integrated the CryptoWall 4.0 payload less than a month after we first spotted it. Given the complexity of both these elements, a month is really a short time to adoption.
It doesn’t stop here, of course. In early December 2015, we saw several new servers become part of the Angler distribution network. The “crime as a service” setup includes various compromised domains. Here is a selection that’s been sanitized by Heimdal Security:
carla campbell [.] co
evancampbell [.] me
upuff [.] us
aero station [.] us
idtsolutions [.] us
linnosnes [.] com
cherhawaii [.] com
hilodayspa [.] com
miracle-touch massage [.] com
evancampbell [.] co
ecupidonline.us
theflightdeck [.] us
bugado [.] com
stock real money [.] com
jerramconsulting [.] com
oldtruckpartsonline [.] com
Over 100 domains were blocked in our database in a single morning, because they were being exploited to deliver CryptoWall 4.0. On top of that, Angler was also used to tie the infected machines into a botnet, so they can use their resources to fuel new attacks.
Also in December 2015, we observed strong activity in the Angler exploit kit. In this case, two servers were used to deliver drive-by attacks via infected websites. Here are their details:
185.46.8 [.] 218
195.64.155 [.] 168
Again, a fresh batch of compromised domains was blocked to protect Heimdal users. You can see some of them below:
galactic parks [.] com
thatcrazycousin [.] com
americanoutlawelixirs [.] com
rocket [.] solar
galactic [.] Energy
rocket [.] voyage
bigsoya [.] com
nyratwo [.] com
hydronest [.] com
seabiofuels [.] com
alpvideophoto [.] com
rocket worldwide [.] com
galactic power [.] Energy
rocket [.] vacations
levoradikal [.] tk
elginjohn [.] com
seberevolta [.] com
ozonitewater [.] com
miamilawgroup [.] com
LATER EDIT [December 14, 2015]:
We detected new movement in the Angler exploit kit on Friday, December 11 2015, , on the servers used to plant CryptoWall 4.0 on outdated PCs running Windows.
This new campaign uses identical methods as the one we exposed on December 2nd, when we first identified Angler spreading CryptoWall 4.0. It also appears that the current campaign is also coordinated by the same group of cyber criminals, who are now targeting outdated versions of Adobe Flash and Adobe Reader or Acrobat Reader.
As it’s specific for the Angler exploit kit, the infection is delivered through compromised web pages that move the user to a series of domains created for this malicious purpose.
Here are the new servers which are used to spread CryptoWall 4.0 via Angler, which, as you can see, are spread in Russia, France and the US:
5101.67 [.] 101 (PIN DATACENTER-NET, Russia)
51254162 [.] 81 (OVH, France)
209133214 [.] 46 (Noc4hosts Inc., USA)
As mentioned before, our researchers observed that malicious traffic is directed from these servers by using a large number of domains whose sole purpose it to carry out the drive-by attacks. Here is a small sample of these domains:
happy keys house [.] com
youniquenatasha [.] com
lovingallthishair [.] com
millenniumsurfaces [.] com
Team doyle [.] net
urbansignsusa [.] net
youregonnaneedabiggerboat [.] net
Clergy-women [.] biz
direktologistics [.] com
abemc [.] net
aircontrols [.] net
clergywoman [.] info
Clergy-women [.] mobi
The infection process also involves using a heap of subdomains associated with the domains presented above. These represent the primary platform that Angler exploit kit uses to distribute CryptoWall 4.0 in drive-by attacks.
In spite of the campaign being over 2 days old, antivirus detection is still very low: only 7 out of 56 antivirus solutions listed in VirusTotal can currently identify and block the attack.
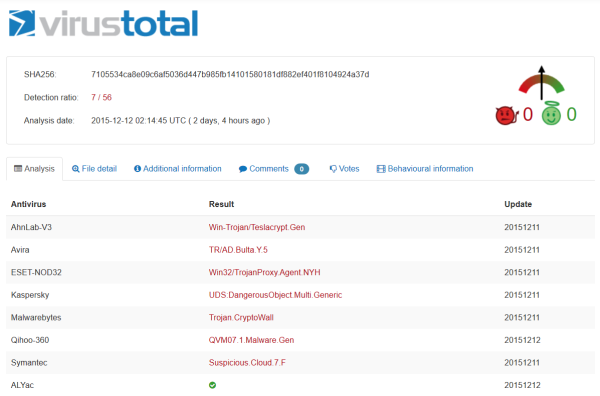
Please click here for the full list of detection rates at the time of the campaign.
Cisco’s Talos shared some figures extracted from their intelligence that show the impact that Angler has on its victims. This is especially because Angler is a favorite infection vector for ransomware. When coupled, the infection has almost sure-fire chances to succeed.
The victim is left with his/her data encrypted and a single way to get it back: to pay the ransom. Of course, should they have a backup, there’s no need to ponder on whether to pay or not to pay. But if there’s no back-up…
Source: Cisco Talos, “Angler exposed”
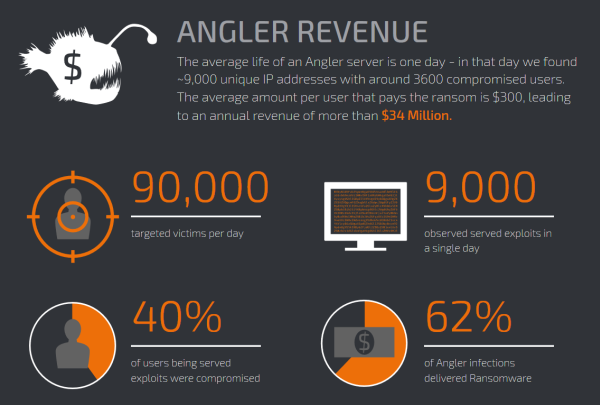
Of course, Angler distribution campaigns have a very low antivirus detection, so it’s no secret that you are most likely be exposed if you don’t follow some basic security rules.
7. How can I keep my system protected from Angler?
We’ve talked about how Angler can integrate the newest software vulnerabilities on the market. But they’re not the only ones that cyber criminals go after.
In fact, Angler can scan for and exploit security holes that have already been patched by software makers. If users don’t apply the updates, the vulnerabilities are still there. And we all know that many of us lag behind on this key security practice.
Exploit kit protection is a relatively simple setup. You don’t need technical knowledge to keep safe from Angler and the malware it distributes. Here’s a helpful checklist to help you get started:
Secure your browser
Many infections delivered by Angler exploit a vulnerability in the user’s browser. There are various ways they can compromise your system: through security holes in plugins, because you haven’t installed the latest version, etc.
But there’s a way to make sure that your browser is not exposing you to cyber attacks! Just follow the steps in the:
The Ultimate Guide to Secure your Online Browsing: Chrome, Firefox and Internet Explorer
Keep your software up to date
As you’ve seen, the most used apps in the world are also the most vulnerable, whether we’re talking about Flash or Chrome.
The trust is that it’s simple to close a lot of security holes in your system just by applying updates regularly. And the same goes for your operating system, of course.

Heimdal® Patch & Asset Management Software
- Schedule updates at your convenience;
- See any software assets in inventory;
- Global deployment and LAN P2P;
- And much more than we can fit in here...
Take a peek at these statistics to see for yourself why you should never ignore an update again:
8 Vulnerable Software Apps Exposing Your Computer to Cyber Attacks [Infographic]
Use antivirus
Antivirus may not be very effective against advanced exploit kits or ransomware attacks, but you still need it. It’s a basic line of defense and you should definitely use it.
If you’re lost among too many options, you can use the guide we put together to help you choose the best antivirus for your system.
What Is the Best Antivirus for My PC? A Step-By-Step Research Guide
Protect your system from ransomware with the right tools
So if antivirus can’t protect me from Angler or ransomware, what can?
There are tools that have the ability to block Angler or ransomware such as CryptoWall from reaching your system. They act proactively and scan your Internet traffic to block access to potentially dangerous websites.
You can read more about these tools in this handy list we created exactly for this purpose:
Is Antivirus Dead? Meet The NextGen Anti-Hacking Tools
Back up your data
Backing up data is not sexy. Most people find it boring and time-consuming and they don’t really see the benefit. But we can’t stress enough how important this is.
Having a backup of your data can get you out of trouble at any moment!
If your computer becomes infected with ransomware, you don’t have to pay the ransom. If you have to do a system erase to remove an infection, you don’t have to lose your files. If anything happens, you’ll still have access to your important documents, pictures and other media.
Keep in mind that a cloud based backup is not enough though. Some types of ransomware can encrypt the data on your Google Drive if it’s synced on the infected computer.
So back up your data NOW and then do it often.
Don’t know where to start?
We have just the thing:
How to backup your computer – the best advice in one place
But remember: all of these guides only work if you apply them. If you do it once, you’ll have your own online security setup you can improve and modify to your liking.
[Tweet “Just found out how to protect my data/PC from Angler exploit kit. Simpler than expected:”]
8. Technical analysis: take a closer look at the Angler exploit kit
For those who have a bit appetite for more Angler-related insights, we rounded up some of the technical analyses that show how this particular exploit kits works.
- Sophos: “A closer look at the Angler exploit kit”
- IXIA: “Angler Exploit Kit Deobfuscation and Analysis”
- SANS Edu: “Angler exploit kit pushes new variant of ransomware”
- Websense Security Labs Blog: “Angler Exploit Kit – Operating at the Cutting Edge”
- Trend Micro: “Evolution of Exploit Kits”
- Cisco blog: “Threat Spotlight: Angler Lurking in the Domain Shadows”
- Cisco Talos: “Angler exposed.”
Conclusion
I hope that now you have a better understanding of what Angler and other exploit kits can do. It’s a big challenge to keep up with online security and I know that from my own experience. But it’s also very important.
The Internet does offer some exceptional opportunities to learn, work and grow as a person. But the “package” also includes some threats that are sometimes difficult to understand.
So I hope that I achieved part of my mission here today, which is to help you see things more clearly and really get why online security should be on your to-do list. The list is long; I have a stack of them too. But I can’t afford my work and passions to be disrupted by cyber criminals.
Do you?











 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security