Contents:
You chose to install Windows operating system on your computer or, maybe, for various technical reasons, you had to reinstall it. No matter your reasons, it’s important to keep in mind various security layers after this procedure, so your computer is safe from threats.
How to secure your PC after a fresh Windows installation
After finishing the Windows installation, whether it’s Windows 7, 10 or another operating system, we encourage you to follow these security measures below to enhance protection:
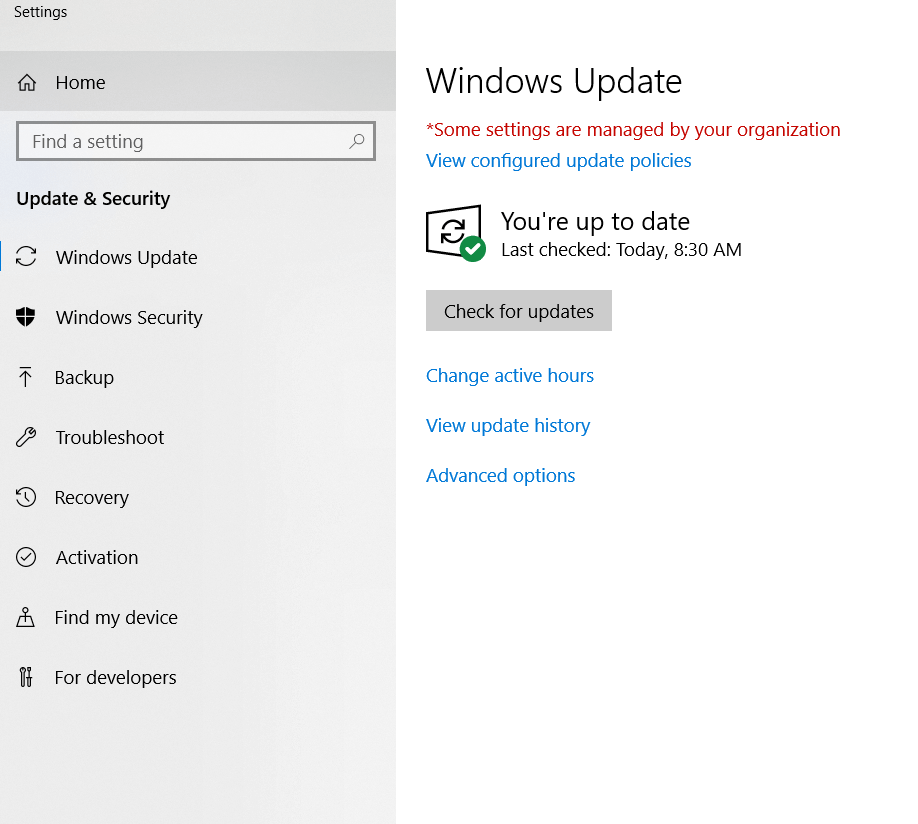
1. Keep your Windows operating system up to date
Probably the most important step to do is checking for the latest security updates and patches available for your Windows operating system.
To get the security updates automatically, go to “Control Panel” and check if your automatic updating system is enabled or follow these steps:
- Access the search box in your Windows operating system, type Windows Update.
- Select Advanced options.
- Click on Automatically download updates in case it is not already selected/turned on.
After checking for available updates for your Windows operating system, keep the automatic update turned on in order to download and install the important updates that can help protect your PC against new viruses or next-generation malware.
Always remember to keep your OS up to date with the latest security available. Software patching remains an essential key to improve online safety and security experts make a good case of emphasizing its importance. Cybercriminals still try to benefit from security holes found in users’ systems and PCs. That’s one of the reasons why cyber attacks still work and they make a lot of money of it.
 2. Update your software
2. Update your software
You don’t have to update only the Windows operating system, but your software as well. Therefore, make sure all the latest updates and security patches for your main programs and apps are installed.
Needless to say that most popular pieces of software (such as Java, Adobe Flash, Adobe Shockwave, Adobe Acrobat Reader), especially the outdated ones, are always under threat from malicious actors who exploit them to get easier access to your sensitive data.
Since these pieces of software are always under threat from criminal minds, don’t just rely on your memory to manually update every program or application you have installed.
A better option would be to start using a dedicated cybersecurity solution for you and keep your software program up to date.
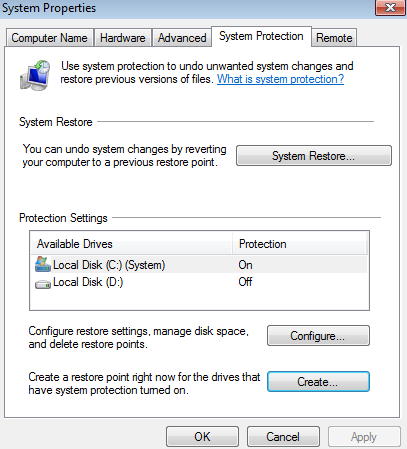
3. Create a restore point
If you already installed the security updates for Windows OS, the next step recommended is to create a restore point in Windows.
You can do this by clicking on the Start button, then select Control Panel -> System and Maintenance (or System and Security) -> System. Then select System protection and click the Create button.
After installing Windows, you can create the Restore Point and name it Clean installation, and continue installing drivers and applications.
If one of the drivers causes issues on the system, you can always go back to the Clean installation restore point.
4. Install a traditional antivirus product
When you consider installing an antivirus program on your PC, make sure you use one from a legitimate company, because there can be fake software programs out there. It is important to have a reliable security solution on your system, which should include real-time scanning, automatic update, and a firewall.
To find the best antivirus that suits your needs, read this ultimate guide that will teach you more about antiviruses, its main features and what should you look for.
If you choose to install a security product that doesn’t have a firewall, make sure you have turned on the Windows firewall.
To turn it on, go to Control Panel, select System and Security, then Windows Defender Firewall and turn it on or off.
[Tweet “Super useful guide on how to secure your PC after a fresh Windows installation:”]5. Install a proactive security solution for multi-layered protection
On our blog, we explained on many occasions why traditional antivirus is no longer the go-to solution, simply because it cannot keep up with the rise of new and advanced online threats. Financial malware especially is created to steal sensitive data and confidential information and it uses sophisticated methods to do so.
Next-gen malware usually has the ability to evade detection and bypass antivirus software that users have installed on their PCs to keep their data safe. We recommend reading these 12 examples of spam campaigns behind the scenes indicating a low detection rate for AV engines during the first stages of a cyber attack.
With the help of a proactive cybersecurity solution, you get the best protection against financial and data-stealing malware, such as Zeus or Cryptolocker.
To improve the financial control of your online banking account, you can always set banking alerts to track your account activity and apply these simple and effective financial protection tips.
6. Back up your system
You updated the operating system and your system applications, you have installed additional security products for your system safe and even created a Clean installation restore point for your Windows.
The steps above are meant to keep you safe from malicious software and online threats, but you may still encounter hardware issues that could endanger your private information.
To make sure your data stays safe, you should be using a twofold strategy, which should include combining external hard drive usage with an online backup service.
We need to emphasize the importance of having a backup solution that provides stability (look for a big company name), it’s easy to use (so you won’t have a headache backing up from files), allows you to synchronize your files with the online backup servers and provides some sort of security, such as encryption capabilities.
Our guide on how to do a data backup includes more information on the most popular backup solutions available and what the best ways to keep your data safe are.
At the same time, you could simply use your Windows Backup system. To set it up, access your Windows Control Panel and then click Backup and Restore to access the location. From this place, you can set an automatic backup, create a schedule and even choose a network location for your backup files.
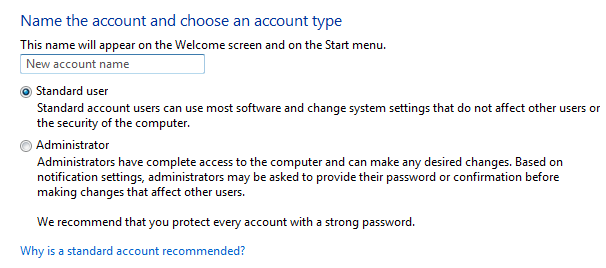
7. Use a standard user account
Windows provides a certain level of rights and privileges depending on what kind of user account you have. You may use a standard user account or an administrator user account.
To secure your PC, it is recommended to have a standard account to prevent users from making changes that affect everyone who uses the computer, such as deleting important Windows files necessary for the system.
With a Standard user account, you have limited rights and cannot do things like changing system settings, or installing new software apps, hardware or changing the username and passwords. Here’s why you should use an account like this one and how to create it.
If you want to install an application or make security changes, remember that you will need an administrator account.
We also recommend that you set a strong password for your Windows user account.
Use this security guide that will help you set unique and strong passwords and manage them like an expert.
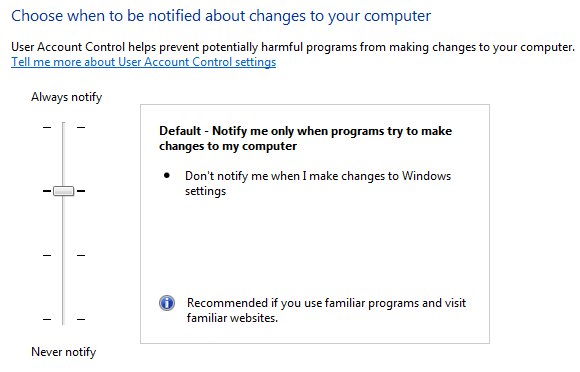
8. Keep your User Account Control enabled
User Account Control (UAC) is an essential security feature of Windows that prevents unauthorized changes to the operating system. Many users have the tendency to disable it after installing/reinstalling the Windows operating system.
We don’t recommend to turn it off. Instead of disabling the UAC, you can decrease the intensity level using a slider in the Control Panel.
UAC monitors what changes are going to be made to your computer. When important changes appear, such as installing a program or removing an application, the UAC pops up asking for an administrator-level permission.
In case your user account is infected with malware, UAC helps you by keeping suspicious programs and activities from making changes to the system.
9. Secure your web browser before going online
Here’s another thing to do after installing Windows: pay attention to browser security. Since our web browser is the main tool used to access the Internet, it is important to keep it safe before going online.
The vulnerabilities in your web browser are like open door invitations to cybercriminals who find creative ways to harvest your most important data. For example, if you are using Adobe Flash, be aware of its security flaws and how it can expose you to attacks.
To stay safe while accessing various web pages, follow these steps:
- Choose the latest version for your browser.
- Keep it updated.
- Choose a private browsing session when you access a website you are not sure about. Choosing this mode will prevent authentication credentials (or cookies) from being stored and steal by attackers.
- Since data-stealing malware spreads through malicious code embedded in pop-up windows even in legitimate websites, make sure your web browser can block pop-ups:
And there’s, even more, you can do. Use these step-by-step instructions to enjoy the best secure browsing.
[Tweet “On my next Windows install, I’ll follow these security tips to improve my data safety:”]10. Use an encryption software tool for your hard drive
Even if you set a password to your Windows account, malicious actors can still get unauthorized access to your private files and documents. They can do this by simply booting into their own operating system – Linux, for example – from a special disc or USB flash drive.
A solution for this case is to encrypt your hard drive and protect all your sensitive files. It is recommended to use this level of security if you have a laptop, which can be very easily stolen. The same thing applies to a computer.
A free encryption tool you can use is BitLocker, which is available on the latest Windows operating systems and you can enable it at any moment. Even after you have enabled the BitLocker protection, you won’t notice any difference because you don’t have to insert anything else but your normal Windows user account password. The benefits of using this encryption tool:
- It encrypts your entire drive, which makes it impossible for malicious actors stealing your laptop to remove the hard drive and read your files.
- It’s also a great encryption software if it happens to lose your PC/laptop or get it stolen.
- Easy to use and already integrated into your Windows OS, so there’s no need to add another encryption software.
If you’d rather want to use another solution, here’s a full list of encryption software tools you can choose to protect your data.
11. Be careful online and don’t click on suspicious links
To make sure you won’t be infected by clicking on dangerous links, hover the mouse over the link to see if you are directed to a legitimate location. If you were supposed to reach your favorite news website, such as “www.cnn.com”, but the link indicates “hfieo88.net“, then you probably shouldn’t access it. Chances are you’ll be infected with malware and cybercriminals steal your sensitive data.
It’s worth trying shortening services, such as goo.gl or tinyurl. But in some cases, an unknown link may send you to a malicious site that can install malware on the system.
So, how can you know where you’ll arrive if you click it?
To make sure you are going to the right direction, use a free tool such as Redirect Detective that will allow you to see the complete path of a redirected link. Another tool which can provide very helpful in checking suspicious links is the reliable URL checker, VirusTotal.
For more information on how to maximize your financial data protection, check out this article.
Conclusion
It’s not just about staying safe.
This guide above is meant to keep you safe online. But, at the same time, following these security measures mean that you also set up your system to work smoothly for online browsing and financial operations, activities you do every day.
Since there are many other solutions to protect a system after a Windows installation, we would like to know your opinion on this.
How do you increase your security after a Windows installation?
Do you have a particular routine? We’d love to add your tips to the list, so share them in the comments below.

INSTALL IT, FORGET IT AND BE PROTECTED
Download Heimdal™ FREE

 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security