Contents:
In June 2014, Operation Tovar, run by the U.S. Justice Department in collaboration with the FBI, Europol and some important names in the private sector, like Heimdal, Symantec, Trend Micro and McAfee, took down a large network controlled by hackers in Russia and Ukraine. They were using the Gameover platform to spread and infect systems with CryptoLocker, a dangerous piece of ransomware that encrypts your files and asks a sum of money in exchange for the decryption key.
What is CTB Locker?
CTB Locker is one of the developments of CryptoLocker, the ransomware trojan that spreads mainly through spam and e-mail attachments.
The name of the ransomware, CTB, comes from its main advantages: Curve-Tor-Bitcoin.
- Curve comes from its persistent cryptography based on elliptic curves, which encrypts the affected files with a unique RSA key;
- Tor comes from the malicious server placed in onion-domain (TOR), which is very difficult to take down;
- Bitcoin refers to the possibility to pay in Bitcoins, avoiding normal payment systems that can lead back to online criminals;
Crime as a Service
First, we need to establish the fact that we are dealing with a type of malware specifically developed to be used by online criminals that don’t have (nor need) a very strong technical background.
For this reason, we find a malware with a well-made infrastructure, easy to use and deploy by even less knowledgeable people. This means that for an amount of money, even You can enter this Crime as a Service network quite easily!
Since we are dealing with an advanced and well prepared network of malware, which is able to provide such a stable “service“, we have to point out to the additional benefits one has from joining such a network of e-crime.
The following information has been obtained by our security analysts, after they gained access to multiple malware forums from Russia and Ukraine.
By purchasing this dangerous ransomware, one also gains access to the following included services:
- How to install the bitcoin payment for the server
- How to edit the Locker options, such as the requested price and the language displayed
- You even receive recommendations for the unlock price
How does CTB Locker spread?
CTB Locker is delivered through aggressive spam campaigns. The email message pretends to be related to a FAX message that needs your immediate attention. When the email is accessed, the potential victim is asked to download and access an attached zip file.
If the zip file is accessed, the data on the system is encrypted and the victim asked for a ransom in order to receive the decryption key.
The email content is similar to this:
From: Spoofed / falsified content
Subject:
Fax from RAMP Industries Ltd
Incoming fax, NB-112420319-8448
New incoming fax message from +07829 062999
[Fax server]= +07955-168045
[Fax server]: [Random ID]
Content:
No.: +07434 20 65 74
Date: 2015/01/18 14:56:54 CST
Pages: 5
ID: [Random ID]
File name: [name of attached zip file]
Our malware analysts discovered the following e-mail subjects:
disgruntled.zip
facto.zip
headband.zip
woodworking.zip
firefly.zip
More information on this new generation of ransomware and how to remove it can be found in this article.
UPDATE 04.02.2015: The notorious CTB Locker ransomware is back. A new big email spam campaign is spreading. As you can see in the image, the spam email has an infected zip archive attached.
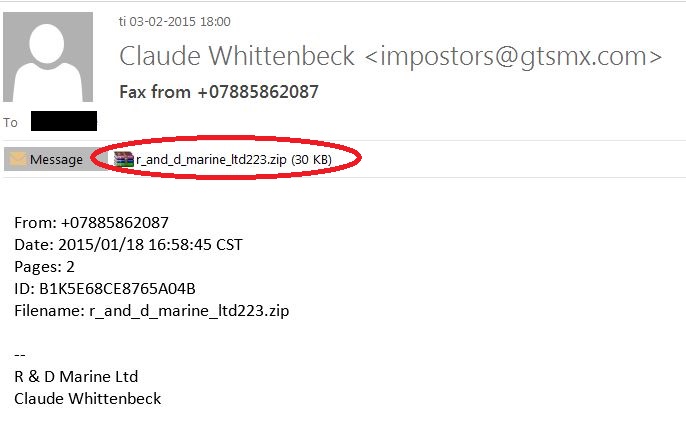
UPDATE 06.02.2015: One of our closest partners, Comendo, a cloud security company, found a clear pattern in this spread mechanism. On the 19th of January:
- – the number of daily blocked botnets was 9.5 times higher than in a regular day, from 2 million to 19 million.
- – the number of filtered spam emails increased 3.5 times, from 700.000 to 2.5 million.
- – an interesting fact is also that the spam emails are reaching the Inbox while the user is actively using the PC.
Furthermore, the number of infected email attachments that were spreading CTB Locker was increasing day by day.
Taking into consideration that this data is referring only to Comendo Danish customers, we can only imagine the huge worldwide impact of this nasty malware.
UPDATE 16.04.2015: Our malware specialists detected a new spam campaign that spreads CTB Locker.
The emails arrive with a semi-dynamic content and the malicious attachments contain a dropper that brings CTB Locker on the system.
If the attachment, which is a cab-file, is unpacked, it offers a .scr file. If activated, it will deliver a dropper of the Dalexis class. This connects to a series of hard-coded URLs, from which it downloads CTB Locker.
The following subject lines were used in this new aggressive campaign:
Message from Drallim Industries Ltd
Message from Dynamic Packaging Ltd
Message from George McIvor Ltd
Message from Harrisonfield Ltd
Message from Piller (UK) Ltd
Message Z16T_571EE9433
[Altran Praxis] Fax2mail +07745 091622
[Blake Emergency Services]
6 pages from +07405-894130 Copy from +07717 60 37 48
[Corus Process Engineering] New fax message WQ-64693855D-3988
Eastman Packaging internet
fax=PCL.7038CAAC.8023
Email to fax-AN-FD6B947E4-7826
Email to fax: T34E1995C959788
Fax2mail: +07416 74 19 36
Fax2mail – L9EE0496C4165
Fax2mail=QI-84B353879-6910
Fax from Tactiq Ltd
Fax message from +07754-267-965
Fax message YJF.435371D6B.5958
And the following attachments:
swindens_patents_ltd.cab
tactiq_ltd.cab
telonic_instruments_ltd.cab
tritec_developments_ltd.cab
union_industries.cab
varivane_industries_ltd.cab
william_hughes_ltd.cab
UPDATE 30.06.2015: On June 30, Heimdal Security sends out a security alert to its users about a new spam run which carries a payload that releases CTB Locker.
The unsolicited e-mail arrives with the following contents:
From: [spoofed / fake return address]
Subject Line: Monthly discounts
Attached:
e-gift.doc
That document contains macros that execute VBA code. The VBA code is designed to download the CTB Locker ransomware from a predefined web page, which has already blocked in the Heimdal Secure DNS.
The malicious download URL looks like the following (sanitized by Heimdal Security)
http://gets-adobe [.] com / fid / ZmlsZToxMTA4NzQzLy8 / acez.exe (MD5: ba372961ca89f1de9521b8f5dd864f0c).
Antivirus detection gives CTB locker 29/56 on this date.
The main component is downloaded as “acez.exe” and drops itself instantly:
C: \ DOCUME ~ 1 \ [% user account%] \ LOCALS ~ 1 \ Temp \ wkqifwe.exe
C: \ WINDOWS \ system32 \ vssadmin.exe
C: \ WINDOWS \ Tasks \ cderkbm.job
The last of a total of three files copied by CTB Locker in the victim’s system creates a job under Microsoft Windows, which initiates encryption of local files and files available via shared tracks / folders. It adds “! Decrypt-All-Files-” for encrypted files containing instructions on how data can be retrieved by paying a ransom via Bitcoins.
The code calls back to the CTB Locker gateway. The communication runs via TOR.
How does CTB Locker ransomware work?
We will present below, without entering into too much technical information, the main steps that take place in the infection phase:
- As we said above, the infection starts with an e-mail received by the victim and with an attached ZIP file.
- When the ZIP file is accessed, a downloader is placed on the system.
- The downloader uses a list to connect to a number of domains controlled by hackers, from where it can download the CTB Locker.
- One of the compromised domains sends back and installs CTB Locker on the system.
- The ransomware encrypts the system data with “Elliptical Curve Encryption”.
- A warning is presented on the screen with instructions on how to pay for the decryption key by using the bitcoin system.
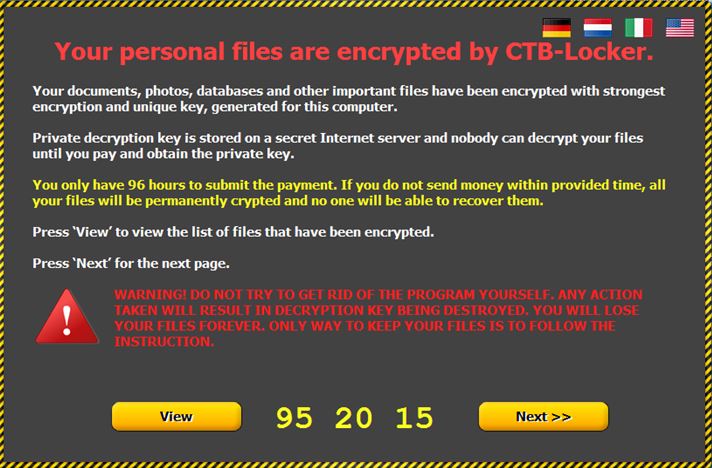
UPDATE 04.02.2015: The malware was deployed through a binary code, which is executed if you open the email spam archive. Further on, when running CTB Locker, it immediately and automatically downloads its harmful main component from multiple domains. And all it’s done through a https:// secure connection.
Usually, the download has the “[% filename%]. Tar.gz” format.
Antivirus detection at the time of this update, was very low. Only 5 from 54 security vendors were detecting the malicious payload. As you can see in this Virus Total report, even now there’s only 46 from 57 security vendors detecting the malicious payload.
How can I keep my system protected from CTB Locker?
Our malware researchers recommend the following security measures to keep your computer safe from CTB Locker:
- Don’t download or access e-mail attachments from people you don’t know. This is the main spreading method for CTB Locker.
- Don’t click links in e-mails you receive from unknown e-mail addresses.
- Create a Backup for your operating system or for your most important data. Make sure the backup is not placed in the same location with your actual operating system. In case your system is affected by malware or ransomware, you will not be able to access the backup.
- Make sure your security solution detects and blocks CTB Locker. At this moment, Heimdal Security is one of the few software solutions that detect this ransomware.
- Increase your online protection level by adjusting your web browser security settings.
- Keep your Windows operating system and your vulnerable software up-to-date with the latest security patches.
We have found a useful security article on CTB Locker, where you can find an extensive presentation of this dangerous ransomware and what steps are available to you. Among the most important elements from the article, we noticed the importance of having a backup for your system or for your valuable information, the fact that it is quite easy to recover files that are in Dropbox, even if your Dropbox folder has been encrypted, and a CryptoPrevent tool, which is a free software that can prevent CTB Locker from being executed on the system.
How does Heimdal Security keep me safe?
First of all, make sure you don’t open e-mails from unknown sources and more than anything, you don’t click any link or access any attachment in the e-mail.
Second, even if the e-mail zip file is accessed and the downloader tries to communicate with the Command & Control servers through TOR, Heimdal blocks the malicious code from being sent to the system. Heimdal manages this blocking operation by blacklisting the hacker controlled domain and preventing CTB Locker from downloading on the system.
Luckily, Heimdal™ Threat Prevention blocks those domains which act as download servers. Here are some of the malicious domains:
- sho p-oye.it
- asp iroflash.fr
- die ideenwerkstatt.at
- WSB .cba.pl
- asp iroflash.fr
- sintjoep .nl
- scottwall .com
- stocksandstares .co.uk
On top of that, Heimdal Security is offering an outstanding integrated cybersecurity suite including the Ransomware Encryption Protection module, that is 100% signature-free, ensuring superior detection and remediation of any type of ransomware, whether fileless or file-based.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Conclusion
The ransomware evolution from last years created a lot of concern in the online world and CTB Locker, together with other similar types of ransomware, are more troublesome than any other types of malicious software in the wild.
This concern is connected not only to the financial demands that are implied in the entire process, but mostly to the fact that the encrypted information may be lost forever.
No one can say for sure in such a case what someone should do: pay or not pay?
And the most important question of all, even if you pay, are they really going to give you access back to your most valuable information?


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










