Contents:
Clop Ransomware, belonging to the popular Cryptomix family, is a dangerous file-encrypting malware. It actively targets systems with inadequate security, encrypting files and appending the ‘.Clop’ extension to them.
The ‘Clop virus’ name comes from the Russian word ‘klop,’ which means ‘bed bug.’ This bug, from the Cimex family, feeds on human blood at night.
This article will cover everything you need to know about Clop ransomware, including:
- What Is Clop Ransomware?
- Clop Ransomware Operating Mode
- How Can this Type of Ransomware Threat Infect Your Computer?
- Technical Analysis
- How to Stay Protected
More on the Clop Ransomware Gang
The cybercrime group usually conducts ransomware attacks by targeting organizations worldwide, not regular users. This is because the Clop operators focus on the big prize: the financial aspect. The attackers behind Clop have stolen and encrypted important files from huge companies. This includes data backups, financial records, thousands of emails, and more.
The malicious actors behind Clop target organizations in many industries, such as multinational oil companies, retail, education, telecommunications, and healthcare. The group shows a particular interest in businesses with revenues over $5 million.
Reports suggest that, to date, Clop has extorted over $500 million in ransom payments from businesses.
Both our article ‘Most Dangerous Ransomware Gangs You Should Know About‘ and CyberTalk’s recent article on the same topic identify this ransomware strain as among the most dangerous and active ransomware gangs.
Operating Mode
This ransomware strain, regarded as highly dangerous, can compromise various Windows operating system versions, from XP to Windows 10, leading to grave consequences.
Clop malware exploits AES cipher to encrypt pictures, videos, music, databases documents, and attach the ‘.CLOP’ or ‘.CIOP’ file extension, which prevents victims from accessing their data. For example, ‘sample.jpg’ is renamed to ‘sample.jpg.Clop’.
This method pressures victims to pay the ransom before a deadline, hoping to recover their sensitive data or files.
Specialists do not recommend the victims affected by ransomware attacks pay the threat actors, no matter what the cost is. Researches reveal that after ransomware hackers receive their payment, they ignore the victims. This leaves no chance to get the encrypted data back.
Make sure to watch our video to learn the 6 reasons businesses should not pay ransomware demands.
Recently, the Clop hacker group has been associated with malicious actors who have been using Accellion File Transfer Appliance (FTA) vulnerabilities: CVE-2021-27101, CVE-2021-27102, CVE-2021-27103, and CVE-2021-27104. These flaws were exploited starting in February, leading to attacks on major organizations. There’s also proof that an affiliate used a webshell called DEWMODE to steal data from Accellion FTA devices.
Several companies decided not to pay the ransom. As a result, the attackers posted their stolen data on the ‘CL0P^_- LEAKS’ data leak site on the dark web.
Clop ransomware is designed to change its targets’ predefined browser settings and has features that activate its encryption tool. It then perverts all important files on their computer, rendering them useless.
When victims try to open a damaged file, they see a ransom note. This note tells them their files are encrypted and explains how to pay the ransom, often in Bitcoin or another cryptocurrency. A unique characteristic of a Clop ransomware attack is the phrase ‘Don’t Worry C|0P’ present in its ransom notes.
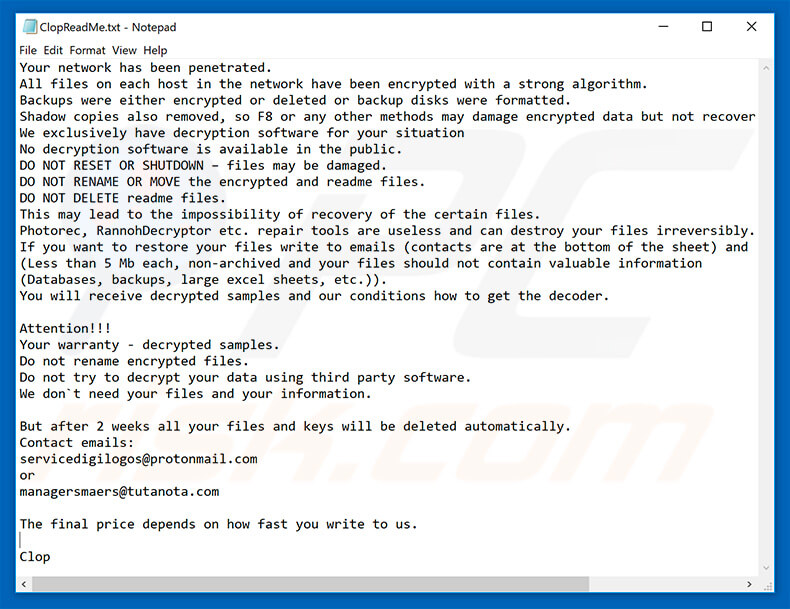
Message encouraging Clop ransomware victims to pay a ransom to decrypt their compromised data
A preventive measure for a ransomware attack is to be a step ahead and invest in backup systems. Always back up your sensitive data and save it to separate locations, like the Cloud, or on devices you can unplug, such as flash drives or external hard drives.
How Can this Type of Ransomware Threat Infect Your Device?
This ransomware strain can get into your system through several methods. These include spam email attachments, trojans, hyperlinks, software cracks, unprotected Remote Desktop Protocol (RDP) connections, and infected websites. Destructive viruses can get into your computer from junk email attachments and download links in the email body. These emails often pretend to be from familiar institutions, like banks or insurance companies.
Pornographic websites are also a major cause of these ransomware infections.
Once injected into the system, a fake certificate issued to the executable grants the Clop virus elevated privileges and initiates the clearnetworkdns_11-22-33.bat file.
This permits malware to overwrite and change system files. It also reads multiple technical details such as computer names and sends them off to threat actors. Also, Clop ransomware creates the \Users\CIiHmnxMn6Ps folder where more malicious files are created.
The ransomware then examines the computer for files to encrypt. In the process, regularly used files such as .jpg, .mp3, .doc, .mkv, etc are targeted. Following the encryption, a file like picture.jpg is transformed into picture.jpg.Clop, and becomes impossible to access.
It is important to know the data is not corrupted, it’s only encrypted by a key that only hackers have access to. The victims need to remove the the virus before trying to recover their files, or else, they will get locked over and over again.
Technical Analysis of Clop Ransomware
The technical analysis section is based on the Clop ransomware retrieved from Malware Bazaar’s repository on the 3rd of August 2023. The sample was last updated on the 6th of June 2023.
Behavioral analysis (via Cape Sandbox)
- Collects and encrypts information about the computer likely to be sent to the C2 server.
- SetUnhandledExceptionFilter detected (possible anti-debug)
- Uses Windows APIs to generate a cryptographic key
- Anomalous file deletion behavior detected (10+)
- Dynamic (imported) function loading detected
- Enumerates running processes
- Expresses interest in specific running processes
- Repeatedly searches for a not-found process, may want to run with startbrowser=1 option
- Manipulates data from or to the Recycle Bin
- Exhibits possible ransomware or wiper file modification behavior: mass_file_deletion overwrites_existing_files
- Creates known CryptoMix ransomware mutexes
- Yara rule detections observed from a process memory dump/dropped files/CAPE.
Post-delivery behavior (via Hatching Triage)
- Suspicious behavior: EnumeratesProcesses
- Drops file in Program Files directory
- Drops file in Windows directory
- Drops desktop.ini file(s)
- Enumerates connected drives
- Modifies extensions of user files
- Clop.
MITRE Mapping
| Defense Evasion | Privilege Escalation | Discovery | Impact |
|---|---|---|---|
| • Process injection • Software packing. • Rundll32. • Obfuscated Files or information. | • Process injection. | • File and directory discovery. • Software discovery. | • OS exhaustion flood. |
How To Stay Protected against Clop Ransomware Attacks
Caution is always essential when it comes to your computer safety. Be careful when browsing the internet, especially when downloading, installing, or updating software.
- Check twice before you open email attachments or click on links. You should not open a file if it does not concern you or if the email address looks suspicious.
- You should also only download apps from official sources, using direct download links. Third-party downloaders usually spawn malicious apps, and thus you should avoid them.
- Always update your apps and systems. Make sure to use only the official tools the developer provides for updates.
- Using pirated software is illegal and risky, leading to malware infections. Software cracking tools used to pirate software often spread malware.
- Invest in a good anti-virus or anti-spyware program. These tools can detect and remove malware before it causes any damage.
How Can Heimdal® Help?
In the fight against ransomware, Heimdal is offering its customers an outstanding integrated cybersecurity suite including the Ransomware Encryption Protection module, that is universally compatible with any antivirus solution, and is 100% signature-free, ensuring superior detection and remediation of any type of ransomware, whether fileless or file-based (including the most recent ones like LockFile).
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.
Try it now and avoid being one more of the victims on the list!

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Wrapping up
Nowadays, malicious actors have discovered how to make their malware more flexible, strong, and harmful than ever before. One of these viruses is Clop ransomware, an invasive ransomware family that has affected organizations worldwide.
The following quote tells us just how destructive this ransomware strain can be:
The most noteworthy ransomware incident in 2023 was the barrage of organizations that became victims to the MoveIt Transfer attacks from the Clop ransomware group. Among the many victims of the MoveIt flaw were multiple U.S. government agencies, the BBC, British Airways (BA), HR software provider Zellis, and the government of the Canadian province of Nova Scotia. In August 2023, some analysts had estimated that the Moveit transfer attack was responsible for more than 600 breaches.
You need to take action and upgrade your cyber defense structures and pay attention when browsing the internet and downloading, installing, and updating software.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










