Contents:
NCC Group security experts said that the Clop ransomware gang has returned following the shutting down of their entire operation for four months between November and February.
CL0P had an explosive and unexpected return to the forefront of the ransomware threat landscape, jumping from the least active threat actor in March to the fourth most active in April.
More on Clop Ransomware
Clop Ransomware belonging to a popular Cryptomix ransomware family is a dangerous file-encrypting virus that actively avoids security systems and encrypts the saved files by planting the .Clop extension. It exploits AES cipher to encrypt pictures, videos, music, databases papers, and attach.CLOP or .CIOP file extension, which prevents victims from accessing personal data. For example, “sample.jpg” is renamed to “sample.jpg.Clop”. This way, the victims are compelled to pay the ransom within a certain time frame in exchange for the alleged recovery of their data.
Clop ransomware is one of the worst computer threats that makes entries in the Windows Registry to attain durability and could start or restrain processes in a Windows domain to stay hidden from the usual antivirus program and computer user.
Impacted Sectors
This increase in activity was observed after the ransomware organization added 21 new victims to their data leak website in just one month, in April.
There were notable fluctuations in threat actor targeting in April. While Lockbit 2.0 (103 victims) and Conti (45 victims) remain the most prolific threat actors, victims of CL0P increased massively, from 1 to 21.
The most affected sector when it comes to Clop ransomware attacks was the industrial sector, with 45% of incidents impacting industrial entities and 27% tech organizations.
As a result, NCC Group’s strategic threat intelligence global lead Matt Hull alerted companies in the ransomware gang’s most targeted industries to take the necessary steps in the event they might become the threat actor’s next victim.
Even if the ransomware group has already made public data belonging to over 20 victims, the number of submissions on the ID Ransomware service indicates that the threat actor is not very active.
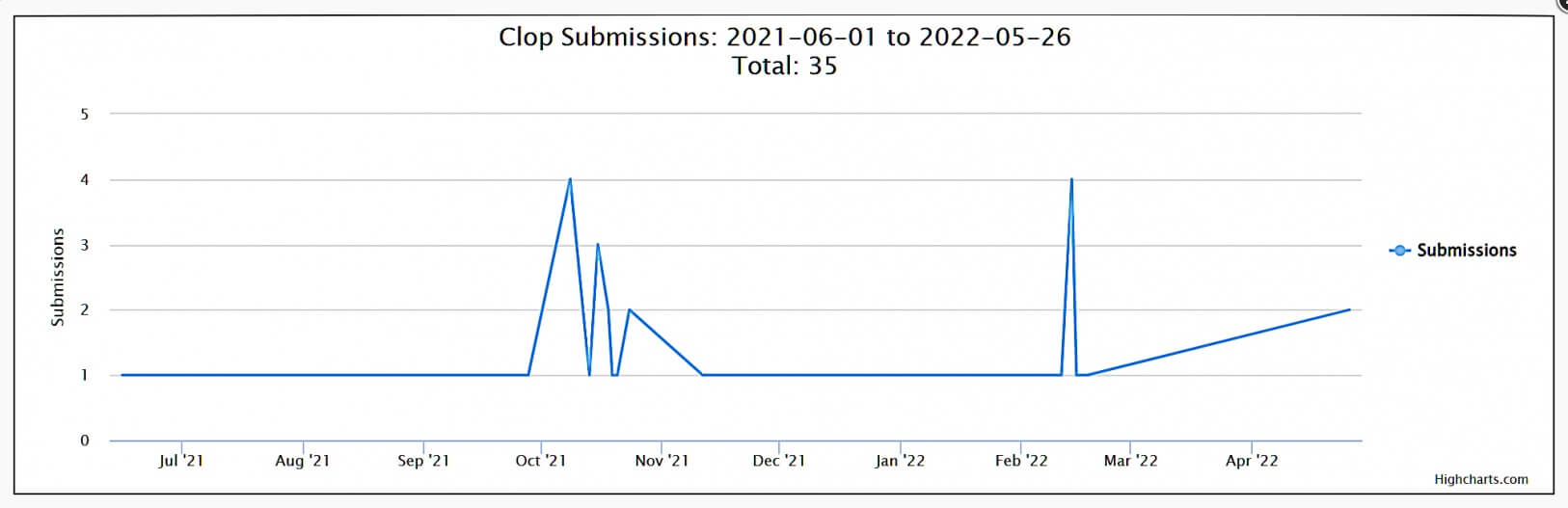
A Possible Explanation
While some of the recent targets have been confirmed to be new attacks, BleepingComputer believes that the Clop group may be finally closing down its activity after such long inactivity. As part of this process, the threat actor would probably leak the data belonging to all previously unpublished victims.
This is similar to what the infamous ransomware gang known as the Conti group seems to be doing right now. The gang has effectively ended its activity by destroying its infrastructure and notifying its team leaders that the brand no longer exists.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










