Contents:
The notorious Clop Ransomware gang has been looking for ways to exploit a now-patched zero-day in the MOVEit Transfer managed file transfer (MFT) solution since 2021, as reported by security researchers.
During the examination of recent Clop data theft attacks targeting weak MOVEit Transfer instances, they uncovered malicious behavior matching the technique used by the gang to deploy the recently disclosed LemurLoot web shell. They did this by studying logs on some clients’ affected networks.
Details About Clop’s MOVEit Exploitation
Activity during the May 27–28 period appeared to be an automated exploitation attack chain that ultimately resulted in the deployment of the human2.aspx web shell. The exploit centered around interaction between two legitimate components of MOVEit Transfer: moveitisapi/moveitisapi.dll and guestaccess.aspx,
Kroll Security Experts (Source)
The security researchers’ review of Microsoft Internet Information Services (IIS) logs of impacted clients found similar activity occurring in multiple client environments in April 2022, and in some cases as early as July 2021.
They also found evidence of threat actors trying, possibly with the aid of automated tools, methods of gathering and extracting sensitive data from compromised MOVEit Transfer servers as long back as April 2022.
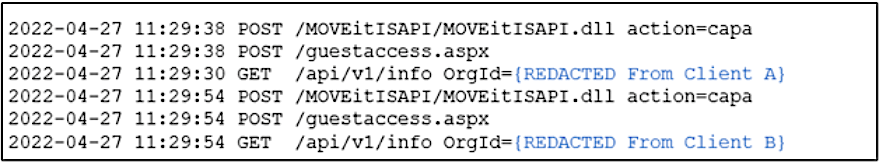
Clop Collecting Information From Victims (Source)
The activity consistent with MOVEit Transfer exploitation collectively occurred on April 27, 2022; May 15 and 16, 2022, and May 22, 2023. The research demonstrates that actors were retrieving data from the MOVEit Transfer servers to determine which organization they were visiting and testing access to organizations through probably automated ways.
Right before the start of the broad zero-day flaw exploitation on May 27, 2023, the automated malicious activity accelerated and became much more widespread starting on May 15.
The ransomware gang waited until it had the resources to launch the ultimate attack in late May 2023 since this command matched similar ones that were manually issued against MOVEit Transfer servers in July 2021.
Hundreds of Companies Breached as a Result
BleepingComputer managed to contact the ransomware gang over the weekend, and Clop confirmed that they were actually behind recent data-theft attacks that allowed them to breach MOVEit Transfers servers belonging to, allegedly, hundreds of companies.
Although the comments of the threat actors cannot be accepted at face value, Clop’s assertion supported a Microsoft analysis that connected the attacks to the hacker group Lace Tempest (also known as TA505 and FIN11), which the company tracks.
The Clop Ransomware group was also behind other high-impact data theft campaigns and is one of the most active threat actors’ groups.
The first companies that were compromised as a result of Clop’s MOVEit data-theft activities have slowly begun to emerge, with UK payroll and HR solutions provider Zellis disclosing a data breach that will probably also affect some of its clients. Between Zellis’s clients who have already confirmed they were impacted include Aer Lingus and British Airways.
All impacted firms have been warned by Clop to get in touch and discuss a ransom if they don’t want their data released public in six days, on June 14.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security