Contents:
The notorious Lazarus Group of North Korean state-sponsored threat actors is currently targeting vulnerable Windows Internet Information Services (IIS) web servers to obtain first access to business networks.
Lazarus’ primary motivation is financial, and many observers think that the hackers’ nefarious deeds help finance North Korea’s weapons-development initiatives. However, the gang has also taken part in a number of covert missions. South Korean researchers at AhnLab Security Emergency Response Center (ASEC) are the ones who discovered the threat group’s latest tactic.
What We Know About Attacks on IIS Servers
Organizations of all sizes utilize Windows Internet Information Services (IIS) web servers to host web content like websites, applications, and services like Microsoft Exchange’s Outlook on the Web.
It’s a flexible solution that has been available since the launch of Windows NT, supporting the HTTP, HTTPS, FTP, FTPS, SMTP, and NNTP protocols. However, if the servers are outdated or poorly managed, they can act as entry points for threat actors.
In order to create files on the IIS server via the w3wp.exe process, Lazarus first acquires access to IIS servers utilizing well-known flaws or configuration errors.
The threat actors drop ‘Wordconv.exe’, a valid Microsoft Office file, together with a malicious DLL called ‘msvcr100.dll’ and an encoded file called ‘msvcr100.dat’. The malicious code in the DLL loads when “Wordconv.exe” is launched in order to decrypt the Salsa20-encoded executable from msvcr100.dat and run it in memory, where antivirus programs cannot detect it.
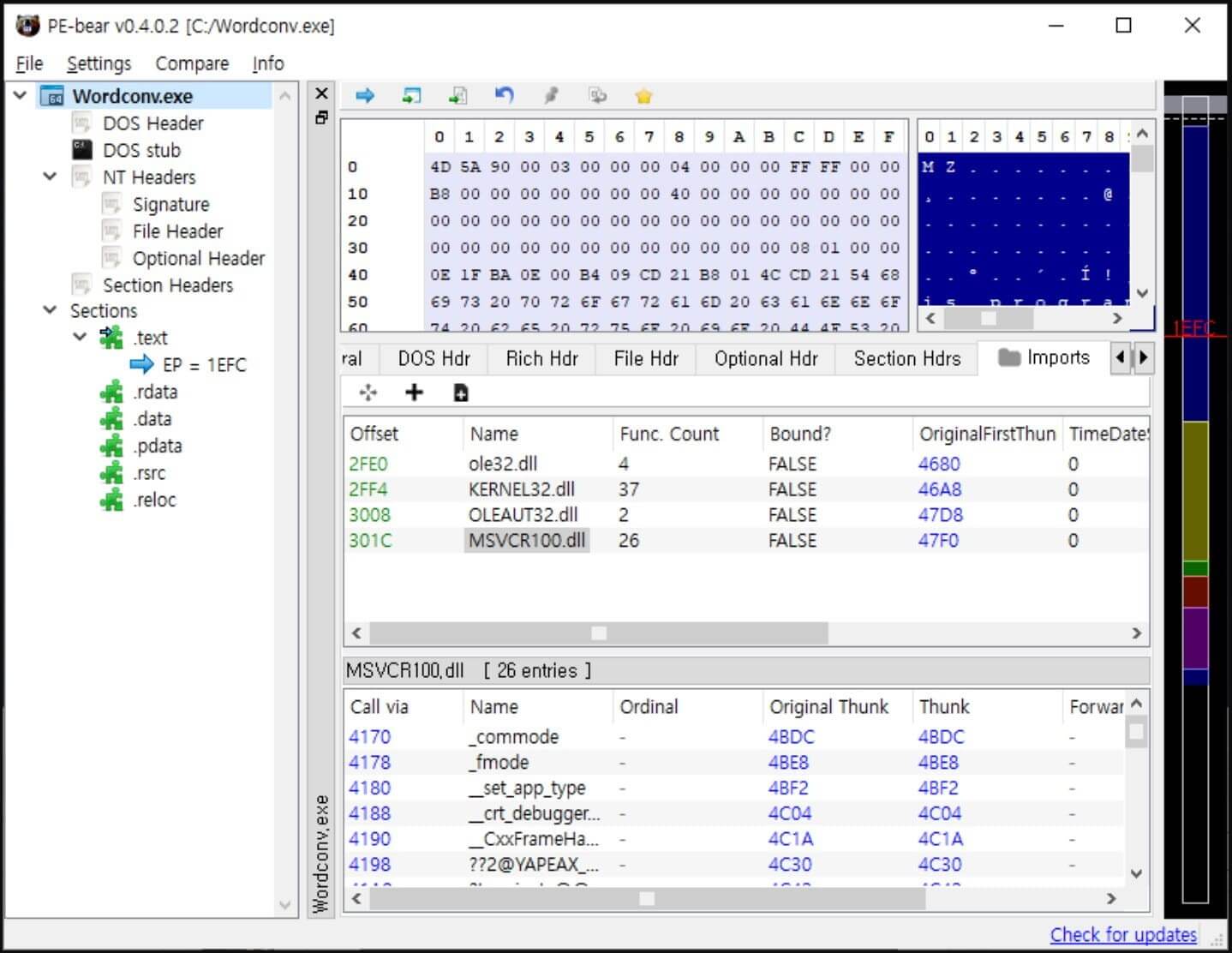
Import DLL List on ‘Wordconv.exe’ (Source)
The virus known as “msvcr100.dll” and “cylvc.dll,” which was used by Lazarus to deactivate anti-malware products via the “bring your own vulnerable driver” strategy, share a number of coding similarities, according to ASEC. Thus, ASEC considers that the newly discovered file is a new variant of the same malware.
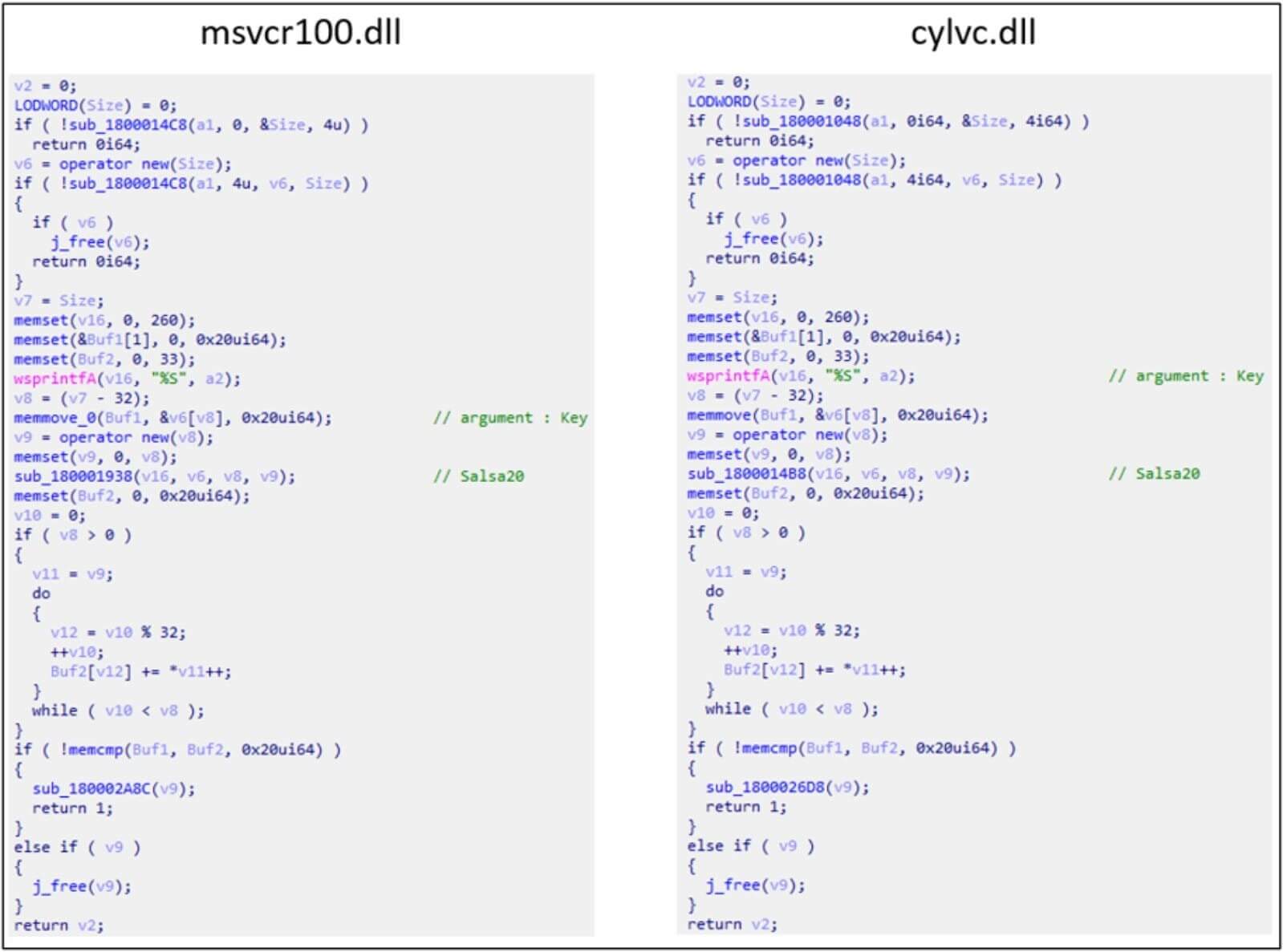
Lazarus proceeds the attacks by creating a second malware (‘diagn.dll’) through the exploitation of a Notepad++ plugin. The second malware then receives a fresh payload, this time encoded with the RC6 technique, decrypts it using a hard-coded key, and runs the payload in memory to conceal its execution.
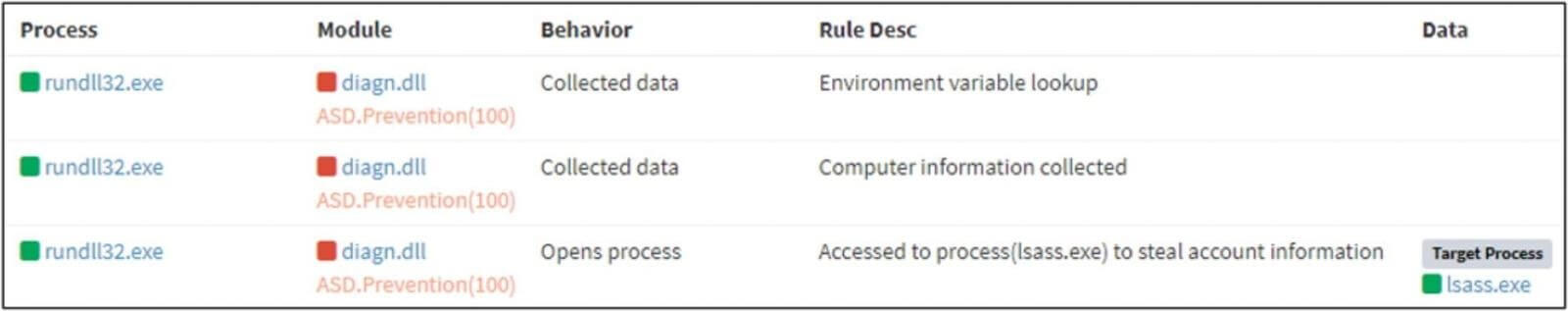
Using legitimate user credentials, most likely taken in the previous stage, the Lazarus attack’s final step was network reconnaissance and lateral movement through port 3389 (Remote Desktop). However, according to BleepingComputer, ASEC is yet to uncover any further malicious activities after the attackers spread laterally on the network.
As part of their attacks, Lazarus mainly relies on DLL sideloading, hence businesses are advised to keep an eye out for unusual process execution.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










