Contents:
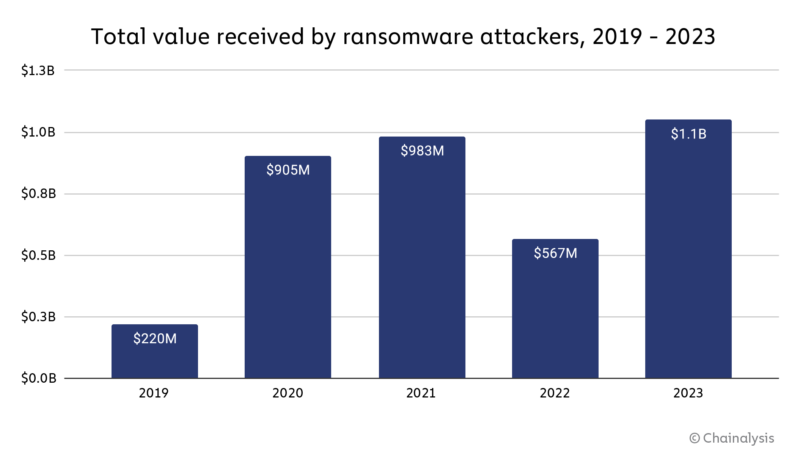
New Chainalysis warns of ransomware payments raised above above $1.1 billion in 2023 and reached a new record. The $983 million previous peak was set in 2021, while in 2022 the ransomware payments dropped to $567.
Chainalysis puts the unusual dropping on threat actors changing focus to politically motivated cyberattacks, due to the war in Ukraine.
There were, reportedly, other two important factors that lead to a decline in ransomware payment in 2022:
- some of the victims refused to pay ransom
- the FBI succeeded to infiltrate the Hive ransomware strain
Source – Chainalysis Report
However, the numbers went back up in 2023 and researchers expect them to continue growing.
Ransomware-as-a-Service continued to expand, making it easier for malicious actors to perform ransomware attacks. Also, the attackers targeted major institutions and critical infrastructure.
Chainalysis considers Cl0p to be one of the most prolific ransomware gangs. Cl0p threat actors are notoriously focusing on large gaining and targeted thousands of organizations worldwide. The report shows that almost half of the cashed ransom in June and July 2023 went to Cl0p.
A top five ransomware groups for 2023, according to cashed ransom payments, includes Cl0p, ALPHV/Blackcat, Play, LockBit, and BlackBasta.
2 main ransomware strategies
The Chainalysis report revealed that the major ransomware threat groups use different strategies to achieve their goals.
- Cl0p goes for big, but less frequent earnings. Their attacks are less frequent, but target organizations that would pay more. They exploited use zero-day vulnerabilities to reach their goals.
- ALPHV/Blackcat works as a RaaS strain. Their carefully chosen affiliates spread the malware and so the number of attacks that use Blackcat ransomware is higher. These ones too prefer attacking big targets, so they can cash larger sums. Phobos seems to use the same business model as Blackcat. This means they are also a Ransomware-as-a-Service (Raas). There`s frequent attacks but lower payments.
Another report, issued by Coverware, showed a decrease in ransom payments for 2023 Q4. However, the decrease is compared to the same year`s Q1, so we can`t actually consider it as a trend.
Although the numbers in 2022 were optimistic, the battle against ransomware crime obviously continues. In the context, companies should adopt a layered defense model to keep data safe and prevent ransomware attacks. Choosing cybersecurity solutions that use end-to-end encryption to protect sensitive data is also a best practice.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









