Contents:
Mutual authentication, also called two-way authentication or website-to-user authentication, is a cybersecurity method. It makes both sides of a communication channel prove their identities to each other, not just one side. This ensures secure communications before they proceed. So, this time, the process goes in both directions.
This authentication process is key for web and online apps. It means that both parties cannot trust each other until they check their identities. This ensures users communicate only with legitimate servers or entities. It also lets servers check if the user trying to access them is genuine.
This article covers everything you need to know about mutual authentication, including:
- What Is Mutual Authentication?
- How Does Mutual Authentication Work?
- Mutual Authentication Use Cases
- Mutual Authentication Main Components
- Types of Cyberattacks Mutual Authentication Helps Prevent
How Does Mutual Authentication Work?
A computer and a server authenticating each other
Mutual authentication requires both the client and server to trust each other’s digital certificates for a connection. They exchange certificates through the Transport Layer Security (TLS) protocol. The client’s digital certificate and private key are stored in a keystore. When the keystore has many signed certificates, the one with the most recent timestamp is used. This certificate authenticates the client to the server.
Mutual authentication minimizes the risk of users accidentally sharing sensitive info with malicious websites. However, users might still get deceptive emails. Yet, if a user clicks on a malicious link, mutual authentication systems stop data from reaching the fake site. It also prevents users from giving their login details to untrusted websites.
To give you an example of how this type of authentication works, imagine a bank customer ends up on a phishing site. With mutual authentication, they can’t enter sensitive info like passwords or Social Security numbers. This is until both their computer and the network server trust the connection.
Some technologies set up mutual authentication to divide both sent and received data into several channels. This strategy makes it harder for hackers to access the data.
Mutual authentication systems can stop a computer from using a webpage or its features if it’s marked as unsafe.
Mutual Authentication vs. Two-factor Authentication
Many think two-factor authentication (2FA) and mutual authentication are the same, but they’re not. In 2FA, the client gives the server two forms of identification, like a token and a password, to get access to resources and data. To boost security, you can use mutual authentication with 2FA and other tools like firewalls and antivirus software.
Mutual Authentications vs One-way Authentication
One-way authentication occurs all the time on the Internet. For example, when you visit a website with HTTPS, your device checks the website’s TLS certificate. Or, when you log into your account on a website or app, it checks who you are. In mutual authentication, both sides must prove their identity, using things like credentials or key pairs, depending on the method used.
Mutual Authentication Use Cases
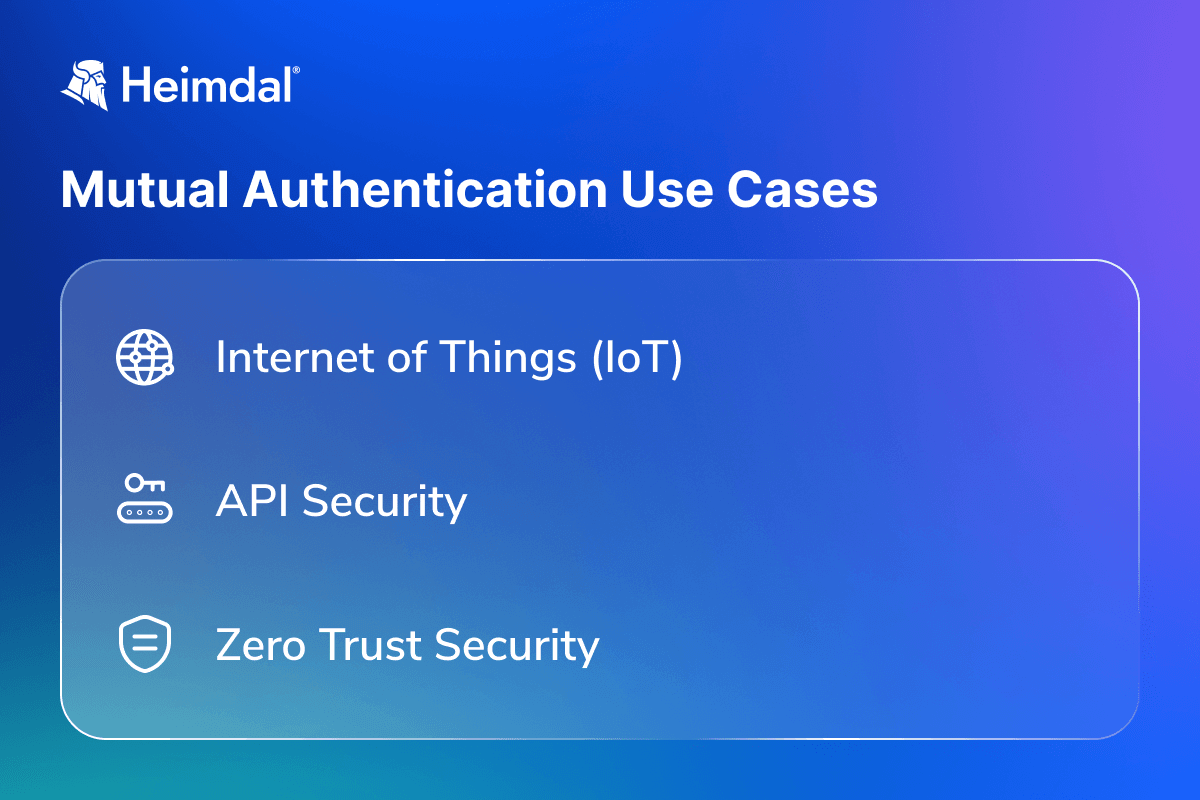
A list depicting mutual authentication use cases
Internet of Things (IoT)
The majority of IoT devices require a connection to a remote server for them to work properly. They may also need to connect to other Internet of Things devices. IoT devices have to do so over an unprotected network. Mutual authentication reduces the chance of a hacker breaking into connections. It does so by checking if the information is correct and from a trusted source.
API security
The API service must confirm its identity with the client application. Thanks to this authentication, the client knows it’s talking to the right API, not some malicious man-in-the-middle service. Similarly, a client has to authenticate itself to an API. This type of authentication tells the API the client is genuine. Mutual authentication stops both the API and its user from accepting fake requests or altered responses from hackers.
Zero Trust security
According to the Zero Trust philosophy, any user or device could pose a security threat. Mutual authentication requires both parties of a connection to prove their identity. This ensures only legitimate users can connect to the network, server, or app. Conversely, users can be certain they are connected to the right network, server, or program.
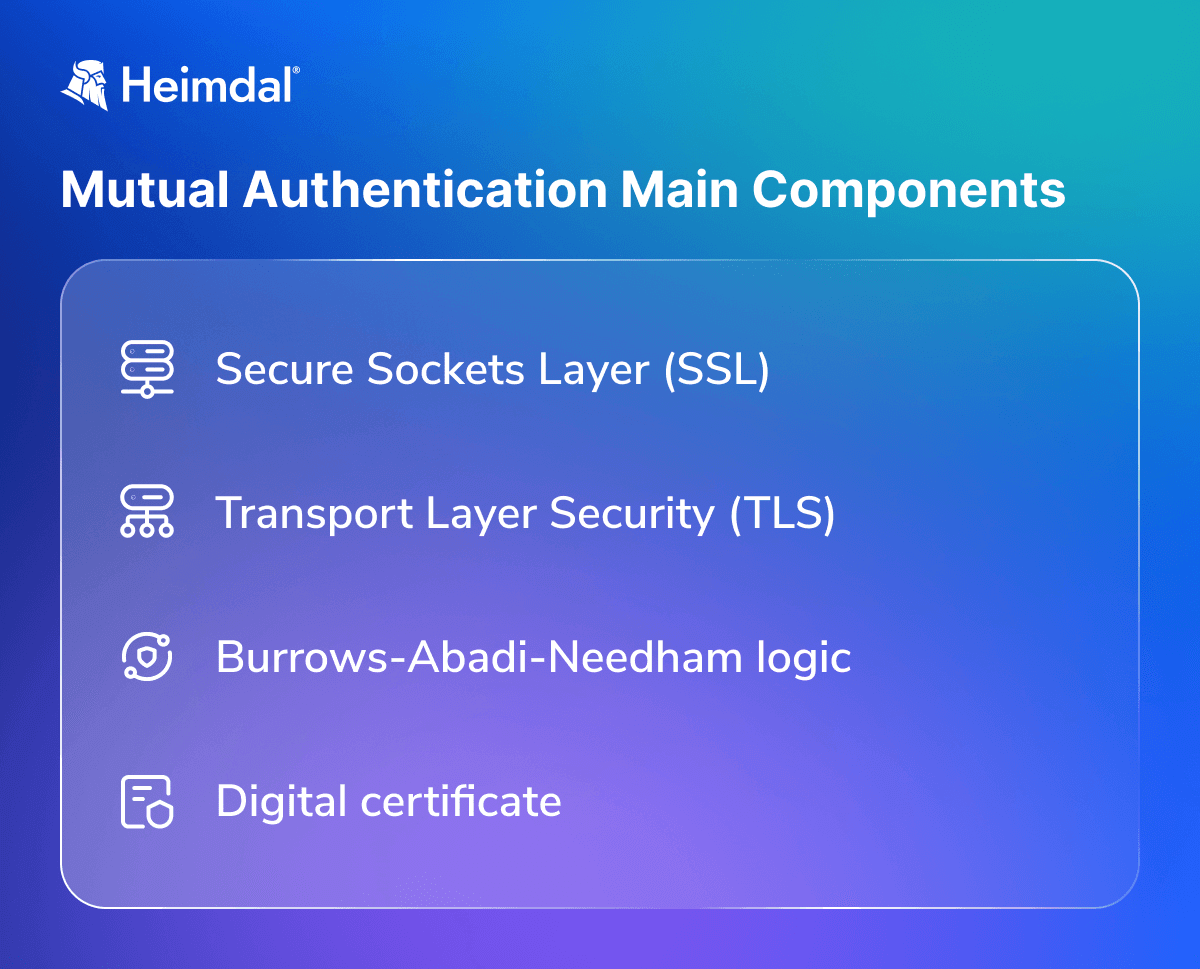
Mutual Authentication Main Components
Secure Sockets Layer (SSL)
SSL stands for Secure Sockets Layer, which is an encryption method used to ensure the security of data transmitted and received from a user to a specific website and back. Encrypting this data transfer guarantees that no one can eavesdrop on the transmission and obtain access to sensitive information, such as card details in the case of online shopping. Encrypted communication sessions are established using digital signatures and keys.
Transport Layer Security (TLS)
The functionality of TLS is similar to that of SSL, which it evolved from. However, when it comes to message authentication, key material generation, cipher suites, and supported algorithms, the technology TLS employs is more secure and efficient than SSL.
Burrows-Abadi-Needham logic
BAN logic is a zero-trust algorithm that defines and analyzes exchange protocols. To be more precise, BAN logic helps users to establish whether exchanged data is reliable and protected from snooping. BAN logic starts from the premise that all information exchanges take place on media that can be tampered with and monitored. As per Wikipedia, this has evolved into the popular security mantra, “Don’t trust the network.” A conventional BAN logic sequence includes the confirmation of the message source, “freshness”, and the origin’s integrity.
Digital certificate
These certificates include a few things that are critical to the mutual authentication process. These are:
- the public key being validated,
- details identifying the organization in possession of the public key,
- the digital signature of the public key the certificate issuer generated,
- related metadata.
Which Attack Types Can Mutual Authentication Help Prevent?
Mutual authentication can safeguard communications against cyber threats including:

Man-in-the-Middle attack
Man-in-the-middle (MITM) attacks happen when a third party tries to listen in or intercept a message and, occasionally, changes the original message for the user who is receiving it. The two sides of the communication openly receive messages without checking the identity of the sender, so they are unaware that a malicious actor has entered the communications channel. Mutual authentication can help stop MITM attacks as both the sender and receiver authenticate each other before sending their message keys, so if one of the sides is not confirmed to be who they claim to be, the session will be terminated.
Replay attack
Similar to an MITM attack, a replay attack involves replaying older messages out of context to trick the server. Nevertheless, this type of intrusion does not work against mutual authentication systems because timestamps are a verification component used in the protocols. If the change in time is greater than the maximum allowed time delay, the session will be terminated.
Spoofing attack
Spoofing is a type of cyberattack in which fake data is used to impersonate another user to get access to a server or be identified as someone else. Mutual authentication helps to prevent spoofing attacks because the server also authenticates the user and confirms that they have the right session key before permitting any further information exchange or access.
Impersonation attack
When each side authenticates the other, they send each other a certificate that only the other entity knows how to decipher, thereby confirming themselves as a trustworthy source. As a result, malicious actors are prevented from carrying out impersonation attacks because they lack the necessary certificates to pose as the other party.
Credential theft
Mutual authentication tools that rely on passwords are still vulnerable to credential theft. However, because mutual authentication is typically public key-based, there are no credentials to steal, making credential theft impossible. This can prevent the effectiveness of a phishing attack.
If you wanna learn more about the different types of password attacks, make sure you check out the video below:
How Can Heimdal® Help?
Mutual authentication is a key component of the zero-trust approach, and Zero-Trust is a central element in the Heimdal cybersecurity strategy. As the company’s CEO, Morten Kjaersgaard, says,
In the Heimdal suite, the Zero-Trust Execution Protection is a cross-module component included in three of the main modules: Privileged Access Management, Application Control and Next-Gen Antivirus. The module enables the intelligent diagnosis of all processes that are running in the IT environment of customers to identify and stop malicious or suspicious executions, because we know that we could not possibly predict future malware with 100% certainty.
Heimdal’s Zero Trust component saves a significant amount of time for system administrators and, most importantly, it ensures limited access, increased compliance, simplification of addressing risks, helping customers to always be one step ahead of any cybercriminal – or insider threat.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
If you liked this article, make sure you follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








