Contents:
[playht_player width=”100%” height=”90px” voice=”Michael (en-US)”]
What Is LockBit Ransomware?
LockBit ransomware is a new ransomware gang that’s been making headlines lately. While commonly known as ABCD ransomware, LockBit has now grown into its unique threat within the scope of these extortion tools.
LockBit ransomware is a new release of malicious software that targets organizations through email attachments and cascading file system infections.
Unlike other types of ransomware, which focus on businesses and individuals, LockBit mainly affects businesses and government organizations.
LockBit has been used in major worldwide attacks, most notably in September 2019. At that time, it was called the “.abcd virus.” The name was a reference to the file extension used by LockBit when encrypting a victim’s files.
Notable past targets include organizations in the United States, China, India, Indonesia, and Ukraine. Additionally, countries throughout Europe (France, the UK, and Germany) have also seen LockBit attacks.
Viable targets feel hindered by the disruption and have enough funds to pay a heavy sum. The relocation of these attacks can result in sprawling attacks against large enterprises, from healthcare to financial institutions.
LockBit ransomware has outstripped others with innovative entry methods and the fastest encryption technology. Defending against this major threat demands a thorough, multi-layered cybersecurity approach, blending basic practices with constant vigilance and learning from past victims’ oversights to avoid joining their ranks.
– Andrei Hinodache, Cybersecurity Expert at Heimdal®
How Dangerous is LockBit Ransomware?
LockBit attackers actively threaten organizations worldwide with:
- Disrupting essential operations by abruptly halting critical functions.
- Extorting money for their financial gain.
- Stealing data and threatening illegal publication as blackmail if victims do not comply.
It is one of the most active ransomware groups today, and its tactics and technologies pose various threats to organizations in any industry.
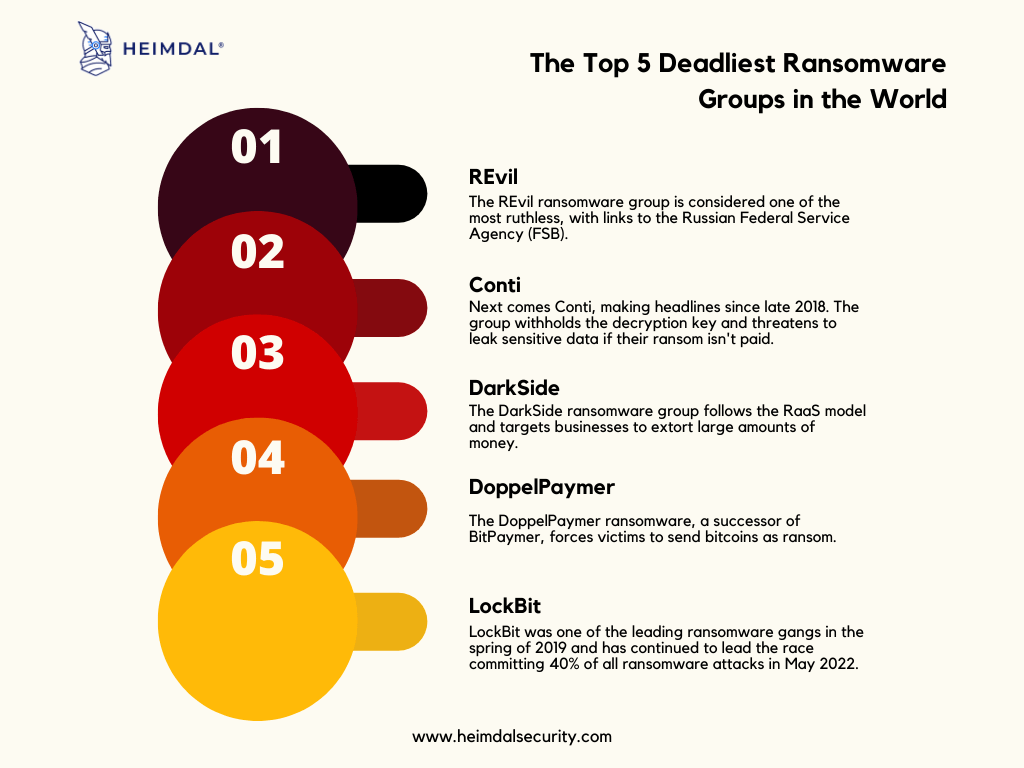
Below we’ve prepared a chart with the top five most dangerous ransomware gangs in the world, LockBit being one of them.
Here’s why LockBit ransowmare is so dangerous:
- The threat gang at LockBit launched the latest version, which includes a new encryption tool called StealBit. It runs on a machine whose speed is unmatched and is much more efficient than previous versions.
- StealBit spreads automatically to other devices on the same network using tools like Windows Powershell and Server Message Block (SMB).
- LockBit initially focused on Windows systems, but LockBit 2.0 has also evolved to attack Linux computers. LockBit deeply infiltrates both operating systems with its malware and can quickly target key data.
- Their strategies are devious and well-thought-out, making it difficult for the system’s defenses to flag them.
- This ransomware group actively markets to affiliates and encourages them to carry out attacks.
- LockBit is well-known for their double-extortion technique. They steal data and encrypt the victim’s system data to create more challenges for their victims.
- In August 2022, LockBit announced they would use triple-extortion on their victims through data leaks, encryption, and DDoS attacks.
We posted a video about the most dangerous ransomware gangs in 2022. You can check it out here if you want more information.
How Does LockBit Ransomware Work?
The LockBit ransomware attacks are self-spreading, which means that they can do severe damage to an organization on their own. They don’t need to be directed by an individual for them to spread like wildfire.
They also use similar tools to spread, like Windows Powershell and Server Message Block (SMB).
The most significant difference with LockBit is that it self-propagates. This means it spreads on its own instead of relying on someone manually applying it within the network. The programming behind LockBit is also different from most other ransomware attacks since it’s directed by pre-designed automated processes, which makes it unique.
A quick explanation reveals our understanding of these attacks as follows:
- They spread by themselves within an organization instead of needing manual direction.
- They are targeted, unlike spam malware, which spreads in a scattershot fashion.
- They use similar tools for spreading, such as Windows Powershell and Server Message Block (SMB).
In addition, it employs malicious tools native to most Windows computers. As a result, it has difficulty flagging suspect activity and will even disguise the executable as the common. PNG file extension to elude system defenses.
Stages Of LockBit Attacks
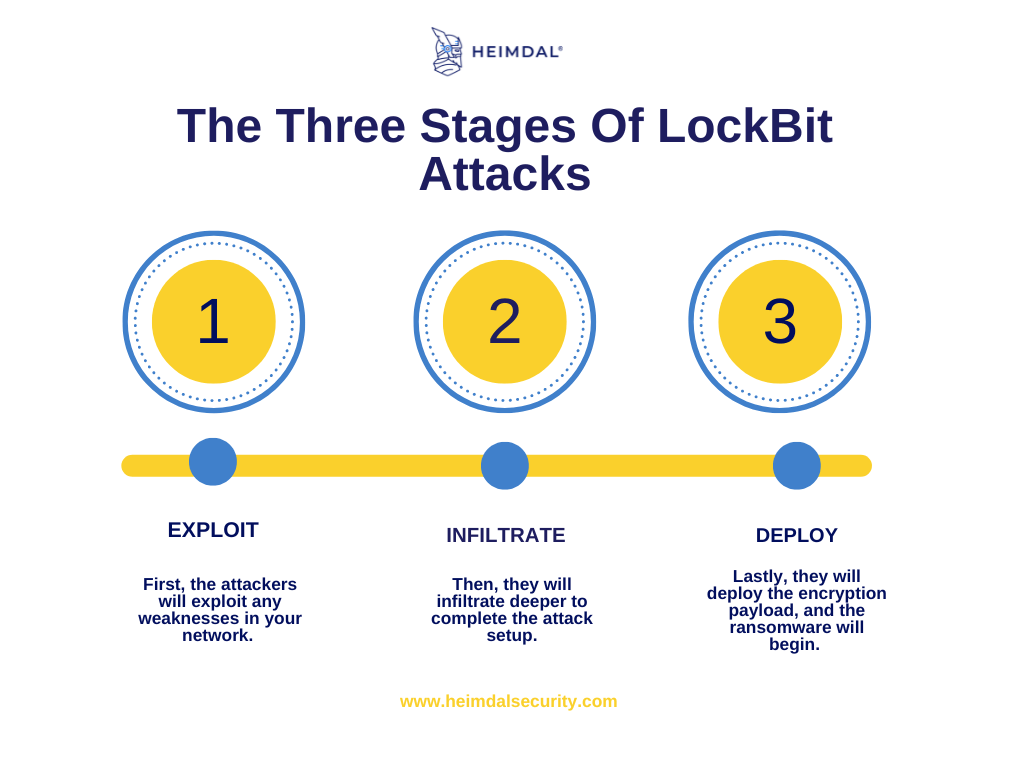
Stage 1: Exploit
Attackers can exploit any weakness in a network.
The initial breach may look like a typical malicious attack, but it’ll quickly escalate. One way to gain access is by using social engineering tactics such as phishing, in which the attackers impersonate trusted personnel or authorities to request access credentials. Alternatively, brute-force attacks on an organization’s intranet servers and network systems can be successful without much time invested.
Once LockBit has made it into a network, the ransomware prepares the system to release its encrypting payload across every device it can. For an attacker to complete the attack, they’ll have to make a few more preparations beforehand.
Stage 2:Infiltrate
From this point forward, LockBit operates independently.
It is programmed to use “post-exploitation” tools to gain access privileges and complete an attack-ready level of access. It will also root through any exploits available for lateral movement to vet viable targets.
One of the scary things about LockBit is that it can take preparative actions before deploying encryption. This includes disabling security programs and other infrastructure that could facilitate system recovery.
When an attacker’s objective is infiltration, their strategy is to slow the victim down to a point where they’re willing to pay the ransom fee. That’s a win-win situation for the attacker because it leads to more significant profits.
Stage 3: Deploy
Once the network has been prepared for LockBit to be fully operational, it will begin propagating across any machine it can touch.
As we mentioned, LockBit doesn’t need much to be ready to progress to this attack stage. A single host with high access can issue commands for other network hosts to download LockBit and execute it.
LockBit will place a “lock” on all system files, blocking the victims. Victims can only unlock their systems via a custom key created by LockBit’s proprietary decryption tool. The process also leaves copies of a message in every system folder instructing the victim on restoring their system and threatening blackmail in some LockBit versions.
For now, the victim will have to decide what to do. They can contact LockBit’s support team and pay the ransom, but it is not advised, as the attackers might not follow through on their promised end of the bargain. Victims do not get any guarantees that the attackers will follow through or keep any information they promise to maintain privacy.
Types of LockBit Ransomware Threats
The latest ransomware attack surge, LockBit, is a significant concern. We can’t rule out the possibility that it will take hold across many industries and organizations, especially with more people working remotely lately. However, spotting LockBit’s variants can help identify your problem.
- Variant 1 —. abcd extension
LockBit’s original version renames files with the “.abcd” extension. Additionally, it includes a ransom note with demands and instructions for allegedly fixing the files in the “Restore-My-Files.txt” file, which has been inserted into every folder.
- Variant 2 —. LockBit extension
From its inception, the second known version of this ransomware virus adopted the file extension “.LockBit” to give it its current name. However, despite some backend revisions and file name changes, victims will find other traits, including targeting instructions and persistence methods, that this version shares with previous versions.
- Variant 3 —. LockBit version 2
In the latest version of LockBit, you no longer need to use the Tor browser to pay the ransom. Instead, it sends victims to an alternate website where they can enter their data and make a payment.
LockBit has recently enhanced the software with more infamous features, such as negating administrator permission checkpoints. In addition, LockBit now also blocks the safety prompts that users may see when an application attempts to run as an administrator.
The LockBit malware now includes additional lines of blackmail; if the victim doesn’t follow instructions, they will release the victim’s private data.
LockBit Removal and Decryption
Thorough protection standards for unified endpoint devices across your entire organization are necessary to combat the trouble that LockBit can cause.
The first step is to have a comprehensive endpoint security solution like Heimdal® Endpoint Detection and Response EDR Software, which provides layered protection for all your devices.
All of its components work together and leverage the intelligence from the other modules to secure your entire ecosystem.
If you fall victim to LockBit, removing it alone will not give you access to your files. Instead, you need a tool to restore your system, as encryption requires a key to unlock. Alternatively, you can correct this by reimaging your system if you have pre-infection backup images already created.
How to Protect Against LockBit Ransomware?
You’ll have to set up protective measures to protect your business, such as losing data and restoring from backup.
The following strategies can help you prepare for ransomware or malicious attacks:
- The first line of defense on your account is a strong password.
However, most account breaches result from easy passwords for programs to figure out within a few days. So make sure you choose a secure password with variations in length and character types and use self-created rules to make your passphrase as tricky as possible to guess.
- Activate multi-factor authentication.
Sometimes you use a password that is easy to remember, but it also means it’s easy for someone to guess. Add second and third layers of authentication to protect yourself from brute force attacks. For example, you can have biometrics or a physical USB key.
- Keep an eye on user account permissions.
Reduce levels for those granted access to limit threats and vulnerabilities from deterring their way through unblocked paths. Focus on accounts accessed by endpoint users and IT accounts with admin-level permissions, web domains, collaborative platforms, web meeting services, enterprise databases, and more.
- Deactivate and close old user accounts.
Some older software systems may have inactive or abandoned accounts from past employees that were never removed. Therefore, complete a checkup on your account to remove potential weak points.
- Ensure that your system configurations follow all security procedures and have the latest updates.
This may take time, but revisiting existing setups may reveal new issues and outdated policies that put your organization at risk of attack. When it comes to standard procedures, you should consider them because they’re one of the most critical parts of any cybersecurity plan.
- Have regular system-wide backups.
To avoid permanent data loss, it’s essential to have system-wide backups. Unfortunately, incidents can happen; when they do, the only safeguard is an offline copy. Periodically your organization should be creating backups up to date with any changes to your systems. If a backup becomes tainted with a malware infection, consider keeping multiple rotating backup points for the option to select a clean period.
- Be sure to have a comprehensive enterprise cyber security solution in place.
One of the worst things that can happen to your business is getting hacked. LockBit might successfully disable protection a few times.
Still, an even more sophisticated level of protection would help you protect against cyber threats in your entire organization with automated real-time prevention.
Heimdal® features and unified protection software can stop even the most sophisticated cyberattacks, no matter what they are or where they’re coming from. You’ll never have to worry about sensitive data security again.
Heimdal™ Ransomware Encryption Protection
Wrap Up
To mitigate the risk of a LockBit ransomware attack, implement strong access controls with tight password policies and two-factor authentication.
Also, maintain an ongoing vulnerability management program that ensures security updates are applied as they’re released, and architect internal resources in a way that makes them hard to access.
Heimdal® Patch & Asset Management provides automated patching for your network and complete visibility and granular control over your entire software inventory.
Additionally, enable Protected Files in the Windows Operating System to secure critical system files from being hacked.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









