Contents:
As its name implies, DNS security refers to the set of practices employed by an individual or an organization to prevent attacks that are either at the level of the Domain Name System or facilitated by it. As mentioned in a preceding chapter, the DNS was simply not built with security in mind because cyberattacks that exploited it were not common in the 1980s. Nevertheless, the entities in charge of administering this infrastructure soon realized the dangers it posed, and thus, Domain Name System Security Extensions (DNSSEC) were created. This was the world’s response to an ever-increasing pool of cyber-threats that aimed to exploit this vulnerable system as much as possible.
What Is DNSSEC?
As hackers started learning new and cunning ways to exploit this then-new infrastructure, the need arose for more robust protection at the level of the Domain Name System.
As a consequence, the Internet Engineering Task Force (IETF) released the first Request for Comments (RFC) about DNSSEC in 1997. This RFC and the subsequent ones released on the same topic are specifications that help protect the DNS against a variety of intrusions. Because DNS queries are not inherently secured and the parties involved in query resolution are always susceptible to one or more types of attacks, these solutions were designed as add-ons or extensions.
DNSSEC ensures the security and confidentiality of data (serving 2 out of 3 points of the CIA triad), which is an aspect that is not normally handled through DNS. Thus, these extensions serve as a cornerstone for digital trust and prevent DNS attacks such as denial-of-service and hijacking. Through signature checking, a DNSSEC resolver can verify if the data that came from a valid server is identical to the data on the authoritative DNS server. This is made possible by the fact that DNSSEC servers digitally sign all server answers. If this is not the case, the request will be denied.
How Does DNSSEC Work?
Fundamentally, DNSSEC was created with the intention of defending Internet users against forged DNS data by confirming the data’s embedded digital signatures. The resolver validates the digital signature when a visitor types the domain name into a browser. The data is granted access to the client machine that submitted the request if the digital signatures in the data reflect those that are kept in the master DNS servers.
You can communicate with the website or Internet address you planned to visit with the help of the DNSSEC digital signature. DNSSEC verifies DNS query responses before providing them to the client machine. DNSSEC uses both standard DNS record types and digital signatures that are maintained in name servers.
Data is verified by DNSSEC using a system of public keys and digital signatures. It merely augments the DNS with additional records. For DNSSEC validation, public key cryptography is used as a foundation. A public key, which is accessible to everyone, offers the ability to decrypt messages that have been signed with a correspondent private key.
The same method used to retrieve standard records like A, CNAME, and MX can also be used to retrieve newer record types like RRSIG and DNSKEY.
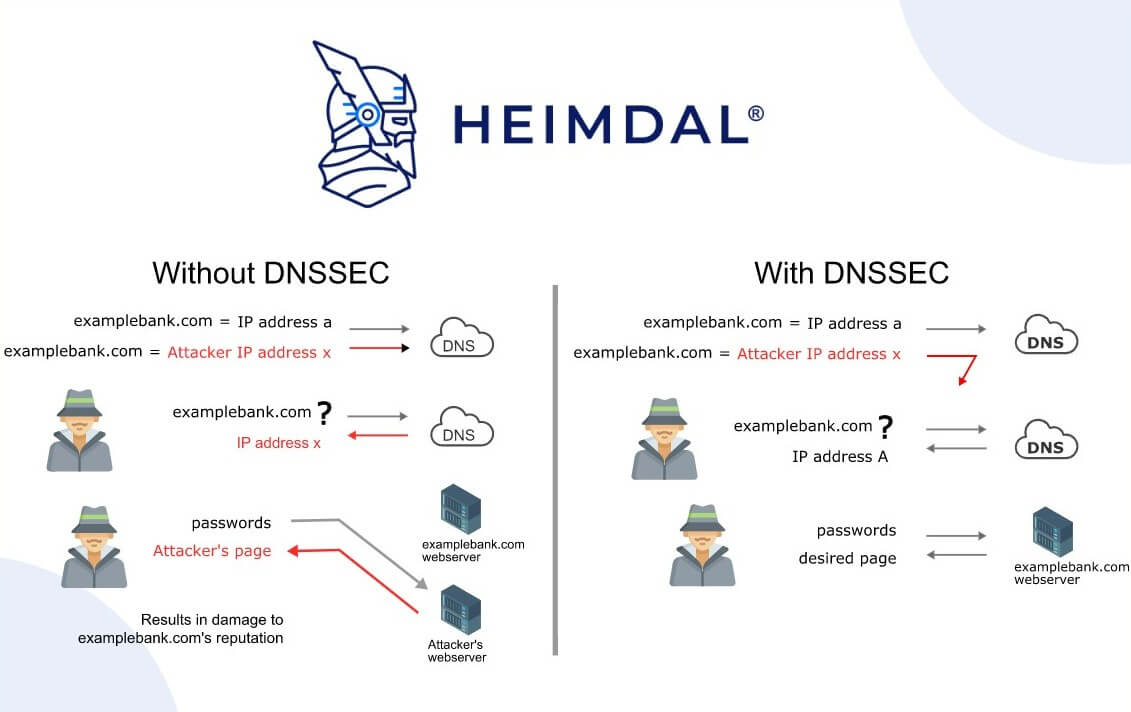
Public key cryptography is used to “sign” a domain digitally using this new information. Each location’s public and private keys are present in a signed nameserver. It uses its private key to sign data when someone requests something, and the recipient uses his public key to decrypt it after receiving it. The recipient will be aware that the information is false if a third party tries to deliver it as it won’t unlock effectively with the public key.
To be clear, popular security solutions like using SSL certificates, DNS data encryption, or shared sensitive data do not constitute DNSSEC security.
Please note that when it comes to DNS-based attacks, DNSSEC should not be your primary line of security. While its security benefits cannot be contested, more sophisticated protocols such as DNS over HTTPS (DoH) and DNS over TPC are available. All DNS queries transmitted from a browser to a server are encrypted using the DoH protocol,which prevents manmade attacks from getting through encryption measures. DNSSEC has been extended to cover DNS over HTTPS and, although the concept is still in its early stages, the idea is that DNS over HTTPS would enable authenticated queries to be checked by DNSSEC.DNS over TPC is another protocol that establishes a dead drop for messages and allows encrypted communications between two parties without first establishing a connection. These sorts of security layers provide data privacy to standard DNS connections, meaning that queries conducted on your company’s endpoints are less likely to be intercepted.
Types of DNS Security Extensions
Just like most things digital, DNSSEC comes in many shapes and sizes that follow the purposes that they serve. Therefore, we need to have a look at the different types to better understand how these add-ons work at the level of your endpoints and network. Some of the most common DNS security extensions are:
Cryptographic authentication of DNS data
It is usually performed with a symmetric key since it consumes fewer network resources as compared to using asymmetric cryptography.
Authenticated DoE (Denial of Existence)
This procedure allows the DNS resolver to tell whether or not a domain exists. At the same time, it can confirm that the yet-to-be-resolved domain does, indeed, exists.
Data integrity and authentication
DNS Security Extensions ensure authentication by binding crypto-generated digital signatures to the corresponding Domain Name Systems RRsets. As explained by Microsoft’s DNS documentation, RR (resource records) are the “building blocks of host-name and IP information and are used to resolve all DNS queries”. RRs come in various shapes and sizes: MicrosoftDNS_MBType for mailbox records, MicrosoftDNS_AType, used for name-to-address-mapping, and MicrosoftDNS_MFT Type (mail forwarding agent for the domain record). These are just a few RR types, but there are plenty more where they came from. Furthermore, DNNSEC also covers origin authentication, providing an extra security boost. Why? Because crypto-generated digital signatures can put the servers and resolvers at ease, knowing that the data came from a trusted source.
Benefits of DNSSEC
Through its role in preventing users from being forcibly redirected to malicious websites and unauthorized domains, DNSSEC seeks to increase confidence on the Internet. Thus, malicious actions including man-in-the-middle cyberattacks, DNS spoofing, DNS hijacking, phishing, and cache poisoning can be avoided.
To ensure that the DNS server’s responses are legitimate and authentic, DNSSEC uses a cryptographic signature to validate the resolution of IP addresses. Users can be assured that they are connecting to the correct website belonging to a given domain name if DNSSEC is correctly set for their domain name.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
How to Improve Your DNS Security
The term DNSSEC, in a nutshell, refers to the methodology used to protect DNS servers, data, and clients from unlawful eavesdropping and data exfiltration. However, said DNSSEC methodology, even when combined with other traditional security components such as RPZs or DMZs, requires heavy backup from additional DNS protection measures to guard your enterprise and all its digital assets against intrusions performed by malicious third parties.
For example, DNSSEC can detect man-in-the-middle attacks by performing data origin authentication. However, the infrastructure will not prevent these types of attacks. Therefore, DNS security extensions and the other standard components that we discussed above are subsets of DNS security, not a synonym for it.
You must enhance the capabilities of these traditional components with cutting-edge solutions in order to improve your cybersecurity posture when it comes to accessing the Domain Name System. The first step is to invest in DNS filtering, a straightforward but effective line of security that sorts through traffic flowing to and from corporate machines. This is a simple approach to ensure that no hostile actors slip through the cracks unnoticed.
Finding a system that can work in tandem with any antivirus program, strengthening its firewall and EDR features with a leading-edge threat hunting component that anticipates dangers of the future, is another crucial factor to take into account. This will enable you to prevent cyberattacks and adopt a proactive approach to the complete DNS-layer security infrastructure. This is crucial in a field like the Domain Name System, where the majority of conventional measures are, at best, reactive.
Threat Prevention, a code-autonomous endpoint DNS threat hunting system from Heimdal, is the perfect solution to this problem. It can identify malicious URLs and processes and then trace the attacker’s sources to provide complete transparency into what is happening behind the scenes in your cybersecurity environment. With such technology at your disposal, you can take full management of both your network and endpoints from a single, easily navigable interface.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;
Wrapping Up
A lot of cyberattacks begin using the Domain Name System as their point of entry. Directly attempting to block legitimate user access or even take over a legitimate website, some threat actors overwhelm it with fraudulent requests. Yet, other online hackers use DNS as a tool to advance their own agendas.
The result is that many threats, including malware, exploits, botnets, ransomware, worms, and more, can spread through this crucial infrastructure. After penetrating your corporate system via fraudulent traffic, hackers can have a field day with the DNS attack methods and tools at their disposal.
Fortunately, over time, common DNS security mechanisms like DNSSEC have been implemented. You can take the necessary measures against cyber attackers attempting to use the Domain Name System for their malicious purposes and add other solutions such as Heimdal Threat Prevention-Endpoint and Threat Prevention-Network on top. As with anything else, prevention is always preferable to cure.
For more information on DNS Security and DNSSEC, make sure you check out my colleague Alina’s latest eBook below.

DNS Security for Dummies
An eBook that gives a comprehensive role-based security approach and addresses the numerous dangers to the Domain Name Systems (DNS) as cyberattacks increase globally.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








