Contents:
Cyber-attacks can come in many forms. In the world of cybersecurity, the terms “ransomware” and “malware” are often used interchangeably, leading to confusion about their distinct characteristics and implications.
While both ransomware and malware fall under the broader category of malicious software, they serve different purposes and have unique impacts on organizations and society.
Understanding the differences between these two threats is crucial for implementing effective cybersecurity measures and safeguarding digital environments.
In this article, we’ll explore ransomware vs. malware, what they are, how do they work, and what’s the difference between them.
The Basics of Malware
“Malware” is a portmanteau of “malicious software”, encompassing various software programs or code designed with harmful intent. Malware is a broad term covering multiple types of malicious software, including viruses, worms, Trojans, spyware, adware, and ransomware. The primary objective of malware is to gain unauthorized access to computer systems, steal sensitive information, disrupt normal system functioning, or compromise user privacy.
- Viruses: These are self-replicating programs that attach themselves to legitimate files and spread throughout a computer system or network when the infected file is executed. Viruses can corrupt or destroy data and impact system performance.
- Worms: Worms are self-contained programs that don’t need a host file to spread. They exploit vulnerabilities in network protocols to replicate themselves across connected devices, often causing network congestion and system slowdowns.
- Trojans: Trojans disguise themselves as legitimate software to trick users into installing them. Once installed, they can create backdoors for remote access, steal data, or enable other malicious activities.
- Spyware: Spyware secretly gathers information about a user’s activities, such as browsing habits, keystrokes, and personal information. This data is then transmitted to the attacker without the user’s consent.
- Adware: Adware displays unwanted advertisements to users, often in a way that generates revenue for the attacker. While it might not be as directly harmful as other types of malware, it can still degrade the user experience and compromise privacy.
- Rootkits: Rootkits are specific kinds of viruses intended to grant access to a computer’s unapproved areas.
- Bots: Bots are software programs made to carry out repeated activities. When bots carry out criminal actions like propagating spam or direct web traffic as part of a DDoS assault, they are classified as malware.
How Does Malware Work?
Malware often infects a machine by persuading users to click on and install a program from the Internet that they shouldn’t. The malicious code executes actions the user does not expect or want when the click or installation occurs. These actions could include:
- Self-replication in many file system components;
- Installing programs that record keystrokes or commandeer system resources, frequently operating covertly and significantly slowing down the system;
- Blocking access to specific files, programs, or even the system itself and occasionally requiring the user to pay to get access back;
- Saturating a desktop or browser with advertising;
- Damaging a device’s critical system components and leaving it unusable.
Many user actions can initiate the malware execution, but the most common is a click, generally on a link or pop-up. The descriptions could include phrases like “Claim your prize” or “Your account has been compromised.” Please log in and see the most current charges.”
A pop-up message will frequently appear shortly after visiting the link, such as “Your system is infected! “Click here to start a scan.” Even if the user does not select one of the alternatives and instead tries to close the program using the corner X, the next click frequently results in the download of a malicious payload.
Malware can also masquerade as a tool or app that purports to convert PDFs, unzip files, locate product discounts, or give caller ID features on a smartphone. However, once downloaded, the malware begins making unauthorized changes to the system, such as tracking user behavior, displaying pop-ups, modifying search engine results, adding icons to the desktop, or redirecting popular websites.
Now, let’s discuss ransomware.
The Basics of Ransomware
Ransomware is a type of malicious software designed to encrypt a victim’s files or lock them out of their computer systems, making the data inaccessible until a ransom is paid to the attackers.
This digital hostage situation can be associated with a real-world kidnapping, where access to vital information is seized until a ransom is delivered. The attackers demand payment in cryptocurrencies, often Bitcoin, due to its pseudonymous nature that makes tracing transactions challenging.
Did you know that enterprises worldwide identified 493.33 million ransomware attacks in 2022? Manufacturing enterprises globally experienced 437 similar assaults in 2022. With almost 50 ransomware assaults, the food and beverage industries came in second.
North America ranks #1 among other global areas regarding the proportion of ransomware attacks on critical infrastructure, followed by Europe. In 2022, healthcare and public health institutions filed the most complaints to US law enforcement regarding ransomware attacks.
How Does Ransomware Work?
Ransomware uses asymmetric encryption. This is cryptography that encrypts and decrypts a file using a pair of keys. The attacker generates a unique public-private pair of keys for the victim, with the private key used to decrypt files saved on the attacker’s server.
The attacker only makes the victim’s private key available once the ransom is paid, although, as demonstrated in recent ransomware attempts, this is not always the case. It is nearly easy to decode the files being held for ransom with access to the private key.
The Mechanics of Ransomware
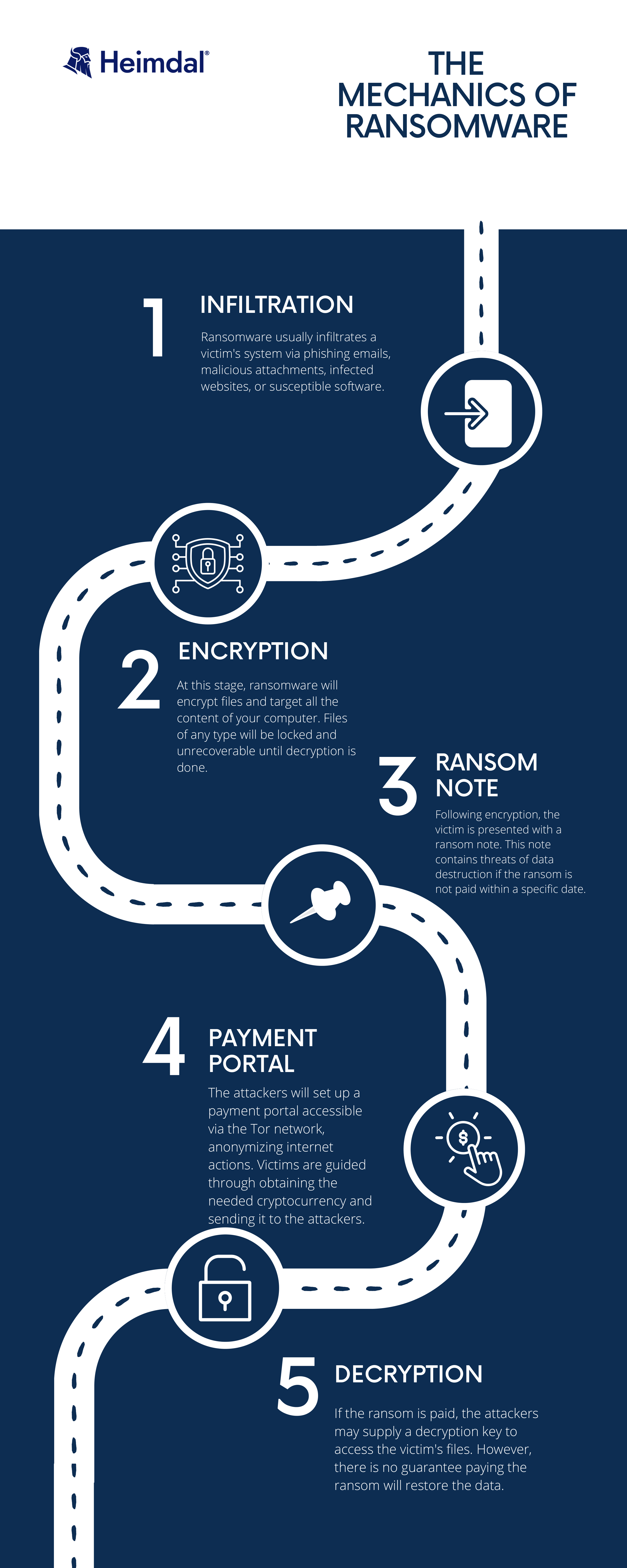
- Infiltration: Ransomware typically enters a victim’s system through deceptive emails, malicious attachments, infected websites, or vulnerable software. Once the initial entry point is exploited, the ransomware propagates through the system, encrypting files.
- Encryption: The ransomware employs complex encryption algorithms to lock the victim’s files with a unique decryption key. The attackers hold this key, making the data inaccessible to the victim without it.
- Ransom Note: After encryption, the victim is presented with a ransom note explaining the situation and providing instructions on how to pay the ransom. This note often includes warnings of data destruction if the ransom is not paid within a specific timeframe.
- Payment Portal: The attackers set up a payment portal accessible through the Tor network, which anonymizes online activities. Victims are guided through purchasing the required cryptocurrency and sending it to the attackers’ wallets.
- Decryption (Optional): If the ransom is paid, the attackers may provide a decryption key to unlock the victim’s files. However, there is no guarantee paying the ransom will result in data restoration, as some attackers may take the money and disappear without providing the key.
Key Differences Between Ransomware & Malware
The fundamental difference between ransomware and other types of malware lies in their objectives. While malware encompasses a wide range of malicious software, including ransomware, its purposes can vary from data theft to unauthorized access. Ransomware, on the other hand, focuses on extortion and financial gain through the hostage-taking of digital assets.
From a cybersecurity perspective, defending against malware and ransomware requires a multi-layered approach. This includes keeping software up to date, employing solid and unique passwords, using reputable security software, educating users about phishing and malicious attachments, and maintaining regular offline data backups.
Purpose
- Malware: As we already mentioned, malware has various purposes, including data theft, system disruption, remote control of infected devices, propagation to other systems, and more. Its intentions can range from cyber espionage to financial gain, among others.
- Ransomware: Ransomware’s primary purpose is financial gain. Attackers demand a ransom from victims to restore access to their encrypted data or systems. The attackers aim to coerce victims into paying the ransom to regain their data or prevent its public release.
Impact
- Malware: The impact of malware can vary widely depending on its type and purpose. It might lead to data loss, identity theft, system crashes, unauthorized access, or other negative consequences.
- Ransomware: Ransomware directly impacts victims by denying them access to their files or systems. It can disrupt business operations, cause financial losses, and potentially lead to reputational damage if sensitive data is released.
Delivery
- Malware: Malware can be delivered through various means, such as infected email attachments, malicious websites, infected software downloads, USB drives, and more.
- Ransomware: Ransomware is often delivered through similar methods as other malware, but its effects are distinct due to the encryption of files or system lockout that follows.
Monetary Gain
- Malware: While some malware can be financially motivated (e.g., banking trojans), the monetary aspect is not as central to its operation as ransomware attacks.
- Ransomware: The primary motivation for ransomware attacks is monetary gain. Attackers demand payments in cryptocurrencies to make tracking transactions more difficult.
Conclusion
In summary, malware is a broader term encompassing various malicious software types. At the same time, ransomware is a specific subset of malware that focuses on encrypting data or locking systems to demand a ransom from victims.
Heimdal®’s Ransomware Encryption Protection
Here’s a quick rundown of what Ransomware Encryption Protection can do for your organization:
- Prevent data breaches by protecting your networks and endpoints against fraudulent encryption attempts;
- Eliminate downtimes caused by ransomware attacks;
- Reduce and eliminate post-ransomware impacts;
- Improve the detection capabilities of your current cybersecurity software;
- Increase conformity;
- Get comprehensive defense against zero-day vulnerabilities;
- Combine with any SIEM for improved detection of policy violations.
Ready to take it for a spin? Click here for a personalized demo.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








