Imagine you’re a burglar, preparing to rob a bank. Which scenario would you go for? Target a random employee with low-level access to the bank’s vaults or go straight to the person who holds the keys to the treasury?
This question shows why privileged accounts are so valuable and so vulnerable. Privileged accounts give users high-level access.
Misusing them can lead to critical system changes or access to sensitive data. These accounts include system administrators, C-suite executives, and IT support roles.
For hackers, privileged accounts are like a golden key to:
- access sensitive data
- bypass security protocols
- gain control over crucial systems
So, keeping privileged accounts safe is a priority for privileged access management strategies.
But before we dive into protecting them, let’s break down what privileged accounts are. Then we’ll move on to learning what are the main types of privileged accounts.
Key takeaways:
- hackers target privileged accounts to gain high-level rights in a system
- using just-in-time access helps prevent privilege creep
- domain-level admin accounts rank highest among the various types of privileged accounts
- automated privileged access management support System Administrators into applying pam best practices across large, complex infrastructures
What are privileged accounts?
Privileged accounts are user accounts with higher-than-normal permissions. Think of them as “super accounts” beyond regular user permissions.
Privileged users can:
- access, read, and edit sensitive data
- manage system configurations
- apply updates and install software, etc.
- set and change passwords on system devices
These accounts are crucial for managing and troubleshooting an organization’s IT infrastructure. Thus, they are prime targets for cyberattacks, which makes them challenging to manage.
Often, the hard part is knowing exactly what privileged accounts exist in the first place. What are their current rights and are they still necessary?
Inventorying privileged accounts can be a tedious, complex task. Yet, the best privileged access management solutions enable IT teams to audit privileged accounts automatically.
Privileged Account Types
Understanding the main privileged account types is the next step in learning how to protect them. Keep reading to learn:
- the three main super accounts categories
- what are their capabilities
- what are their key vulnerabilities
Privileged User Accounts
The first category of privileged accounts is the easiest to understand. User accounts belong to named employees in the organization. There are several types of user accounts, with varying levels of access and oversight.
Each type poses specific threats if hackers manage to seize them. Implementing the principle of least privilege for user accounts prevents or mitigates data breaches.
Heimdal's PAM solution makes enforcing the least privilege across your organization seamless and effective.
Implement Least Privilege with Ease!
Domain-Level Administrator Accounts
Domain-level administrators are the highest level of administrative account.
They usually have unrestricted rights and access to the entire IT infrastructure.
They are also known as ‘Admin’ in Windows and ‘Root’ accounts in Unix/ Linux environments.
Key vulnerability: If hackers compromise a domain-level account, they can take over the whole system.
It is best practice to restrict domain admin accounts to very few users. Use extra security measures, like jump servers, privileged access workstations, PAM tools, etc. to protect them.
Superuser Accounts
Superuser accounts have unrestricted access and control over a single system. They are one level below Admin accounts.
They have high-level rights like:
- changing system files
- installing software
- configuring the system
Generally, local system maintenance and administration personnel need this access level to perform.
Key vulnerability: If hackers gain superuser access, they can take over the system. Further on they can attempt privilege escalation to compromise an admin account.
Local Administrator Accounts
Local administrators have privileged rights over their own local devices. They have no authority over networks, systems, or domains. Instead, they can make changes to their own device operating system:
- install apps
- read, edit, and delete files
- adjust active directory details
Key vulnerability: Despite their limited privileges, local admin accounts are a risk, due to their ubiquity. Local privileges are a shortcut to approval processes for software installation and OS changes.
This makes them a key target. Hackers use them to attempt lateral movement through an IT environment and elevate their privileges. Most security experts recommend limiting or disabling local admin rights.
Emergency Accounts
Also known as ‘break glass’ accounts, emergency accounts get into action in special situations. IT teams use them to restore critical systems after an outage or in case of a cyberattack.
Generally, these accounts are disabled until they are needed. Access to them is restricted. When enabled, these privileged user accounts have high-level permissions.
Key vulnerability: Emergency accounts can bypass authentication and monitoring processes. This special feature allows them to offer quick responses in a crisis.
Hackers might target these accounts to get superuser or domain-level privileges.
Using emergency accounts during an attack might make a post-incident analysis more difficult. This depends on the specific auditing and monitoring processes they’re designed to work around.
Privileged Business Users
Privileged business users don’t have admin rights over any IT device or infrastructure. Instead, they need access to sensitive information, like customer or employee sensitive data.
HR teams and managers viewing employee salary data use these privileged accounts.
Key vulnerability: Privileged business users are popular entry points for hackers. Their cybersecurity awareness is often scarce.
Low-level phishing scams and brute-force attacks often break their defense and cause data breaches.
Also, these users connect with many other accounts and their main focus is completing specific tasks. Privilege creep is another common vulnerability of privileged business users’ accounts.

- Mikkel Pederson, Head of Global Sales Enablement, Heimdal®
Privileged Service Accounts
Privileged access is now required for a whole range of machine identities. This could include, for example, IoT devices, Robotic Process Automation (RPA) processes, or system configurations.
IT teams often lack complete visibility over the number of privileged service accounts. Neither are they aware of what permissions they hold.
Thus, enforcing the least privilege principle or password rotation is challenging.
Privileged service accounts use plain text credentials, hard-coded into the service or application’s source code.
Developers use this method to ease friction in the machine-to-machine processes. Hackers exploit this malpractice to compromise credentials, once they get access to the source code.
Here’s an easier and safer way to streamline privileged service access. Heimdal’s Privileged Account and Session Management solution offers credential vaulting, among others.
Read more about the tool’s capabilities and ask for a personalized demo here.
Application Account
These provide applications access to other apps, databases, or running scripts. Some applications need access to sensitive assets to complete their tasks. They may need to apply updates, deploy software, or configure changes.
Service Accounts
Service accounts interact specifically with the operating system in an IT environment.
In Unix and Linux environments, they are called iNet or InetD accounts. System accounts are another, similar example – generally created by operating systems during installation.
Examples of privileged tasks include:
- installing applications, updates, and patches
- running database backups
- cleaning up log files
Active Directory/ Domain Service Accounts
Domain service accounts also help machine identities interact with the operating system. They can access databases, APIs, or other sensitive endpoints.
Key vulnerability: Changing the password to these accounts can lead to complications.
That’s why organizations rarely implement effective password rotation on these accounts. Hard-coded credentials, another major security risk, are often used as a shortcut.
Best practices for privileged user accounts
Now we’ve got an idea of the main privileged account types. Let’s explore some PAM best practices that keep them safe.
Remove standing privileges
Standing privileges exist when a single account (user or service) has ‘always on’ access. Standing privileges are particularly dangerous on domain-level and superuser accounts.
If they’re hacked, nothing is stopping the attacker from taking over the infrastructure.
Instead, allow “conditional” or “just-in-time” permissions. Just-in-time access grants permission for a specific task and revokes it once it’s complete.
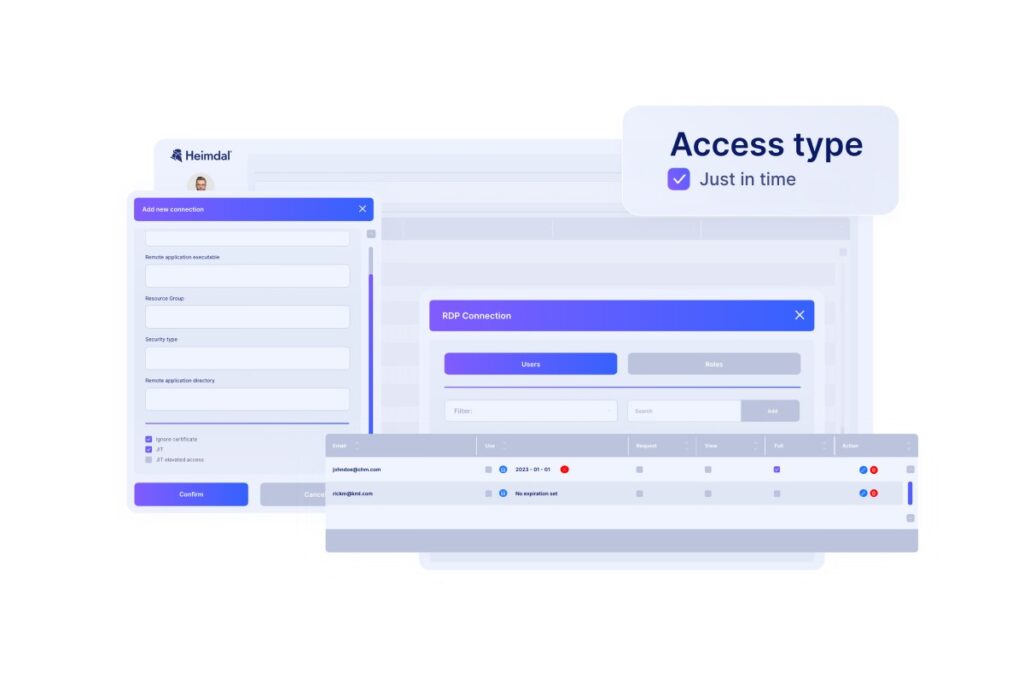
Conduct regular privilege audits
Regular audits of privileges prevent ‘privilege creep’. Users may accumulate access permissions over time if no one revokes unnecessary privileges.
Imagine an employee changes jobs and moves from Accounting to Human Resources. You should revoke their access rights to databases in Accounting and grant them the rights they need for HR-related tasks.
Not revoking old, unnecessary rights expands the attack surface. If hackers compromise such a privileged user account, they’ll damage both the Accounting and the HR databases.
Top PAM security tools automatically identify all the privileged accounts in a network. It’s the only effective way to map out the entire scope of privileged accounts.
After the inventory, enforce the least privilege to remove unnecessary permissions. Repeat the audit regularly to avoid the risk of privilege creep.

- Mikkel Pederson, Head of Global Sales Enablement, Heimdal®
Eliminate superuser accounts and distribute privileges
Where possible, you should eliminate superuser and domain-level privileged accounts. Their having full control over a network or system makes them a critical entry point for hackers.
Instead, separate these elevated privileges and distribute them to different accounts. Thus, none will have complete control. Separation of privileges is a common PAM best practice.
Enable MFA for all privileged accounts
The more defense layers you create for hackers to pass through, the less likely it is that they’ll breach your system.
Enabling multi-factor authentication for all privileged accounts protects them against compromised credentials.
MFA can save the day in case some privileged users use the same password or get tricked by phishing scams.
Yes, multi-factor authentication isn’t a silver bullet. Hackers can use SIM swap scams, for instance, to gain access to an employee’s phone.
But with the right technology, MFA is an easy protection to put in place and a difficult one for hackers to get around.
Remove hard-coded credentials
Hard-coded credentials also create a key vulnerability. Unfortunately, they are still common in service accounts.
If hackers can view plain text passwords from source code, gaining access becomes a piece of cake.
Use the most recent cloud PAM solutions, to automatically identify these vulnerabilities. Replace hard-coded credentials with an alternative:
- a secure password vault
- digital token-based authentication
Safeguard privileged accounts with Heimdal®

The challenge with modern, cloud-based IT environments comes down to complexity and scale.
The high number of endpoints across a diverse range of systems makes it impossible for IT teams to manage manually.
Automated, cloud-based PAM solutions like Heimdal®’s enable them to enforce the best security measures.
Among other capabilities, Heimdal’s Privileged Account and Session Management offers:
Total privilege management
This function lets you define and manage role-based access control and delegation policies with ease.
Just-in-time privileged access
Allows your admins to grant temporary enhanced privileged access to users only when necessary.
Audit and reporting
Enables you to generate comprehensive reports and monitor privileged access/session activities.
It helps prove adherence to local or global regulatory standards. In case of data breaches, this feature offers trackability.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








