Contents:
It’s no secret that the expansion of the Internet benefitted the entire world in one way or another. Unfortunately, that also includes cybercrime. The digital world is ripe with opportunities for malicious activities, and there are individuals out there waiting to seize each one of them.
But what is cybercrime? And, more importantly, how can we collectively prevent it? Keep reading to find out.
What is Cybercrime?
Cybercrime is a type of criminal activity that involves the use of computers and the Internet. It represents the perpetuation of previous criminal activities in the digital age, as well as novel illicit behaviors that became possible with the advance of technology.
What this means is that the type of criminal behavior associated with cybercrime has existed long before computers were invented. However, the apparition of advanced electronic devices with the potential to connect to the Internet and reach anyone and anywhere in the world has exacerbated these wrongdoings.
Types of Cybercrime
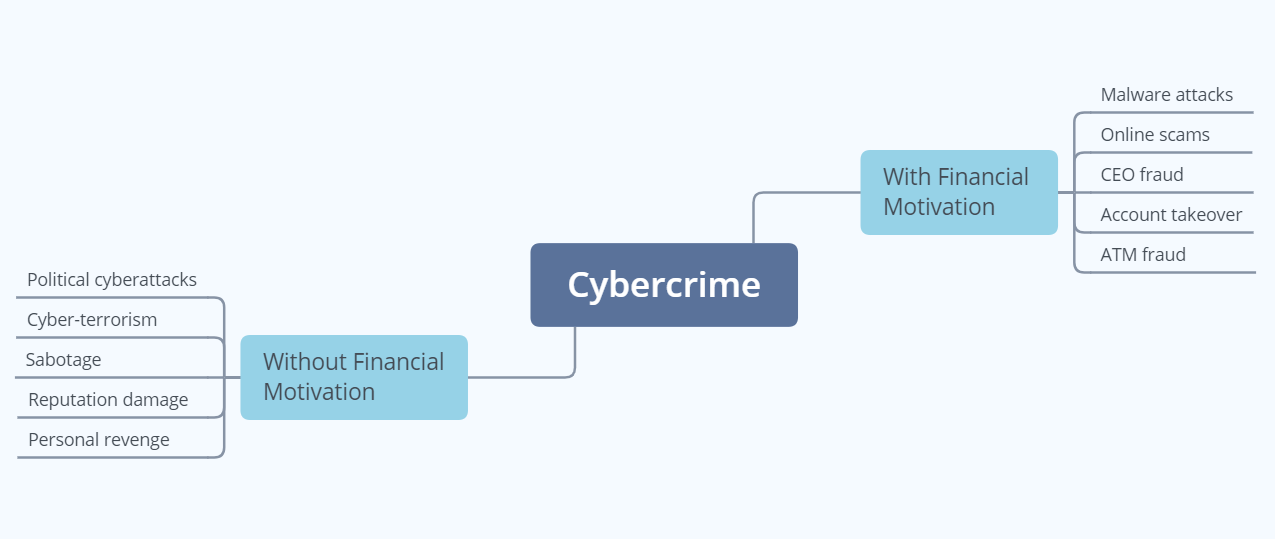
Cybercrime is split into two main categories according to the financial motivation behind it or lack thereof. While some malicious actors are in it for the cash, others have other incentives driving their actions. Below, you can find a list of the most widespread instances of cybercrime depending on whether they have a monetary component or not.
a. With Financial Motivation
When cybercrime has a financial motivation behind it, it means that hackers have a clear monetary gain following their actions. According to the Verizon Data Breach Investigations Report, a whopping 95% of all cyberattacks are driven by money. There are five subtypes to consider here:
- Malware attacks
- Online scams
- CEO fraud
- Account takeover fraud
- ATM fraud
Malware attacks on companies, especially those using ransomware, are the most widespread type of financially motivated cybercrime out there. A study led by Atlas VPN uncovered that 81% of all the financially motivated cyberattacks that took place in 2020 were perpetrated via ransomware.
Unfortunately, the Coronavirus pandemic exacerbated this hazard even more. According to the Ponemon Institute’s 2020 global risk report titled Cybersecurity in the Remote Work Era, the effectiveness of IT security in worldwide organizations dropped by 27% during this period.
Online scams are another common type of financially motivated cybercrime to watch out for, as they target enterprises and home users alike. Catfishing, hijacked Facebook profiles, or even the infamous Nigerian prince method are just a few examples.
CEO fraud is another insidious type of cyber fraud where hackers pose as figures of authority in a company to demand illicit money transfers. On the other end of the spectrum, account takeover fraud implies identity theft and the misuse of unlawfully obtained credentials to carry out fraudulent transactions.
Finally, ATM fraud might not seem like a cybercrime at first, but offenders use computers and other digital means to carry it out. Over time, they have developed methods to intercept both the user’s PIN and the data on the card’s magnetic strip. For this reason, it is still very lucrative for malicious actors to attempt it.
b. Without Financial Motivation
While it is true that the vast majority of cybercrime is driven by monetary gain, 5% of it has no financial motivation whatsoever. However, this doesn’t mean that its intent isn’t malicious. In fact, it might be even more so. This category contains the following five subtypes:
- Political cyberattacks
- Cyber-terrorism
- Sabotage
- Reputation damage
- Personal revenge
The affairs of the state are an important driving force in cybercrime, and the stakes are higher than money. The Center for Strategic International Studies (CSIS) lists seven politically motivated cyberattacks in the last year alone. Malicious actors with this intent are mainly located in Russia, China, and Iran nowadays.
Closely linked to political cyberattacks is the matter of cyber-terrorism. The term refers to a type of cybercrime that makes use of computers to intimidate a country’s civilian population and influence the policy-making of its government.
Two other types of cybercrime that are intimately related are sabotage and reputation damage. While the former implies the damage of assets, the latter can take multiple forms. However, the end goal is the same, and it consists of tarnishing the name and standing of an organization.
Last, but certainly not least, personal revenge is another type of cybercrime that targets both enterprise or home users. Research published by Statista in 2021 showed that India alone registered nearly 1,200 cybercrime cases motivated by retaliation in one year.
What Methods Do Cybercriminals Use?
When it comes to attacking enterprises for financial gain, breaching organizations with ulterior motives, or even harassing home users for personal revenge, hackers have a wide array of tools under their belt. Examples include, but are not limited to:
- Social engineering
- Malicious code
- Denial of service attacks
- Credential theft
- Impersonation
- Online stalking
- Traffic sniffing
- Etc.
Countermeasures That Will Enhance Your Security
Knowing what the methods cybercriminals use to get to you are is the first step. The next focal point on your agenda should be prevention. Here are the three pillars of a strong defense that you need to implement as soon as possible.
#1 Secure Accounts
In terms of cybercrime prevention, what you first need to do is safeguard your organization against phishing attacks and implement an email security solution. Traditional email services such as Gmail, Outlook, or Yahoo! Mail already come with a few layers of defense that will detect malicious activity.
Credential theft is another threat you should consider in the prevention of cybercrime. Besides infecting the devices in your corporate network with malware, hackers are also looking to get their hands on as many login credentials as possible. This is a lucrative business opportunity for them, as they can further use them to steal your data or even sell them on the Dark Web. The shadiest corners of the Internet are swarming with password databases that anyone can purchase.
This is why your company needs a strong password policy. Credentials that contain both uppercase and lowercase letters, as well as alphanumeric characters are harder to crack. Create strict guidelines for this, and include cybersecurity tips on how often they should be changed as well.
Another way to make sure your accounts are bulletproof is through multi-factor authentication. The term refers to a verification system that sees users provide at least two if not more pieces of evidence that they are the owners of an account or have lawful access to it
The first step in a multi-factor authentication system is a standard one – you put in your username or email address, then your password. Additional layers of security then follow. Depending on the platform and method, you might be required to:
- Provide a biometric authentication vector such as facial recognition or fingerprint scanning.
- Use a verified mobile device like a smartphone or tablet to confirm the login attempt.
- Insert an additional PIN code that you get via email or text, etc.
#2 Cybersecurity Education
Other than protective tools and policies, your employees can be a valuable asset for your company in the prevention of cybercrime. Nonetheless, for them to be able to help, you must provide them with the appropriate cybersecurity education on issues that might pose a concern for your enterprise and industry. Here are but a few possible topics:
- how to recognize social engineering tactics,
- how to spot a malicious attachment or link,
- how to identify a cyberattack,
- how to create a strong password,
- and how to browse securely.
These are just a starting point. The field of cybersecurity is a lot vaster than these five pointers, which is why I recommend hiring an expert to hold these training sessions if you are not qualified to do it. Investing in your staff will pay off tenfold in the long run when they won’t fall victim to clever cyberattacks.
#3 Protected Systems
Having all your bases covered for the prevention of cybercrime requires a complete endpoint prevention, detection, and response solution. The particularity of this approach is that it takes protection one step beyond traditional EDR software, adding advanced threat hunting capabilities to your company network. This helps you prevent even the most cunning hackers from taking over your sensitive data and accounts.
Our Heimdal™ EPDR offering consists of five modules:
- DNS traffic filtering
- Artificial intelligence
- Patch management
- Privileged access management
- Antivirus with firewall
By their powers combined, these state-of-the-art technologies not only detect and respond to cyberattacks but actively prevent them as well. Heimdal™ EPDR closes vulnerabilities in your system and keeps detailed lists of both known and unknown threats that keep your digital assets safe from cyber-harm.
Wrapping Up…
Cybercrime is a multi-faceted affair. Most attacks are financially motivated, but some are not. Regardless of their target, hackers have a nefarious purpose in mind and will stop at no lengths to fulfill it.
For this reason, prevention comes with several layers of defense that consist of both technologies and individuals. Having the appropriate cybersecurity tools under your belt should always be accompanied by relevant policies and cybersecurity training for your employees.
Heimdal™ Security can help you with the former, so don’t hesitate to reach out at sales.inquiries@heimdalsecurity.com for more info.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











