Contents:
After the XSS Russian-speaking hacking forum announced last week it had completely banned ransomware sales, ransomware rental, and ransomware affiliate programs on their platform, it’s now Exploit’s turn to make the same decision.
Exploit is an important cybercrime forum where ransomware hackers usually hire affiliates and advertise their Ransomware-as-a-Service (RaaS) services.
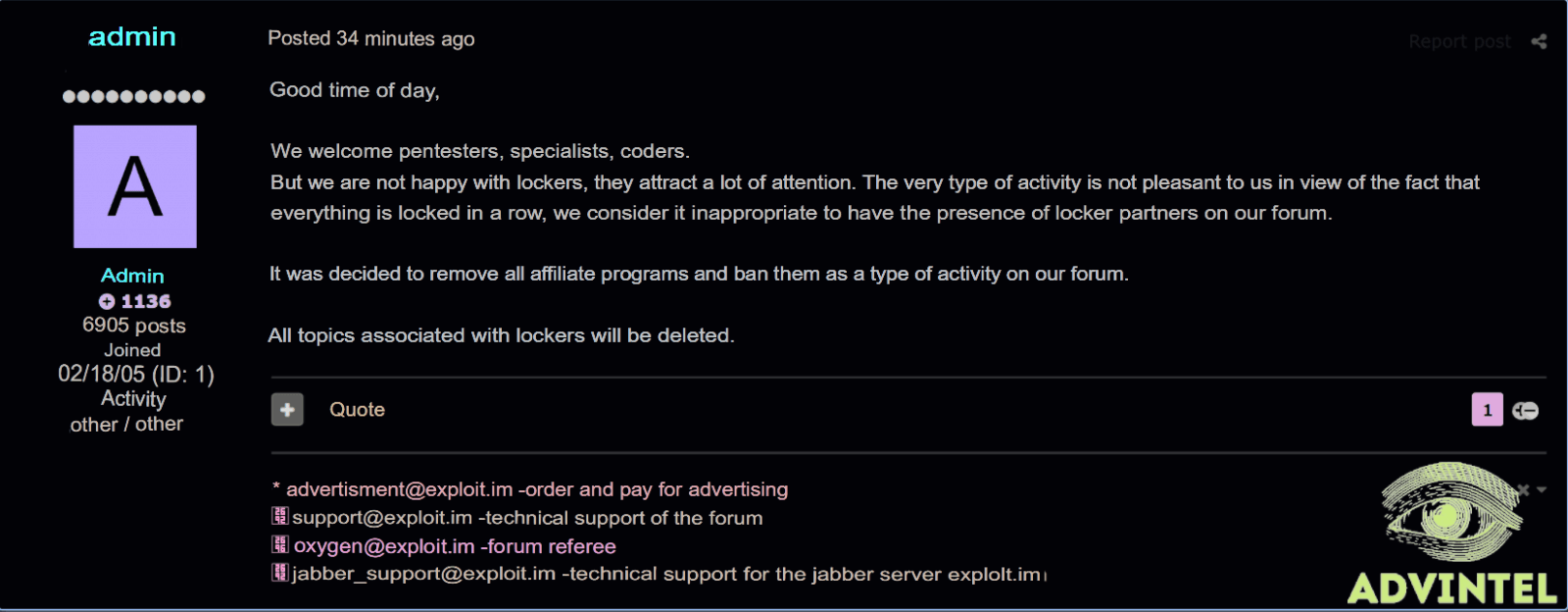
Exploit stated that the decision of banning and removing ransomware ads was taken because ransomware groups attacking targets randomly draw “a lot of attention.”
And not only that, but the forum also said that all topics associated with ransomware activity and affiliate programs will be removed.
The XSS decision that banned them from the forums wasn’t well-received by the ransomware gangs who immediately announced that their operations will move to other forums. For example, REvil ransomware gang said it will start using Exploit.
Too bad that Exploit has also forbidden ransomware subjects in order to avoid undesired observation from US law enforcement.
We will see in what manner and whether ransomware hackers will continue to advertise their activities and employ new affiliates now that more and more cybercrime forums are taking their operations off their platforms.
With the rise of ransomware gangs, such as REvil, LockBit, DarkSide, Netwalker, Nefilim, have been using the two forums to recruit new partners to their operation, leading to the forums feeling pressured into making these decisions.
Following the DarkSide ransomware’s attack on Colonial Pipeline that damaged the US fuel pipeline’s operation, the two forums decided they don’t want the attention of the security researchers and US law enforcement.
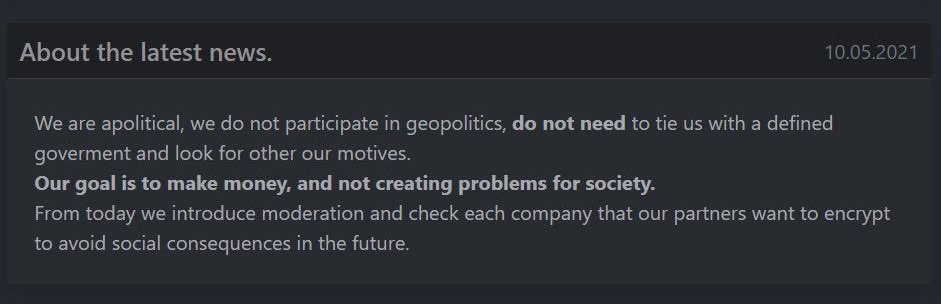
In a “press release” following the attack, the DarkSide ransomware group declared that they are not interested in politics and that they will start making a careful and critical examination of all targets before assaults.
Colonial Pipeline paid the hackers nearly $5 million in cryptocurrency in return for a decryption key to restore its systems. Since the tool was too slow, the pipeline operator used its backups to restore the systems.
As stated by UNKN, a bad actor who claims to represent a rivaling hacking operation, at the request of US law enforcement, DarkSide RaaS activity has stopped after losing entrance to unrestricted data leak site, payment servers, and CDN servers. Their cryptocurrency was also moved to an unknown wallet.
DarkSide gang stated they decided to stop their operation because of the pressure from the US. Following that, new limitations on targets that can be encrypted by partners were presented.
The new rules say that REvil partners need to acquire authorization before they target an enterprise and that health care organizations and educational institutions are forbidden. It is also prohibited to work in the gov-sector of any country.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










