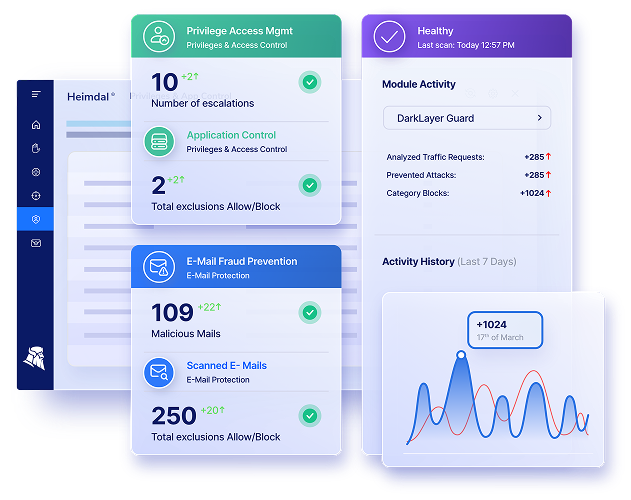
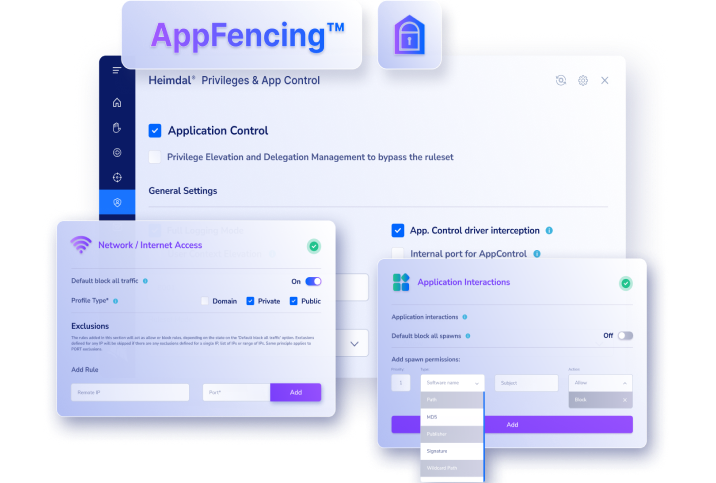
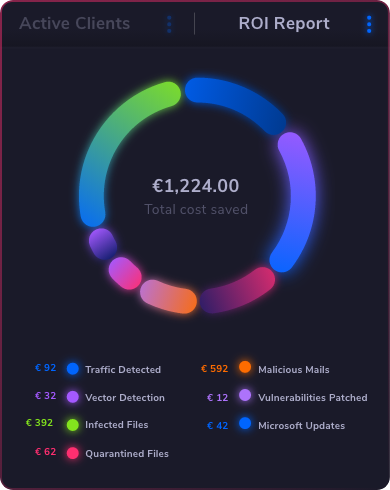
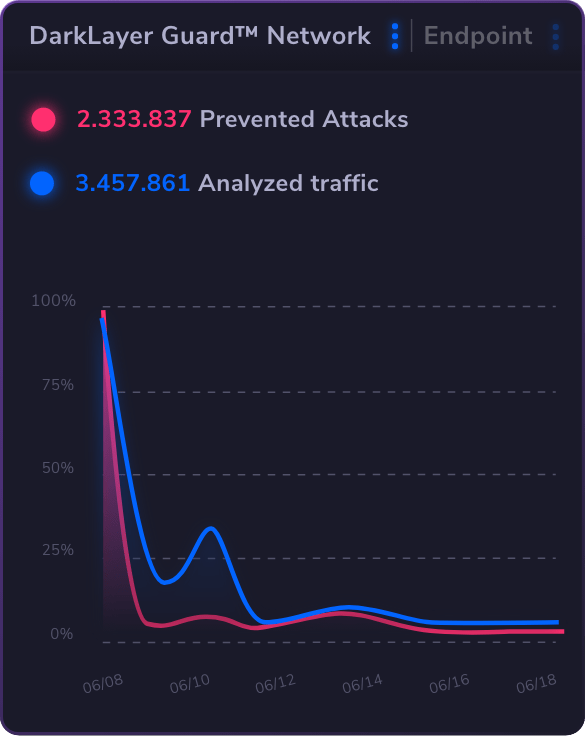
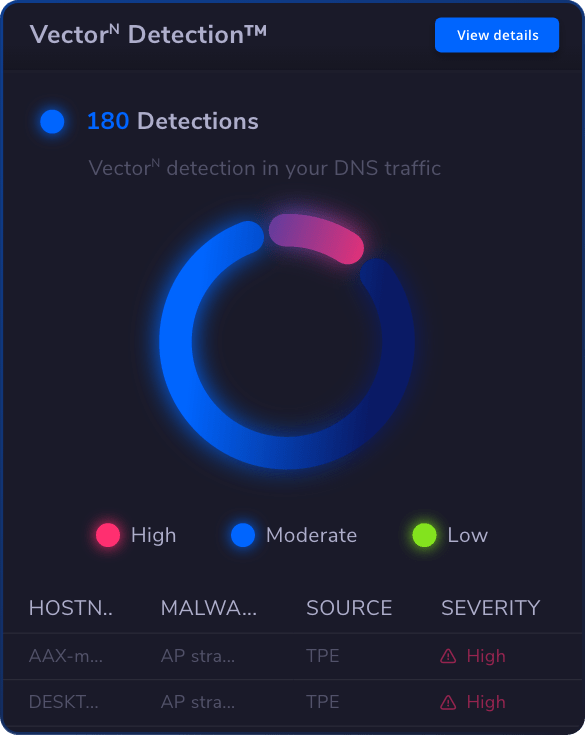
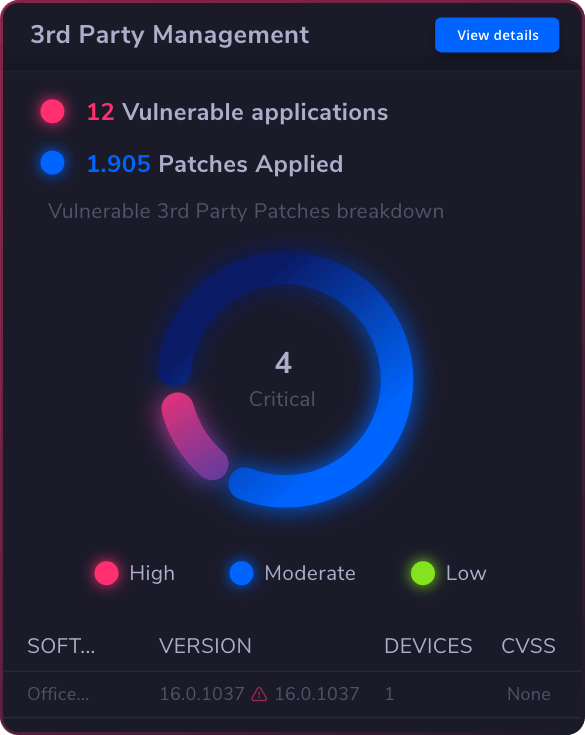
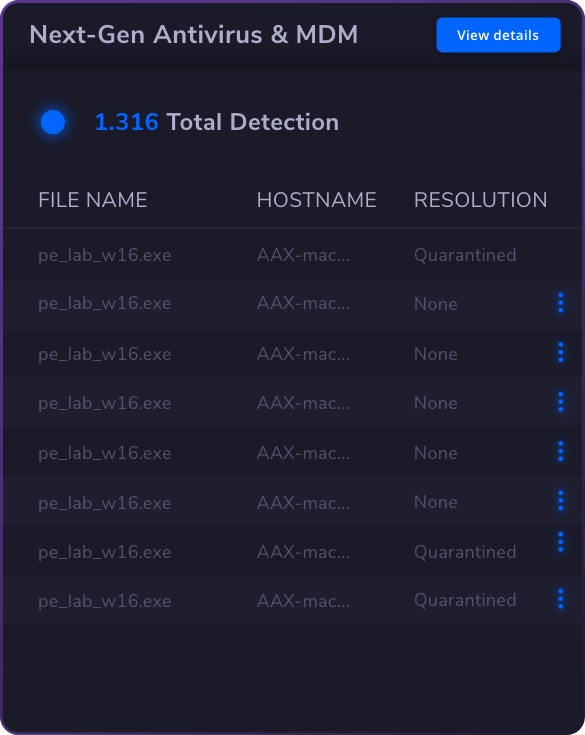
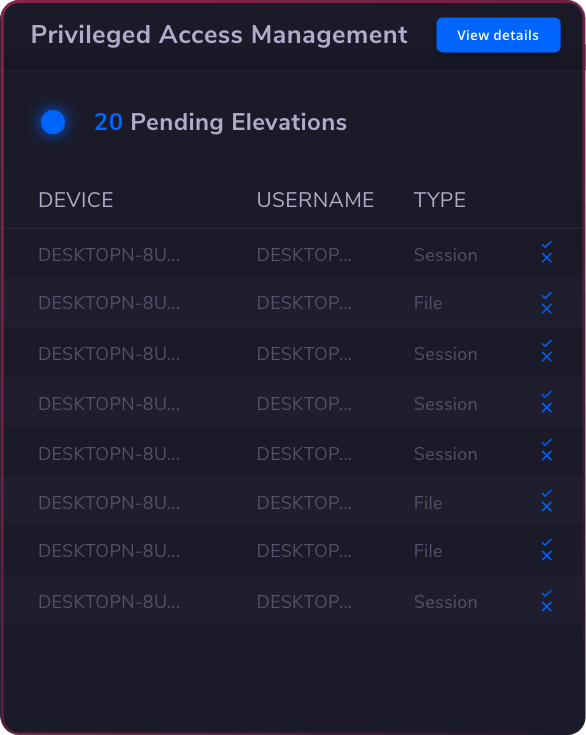
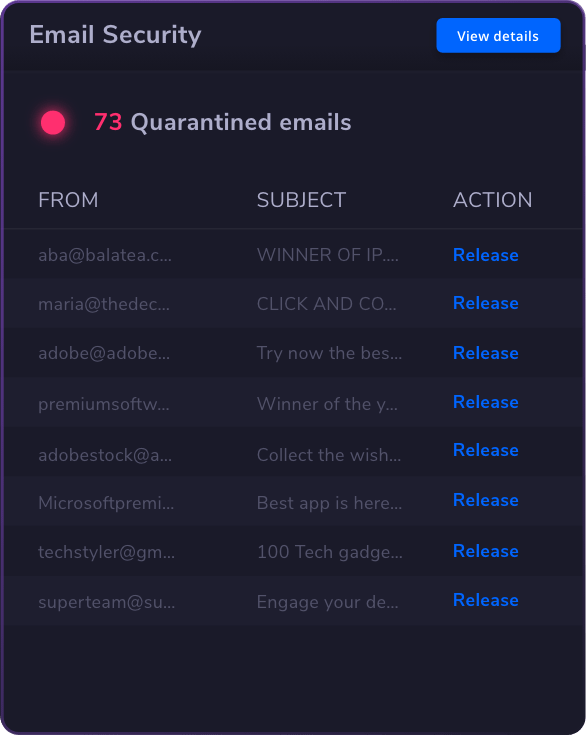
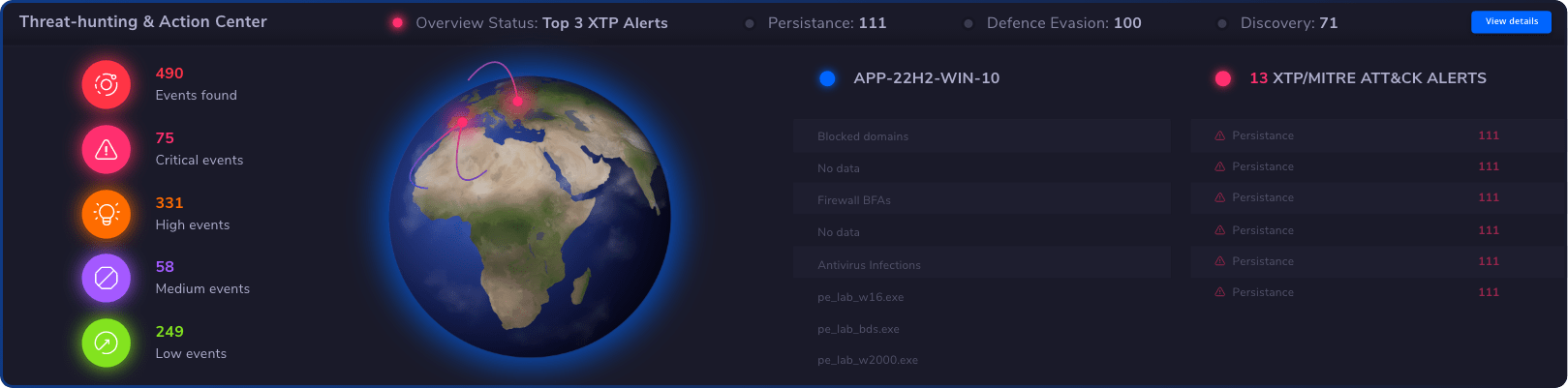
The best privileged access management solution is one that offers comprehensive features tailored to your organization’s needs. Look for software solutions that provide strong access control, robust session management, and effective secrets management.
A well-rounded PAM solution should also support privileged identity management and integrate seamlessly with your existing identity and access management infrastructure.
Consider Heimdal’s privileged access management solution, which excels in these areas with its user-friendly interface, advanced security protocols, and seamless integration capabilities, ensuring your organization is protected while simplifying access processes.













 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security