In 2025, cyber attackers increasingly target identity and access points, not just infrastructure. Mismanaged credentials, excessive privileges, and orphaned accounts remain among the top causes of data breaches, especially with remote and hybrid work models in full swing.
To effectively reduce your organization’s attack surface and uphold regulatory compliance (NIS2, ISO 27001, GDPR), you need to understand and implement the trifecta: PIM, PAM, and IAM.
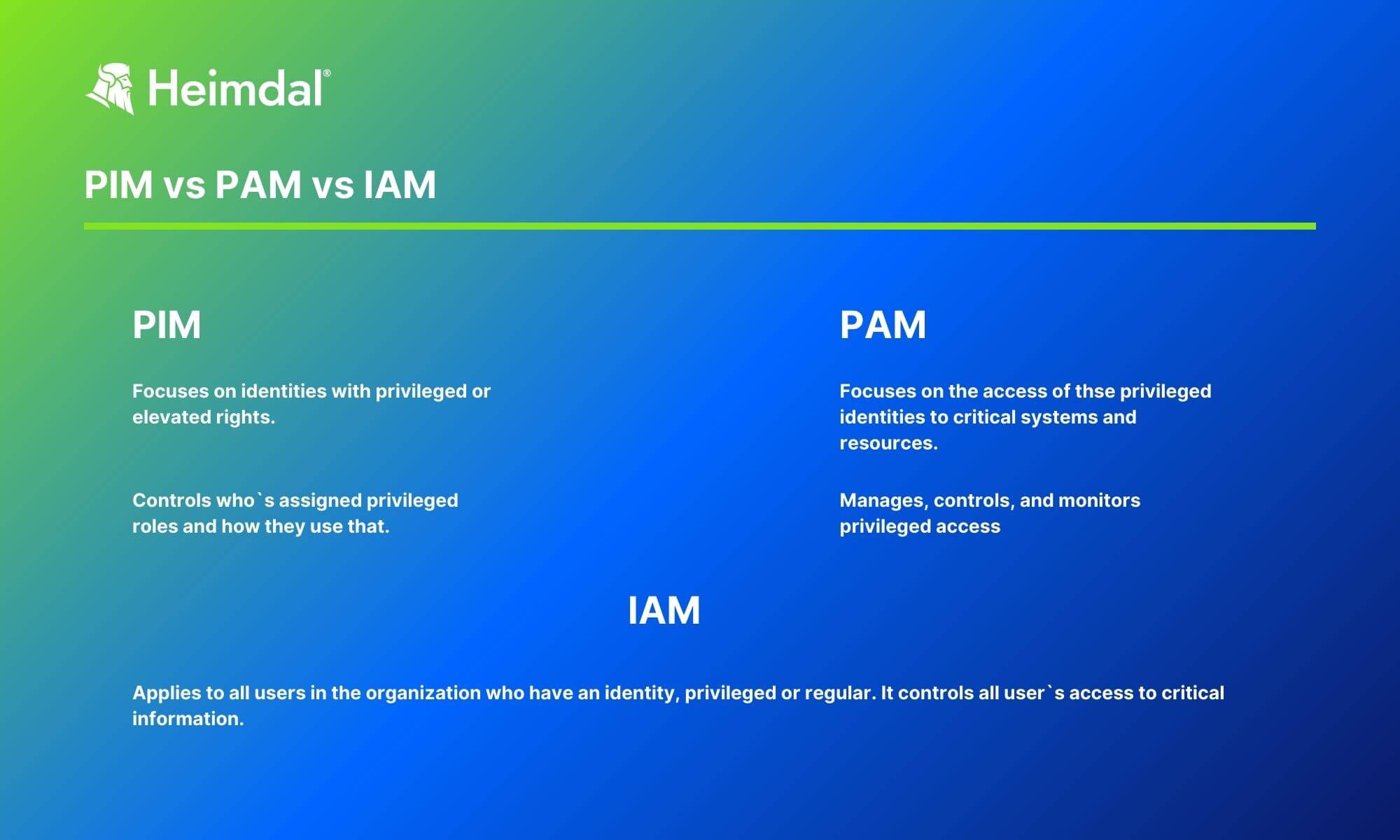
PIM vs PAM vs IAM are three distinct systems that cover different areas of safeguarding privileged access in an organization.
- PIM: Privileged Identity Management
- PAM: Privileged Access Management
- IAM: Identity Access Management
All three are crucial for your organization’s safety.
They’re built around the concept of granting specific rights to user groups.
Privileged Identity Management and Privileged Access Management are subsets of Identity Access Management (IAM).
PIM vs PAM vs IAM Explained
PIM, PAM, and IAM are acronyms that are sometimes used interchangeably, although they shouldn`t be.
These concepts reflect numerous security aspects that function in tandem to safeguard an organization’s data and systems.
Below you can see a comparison of these terms.
✅ Note: PIM and PAM are both part of IAM, but serve different scopes and use cases.
Each of these solutions has its own benefits that can be leveraged to help organizations better manage their identities.
- PIM solutions help organizations to better control and manage user privileges. By granularly controlling which users have access to which resources, PIM solutions help preventing unauthorized access. Thus, they reduce the risk of data breaches. Inside IAM, PIM focuses most on the authentication process.
- PIM handles the lifecycle of privileged accounts: their creation, governance, and deactivation.
- PIM supports: Compliance with frameworks like NIST AC-6; visibility into who can access what, when, and why; risk reduction by limiting identity sprawl.
Additionally, PIM solutions can help increase productivity.
A good PIM system makes it easier for authorized users to access the resources they need.
Privileged Identity Management is a subset of Privileged Access Management.
- PAM solutions focus on “how” rather than “who”, as opposed to PIM. Inside IAM, PIM focuses rather on the authorization process. PAM solutions set, monitor and audit how privileged accounts use their privileged access rights.
-
Unlike PIM, PAM tools actively control sessions and automate privilege elevation workflows, ensuring that access to sensitive resources is tightly guarded and context-aware.
PAM adds extra layers of security where they matter most.
By monitoring and controlling the use of administrator accounts, for example, it prevents abuse.
- IAM solutions offer the most comprehensive approach to identity management in general. IAM governs the access of all kinds of users to all the data and systems they need. While it includes PIM and PAM, it also provides other features, like identity lifecycle management (ILM) and identity federation.
- IAM is the umbrella that governs all user access, not just privileged users. It ensures that every identity (human or machine) has appropriate access to resources across your enterprise environment.
- IAM systems are foundational to Zero Trust architectures, where no user is inherently trusted, and every request is verified.
PIM
Oxford Computer Training defines Privileged Identity Management as follows:

- ,
PIM also monitors and protects superuser accounts. A superuser is an account with privileges well above that of regular user accounts.
This type of network identity is typically allocated to system or database administrators. Superuser accounts have elevated privileges.
If hackers manage to gain access to such an account, they can bypass the internal restrictions of a network.
These accounts need to be carefully managed and monitored, with PIM procedures and systems being set up to protect an enterprise’s networks from exploitation.
Here are the main points you can follow to implement Privileged Identity Management in your organization:
- Identify and keep track of all superuser accounts.
- Define how superuser accounts will be managed and what their corresponding users can and can’t do.
- Set up procedures and deploy tools for superuser account management.
In short, Privileged Identity Management is the most efficient approach for the organization-wide management of superuser accounts.
C-level company members and senior management may also have admin rights and access to classified information.
To prevent any compromise, certain privileges and access require close supervision and appropriate controls.
PIM guarantees a specific distribution of identity and rights for each user, ensuring that they can only access data under their privilege boundaries, and only perform certain actions.
PAM
What does PAM stand for – Privileged Account Management or Privileged Access Management?
Well, this is the acronym used for both terms, but keep in mind these are not exactly synonyms.
Privileged Account Management is part of Identity and Access Management (short for IAM, which I will explain a bit later), focused on safeguarding an organization’s privileged accounts.
On the other hand, Privileged Access Management includes all security strategies and tools that enable organizations to manage elevated access and approvals for users, accounts, applications, and networks.
In a nutshell, PAM lets companies limit their attack surface by granting a certain level of privileged access, thus helping them avoid and minimize the potential harm that may result from external or internal threats.
Privileged Access Management requires multiple tactics, with the key purpose of upholding the Principle of Least Privilege, described as restricting access rights and permissions to the bare minimum required for normal, daily operations of users, programs, systems, endpoints, and computational processes.
The PAM field falls under IAM, where it deals with the authorization processes. PAM enables organizations to gain visibility and easily manage all users` privileges.
To better understand how to implement PAM in your company, I recommend you check out the following articles:
IAM
Identity and Access Management recognizes the need to enable adequate access to services and to satisfy stringent regulatory required standards.
IAM is a vital endeavor in every organization, requiring technological competence and a high-level understanding and overview of the business.
Here’s how Gartner defines Identity and Access Management:

- ,
Basically, PAM offers more granular control, monitoring, and auditing of privileged accounts and sessions.
On the other hand, IAM checks all users` identities to confirm that a certain user has the right access at the right time.
When implementing Identity and Access Management, these are the steps you should follow:
- Appoint identity as one of your main protections.
- Label access rights, find unnecessary privileges, accounts, and irrelevant user groups.
- Conduct a risk evaluation of corporate applications and networks to start building your IAM project on a solid foundation.
- Enforce a strong password policy.
- Implement the Principle of Least Privilege and the Zero Trust Model.
How Can Heimdal® Help?
One of the main concerns within the PAM area refers to the large volume of elevation requests coming from users who need elevated rights to complete certain tasks.
To end this hassle, Heimdal has come up with a cutting-edge Privileged Access Management solution that helps organizations handle user rights safe and effectively.
As it’s the only tool to auto-deny/de-escalate admin rights on infected machines – if you add the Application Control module into the mix -, Heimdal`s PAM solution substantially your organization security posture.
System admins waste 30% of their time manually managing user rights for installations.
Heimdal Privileged Access Management
Wrapping Up…
As the network perimeter lines are now blurring due to the increasing popularity of remote work, network security alone may not suffice.
One of the potential risks for all companies are unmanaged accounts, which means that all users must always be recognizable and permanently monitored for adequate rights.
Lack of access controls will increase threats and can lead to the abuse of highly sensitive data.
For instance, an ex-employee may still have access to your confidential data, an attacker may compromise an account and misuse it, or insider threats could exist in your company.
This is where PIM, PAM, and IAM come into play, protecting your organization against various types of identity management dangers.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








