Contents:
Glupteba is a backdoor trojan that can be downloaded via computer networks to infiltrate your device on the Internet and steal confidential information.
The botnet operator can then deploy additional modules, such as exploiting vulnerabilities in various devices to steal sensitive data from your network. Glupteba has been involved with malware, including stealing sensitive data from internet-connected routers and cable modems.
Nearly a year after Glupteba malware was disrupted, the botnet has resurfaced and is now spreading across devices.
In December 2021, after years of mounting complaints and proof of abuse, Google gained control of the botnet that constantly disrupted content and compromised web security.
In addition, a Russian operator was arrested for providing hosting and maintenance support for the botnet on behalf of two other operators.
Analysis of the pattern of food poisoning incidents and associated blockchain transactions, TLS certificate registrations, and reverse engineering Glupteba samples reveals a new, large-scale campaign.
Hidden in the Blockchain
Glupteba is a malicious software program that secretly installs when users browse unknown or untrusted websites. It then steals user credentials and cookies and deploys proxies on their Windows systems and other IoT devices.
These residential proxies are later sold to other cybercriminals.
Malware is distributed through malvertising on pay-per-install (PPI) networks and traffic distribution systems (TDS). These include websites disguised as free software, videos, and movies that push installers to unsuspecting viewers.
Glupteba can remain undetectable even when your command and control servers are disrupted by fake messages and distributed denial of service attacks.
The client’s botnet retrieves the C2 server address using a discover function to find Bitcoin wallet servers, collects raw transactions, and looks for an AES-encrypted address.
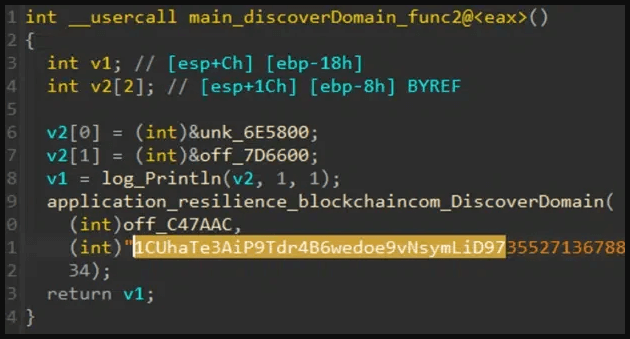
Glupteba has employed a spam-fighting strategy for several years to ensure your content’s safety and security. This one-of-a-kind approach is what allows Glupteba to remain resilient against takedowns.
That’s because blockchain transactions cannot be erased, and C2 address takedown efforts have a limited impact on the botnet.
Law enforcement cannot hack the controller address and plant payloads with the private key. They can’t happen with your bitcoin botnet.
The only downside is that the Bitcoin blockchain is public, and you can track transactions to acquire information.
Glupteba, an Old Enemy Returns
Nozomi reports that Glupteba continues to use the blockchain, in the same way today, so its analysts scanned the entire blockchain to unearth hidden C2 domains.
The effort to create a decryption tool for the malware that caused this crypto exchange hack was immense. It involved scouring 1,500 Glupteba sample files uploaded to VirusTotal and decrypting transaction payload data using keys it struck against the malware’s program code.
To uncover more information about Glupteba’s infrastructure, Nozomi used passive DNS records, examined TLS certificates, and more.
The Nozomi investigation identified 15 Bitcoin addresses used in four Glupteba campaigns. One of these campaigns started six months after Google’s disruption and is still ongoing.
Botnets use more addresses than past operations. They’re resilient because they have more Bitcoin addresses.
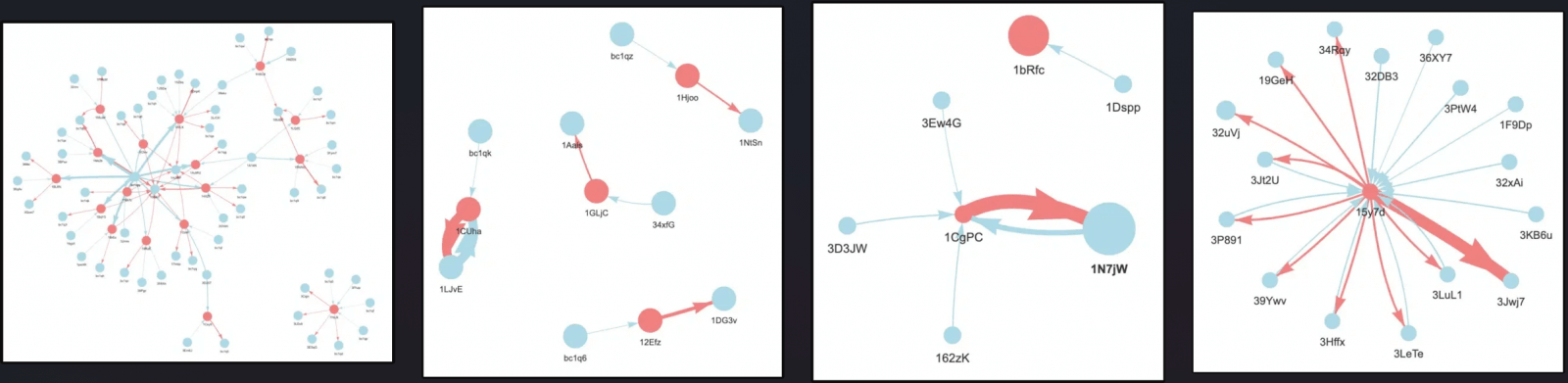
The number of TOR hidden services used as C2 servers has increased tenfold since the 2021 campaign. After being identified, these servers were preemptively destroyed to minimize their risk.
The most recent transaction on this PO Box was registered on November 8, 2022.
Passive DNS data indicated that noizomi.jp was recently registered on November 22, 2022. An analysis of the passive DNS information discovered this fact.
According to the information we have gathered from our sources, the Glupteba botnet has returned, and it’s much more massive than before, possibly even more resilient. It also set up many fallback addresses to resist takedowns by researchers or law enforcement.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








