When it comes to threat detection, it’s important to get the right tools for the job. Unfortunately, that can be easier said than done.
Whether it’s a SIEM, EDR, XDR, MDR, or any of a whole other range of confusing and overlapping terms – there are a lot of products on the market.
EDR and SIEM solutions are two of the most common. And to add to the confusion, some companies will need both products, some need one or the other, and others neither.
Sounds simple, right? Here is everything you need to know about EDR vs. SIEM.
EDR vs. SIEM: Key Differences in a Nutshell
Endpoint Detection And Response (EDR)
EDR solutions focus on identifying threats and vulnerabilities on specific devices and endpoints, like desktops, tablets, servers, and more.
Unlike SIEMs, they aren’t designed to provide network-wide visibility.
EDRs are often used alongside SIEM products to provide greater protection against threats like malware injection.
Read more: EDR Implementation: Essential Features, Considerations, and Best Practices
Security Information And Event Management (SIEM)
SIEM products offer a birds’ eye view over almost any action a user can take within your IT environment.
Using anomaly analysis and other measures, they aim to identify security events like suspicious login attempts, lateral movement, and more.
Read more: Security Information and Event Management (SIEM). What It Is and How It Works
SIEM + EDR - Get the Best of Both Worlds with Heimdal's Unified Threat Hunting and Action Center
What is SIEM? Intro And Key Features
SIEM: How it Works?
SIEM products are built on the concept of a security ‘event’. This can encompass almost anything that happens in an IT environment, including:
- Signing in to a device or app;
- Sending an email;
- Clicking on a file;
- Opening a webpage.
Each of these events creates log files, which are the principal datasets that SIEMs analyze.
They aim to identify suspicious activity, generally using machine learning, AI, and anomaly detection algorithms.
These insights are then correlated into a unified dashboard, which gives security analysts visibility over events across:
- Servers;
- Network devices;
- Databases;
- Routers;
- Switches;
- Firewalls;
- Proxies.
SIEM Benefits And Key Features:
Like all security solutions, SIEMs can be quite a broad and ill-defined category, with functionality varying between providers.

Nonetheless, there is a baseline of core features you can expect to find across most of the industry’s leading tools:
- Event collection and analysis: SIEMs analyze and record log file information from across the IT environment, in order to analyze user behavior and identify suspicious activity.
- Dashboard visualization: Visual representations of events and data are also provided through charts, graphs, and heatmaps. This lets security teams view events, understand trends, and quickly identify the most critical updates.
- Alerting and notifications: SIEMs can notify IT teams when particular threats or anomalies are detected, meaning you don’t have to constantly monitor the dashboard. There are generally also tools available to customize the alerts being sent.
- Incident management: This includes functionality to track, prioritize, and document security incidents, allowing for a quicker and more effective response. Some SIEMs also include limited automated response policies like disabling accounts or blocking IP addresses.
- Data and compliance reporting: A hugely important feature, SIEM platforms also offer predefined or customized reports that are specifically designed to comply with particular compliance frameworks – such as GDPR, HIPAA, SOC2, and others. This helps companies fulfill their compliance obligations by quickly creating audit-ready reports.
- Integrations: SIEM products also feature integrations with a range of tools such as SOARs, EDRs, email management tools, DNS security, and more. However, a word of caution: If you’re integrating too many separate products into your SIEM, it could be a sign that a more comprehensive alternative like XDR might be needed.
What Does a SIEM NOT Include?
Security teams use SIEMs because they improve overall security posture by providing visibility across the entire IT environment. But that doesn’t mean they’re the only cybersecurity product you’ll ever need. In fact, there is plenty of functionality that major products lack:
- Endpoint management: SIEM products focus on events and behavior, rather than endpoints. This means they’re better at detecting, e.g., suspicious login attempts than malware injection. This means organizations generally combine SIEMs with EDR or XDR platforms if they want to protect diverse remote devices like laptops, mobile devices, tablets, and IoT devices.
- Automated response: Some SIEMs offer response capabilities, but the functionality is generally quite limited. Therefore, SIEMs are often combined with security orchestration, automation, and response (SOAR) platforms. These allow security teams to design granular response policies like locking accounts, blocking webpages, revoking privileges, enforcing patches, and more.
- Network monitoring: SIEMs focus specifically on the actions of accounts within the IT environment, rather than identifying malicious activity outside of it. This means monitoring for network, DNS, and other inbound threats is generally outside the scope of these platforms.
- Access management: Privileged access management (PAM) and information access management (IAM) tools are generally available through separate products, such as PASM, PEDM, or CIEM solutions.
- Vulnerability management: SIEM products don’t generally specialize in vulnerabilities and patching, meaning they’re often used in combination with EDR, XDR, or other vulnerability management tools.
Protect Every Endpoint with Heimdal's Unified Cybersecurity Platform!
Discover Heimdal's all-in-one security solution here.
What Is EDR: Intro And Key Features

- Mikkel Pederson, Head of Global Sales Enablement, Heimdal®
EDR: How it Works
To understand EDR, we need to first discuss endpoints.
In simple terms, you can think of endpoints as any physical device in an IT environment. In the past, the main endpoints were largely servers, desktop computers, and printers.
But in the past fifteen years, the list has exploded to include mobile devices, tablets, laptops, IoT and smart devices… the list goes on.
Stay ahead of cyber threats with AI-powered protection designed for complete security.
Ready to outsmart cybercriminals? Click here to get started!
Therefore, a more specialized range of tools has emerged to help manage these devices – of which EDR is the best-known.
Often, they’re used alongside SIEMs to paint a more detailed and granular picture of cyber threats at the endpoint level. They are particularly effective at detecting unpatched vulnerabilities and malware on specific devices – which SIEMs are less effective at.
To do this, EDR products collate a whole range of information across:
- ARPs;
- DNS;
- Sockets;
- Memory dumps;
- System calls;
- IP addresses;
- Registry data.
This is a much wider range of data sources than SIEMs, which mostly focus on log file analysis. That’s how these products manage to create a more detailed and focused picture of endpoint health.
EDR Benefits And Key Features:
EDR products have a wide range of features designed to identify issues, vulnerabilities, and malicious attacks on a whole range of devices.

These include:
- Endpoint data collection: EDR tools gather data from a whole range of endpoint-specific data sources to identify and detect endpoint-specific threats and vulnerabilities – both proactively and in realtime.
- Endpoint detection and visibility: These tools also enable detection and classification of endpoints. This helps IT teams gain a birds’ eye view over devices in the IT environment (including ‘shadow devices’ you don’t know about). This provides a strong basis for least privilege implementation.
- Realtime threat detection: Like SIEMs, EDR products analyze realtime data to detect potential threats as they happen. This principally includes malware and viruses, but it can also extend to phishing, data exfiltration, denial of service, and vulnerability exploits – depending on the product in question.
- Automated responses: There are also various features to respond (automatically or manually) to threats when detected. This can include remotely containing or isolating devices, as well as some custom rules to define and customize automated responses.
- Vulnerability detection: EDR products can also identify issues like unpatched vulnerabilities on specific endpoints, defending against threats like escalation of privilege and remote exploit attacks. Some products also include tools (eg CSS and MITRE ATT&CK data) to quantify the relative risk of certain vulnerabilities and, by association, how urgent they are to patch.
What Does an EDR NOT Include?
EDR products are designed to offer advanced functionality in one area of cybersecurity. For this reason, they’re often combined with other products, including SIEMs, to provide a more holistic and far-reaching solution. Here are the main features that EDR products lack:
- Network-wide visibility – EDR products aren’t designed to provide visibility over the entire IT environment. These products create a silo by design.
- Log and event analysis – Unlike SIEMs, EDR products don’t focus on user activity. While they excel at detecting issues like malware injection, they have no visibility over issues like suspicious logins and can’t generally identify anomalous behavior.
- Privileged access management – Tools to identify privileged accounts, manage access, and enforce login policies are usually only available through specialist third-party PAM tools.
- Compliance and reporting – The compliance and reporting features aren’t as extensive in EDR products as they are with SIEMs. This is partially because they don’t have visibility over user activity, sensitive data, or access privileges. They also don’t tend to store information for as long as SIEMs.
- Network and cloud monitoring – EDRs have limited visibility over network and DNS activity. They also can’t effectively monitor the wide range of cloud-based instances and workflows that organizations increasingly rely on. You will need separate tools to secure DevOps environments, cloud databases, virtual machines, and any workflows built in an AWS or Azure environment.
Going beyond SIEM and EDR
By now, you’ll probably have noticed significant crossover between the functionality offered by SIEMs and EDRs.
Here’s the key challenge: Even when they appear to do the same thing on the surface (e.g. realtime threat detection), the different focuses of each product means they often do it in very different ways.
To oversimplify, an EDR tool is more likely to detect threats like malware injection, whereas SIEMs are better suited to detecting suspicious login attempts.
This can be frustrating for IT and security teams looking to build a coherent and integrated cybersecurity solution – which is why EDRs and SIEMs are so often combined. But unfortunately, the complexity doesn’t stop there.
There are several separate tools that are often integrated with EDRs and SIEMs to help fill the functionality gaps of each product. Some of these include:
- SOAR – These integrate with SIEMs and allow security teams to customize automated responses to the specific threats being detected.
- MDR – Managed detection and response is effectively the same as EDR, except the tech provider also provides an additional managed service. This can include remote monitoring, policy configuration, reactive response, compliance reporting, and more.
- Device management – Including MDM, MAM, EMM, and UEM. These help IT teams manage remote devices like laptops, mobile phones, tablets, and smart devices.
- PAM – Privileged access management is a notable gap of both SIEMs and XDR tools, meaning they’re often combined with PAM tools such as PASM, PEDM, or CIEM.

- Network and DNS security – Another key gap of SIEMs and XDRs. DNS and network security tools are principally designed to detect suspicious activity across DNS and internet networks.
Long story short: There are a lot of different types of cybersecurity products that can be used alongside SIEMs and EDRs. By the time you’ve knitted together your SIEM, EDR, PAM, DNS, and whatever other tools you need – you’re going to end up with a complicated, expensive, and unwieldy platform.
Wouldn’t it be nice if somebody bought all these tools together under the same roof?
XDR: One Platform to Rule Them All

- Nabil Nistar, Director, Strategy and Portfolio Marketing, Heimdal®
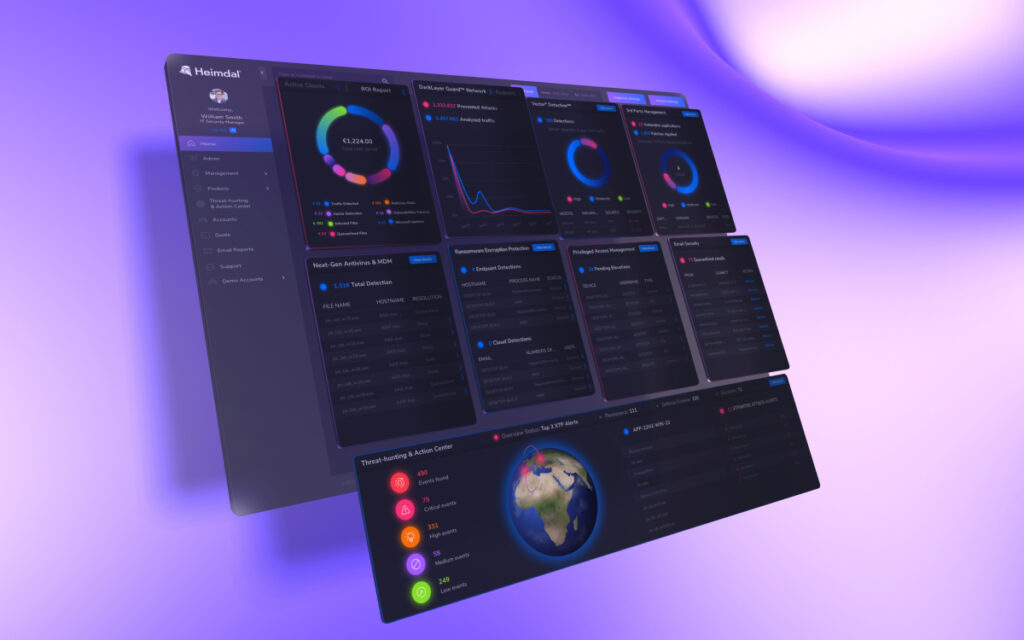
Heimdal’s mission is to reduce complexity in cybersecurity as much as possible. And as you can tell from this piece, there is plenty of confusion to clear up. That’s why we created our extended detection and response (XDR) platform.
Read more: What Is XDR (Extended Detection and Response)? Features, Benefits, and Beyond
Each individual security tool we’ve discussed in this blog has a slightly different scope, purpose, and functionality.
Here’s the issue: The more tools you combine, the less effective your overall cybersecurity approach becomes. If a hacker gains entry to your environment, you need one focused and targeted response.
The last thing you need is your SIEM, SOAR, and EDR products all trying to respond to the same threat in different ways.

Instead, Heimdal’s XDR platform brings all the tools, features, and functionality we’ve discussed in this piece into one dashboard. That includes:
- Network security;
- Endpoint security;
- Vulnerability management;
- Privileged access management;
- Email and collaboration security;
- Unified endpoint management.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








