Contents:
DNS security risks are everywhere, and the stats show it too. A 2021 IDC survey of over 1,100 organizations across North America, Europe, and the Asia Pacific revealed that 87% had encountered DNS attacks.
The average cost per attack was approximately $950,000 globally, rising to about $1 million for organizations in North America.
That’s a lot!
But that’s not the end. The numbers are increasing every day. In Q1 of 2024 alone, there were 1.5 million DNS DDoS attacks.
This is an alarming rate.
And this is why you need to be aware of common DNS security risks, along with the emerging ones, to stay alert and safe.
Before we start discussing them in detail, here’s a quick list of solutions you can implement to safeguard your organization in case you’re too busy to read the entire article:
- Implement DNSSEC (DNS Security Extensions): Uses digital signatures to verify DNS data, preventing spoofing and cache poisoning.
- Using DNS Filtering and Blocking: Analyzes and blocks malicious domains to protect against phishing and malware.
- Monitoring and Logging DNS Traffic: Continuously tracks and analyzes DNS traffic to identify and respond to suspicious activities.
- Configuring DNS Servers Securely: Secures DNS servers through hardening, access control, and secure protocols to reduce vulnerabilities.
- Employing Multi-Layered Security Strategies: Combines various security measures to create a robust defense against DNS attacks.
- Choosing the Right DNS Software: Selects DNS software with advanced security features, scalability, and reliability for optimal protection.
The Biggest DNS Security Risks in 2025
1. DNS Spoofing and Cache Poisoning
DNS spoofing, also known as DNS cache poisoning, is an attack where corrupted DNS data is inserted into the cache of a DNS resolver, causing the resolver to return an incorrect IP address.
This redirects users to malicious sites without their knowledge, potentially leading to data theft, malware infections, and other security breaches.
How It Works:
- Manipulation of DNS Records: Attackers intercept and modify DNS responses to direct users to fraudulent sites.
- Corrupting DNS Cache: Malicious data is inserted into the cache of a DNS server, which then returns false information to users.
Detour Dog Attacks Explained by Ethical Hacker Glenn Wilkinson and Former Cybercrime Detective Adam Pilton
byu/liv_v_ei inHeimdalSecurity
2. DDoS Attacks on DNS Servers
Distributed Denial of Service (DDoS) attacks overwhelm DNS servers with a massive volume of requests, causing them to become unresponsive and disrupting access to websites and online services.
These attacks are particularly effective because DNS servers are critical for internet functionality and statistics from 2023 show that the number of DDoS attacks will double from 7.9 million to 15.4 million, compared to 2017.
How It Works:
- Flooding DNS Servers: Attackers use botnets to send an overwhelming number of requests to a DNS server.
- Exhausting Resources: The server’s resources are exhausted, leading to service downtime or degraded performance.
3. DNS Tunneling and Data Exfiltration
DNS tunneling is a sophisticated attack method that exploits the DNS protocol to tunnel unauthorized data or create covert communication channels.
It involves encoding data within DNS queries and responses, allowing attackers to bypass traditional security measures such as firewalls and intrusion detection systems.
This technique can be used for a variety of malicious purposes, including data exfiltration, command and control (C2) communication, and bypassing network restrictions.
How it Works:
- Data Encoding in DNS Queries: Attackers encode the data they wish to exfiltrate within the DNS queries. These queries are sent to a compromised or attacker-controlled DNS server.
- Decoding at the Attacker’s End: The attacker’s DNS server receives the encoded queries, extracts the data, and sends back encoded responses to the compromised machine.
- Establishing C2 Channels: DNS tunneling can also be used to establish C2 channels, allowing malware to communicate with remote servers through DNS traffic.
4. DNS Hijacking and Redirection
DNS hijacking involves taking control of a DNS server or modifying DNS records to redirect traffic to malicious sites.
This can be achieved through various methods, including compromising DNS settings on routers or manipulating DNS records at the registrar level.
How It Works:
- Compromising DNS Settings: Attackers gain access to DNS settings and change them to point to malicious IP addresses.
- Manipulating Registrar Records: DNS records are altered at the domain registrar, redirecting traffic to attacker-controlled sites.
5. Man-in-the-Middle Attacks on DNS
In a man-in-the-middle (MitM) attack, attackers intercept and alter DNS communications between the user and the DNS server.
This allows them to redirect users to malicious sites or manipulate DNS responses to facilitate other types of attacks.
How It Works:
- Intercepting DNS Traffic: Attackers position themselves between the user and the DNS server, intercepting DNS queries and responses.
- Modifying DNS Responses: DNS responses are altered to redirect users or deliver incorrect information.
6. DNS Rebinding Attacks
DNS rebinding attacks exploit the DNS system to bypass the same-origin policy in web browsers, allowing attackers to interact with internal network services. This can lead to unauthorized access and manipulation of internal systems.
For unauthorized software the first and most important thing you should have is application whitelisting and I cannot stress the importance of this layer.
Andrei Hinodache, Cybersecurity Community Leader, Heimdal®
How It Works:
- Rebinding DNS Responses: The attacker tricks the victim’s browser into repeatedly resolving a domain name to different IP addresses, including those within the internal network.
- Bypassing Same-Origin Policy: The attack leverages the browser’s same-origin policy to access internal services.
7. DNS Protocols Vulnerabilities
The DNS protocol itself can have vulnerabilities that attackers exploit to cause various security issues. These vulnerabilities can be inherent to the protocol or result from improper implementation.
How It Works:
- Exploiting Protocol Flaws: Attackers leverage weaknesses in the DNS protocol or its implementation.
- Crafting Malicious DNS Queries: Specially crafted DNS queries are used to exploit vulnerabilities in DNS software.
Emerging DNS Threats
1. DNS Amplification Attacks
DNS amplification attacks are a type of DDoS attack. In 2023 Q4, experts observed a 117% year-over-year increase in this type of attacks.
In it, attackers exploit the open nature of DNS servers to flood a target with an overwhelming amount of traffic.
This attack leverages the disparity between the small size of a DNS query and the significantly larger size of the response.
By sending a small query with a spoofed IP address to a DNS server, attackers can amplify the response, causing a significant traffic load on the target server.
How It Works:
- Query Spoofing: Attackers send DNS queries with the IP address of the target, causing the DNS server to send responses to the target instead.
- Traffic Amplification: The large size of DNS responses compared to the queries creates an amplification effect, overwhelming the target with excessive traffic.
2. DNS-Based Malware Distribution
A report indicated 38% of DNS attacks involved DNS-based malware distribution in 2023.
This shows that DNS is increasingly being used as a vector for distributing malware. Attackers use DNS queries to deliver malicious payloads, exploiting the trusted nature of DNS traffic to bypass security controls.
This method is particularly insidious because DNS traffic is often allowed through firewalls without scrutiny, providing a covert channel for malware distribution.
How It Works:
- Malicious DNS Responses: Attackers configure malicious DNS servers to respond with IP addresses hosting malware.
- Payload Delivery: When users unknowingly query these malicious servers, they are redirected to sites that automatically download and install malware.
3. AI-Powered DNS Attacks
75% of security professionals reported an uptick in attacks over the past year, with 85% attributing this rise to bad actors using generative AI, according to a new report by Sapio Research and Deep Instinct.
The integration of AI in cyber attacks has led to the emergence of AI-powered DNS attacks.
These attacks leverage machine learning algorithms to dynamically adapt and evade detection, making them more effective and harder to mitigate. AI can be used to automate and optimize DNS attack strategies, increasing their success rates.
How It Works:
- Adaptive Attack Strategies: AI algorithms analyze network defenses and adapt attack strategies in real-time to bypass security measures.
- Automated Execution: AI automates the execution of complex DNS attacks, such as tunneling, amplification, and spoofing, making them more efficient and harder to detect.
4. Hybrid DNS Attacks
Hybrid DNS attacks combine multiple DNS attack techniques to create more complex and effective threats.
By integrating methods such as spoofing, tunneling, and amplification, attackers can achieve a higher impact and evade detection more successfully.
How It Works:
- Combining Techniques: Attackers integrate various DNS attack methods to exploit multiple vulnerabilities simultaneously.
- Increased Evasion: The use of multiple techniques makes it difficult for security systems to detect and mitigate all aspects of the attack.
How to Mitigate DNS Security Risks
1. Implement DNSSEC (DNS Security Extensions)
DNSSEC (Domain Name System Security Extensions) enhances DNS security by allowing DNS data to be verified using digital signatures.
This ensures the authenticity and integrity of DNS responses, preventing DNS spoofing and cache poisoning attacks. DNSSEC works by signing DNS data at each level of the DNS hierarchy, enabling resolvers to verify the source and integrity of the data.
Best Practices for DNSSEC:
- Sign Your DNS Zones: Apply digital signatures to your DNS zones to ensure their authenticity.
- Enable DNSSEC Validation: Configure your DNS resolvers to validate DNSSEC signatures.
- Monitor and Maintain: Regularly check the health of DNSSEC deployments and update keys as necessary.
2. Using DNS Filtering and Blocking
DNS filtering and blocking involve analyzing DNS queries and responses to identify and block malicious domains. This helps prevent access to harmful sites and reduces the risk of phishing, malware, and other cyber threats.
Advanced DNS filtering solutions use threat intelligence to keep up with emerging threats and provide real-time protection.
Best Practices for DNS Filtering:
- Utilize Threat Intelligence Feeds: Integrate threat intelligence to identify and block malicious domains.
- Implement Category-Based Filtering: Block entire categories of malicious or unwanted content (e.g., phishing, malware).
- Customize Policies: Tailor filtering policies to meet specific organizational needs and compliance requirements.
3. Monitoring and Logging DNS Traffic
Continuous monitoring and logging of DNS traffic are critical for detecting suspicious activities and potential threats. By analyzing DNS traffic patterns, organizations can identify anomalies that may indicate an ongoing attack or data exfiltration attempt.
Best Practices for DNS Traffic Monitoring:
- Deploy Monitoring Tools: Use DNS monitoring tools to capture and analyze DNS traffic in real-time.
- Set Alerts for Anomalies: Configure alerts for unusual DNS activities, such as spikes in traffic or unexpected query types.
- Conduct Regular Audits: Regularly review DNS logs to identify trends and potential security issues.
4. Configuring DNS Servers Securely
Secure configuration of DNS servers is essential to reduce vulnerabilities and protect against attacks. This includes implementing best practices for server hardening, access control, and security protocols.
Best Practices for Secure DNS Server Configuration:
- Disable Unnecessary Services: Turn off any services or features that are not needed.
- Implement Access Controls: Restrict access to DNS server management interfaces to authorized personnel only.
- Use Secure Protocols: Employ secure communication protocols such as DNS over HTTPS (DoH) or DNS over TLS (DoT) to encrypt DNS traffic.
5. Employing Multi-Layered Security Strategies
A multi-layered security approach involves combining various security measures to create a robust defense against DNS attacks. This strategy ensures that even if one layer is breached, additional layers of protection can mitigate the impact.
Best Practices for Multi-Layered Security Strategy:
- Firewalls and IDS/IPS: Deploy firewalls and intrusion detection/prevention systems to block and detect malicious activities.
- Endpoint Security: Protect individual devices with antivirus and endpoint protection solutions.
- Regular Security Assessments: Conduct regular security assessments and penetration testing to identify and address vulnerabilities.’’
Top Tip: Checkout our masterclass video to get in-depth insights on layered defense systems.
6. Choosing the Right DNS Software
Selecting the right DNS software is crucial for ensuring robust DNS security. The software should offer advanced security features, scalability, and reliability to handle your organization’s needs.
When evaluating DNS software, consider factors such as:
- Threat detection capabilities;
- Ease of management;
- Integration with other security tools.
One of the leading solutions in DNS security is Heimdal®.
Heimdal provides comprehensive DNS protection with features like real-time threat detection and blocking, DNS filtering, and secure DNS resolution.
Their solutions are designed to protect against a wide range of DNS-based attacks and enhance overall network security.
Heimdal® — Your Ultimate DNS Security Solution
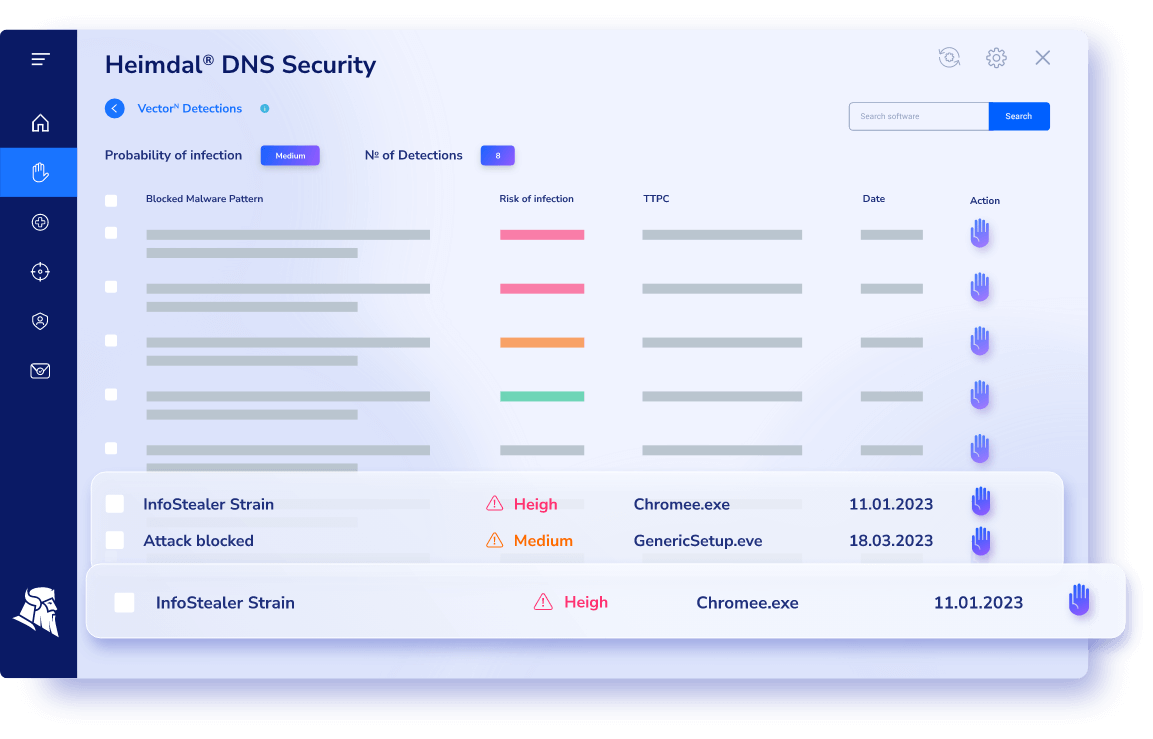
Here’s an overview of multiple ways Heimdal® ensures your DNS security:
- Heimdal®’s DNS Security employs the DarkLayer Guard® engine to filter DNS traffic. This engine creates a local DNS server that examines data packets before resolving DNS queries.
If any suspicious activity is detected during the query process, the connection is automatically blocked. This proactive filtering prevents malicious data from reaching your endpoints and network.
- VectorN Detection® enhances security by identifying patterns in domain blocks using advanced Machine Learning algorithms. It can detect even the most stealthy malware by analyzing the behavior of blocked domains.
When malicious patterns are found, the system flags potentially infected endpoints for further investigation. This includes recognizing unusual domain blocking frequencies, which might indicate the presence of advanced persistent threats or botnets.
- Heimdal®’s DNS Security works across DNS, HTTP, and HTTPS layers to provide comprehensive protection. By routing all internet traffic through a locally configured database, Heimdal® can identify and block access to known malicious websites.
In 2022 alone, this system blocked over 17 million network-based attacks, safeguarding users from malware and ransomware.
- Since September 2022, Heimdal® has integrated DNS over HTTPS (DoH) into its security solution. DoH encrypts DNS traffic, reducing the risk of DNS spoofing and Man-in-the-middle (MitM) attacks.
This encryption ensures a secure and private browsing experience without compromising system performance, ultimately saving time and resources for organizations.
- Heimdal®’s DNS Security suite is designed to work seamlessly with any existing security infrastructure.
Available at both endpoint and network levels, it can be deployed quickly and integrates well with other security tools, such as firewalls and antivirus software. This compatibility allows organizations to enhance their security posture with minimal disruption.
We mainly use Heimdal® for their Privileged Access Management (PAM) and Patch Management tool. But we started adding more of their modules afterwards such as DNS filtering and remote desktop. They are all simple and easy to set up, which saves us a lot of time.
In addition to these five primary features, Heimdal®’s DNS Security Solution also:
- Detects DNS hijacking attempts.
- Identifies processes, users, URLs, and attacker origins involved in network infiltration.
- Predicts future DNS threats with 96% accuracy using AI.
- Offers category-based blocking for endpoint solutions.
- Logs network traffic comprehensively for better visibility and management.
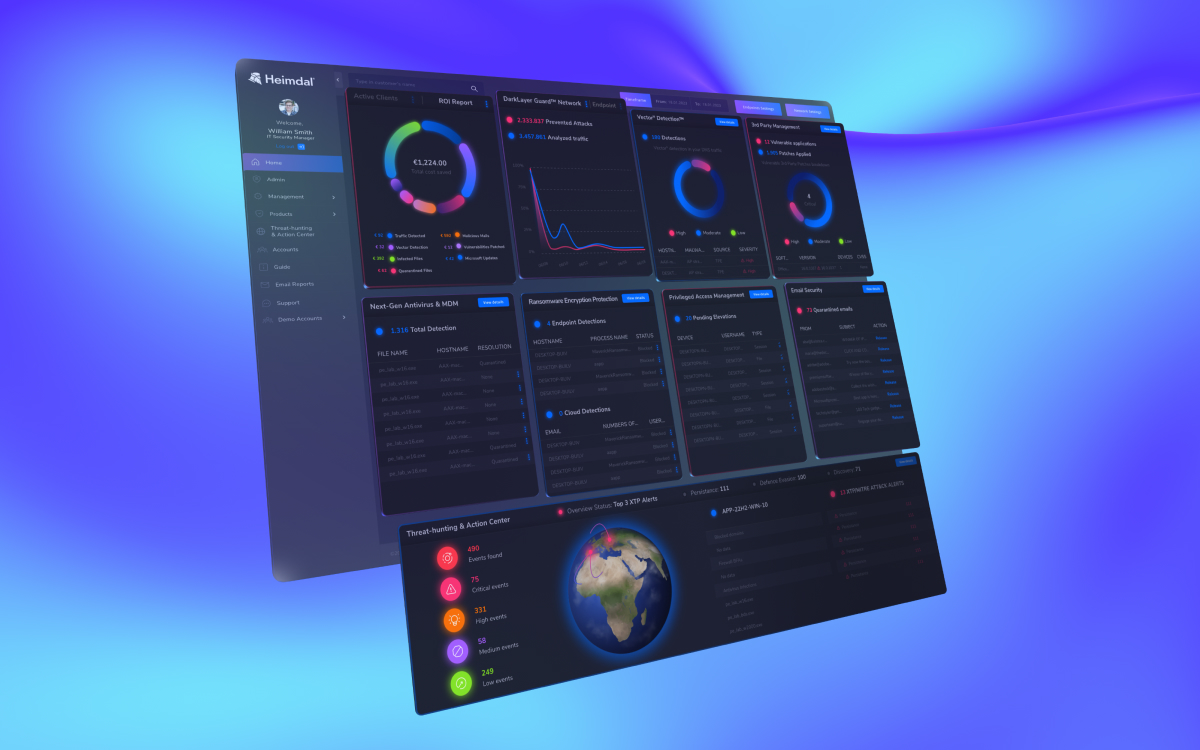
Need More Protection? Fortify Your Defenses With Our Heimdal® XDR Platform!
If you take 10 pieces of paper and break them, you can break them, but if you put more pieces, you might break them, but if you put 100 pieces of paper together and try to break them like this, will you be able to break them? Nope. Have as many as you can but there’s another caveat to these: as many as you can, out of those that you have, have them unified. We at Heimdal® have a unified platform, exactly unifying all these layers together, and under each of these layers we have multiple products.
Andrei Hinodache, Cybersecurity Community Leader, Heimdal®
If you are looking for a DNS solution and some extra tools, we have you covered as well. Our Heimdal® XDR platform bundles our top cybersecurity solutions into one agent, so you can have maximum protection across your endpoints and networks without the fuss of opting for a dozen other different tools from different vendors.
Our platform is the widest on the market, and from a single agent, you can manage all the solutions included. And because we know that not everyone has the same security needs, we let you customize the solutions to your specific needs. Curious to see what you’ll get with Heimdal® XDR?
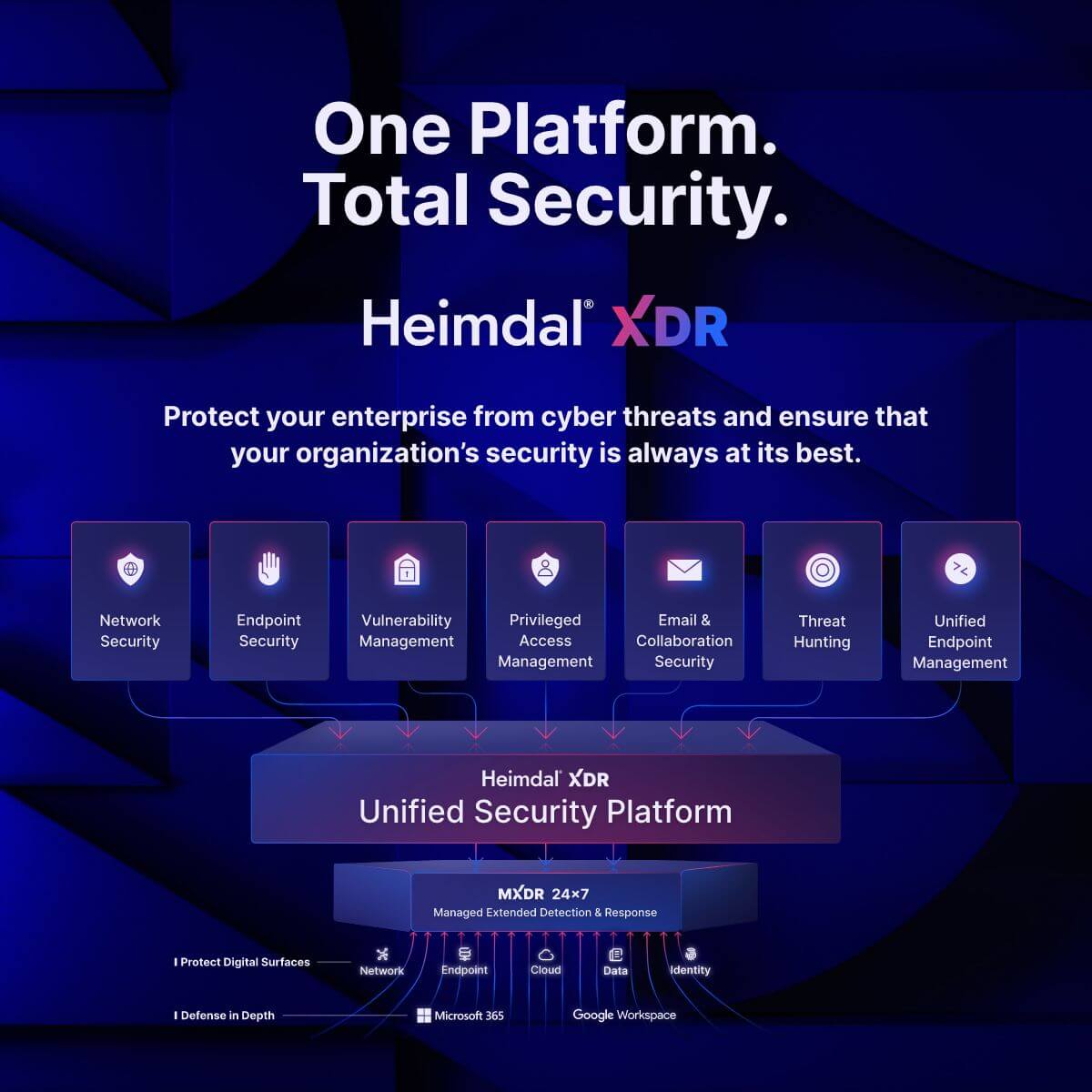
- Network Security: A range of market-leading DNS security tools to help monitor, manage, and secure network-based connections.
- Endpoint Security: Secure remote devices of all shapes and sizes through endpoint DNS security, next-gen antivirus, firewalls, and ransomware encryption protection.
- Vulnerability Management: Create policies to automatically install patches and updates, so you can take the admin out of vulnerability management.
- Privileged Access Management: Define granular policies to govern who has access to what files, applications, and other devices. This includes tools to dynamically accept or deny access based on contextual signals – eliminating the need for standing privileges.
- Email and Collaboration Security: Detect and prevent incoming email-based threats, with advanced anomaly analysis to detect and repel even the most convincing phishing attempts.
- Threat Hunting: Our threat detection platform allows IT teams to quickly detect and track anomalous behavior, together with risk scores and a forensic breakdown of the event, device, and associated applications. This makes effective and targeted responses much easier.
- Unified Endpoint Management: Manage devices of all shapes and sizes from one simple dashboard. No more clicking between disconnected apps to manage laptops, mobile devices, or BYOD devices.
Enjoy total security from one platform today!
Frequently Asked Questions (FAQs)
What is DNS security?
DNS security involves safeguarding the DNS infrastructure against cyber threats to ensure its fast and reliable performance. A robust DNS security strategy includes multiple layers of defense, such as deploying redundant DNS servers, implementing security protocols like DNSSEC, and enforcing thorough DNS logging.
What are the risks of DNS poisoning?
The risks of DNS poisoning include data theft, malware infection, delayed security updates, and censorship.
What is DNS layer security?
DNS layer protection encompasses solutions like domain categorization, content filtering, and advanced threat protection against sites known to host malicious content. With DNS security enabled, any attempt to visit an unsafe web page would be blocked at the DNS layer, preventing access to the infected site.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security