Contents:
Several campaigns employing spyware have come to light, a new report shows. Researchers name these cyberattacks “Anomalous”. The threat actors’ targets are industrial enterprises and their final goal consists of email accounts credential theft, financial fraud, or even the reselling of this spyware to other hackers.
The ‘Anomalous’ Spyware Cyberattacks: More Details
Researchers from Kaspersky were the ones who published a report on this topic. Hackers leverage spyware tools that are ready-made, however, every variant is deployed for a limited and specific period of time. This technique helps threat actors remain undetected.
The commodity malware employed in these cyber-attacks includes:
- AgentTesla/Origin Logger
- HawkEye
- Noon/Formbook
- Masslogger
- Snake Keylogger
- Azorult
- Lokibot
The experts referred to these attacks as “anomalous”, this conclusion being drawn out of the fact that they are characterized by a short-lived nature, which is not a common thing in this field. Hence, the spyware attacks under discussion have a lifespan of almost 25 days compared to usual campaigns extended over a period of months or even years.
The lifespan of the “anomalous” attacks is limited to about 25 days. And at the same time, the number of attacked computers is less than 100, of which 40-45% are ICS machines, while the rest are part of the same organizations’ IT infrastructure.
This has become a trend: around 21.2% of all spyware samples blocked on ICS computers worldwide in H1 2021 were part of this new limited-scope short-lifetime attack series and, depending on the region, up to one-sixth of all computers attacked with spyware were hit using this tactic.
The leveraging of the SMTP-based communication protocol is yet another particularity of this campaign as this helps threat actors perform data exfiltration activities and send it to their C2 server. In usual spyware attacks, the HTTPS protocol is normally used to establish a C2 communication.
The researchers underline the fact that hackers do not commonly choose SMTP because of its incapacity to fetch binaries or non-text files. On the other hand, the protocol shows simplicity and is able to blend with regular network traffic.
Extending the Network Infiltration through Stolen Credentials
The hackers perform spear-phishing cyberattacks to steal the credentials of employees. These serve further for advanced infiltration purposes, as the cybercriminals manage to move laterally onto the network.
Compromised corporate mailboxes leveraged in past malicious campaigns are used as C2 servers related to new attacks. This thing makes the detection of malicious internal correspondence particularly challenging.
The researchers also showed in an operational diagram the mechanism used by threat actors in these “anomalous” spyware attacks:
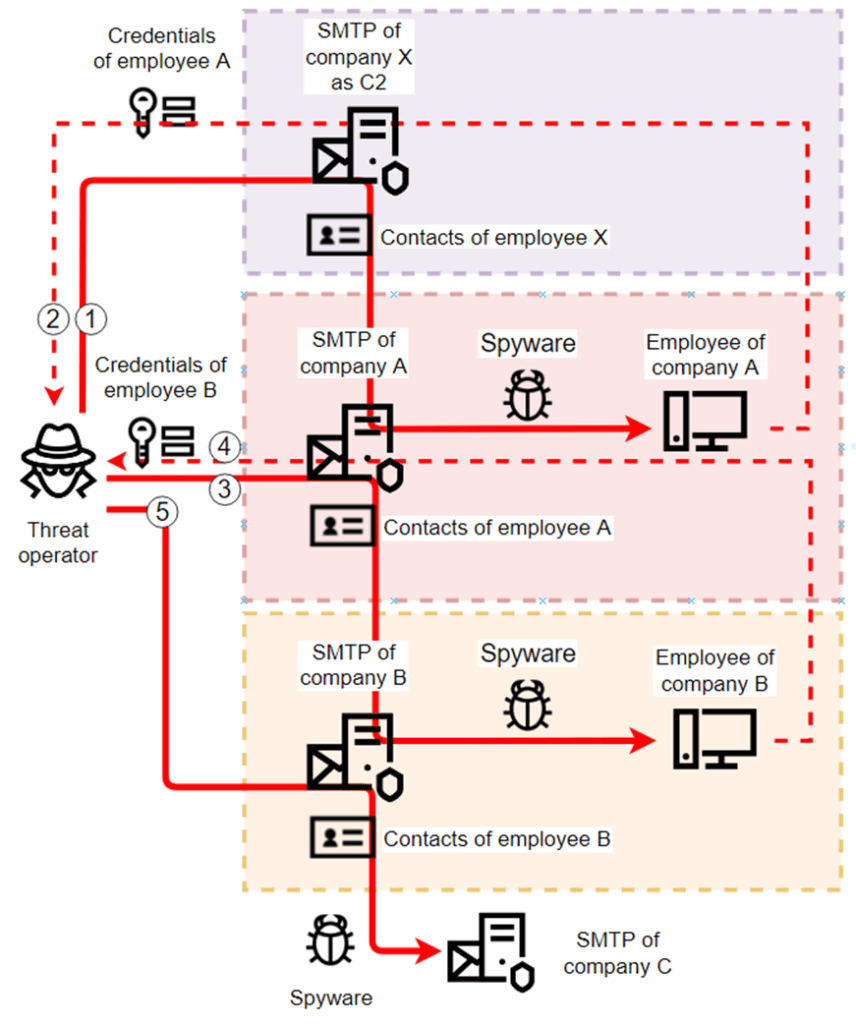
2000 abused corporate emails were detected by the experts posing as temporary C2 servers.
What’s Next? The Dark Web Market Commerce
Many of the stolen email account credentials like VPN, RDP, SMTP, SSH, or cPanel end up for sale on the dark web marketplace with other hackers becoming the buyers.
Industrial companies are targeted in these attacks, as the researchers emphasized that 3.9% of all sold RDP accounts belong to this field.
How Can Heimdal™ Help?
Email Security is a necessity in today’s corporate context. Choose our Email Security solution, an outstanding spam filter that combines human expertise with threat intelligence, for the perfect cloud and on-premises email protection.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










