Contents:
No less than 180 journalists around the world have been targeted by clients of the cyber-surveillance company NSO Group.
What Happened?
On Sunday, an investigation into a massive data leak revealed that activists, politicians, and journalists from all over the world were targeted in a surveillance operation using the Pegasus software sold by the Israeli cyber-surveillance company NSO Group.
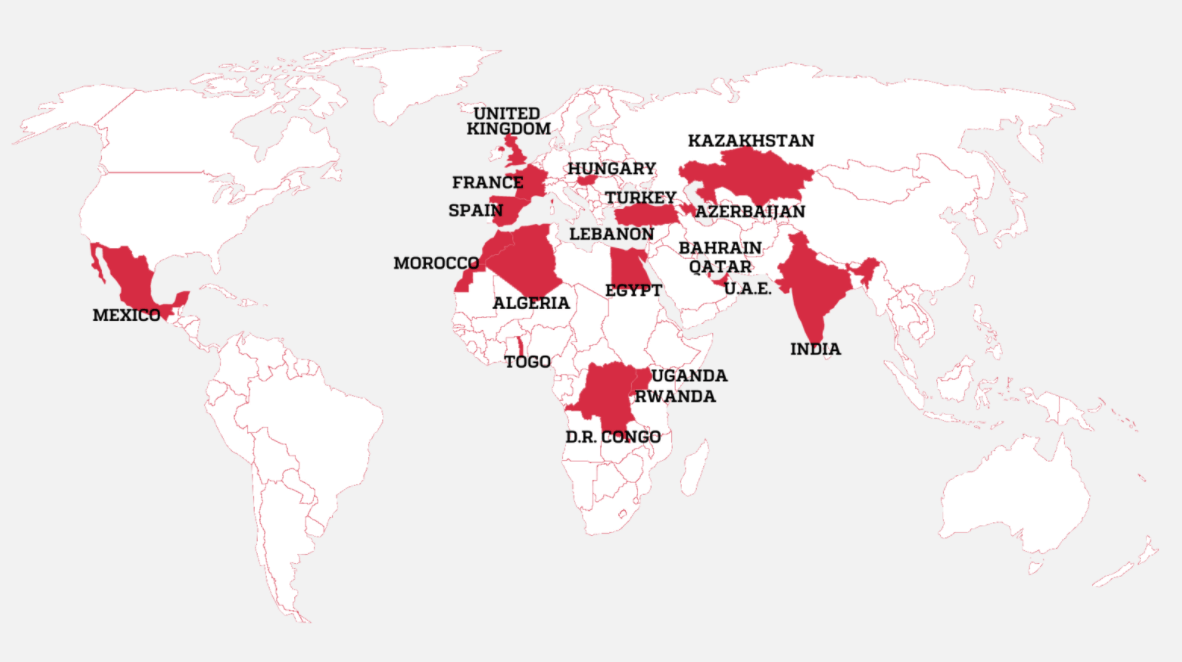
Countries Where Journalists Were Selected as Targets
Image Source: Forbidden Stories
As reported by the Washington Post, NSO Group’s Pegasus software was used in hacking attempts on 37 smartphones belonging to human rights activists and journalists. The phones were on a leaked list of numbers discovered by nonprofit organization Forbidden Stories and human rights group Amnesty International. The report states that the numbers on the list were singled out for possible surveillance by countries that are clients of NSO, which markets its spyware to governments to track potential terrorists and criminals.
Amnesty examined 67 smartphones where attacks were suspected. Of those, 23 were successfully infected and 14 showed signs of attempted penetration. For the remaining 30, the tests were inconclusive, in several cases because the handsets had been replaced. Fifteen of the phones were Android devices, none of which showed evidence of successful infection. However, unlike iPhones, phones that use Android do not log the kinds of information required for Amnesty’s detective work. Three Android phones showed signs of targeting, such as Pegasus-linked SMS messages.
The Guardian notes that Pegasus is able to extract a mobile device’s data, and activate the device’s microphone to secretly listen in on conversations. The list of journalists dates back to 2016 and includes reporters from the Washington Post, CNN, Al Jazeera, the Associated Press, the New York Times, Voice of America, the Wall Street Journal, Bloomberg News, Le Monde, the Financial Times, Radio Free Europe, Mediapart, El País, Reuters, and others.
Numbers on the list also belonged to heads of state and prime ministers, members of Arab royal families, diplomats and politicians, as well as activists and business executives.
NSO Group’s Reply
The Israeli company has always declared it does not have access to the data of its customers’ targets. According to NSO, the consortium had made “incorrect assumptions” about which clients use the company’s technology, and that the 50,000 number was “exaggerated” adding that the list could not be a list of numbers “targeted by governments using Pegasus”.
Following the publication of the article, the company released a statement saying that
The report by Forbidden Stories is full of wrong assumptions and uncorroborated theories that raise serious doubts about the reliability and interests of the sources. It seems like the “unidentified sources” have supplied information that has no factual basis and is far from reality.
After checking their claims, we firmly deny the false allegations made in their report. Their sources have supplied them with information which has no factual basis, as evident by the lack of supporting documentation for many of their claims.
In fact, these allegations are so outrageous and far from reality, that NSO is considering a defamation lawsuit.
Over the years, NSO has repeatedly said Pegasus is only meant for use against terrorists and serious criminals.
Pegasus M.O.
The Citizen Lab researchers Bill Marczak, John Scott-Railton, Sarah McKune, Bahr Abdul Razzak, and Ron Deibert explained that in order to monitor a specific target, a Pegasus operator must convince the victim to click on a specially crafted exploit link, which, when accessed, delivers a chain of zero-day exploits to penetrate security features on the phone. Of course, it also installs the malicious software without the user’s knowledge or consent.
Once the phone is exploited and Pegasus is installed, it begins contacting the operator’s command and control (C&C) servers to receive and execute operators’ commands, and send back the target’s private data, including passwords, contact lists, calendar events, text messages, and live voice calls from popular mobile messaging apps. Pegasus can even turn on the phone’s camera and microphone to capture activity in the phone’s vicinity.
As The Guardian reporters highlight, given the software has been sold to some of the world’s most repressive regimes, the selection of activists, dissidents, and journalists by NSO clients is one that campaigners will say was grimly predictable. Media outlets were able to identify 10 governments believed to be responsible for selecting the targets: Azerbaijan, Bahrain, Kazakhstan, Mexico, Morocco, Rwanda, Saudi Arabia, Hungary, India, and the United Arab Emirates, all clients of NSO.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security