Contents:
A malicious IcedID malware campaign was identified recently. According to researchers, threat actors are actively spreading malware using modified versions of the Zoom application that have been trojanized.
Zoom has become increasingly popular in recent years since the COVID-19 pandemic emerged and remote work has increased dramatically, along with the virtual communication tools.
Most malware is delivered to users’ machines by threat actors using these types of software tools.
IcedID Banking Malware Via Zoom App
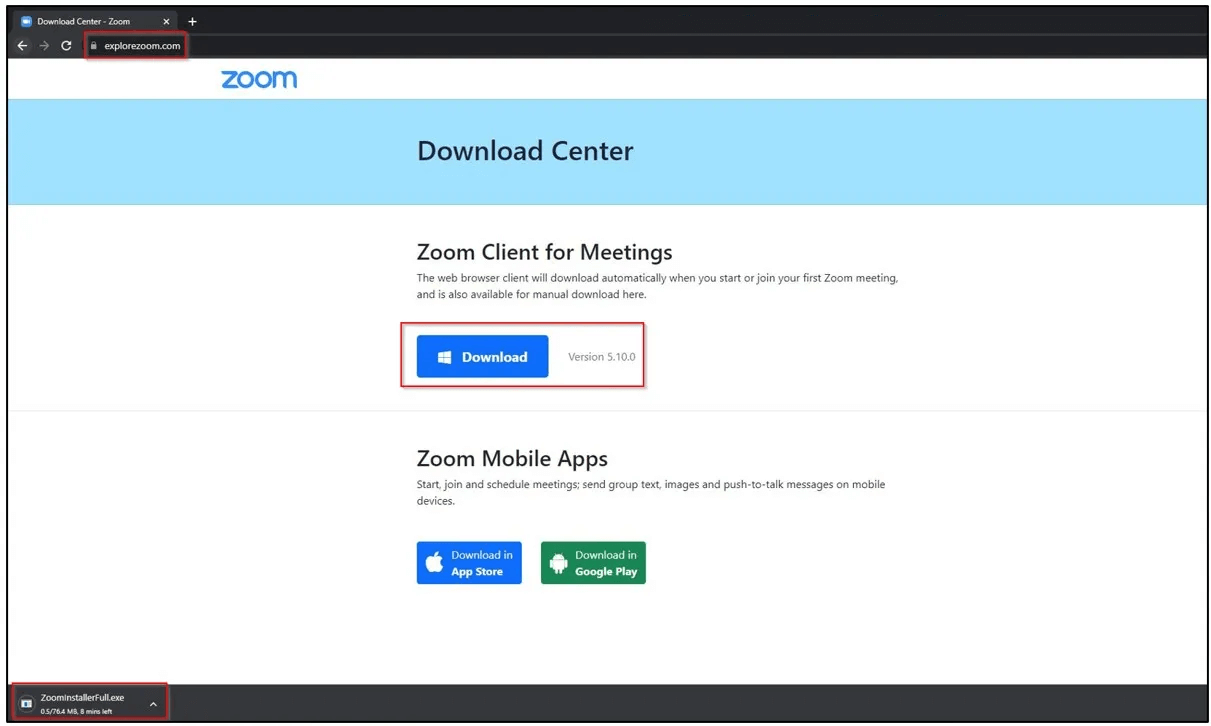
Modified Zoom App.
A large number of businesses are being targeted by this campaign in an attempt to steal sensitive information and install additional malware on their computers. Besides acting as a loader, IcedID can also download additional modules from the internet or deliver other malware strains.
It is most commonly spread via spam email attachments attached to malicious Office files. In this campaign, the attackers used a phishing site to deliver the IcedID payload.
It is an unusual method of delivering the IcedID payload to a victim, as IcedID itself is not typically distributed this way.
Further into the Technical Analysis
The attackers created a phishing website with a download button to lure people into clicking on it. It prompted them to download a Zoom installer file from the hxxps[:]//explorezoom[.]com/products/app/ZoomInstallerFull[.]exe URL.
According to Cyber Security News, there are two binaries that are dropped in the %temp% folder as a result of executing the “ZoomInstallerFull.exe” file:
- ikm[.]msi: It’s a legitimate installer, and it installs the Zoom app on the user’s system.
- maker[.]dll: This file carries out various malicious activities
With the “init” parameter the execution of the “maker.dll” file is done at this point by the “ZoomInstallerFull.exe” with the help of rundll32.exe. The program also runs an installer of the Zoom application, called “ikm.msi” to avoid suspicion.
This method allows threat actors to disguise their intentions and trick users into believing they are installing legitimate Zoom software.
The IcedID malware is loaded by the malicious DLL file known as “maker.dll” and the execution of this program loads into memory the original IcedID DLL file.
IcedID in Review
The IcedID malware is one of the most advanced and long-lasting viruses that has affected users all over the world for many years. It is a banking trojan that can be employed to steal account credentials or as a loader for other malware such as Cobalt Strike, ransomware, wipers, and more.
Last year, IcedID has been used in a hacking campaign against the Ukrainian Government. That time around, threat actors would exploit a Zimbra vulnerability (CVE-2018-6882.) in the second stage of the attack.
What Can Be Done?
Here is a list of recommendations for you to consider:
- Ensure that you do not download pirated software from the internet.
- Enforce multi-factor authentication and use strong passwords.
- Make sure that automatic software updates are enabled.
- Make use of a reputable anti-virus and internet security program.
- Do not open email attachments or links from untrusted sources without verifying their authenticity first.
- Provide employees with information on how to protect themselves against phishing attacks and untrusted URLs.
- Malware-distributing URLs should be blocked.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









