Introducing the Heimdal XDR Unified Security Platform
Protect your enterprise from cyber threats and ensure that your organization’s security posture is always at its best.
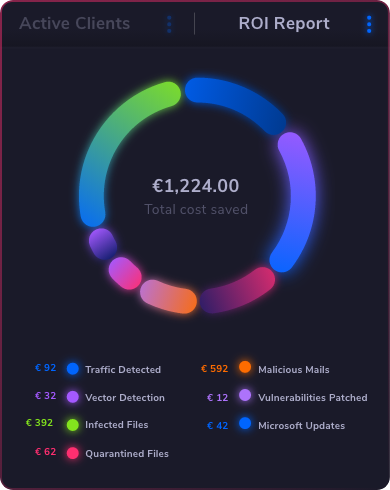
Empower your security and IT teams with Heimdal’s unified platform, built to defend against next-gen threats and provide comprehensive protection across multiple fronts. From endpoints and networks to emails, identities, and beyond, Heimdal has you covered with advanced detection and response capabilities.
Protect your enterprise from cyber threats and ensure that your organization’s security posture is always at its best.
Supercharge Detection & Response
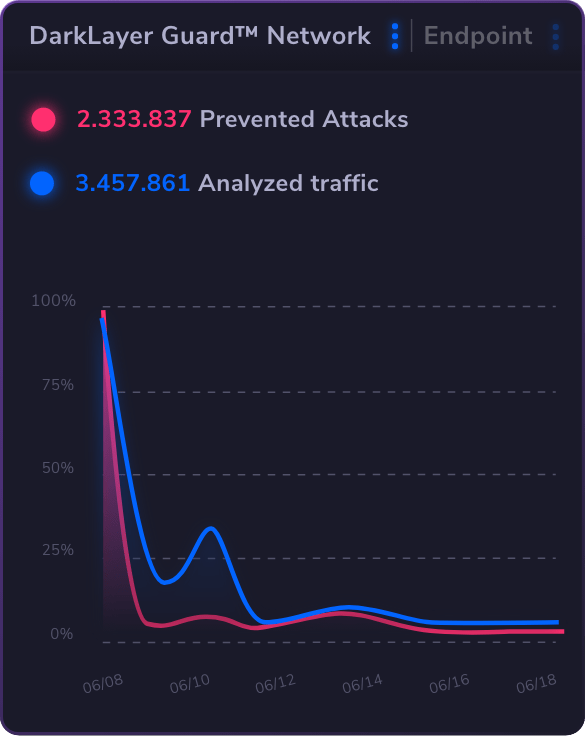
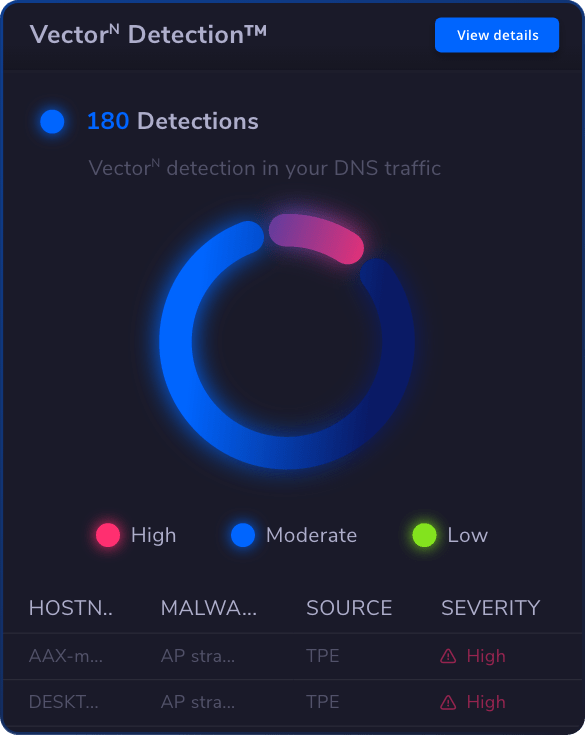
Our XDR provides advanced AI/ML-based threat detection for swift incident resolution.
Unified
Security
Our XDR platform offers consolidated security, unlike siloed point solutions.
Reduce Complexity & Costs
Our XDR simplifies compliance & reduces costs by consolidating multiple technologies.

Network
Security

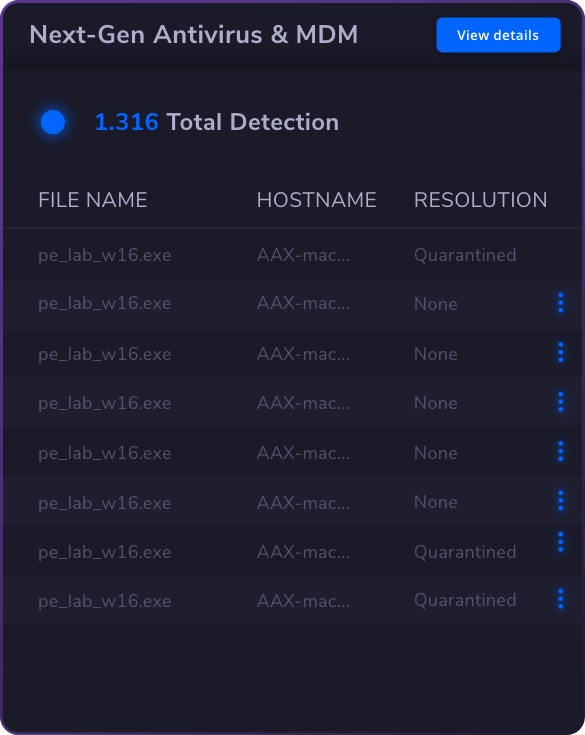
Endpoint
Security

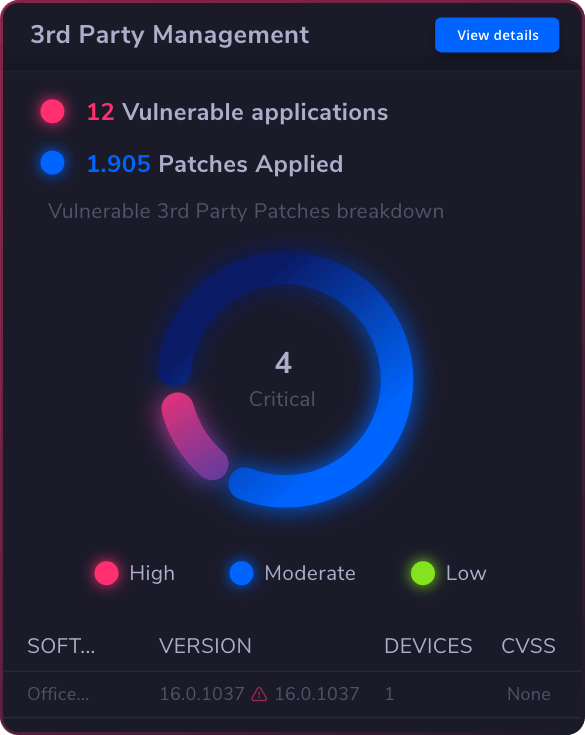
Vulnerability
Management

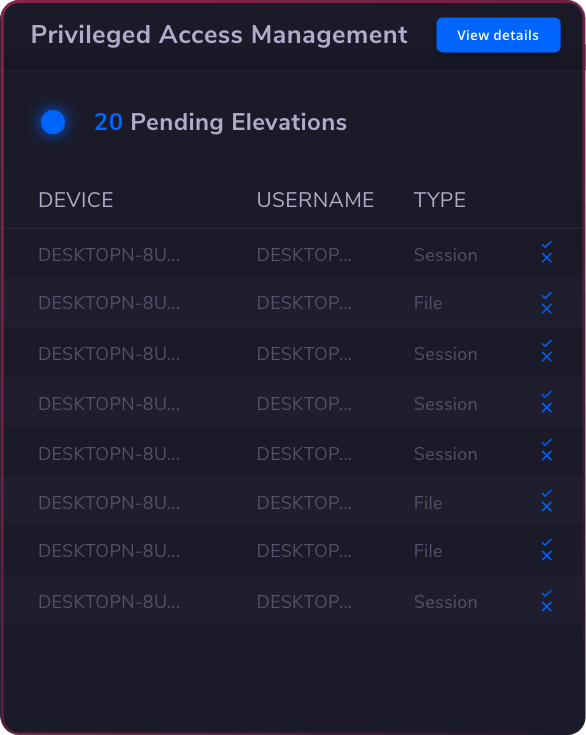
Privileged
Access
Management
Privileged Access Management
Privilege Elevation & Delegation Management Privileged Account & Session Management Application Control
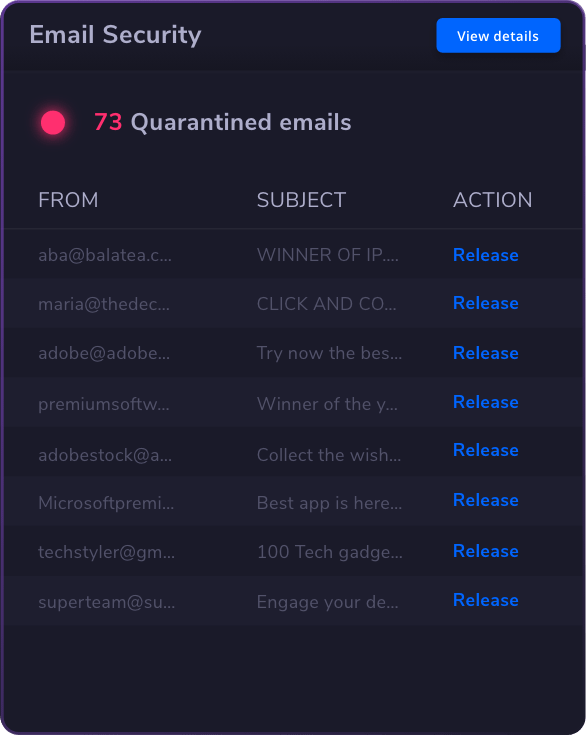
Email &
Collaboration
Security

Threat
Hunting
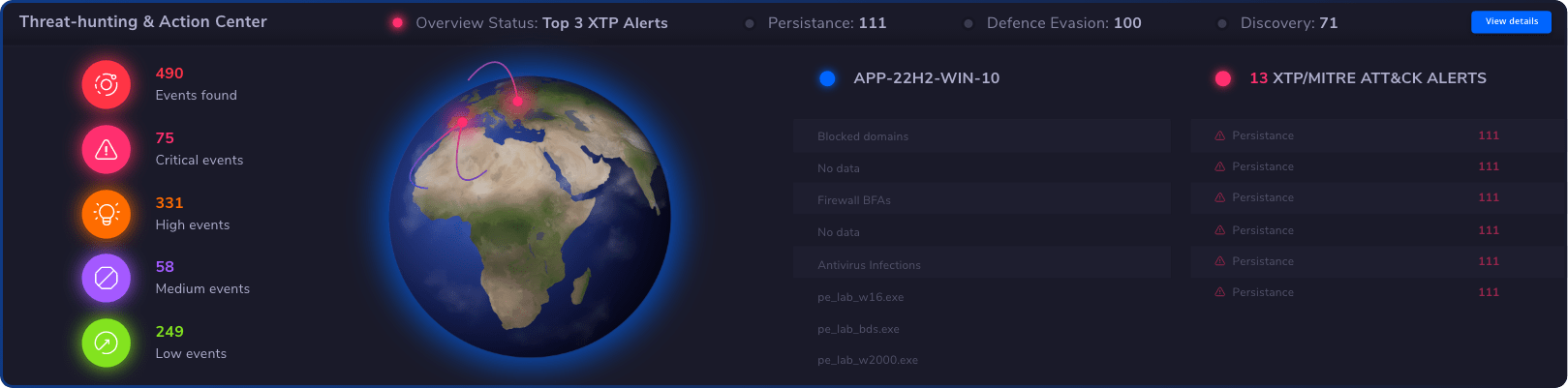
Threat Hunting
Threat-hunting & Action Center
Unified
Endpoint
Management


Patch & Asset Management
Ensure compliance & minimize risks across OS and 3rd Party solutions.
See Heimdal XDR in Action: Schedule a Live Demo Now!