Contents:
A warning comes from Microsoft about a data-wiping malware that poses as ransomware and is being leveraged by threat actors to target several companies from Ukraine. The attacks were identified by Microsoft starting the 13th of January and according to it, their purpose is the destruction of the victim’s information by combining a malicious MBRLocker with a data-corrupting malware.
About the Data-Wiping Attack Employing WhisperGate
Microsoft dubbed the malware family ‘WhisperGate’. The company published a report on this topic pointing out the fact that the malware operates through two distinct components.
The first component was given the name stage1.exe and C:\PerfLogs, C:\ProgramData, C:\ or C:\temp folders are used to launch it, means by which Master Boot Record is overwritten in order to show a ransom note.
The MBR Lockers use a program whose role is to perform encryption on the partition table and show a ransom note to replace the loader in the master boot record with it. This way, the operating system will not be able to load and the information becomes inaccessible until the decryption key for it is provided and the ransom paid.
The second component is dubbed stage2.exe. It will be executed at the same time in order to download malware that destroys data. This is called Tbopbh.jpg, being located on Discord. The targeted files will be overwritten with static data.
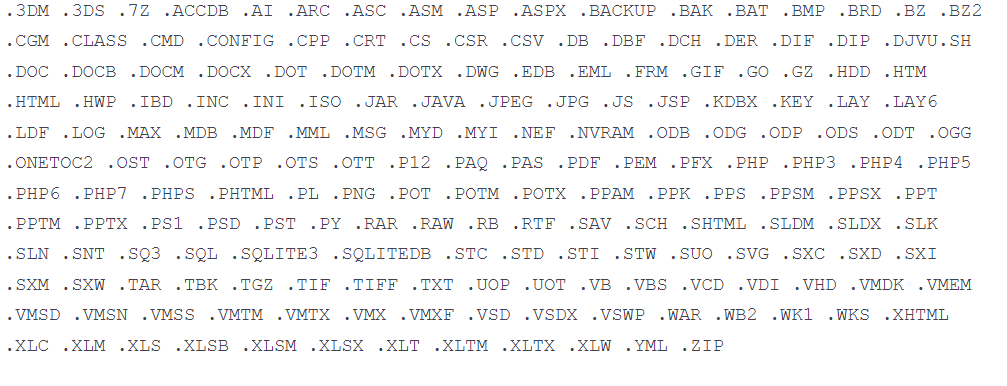
After the overwriting process will be completed, every file will be renamed by the destructor by means of a four-byte extension.
Here are the file extensions targeted by this second component
Is the Ransomware False? Particularities of the Ransom Note
What does the WhisperGate ransom note display? It contains a message urging the victim to send $10,000 to the address 1AVNM68gj6PGPFcJuftKATa4WLnzg8fpfv as the transfer should be made in bitcoin. Then, the victim should use a Tox chat ID to contact the hackers.
Here is an illustration of the ransom note displayed by Microsoft in their report:
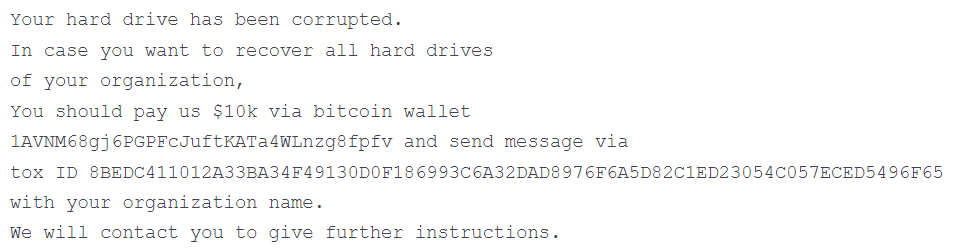
The fact that the victims should use a Tox chat ID to contact the threat actors makes Microsoft be of the opinion that the ransomware is false, as the researchers state.
The same money transfer address is leveraged for all the victims in the ransom note. However, a way to input the decryption key is not specified.
Ransomware payloads are typically customized per victim. In this case, the same ransom payload was observed at multiple victims. (..) Explicit payment amounts and cryptocurrency wallet addresses are rarely specified in modern criminal ransom notes, but were specified by DEV-0586. The same Bitcoin wallet address has been observed across all DEV-0586 intrusions and at the time of analysis, the only activity was a small transfer on January 14. (…) It is rare for the communication method to be only a Tox ID, an identifier for use with the Tox encrypted messaging protocol. Typically, there are websites with support forums or multiple methods of contact (including email) to make it easy for the victim to successfully make contact. (…) Most criminal ransom notes include a custom ID that a victim is instructed to send in their communications to the attackers. (…) The ransom note in this case does not include a custom ID.
says Microsoft emphasizing the fact that this activity appears to not be related to a typical ransomware activity, hence the opinion that is not ransomware.
What’s more, is that Microsoft classifies this as a destructive cyberattack instead of indicating it as a ransomware attack because neither of the two malicious components described above provides means to enter the decryption keys in order to recover the lost data, and also static undecryptable data is used to overwrite the files.
Ukraine Organizations Targeted
At least fifteen websites belonging to government agencies and public institutions from Ukraine were impacted by hacking attacks and eventually went down, according to BleepingComputer.
The websites were defaced by the threat actors and visitors will see a message that warns them about the data theft and potential public release of the stolen data.
New accounts on RaidForums were created by hackers in order to release the allegedly stolen information. Some threat actors reviewed the data and assert that this has no relation with Ukraine government agencies, but instead includes information from an old leak.
Ukraine related these cyberattacks to Russia, as a public statement released by the Ukraine government states:
Russia’s cyber-troops are often working against the United States and Ukraine, trying to use technology to shake up the political situation. The latest cyber attack is one of the manifestations of Russia’s hybrid war against Ukraine, which has been going on since 2014.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










