Contents:
The financial cybercrime world is facing new threats. As hackers become more creative day by day, they are also cunning and determined to become pros. A 2017 IBM-X-Force Research pointed out a fresh new malware entering the cybersecurity domain: the IcedID Banking Trojan. This targeted mobile service and payment card providers, bank web-mails, and e-commerce websites and acted through a modular malicious code. Now, a mid-March Kaspersky report traced two new spam campaigns that promote an enhanced variant of the malware.
What Is an IcedID Banking Trojan and How Does it Work?
IcedID stands for modular banking trojan. Its goal is to deploy several second-stage malware payloads. Among these malware Ryuk ransomware, Qakbot and TrickBot can be found. These types of malware can perform actions like: credential and financial theft, additional modules download and attempts to deploy more payload through users’ networks.
IcedID Banking Trojan and Emotet: Similar in Techniques
Emotet is part of the banking trojans family and represents a kind of malware that would spread through spam e-mails pretending to belong to reliable companies. It made its appearance in 2014 and has 3 ways of attack: phishing links, malevolent scripts, and macro-enabled files.
How is this similar to IceID Banking Trojan? Both are modular malware and they started their spreading as financial data thief malware.
Two Spam Campaigns Ongoing: Face the New Threat
Kaspersky’s researchers traced and discovered 2 new phishing campaigns targeted by the IceID Banking Trojan, upgraded versions of those from 2017.
The first campaign was called by Kaspersky analysts DotDat and it acted as below:
- Users received spam e-mails with .zip files referred as: [document type (optional)]-[some digits]-[date in MMDDYYYY format] format.
- These indicated some sort of compensation claims or operations that were canceled.
- A compromised Excel file with Excel 4.0 macro formulas came alongside this archive.
- By accessing an URL it led to a macro that downloaded and executed a malicious payload.
- The payload could pose as QBot or IcedID downloader (Trojan.Win32.Ligooc).
- Windows Rundll32 and EXEC function were then used after downloading to launch the payload.
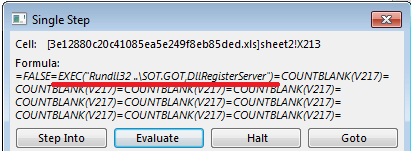
The second phishing campaign, by its name Summer.gif, performed the following steps:
- Users received phishing e-mails containing malicious URLs that were home for .zip files again.
- It followed the same pattern, in terms that the archives contained macro embedded- Excel files.
- 2 functions characterized the second campaign: the URLDownloadToFile function and Excel 4.0 macro formulas.
- This time though, the URL could be found in a malicious file’s cell.
- Summer.gif stands apparently for a gif picture, but it hid an executable payload displayed through regsvr32 tools and WMI.
Upgrading Raised to Another Level: a New IcedID Downloader in Plain Sight
The main feature that enhanced the IcedID Banking Trojan was the addition of a new Downloader, as explained on ThreatPost. The IcedID is made of 2 parts: the core body and the downloader. They work in synergy, the downloader breaks the ice by obtaining the image, decrypting, and executing. After that, the main body takes over the course of action and maps into the memory, injects the web, downloads and executes payloads and exfiltrates vital data.
The downloader has now an x86-64 version compared to the x86 old one and is better in terms of C&C addresses, as the old version provided fake C&C addresses that led to a wrong analysis.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security