Contents:
This year reveals Ryuk Ransomware’s predilection towards targeting hosts with remote desktop connections exposed on the public Internet. What’s more, the threat actors’ personal favorite initial infection vector continues to be the targeted phishing emails for malware delivery.
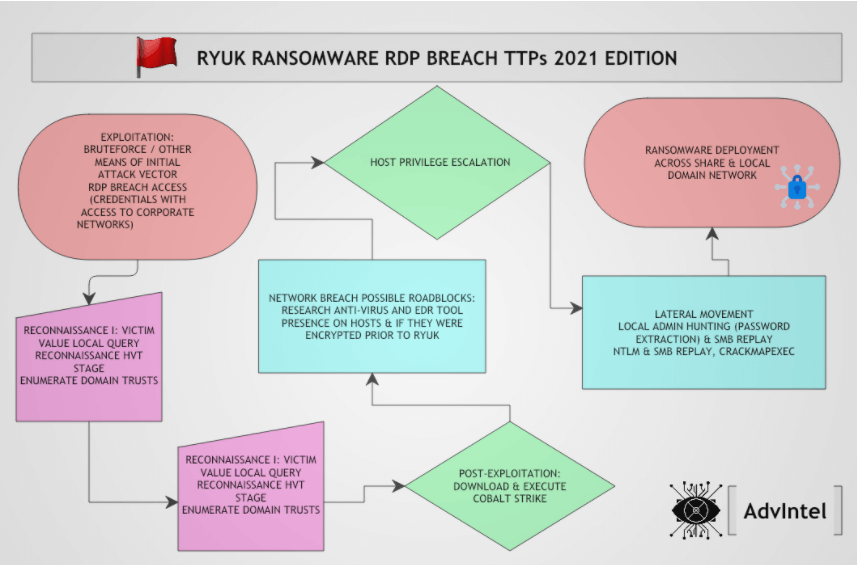
Image Source: AdvIntel
According to a report issued by Advanced Intelligence (AdvIntel) security researchers, this year, Ryuk ransomware attacks relied more often on compromising exposed RDP connections to gain an initial foothold on a target network.
Additionally, spear phishing was another vector for initial compromise, as well as the use of the BazarCall campaign to distribute malware through malicious call centers. The latter targeted corporate users and directed them to weaponized Excel documents.
AdvIntel has noticed an overall increase of RDP compromise as the initial infection vector across Ryuk-attributed attacks. Threat actors have been observed in the wild employing large-scale brute force and password spraying attacks against exposed RDP-hosts to compromise user credentials.
Targeted phishing emails coupled with the support service center calls such as “BazaCall” have also been observed as an initial infection vector in many Ryuk-attributed attacks. This weaponized document will have instructions that tell the user to “enable content” which will activate a macro and enable the document to download a malicious payload through a PowerShell script that is executed through a command prompt.
Ryuk attackers ran reconnaissance on the victim in two stages, researchers say. First, to determine the valuable resources on the compromised domain (network shares, users, Active Directory Organization Units). And second, to find information on the company’s revenue in order to set a ransom amount that the victim can afford to pay to recover systems.
What’s more, to discover attack paths, Ryuk ransomware operators rely on the tried and tested AdFind (AD query tool) and the post-exploitation tool Bloodhound that explores relationships in an Active Directory (AD) domain.
Accessing victims’ financial details relies on open-source data. AdvIntel researchers say that the hackers look for information about the company’s recent mergers and acquisitions and other details that can benefit them on services like ZoomInfo.
The Cobalt Strike post-exploitation tool has become a standard in most ransomware operations and scans that reveal the security products like antivirus and endpoint detection response (EDR) defending the network.
New Ryuk Ransomware Techniques
Ryuk ransomware operators engage other cybercriminals to learn about the defenses on a network they attack to find a way to disable them.
New Ryuk techniques the researchers saw in their attacks include KeeThief, an open-source tool for extracting credentials from KeePass password manager, the deployment of a portable version of Notepad++ to run PowerShell scripts on systems with PowerShell execution restriction, as well as the usage of the open-source CrackMapExec penetration tool to extract admin credentials and move laterally on the victim network.
This year, researchers say that Ryuk ransomware attacks are exploiting two high-severity vulnerabilities to increase their permissions on a compromised machine.
- CVE-2018-8453 – An elevation of privilege vulnerability exists in Windows when the Win32k component fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
- CVE-2019-1069 – An elevation of privilege vulnerability exists in the way the Task Scheduler Service validates certain file operations. An attacker who successfully exploited the vulnerability could gain elevated privileges on a victim system.
AdvIntel security researchers recommend the following risk mitigations:
- Detections for use of Mimikatz and PsExec execution within the network.
- Detections and alerts for the presence of AdFind, Bloodhound, and LaZagne within the network.
- Ensure all operating systems and software are up to date with the latest updates and security patches.
- Implement multi-factor authentication for RDP access.
- Implement network segmentation and controls to scrutinize SMB and NTLM traffic within the network.
- Routinely review account permissions to prevent privilege creep and maintain principle of least privilege.
- Routinely review Group Policy Objects and logon scripts.
- Update systems to prevent exploitation of CVE-2018-8453 and CVE-2019-1069.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










