Contents:
Network Access Control (NAC) is a cybersecurity technology that regulates access to network resources based on predefined policies and regulations. By identifying, verifying, and assessing the compliance of devices and users trying to connect to a network, NAC helps guarantee that only authorized and secure devices obtain access.
It does this by checking device characteristics, such as the operating system version and the status of the security software, against specific security standards. After verification, NAC grants access levels accordingly, varying from complete access to restricted or no access at all. Throughout the connection, most NAC systems continuously monitor the device to ensure continuous compliance, changing or revoking access rights if necessary.
Continuous monitoring of connected machines guarantees that network security policies are followed at all times. A fundamental requirement for any organization’s Zero Trust Security approach is the ongoing verification of device compliance.
The Importance of NAC for Organizations
The need for control becomes more pressing when an organization’s endpoint number grows, mostly as a result of BYOD (Bring Your Own Device) policies and increasing IoT device usage. Even the largest IT organizations cannot manually configure each and every piece of equipment in use. The automation provided by NAC technology has many benefits, reducing the time and cost needed to verify users and make sure their devices adhere to compliance standards.
Furthermore, threat actors are keenly observing the increase in endpoint usage and constantly developing and launching sophisticated campaigns to abuse vulnerabilities in corporate networks. An increase in endpoints broadens the potential attack surface, providing cybercriminals with more entry points. NAC solutions can be configured to detect any unusual or suspicious network activity and take immediate action, such as disconnecting the device from the network, to prevent any potential propagation of the threat.
Moreover, enterprises have the flexibility to determine how NAC verifies users and devices attempting to access the network. IT administrators can choose Multi-Factor Authentication (MFA), adding an extra layer of security beyond the standard username and password login information.
Limiting network access also entails control of the applications and data within the network, which are frequently attractive targets for attackers. Enhanced network controls make it more difficult for cyberattacks to penetrate the network.
Types of Network Access Control
There are two basic forms of Network Access Control, and both are vital for network security:
Pre-admission
Pre-admission network access control happens prior to access being given. A user trying to connect to the network sends an entry request. A pre-admission network control evaluates the request and grants access if the device or user can verify their identity.
Post-admission
Post-admission network access control is a security measure that ensures that even after a device or user has been verified and given access to a network, they must request and obtain additional authorization if they attempt to access a new or distinct part of the network for which they have not previously been granted rights. It entails re-verifying a device’s or user’s identity or checking their security posture before they are allowed to access certain areas or resources of the network.
As pre-admission and post-admission NAC work great together, the best approach for an organization is to implement both. This defense-in-depth strategy prevents as many threat actors as possible from accessing the network in the first place and strives to discover any that haven’t been noticed by the security system before they can move laterally and obtain access to even more company resources.
NAC Capabilities
Network Access Control (NAC) systems provide numerous capabilities for improving network security by determining which devices and users have access to network resources. NAC’s key capabilities are as follows:
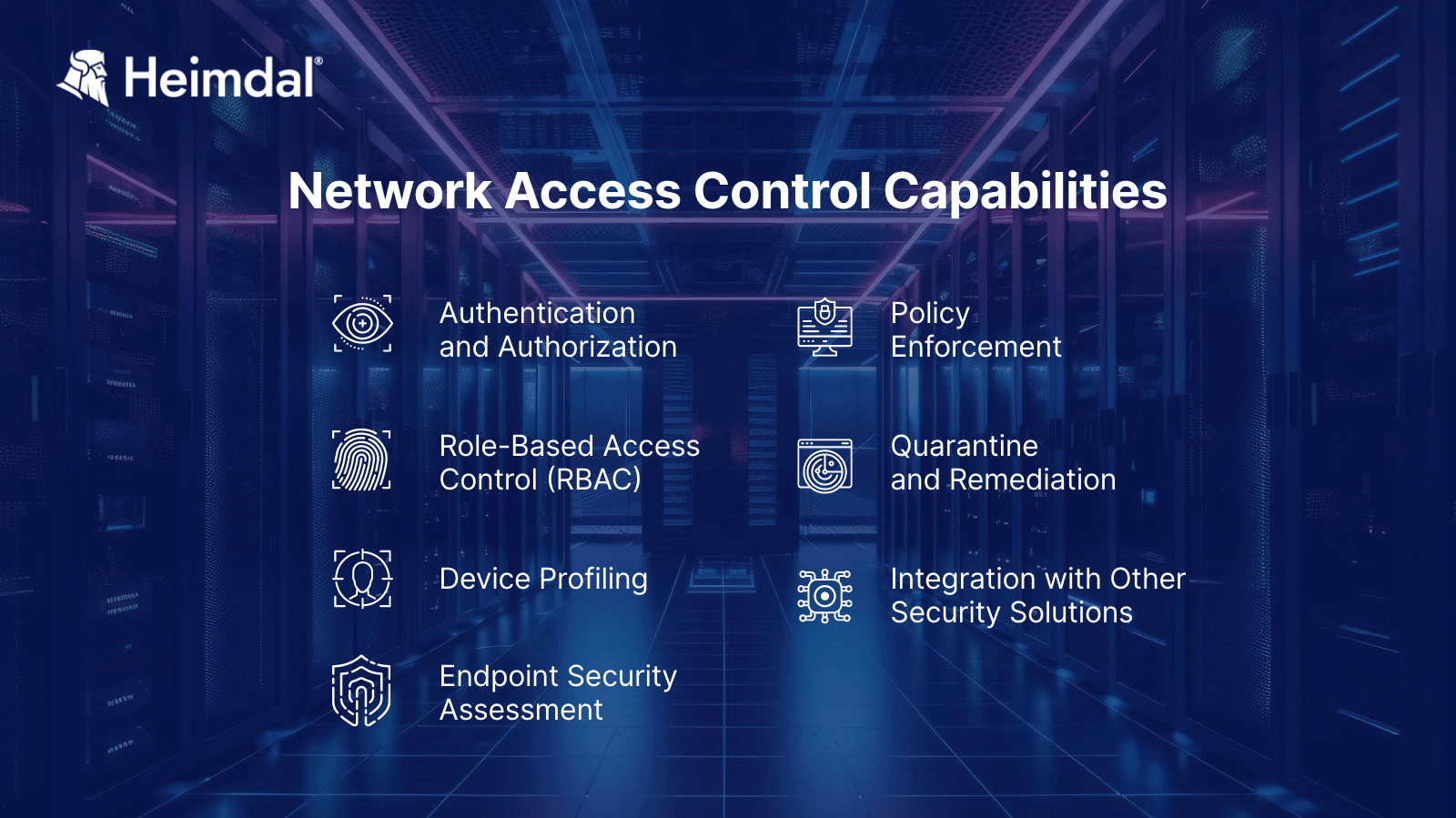
- Authentication and Authorization: Validates users or devices and determines their access level to network resources.
- Role-Based Access Control (RBAC): Assigns access based on the user’s role, like employee or guest, making sure that users only access the resources they need to do their job and nothing else.
- Device Profiling: Identifies and categorizes devices trying to connect, ensuring predefined policies for each device type.
- Endpoint Security Assessment: Before permitting access, it checks devices for security standards, such as updated antivirus software.
- Policy Enforcement: Creates and enforces network access controls based on factors such as device type or user role.
- Quarantine and Remediation: Redirects devices that are not compliant to a restricted area, along with instructions for becoming compliant.
- Integration with Other Security Solutions: Links with systems like Intrusion Detection System (IDS) and s for a comprehensive, layered security approach.
What Are the Benefits of NAC?
Improves Security and Prevents Unauthorized Access
Since NAC manages all devices used in an organization, security is improved while authenticating users and devices as soon as they connect to the network. By actively monitoring network activity and quickly responding to unauthorized access or abnormal activity, the risk of malware and other cyber threats is lowered.
Saves Costs
Automatically monitoring and safeguarding devices on a large scale saves organizations money as they require fewer IT resources. Moreover, stopping unauthorized access or potential malware attacks helps businesses avoid financial setbacks that may result if such incidents are not thwarted.
Automation
As organizations keep adding more diverse devices, it becomes impractical to manually check the security policies of users and their devices when they attempt to enter the network. Network Access Control automation greatly streamlines the process of authenticating and authorizing users and devices.
Enhanced User Experience
Users can effortlessly connect to the network with seamless access. Knowing that there are background security measures give users peace of mind, ensuring their experience is safe without requiring any action from them.
Ease of Control
The NAC’s visibility functions effectively act as an ongoing inventory of all the endpoints that the company has given permission to use. This is helpful for IT when figuring out which users or devices gained network access, and also during life-cycle management when devices need to be retired or replaced.
Meet Compliance
Strict government regulations and data privacy laws dictate how organizations can gather, store, and share data. Without a proper network access control policy, companies can’t clearly see what’s happening with their network resources, devices, and information. In order to safeguard network access and meet regulatory compliance standards, your organization must have an effective NAC strategy.
Stronger Authentication
A benefit of network access controls is that they can mandate users to use multi-factor authentication. This method is far more secure than relying solely on IP addresses or just usernames and passwords for identification.
Network Access Control Use Cases
BYOD (Bring Your Own Device) Management
As work-from-home practices are here to stay, employees commonly use their personal devices for job-related activities. The BYOD (Bring Your Own Device) concept, which enables employees to use their own devices for work, enhances productivity and cuts costs. Workers frequently perform better when using equipment they are familiar with rather than those provided by the employer. Organizations can ensure that both the device and its user are authenticated and allowed network access by integrating NAC policies with BYOD.
Network Access for Non-employees
NAC helps by granting temporary network access to external users (visitors, contractors, consultants, and partners). These users can easily access the network with NAC without requiring direct action from the IT staff. Naturally, the policies governing access for these non-employees should vary from those governing regular employees.
IoT Devices
The Internet of Things (IoT) brings a variety of new devices into corporate networks, many of which might not have robust built-in security measures. The diverse array of devices in today’s landscape presents potential security risks, highlighting the importance of Network Access Control (NAC) for IoT.
NAC enables businesses to effectively detect, classify, and control these devices. NAC guarantees that only compliant IoT devices access the network by establishing specific security criteria and access regulations. Furthermore, it can separate these devices, isolating them from critical network areas, and continuously monitor their behaviour for any irregularities.
Visibility and Reporting
NAC can assist organizations in gaining insight into who and what is connected to their network, which can aid in asset management, compliance reporting, and threat analysis.
Incident Response
NAC systems detect devices that have been compromised and automatically block access to prevent an attack from spreading throughout the network.
How to Choose a Network Access Control Solution
NAC solutions offer a variety of capabilities and claim to improve the overall security posture of your organization’s network. First of all,consider systems that provide native integration with your company’s current software and hardware.
Additionally, look for all-in-one solutions that include firewall mechanisms, virus scanning capabilities, among others. You can also take advantage of free trials to learn about the features and functions of NAC systems.
NAC Implementation
It is important to plan your NAC implementation thoroughly. Here are some steps you can take to ensure a successful outcome.
Gather Information
Collect important data about your network, connected devices, assets, and users before taking a NAC approach. Each endpoint of your network must be thoroughly assessed. It can be difficult to manage identities and give permissions without having this data. Some NAC systems include this data gathering as part of the initial scan.
Manage Identities
Identity management is an essential step in implementing NAC solutions. Setting up and updating directory systems is critical for validating and authorizing user identities. This process also aids in assigning permission roles and providing network access to users.
Apply Permissions
After your IT team has set user permissions, you can directly transfer these access rights, policies, or the whole directory system into your NAC solution, which helps minimize potential security gaps.
Update when Needed
Managing a network is an ongoing process. As your organization grows, it’s essential to keep an eye on security operations and oversee user and device permissions (or automate these operations).
How Can Heimdal® Help with Network Security?
Network Perimeter DNS Security
With Heimdal DNS Security – Network module, you hunt, prevent, detect, and respond to any network and IoT threats. It allows you to confidently own your BYOD governance and secure all your users’ devices.
Heimdal DNS Security – Network uses machine learning on device-to-infrastructure communication to spot and stop attacks that firewalls can’t see, offering you an essential threat-hunting tool to prevent attacks on your network. This module to any Antivirus, Firewall, IDS, or IPS and can be combined with more Heimdal® products to deliver an authentic Endpoint Prevention, Detection, and Response (EPDR) stance. One agent, one platform.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;
Conclusion
Network Access Control (NAC) stands as an indispensable tool in the modern cybersecurity landscape. As organizations struggle with an increasing number of devices and a constantly evolving threat environment, NAC offers a powerful solution to enable secure and efficient network access.
Adopting and regularly updating NAC procedures paves the way for a more seamless and safer organizational workflow, in addition to protecting critical information and systems.
If you enjoyed this article, follow us on LinkedIn, Twitter, Facebook, or YouTube to keep up to date with everything we post!










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








