Contents:
Domain generation algorithms (DGA) are software that creates large numbers of domain names. This helps hackers deploy malware easier. Let`s take a closer look at what DGA is, how it works, and why it’s still popular among threat actors after all these years.
Threat actors use DGA so they can swiftly change the domains they’re using to launch malware attacks. Since cybersecurity providers fastly block and put down malicious domains, hackers developed this technique in response. Using a Domain Generation Algorithm to deploy malware also helps them evade detection.
DGA can provide hundreds of new, random domains. This enables hackers to keep their servers up and running without being blocklisted or taken down by the victim. Malware switch between domains faster than security software can take them down. So, threat actors will be able to carry on with the attack.
How Does a DGA Work?
The domains act as a meeting point for malware C&C servers. The generators have to deliver domains that are predictable for the two communicating entities. But for security researchers, these domains should be as unpredictable as possible.
The process has to be very fast, in order to reach its goal. Domains have to be registered anonymously or untraceable. Also, the registration cost should be very low, hence the increased number of domains needed.
The Domain Generation Algorithms follow a three elements structure:
- A base element called a seed. It can be a phrase or a number that hackers can change when they need it. The seed must be known to both sides of communication: client and source. It is important because the threat actors need to know in advance which domain name the malware will use.
- An element that changes with time. It will be combined with the seed in an algorithm. The word „time” does not refer to a date or hour, but rather to a certain event of the moment.
- Top Level Domains (TLDs). The ”body” constituted from the seed and the time element is combined with available TLDs.
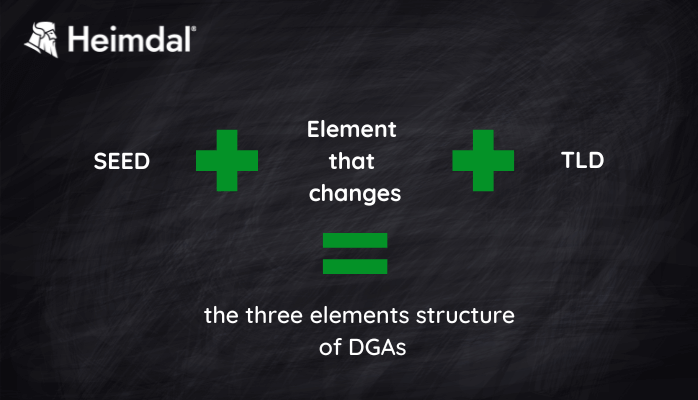
The three elements structure of DGAs
After the hacker knows which will be the domain name, he registers it from the sequence and creates a communication channel for the malware. The moment the domain is marked as malicious and taken down, the domain and C&C server are swiftly switched.
CryptoLocker was a ransomware that was active from September 2013 to May 2014. It encrypted the files on infected computers and demanded a ransom payment in exchange for the decryption key.
How Does Malware Use DGAs
If the Command and Control center relies on a fixed domain or an IP address, it will be easy for the security team to rapidly block it. Threat actors know this, so in return they use DGAs. This enables them to constantly switch the malware to a new domain.
The huge number of meeting points gives law enforcement a really hard time shutting down the malware. So, the hackers don`t need to bother with coming up with a new malware version. Or to set up a new server.
By communicating with command and control systems, the malware and ransomware also receive instructions: on whom to target, encryption keys for ransomware, targets for DDoS bots, etc.
According to researchers, IoT devices are a vulnerable target to DGA attacks.
How to Detect DGA Domains
There are two ways you can spot a DGA domain:
- Reactionary – Check data statistics like DNS responses, IP location, WHOIS, and TLS certificate information.
- Real-time – Analyze the domain name and beware of unnatural sequences of characters.
How to Avoid DGA-powered Malware
A Domain Generation Algorithm is actually a technique that malicious actors use to deploy malware. So in order to keep your machines safe, all you have to do is enforce the usual endpoint security best practices:
- Run anti-malware security software.
- Educate your team not to open attachments that come from unknown sources or „look funny”.
- Never miss a patch. To make sure all the devices are patched in time, use an automatic patch management solution.
- Use machine learning and big data to detect suspicious activities.
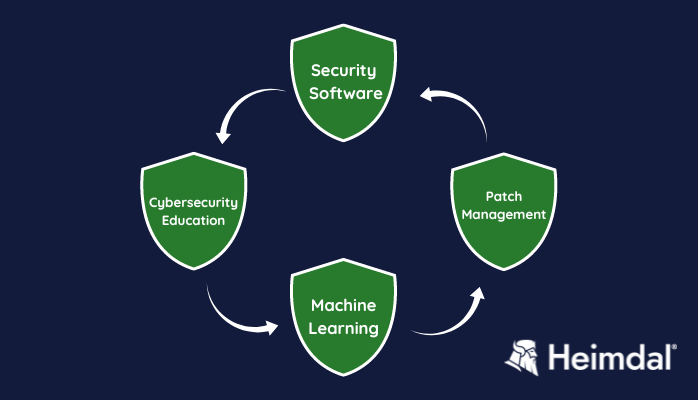
Domain Generation Algorithm (DGA) Practices
Famous Malware Strains That Used a Domain Generation Algorithm
According to researchers, Kraken was, in 2008, one of the first malware families that employed a DGA for its attack. Researchers estimated it had infected 10% of all Fortune 500 companies. Conficker followed the same year.
But over time, the technique became largely employed. Here are some famous examples of malware strains that used a DGA. They all used it to generate new domain names to connect to their C&C servers.
- Conficker, also known as Downup, Downadup, or Kido. It was a computer worm that spread through the Windows OSs in 2008. The malware infected millions of computers worldwide.
- Necurs is a botnet that has been active since 2012. It spread various malware, including ransomware and banking Trojans.
- Gameover Zeus was a banking Trojan that was used to steal banking credentials and other sensitive information from infected computers.
- Torpig, also known as Sinowal or Anserin, was a banking Trojan that targeted Windows computers. The malware stole banking credentials and other sensitive information from infected computers.
How Can Heimdal® Help Detect DGA Activity
Traffic filtering is always a useful tool. But since threat actors started to use DGAs and create thousands of domains, it has become impossible for the human eye to follow.
Heimdal`s Threat Prevention – Endpoint solution comes with the DarkLayer Guard engine. This is currently the world’s most advanced endpoint DNS threat-hunting tool. Its filtering engine deals with over 800.000 new weekly updates, roughly.
This way, the endpoint users will not be able to establish untrusted connections and open the gate for zero-day attacks or execute remote shellcodes.
But I`ll let one of our long-term customers explains it best:
The ability to also protect mobile clients from phishing schemes, malware attacks, adware, and many more security risks when not behind the corporate office firewalls has saved us from numerous threats and possible infection of our internal networks.
Luckily, the DarkLayer Guard prevents malware from communicating with criminal infrastructure by blocking it at the traffic level, which is a massive advantage.
Robert Vilhelmsen, Senior System Manager AXEL KAUFMANN ApS

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
Wrap Up
Threat actors had been using domain generation algorithm for about years. So, this is not at all a new technique. However, after all these years, it is still effective and, of course, useful to malicious actors.
We will keep reading about malware and ransomware attacks where DGAs were used. For a security team that is not supported by top technology, being under this kind of attack is overwhelming. And as it happens with cyberattacks, it is not anymore a matter of ”if”, but a matter of ”when” a company can become a target.
Don`t let this kind of event catch you off guard! Upgrade your endpoint protection strategy and partner with the best. Choose cutting-edge cybersecurity solutions to avoid being a victim of DGA-fueled malware.
And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







