Contents:
Vulnerability management proactively identifies, prioritizes, and fixes security weaknesses to reduce an organization’s exposure to threats.
Its goal is to lower the risks these vulnerabilities pose to an organization.
This task can be difficult due to the large number of possible vulnerabilities and the limited resources for fixing them.
Key Takeaways:
- Definition and Purpose of Vulnerability Management;
- Vulnerability Management vs. Patch Management;
- Vulnerability Management vs. Vulnerability Assessment;
- Vulnerability Management vs. Risk-Based Vulnerability Management (RBVM);
- Vulnerability Ranking;
- The Vulnerability Management Process;
- Benefits of Vulnerability Management;
- Vulnerability Management Best Practices.
Vulnerability Management vs. Patch Management
Vulnerability management is an active approach to find, stop, lessen, and categorize security weaknesses.
Different types of vulnerabilities need different solutions.
Patch management is a key part of this, focusing on fixing software vulnerabilities by applying updates or ‘patches. It’s a crucial part of the overall process of managing vulnerabilities.
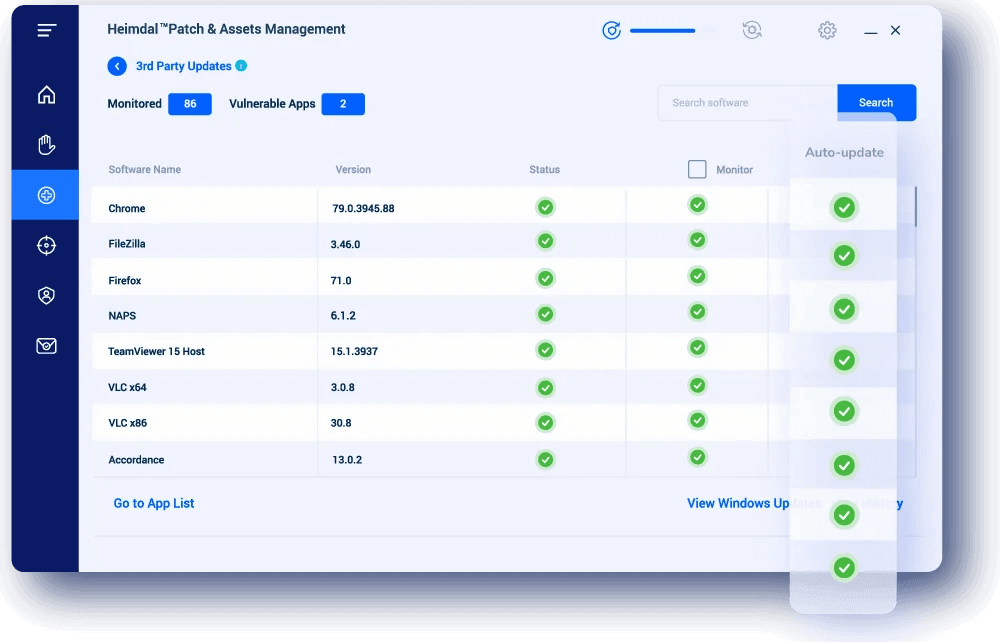
For more details on how they differ, you can refer to a previous article I wrote.
Vulnerability Management vs. Vulnerability Assessment
Usually, a vulnerability assessment is part of the larger process.
Organizations often run multiple vulnerability assessments to come up with an effective vulnerability management program.
Vulnerability Management vs. Risk-Based Vulnerability Management
Risk-based vulnerability management (RBVM) is a cybersecurity strategy that allows organizations to use security intelligence to identify, prioritize, and address the most serious vulnerabilities based on the context of their risk.
This concept is also met under the name of Vulnerability Risk Management.
Unlike vulnerability management, RBVM is a risk-based approach that focuses on the likelihood of a vulnerability being exploited, rather than just on the severity of potential consequences if it is exploited.

How Are Vulnerabilities Ranked?
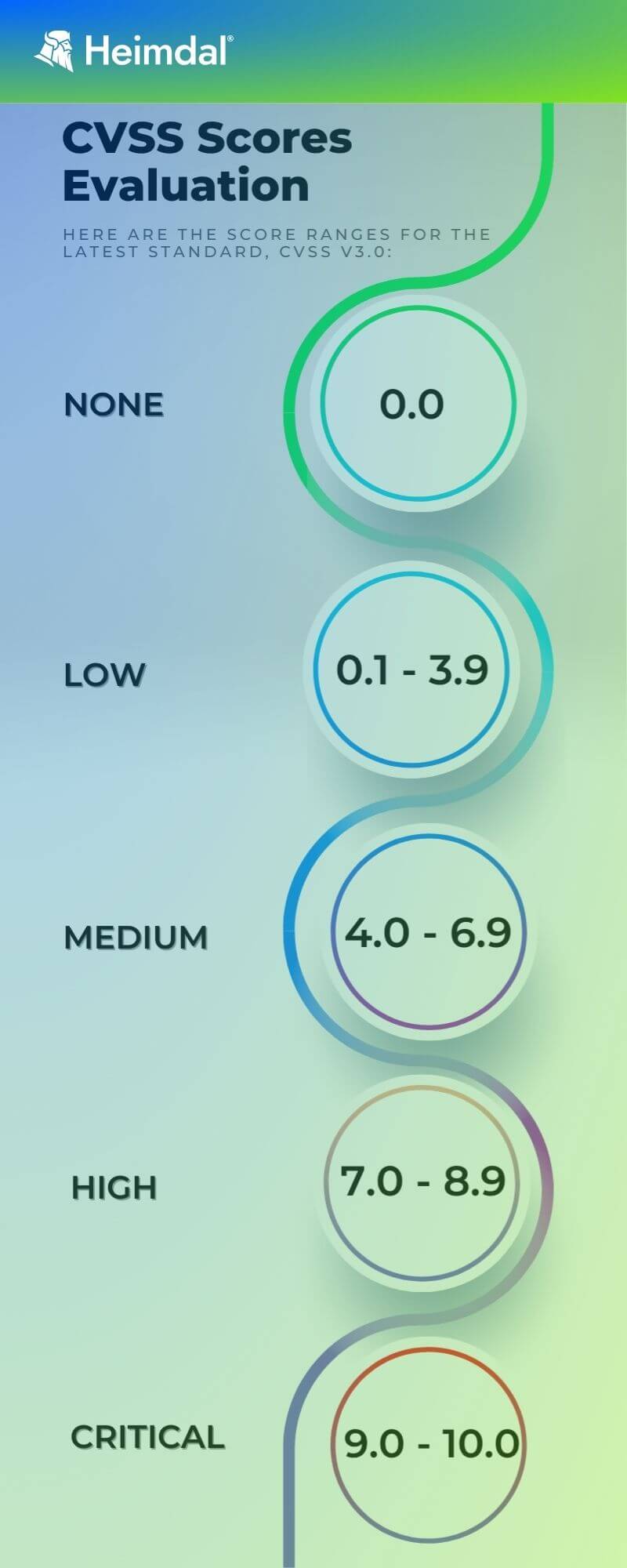
Many cybersecurity organizations use the Common Vulnerability Scoring System (CVSS) to assess and convey software vulnerabilities’ severity and characteristics.
It is a free and open industry standard. The CVSS Base Score ranges from 0.0 to 10.0, and CVSS scores are given a severity grade by the National Vulnerability Database (NVD).
The NVD also contains vulnerability data that automated vulnerability management solutions and IT staff pull from.
Vulnerability Management Process
- Asset Discovery: Create an inventory of your organization’s assets such as software, hardware, operating systems, and services.
- Asset Prioritization and Categorization: Once you complete the inventory, classify assets by risk level and importance to business operations.
- Vulnerability Assessment: Establish baseline risk profiles and prioritize. Assess each asset for criticality and vulnerability.
- Reporting: Assess and document the risk levels for each asset. Report your security plan and any known vulnerabilities.
- Remediation: Address vulnerabilities, typically by applying patches.
- Reassessment: Check the effectiveness of the solutions after fixing vulnerabilities.
- Verification and Monitoring: Regularly verify and monitor to ensure all threats are managed.
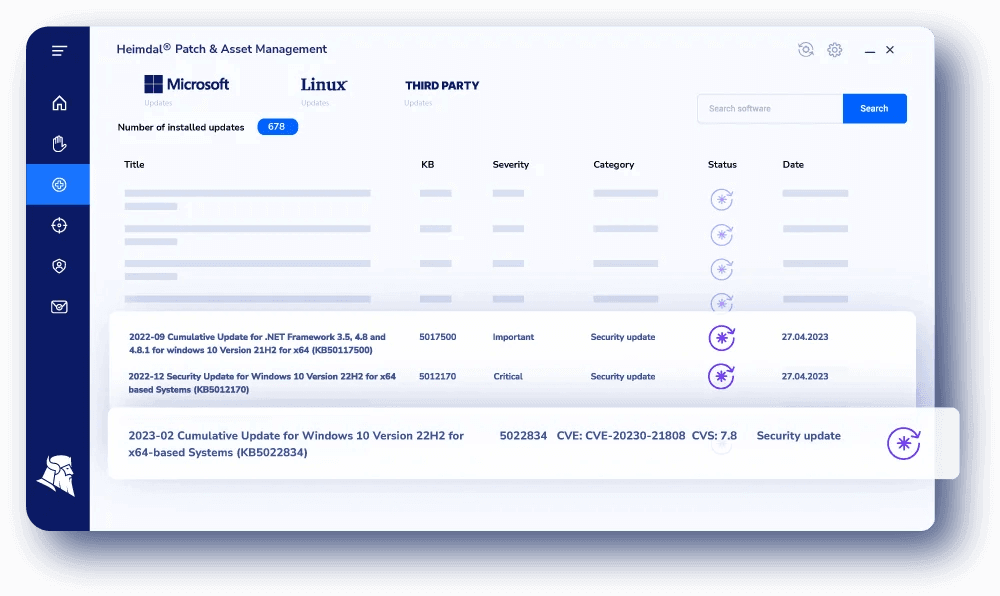
With our Heimdal® Patch & Asset Management module, patching can be fully automated, allowing you to schedule the process according to your own needs.
Benefits of Vulnerability Management
Improved Security and Control
Regular vulnerability scans and prompt patching make it harder for attackers to access systems.
A strong program also allows organizations to spot security weaknesses before attackers do.
Cost-Effectiveness
It is cost-effective because automated solutions prevent poor patching and reduce technical debt.
It clarifies and strengthens your security stance, which can win stakeholder support.
Quick Response to Threats
Attackers never rest, and vulnerabilities can appear anytime.
Vulnerability management shifts your response from reactive to proactive.
Establishing a continuous patch management strategy ensures quick identification and prioritization of major threats, enabling faster, more effective responses.
Enhances Visibility and Reporting
Visible projects help stakeholders see the security investment’s return and guide future projects.
Reports provide senior management with essential metrics for informed decision-making.
These reports also offer the team actionable dashboards and trends, helping them monitor program performance.
Operational Efficiency
Aligning teams and systems with security objectives is critical.
The process helps find and fix vulnerabilities to maintain this alignment.
It reduces manual tasks, enhances continuous monitoring, and ensures timely alerts and fixes.
Best Practices
- Conduct Asset Discovery and Inventory: Include all devices and software owned by your organization and third-party vendors. This helps identify which assets are most at risk and prioritizes vulnerability scanning.
- Classify Assets and Assign Tasks: Classify identified assets based on their vulnerability risk. This classification guides the frequency of scans and priority of remediation efforts.
- Prioritize Vulnerabilities and Take Action: After scanning, prioritize vulnerabilities based on their impact and take appropriate corrective actions.
- Set Up a Comprehensive Strategy: Develop a strategy that encompasses people, processes, and technology to manage vulnerabilities effectively. Establish clear KPIs to guide the security team and assess ROI.
How Can Heimdal® Help?
Vulnerability management is ongoing.
Handling it manually can stress your IT team and tie up resources for long periods.
Manual management also has a high error rate.
Choosing an automated solution is often the best approach today.
Fortunately, Heimdal® Patch & Asset Management solution is ideal for your organization.
With our solution, you will be able to:
- Patch Windows, Linux, macOS, Third-Party, and even proprietary apps, all in one place;
- Generate software and assets inventories;
- Easily achieve compliance with automatically generated detailed reports (GDPR, UK PSN, HIPAA, PCI-DSS, NIST);
- Automatically conduct vulnerability and risk management processes;
- Close vulnerabilities, mitigate exploits, deploy updates both globally and locally, anytime, from anywhere in the world;
- Customize your solution to perfectly fit the needs of your organization.
Enjoy a fully customizable, hyper-automated solution, that you govern! Additionally, we deliver to your endpoints locally utilizing HTTPS transfers encrypted packages that have been repackaged and are ad-free.

Heimdal® Patch & Asset Management
- Create policies that meet your exact needs;
- Full compliance and CVE/CVSS audit trail;
- Gain extensive vulnerability intelligence;
- And much more than we can fit in here...
If you want to keep up to date with everything we post, don’t forget to follow us on LinkedIn, X, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








