Contents:
A new email phishing operation has been noticed employing the conversation hijacking strategy to distribute the IcedID banking trojan-type malware onto compromised computers via unpatched and publicly-exposed Microsoft Exchange servers.
According to an Intezer report shared with The Hacker News,
The emails use a social engineering technique of conversation hijacking (also known as thread hijacking). A forged reply to a previous stolen email is being used as a way to convince the recipient to open the attachment. This is notable because it increases the credibility of the phishing email and may cause a high infection rate.
The most recent wave of attacks, which began in mid-March 2022, is believed to have targeted businesses in the energy, healthcare, legal, and pharmaceutical industries.
What Is IcedID?
IcedID (also known as BokBot) is a banking trojan-type malware that allows malicious actors to steal victims’ banking information. It was first discovered by security researchers in 2017.
More advanced threats, such as human-operated ransomware and the Cobalt Strike threat emulation software, have used this malware as an entry point.
IcedID M.O.
The IcedID banking trojan can communicate with a remote server and download next-stage implants and software, enabling threat actors to perform follow-on activities and move laterally across impacted networks to spread additional malware.
In June 2021, American enterprise security company Proofpoint revealed an evolving cybercrime strategy in which initial access brokers were noticed invading target networks via first-stage malware payloads such as IcedID to deploy Egregor, Maze, and REvil ransomware payloads.
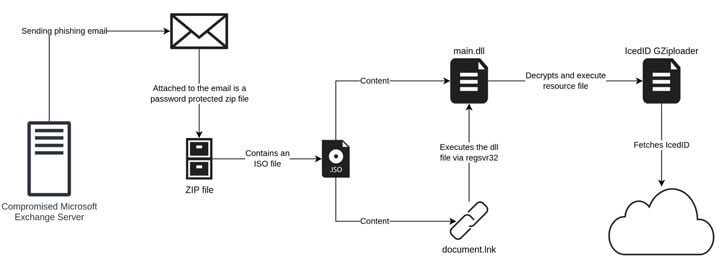
Earlier IcedID operations used website contact forms to deliver malware-laced links to companies; however, the newest variant of the attacks uses vulnerable Microsoft Exchange servers to send the bait email messages from a hijacked account, denoting that the social engineering scheme has evolved.
The payload has also moved away from using Office documents to the use of ISO files with a Windows LNK file and a DLL file. The use of ISO files allows the threat actor to bypass the Mark-of-the-Web controls, resulting in execution of the malware without warning to the user.
To make the phishing emails seem more authentic, the compromised individual’s email address is used to send fraudulent replies to an already existing email thread removed from the victim’s account.
The use of conversation hijacking is a powerful social engineering technique that can increase the rate of a successful phishing attempt. By using this approach, the email appears more legitimate and is transported through the normal channels which can also include security products.
How Can Heimdal™ Help?
Heimdal Security has developed two email security software aimed against both simple and sophisticated email threats: Heimdal Email Security, which detects and blocks malware, spam emails, malicious URLs, and phishing attacks, and Heimdal Email Fraud Prevention, a revolutionary email protection system against employee impersonation, fraud attempts – and BEC, in general.
For example, you may want to consider Heimdal Security’s Heimdal Email Fraud Prevention, the ultimate email protection against financial email fraud, C-level executive impersonation, phishing, insider threat attacks, and complex email malware. How does it work? By using over 125 vectors of analysis and being fully supported by threat intelligence, it detects phraseology changes, performs IBAN/Account number scanning, identifies modified attachments, malicious links, and Man-in-the-Email attacks. Furthermore, it integrates with O365 and any mail filtering solutions and includes live monitoring and alerting 24/7 by our specialists.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










