Contents:
A new year brings about countless new opportunities, but also, unfortunately, the chance for old threats to make a comeback and evolve. Such is the case with Egregor ransomware. Since anticipation and prevention are more than welcome, let’s find out more about Egregor and what you can do to combat this type of ransomware in order to keep your business safe.
What Is Egregor Ransomware?
Egregor ransomware is a sophisticated piece of ransomware linked to the now-retired Maze ransomware and to the Sekhmet ransomware family that has been active since September 2020. The name itself derives from an occult concept representing a distinct non-physical entity that arises from a collective group of people.
As you probably heard, Maze ransomware was particularly dangerous as it was not only used to steal data and encrypt it like any other ransomware, but its operators also threatened to expose this data if they didn’t receive the ransom, which transformed the attack into a data breach as well. Egregor News is an extortion website used by the threat actors to disseminate the names and domains of their victims, as well as data sets. The website includes details about the date when they were targeted, links for downloading the stolen data, and even social media buttons for the users to spread the word. If the victim does not pay within three days, the attackers will continue to disclose further information in increments ranging from 1% to 100% of the entire stolen information. Barnes & Noble has been the most high-profile Egregor victim to far, with the ransomware authors claiming they took unencrypted data before encrypting files on their computers back in October 2020.
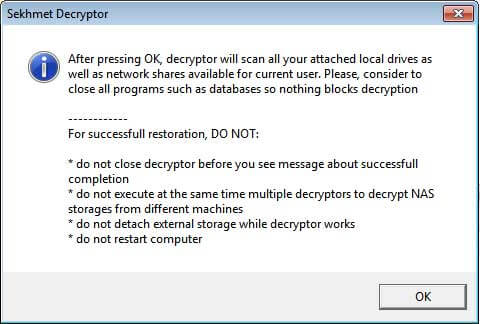
According to ransomware expert Michael Gillespie, who analyzed both Egregor and Sekhmet, Egregor victims who paid a ransom were sent decryptors that were titled ‘Sekhmet Decryptor.’
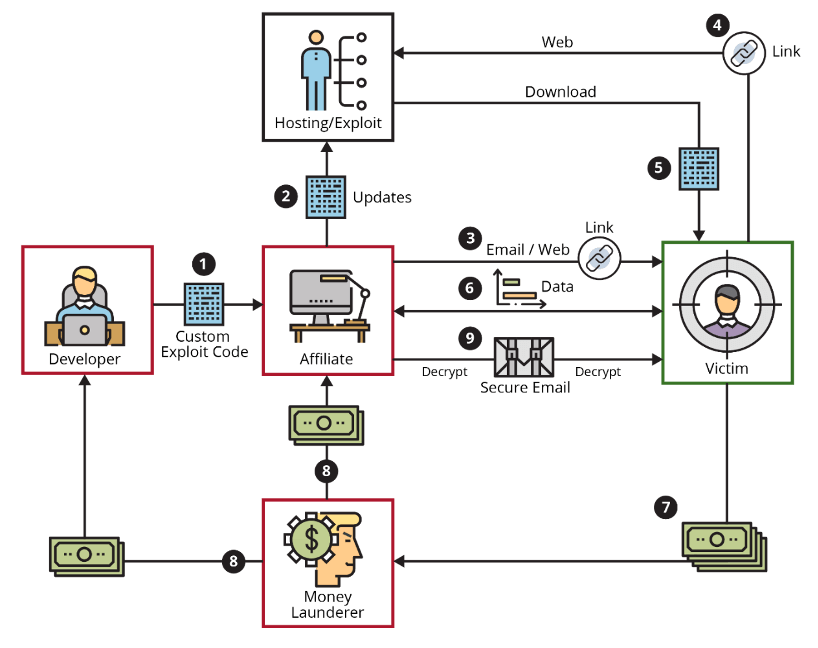
The first mention of Egregor Ransomware on a forum happened on the 18th of September 2020. ZDNet writes that “Egregor has also been associated with the Ransomware-as-a-Service (RaaS) model, in which customers can subscribe for access to the malware.” Ransomware-as-a-Service is a model that allows any novice cybercriminal to launch ransomware attacks by becoming an affiliate of a RaaS package or service.
However, researchers don’t know much about it, since the ransomware protects itself with various anti-analysis techniques, like payload encryption and code obfuscation, but one thing is clear: Egregor ransomware operators, just like in the case of Maze ransomware, threaten to release the stolen data if the ransom is not paid (within the mythical three days).
Ransomware-as-a-Service Workflow
Egregor Ransomware Operating Mode
Initial access is gained through a variety of ways, including the use of stolen credentials, remote access technology hacking, and spear-phishing operations targeting specific employees with harmful attachments. To surreptitiously discover knowledge about their victim’s network and migrate laterally, threat actors employ the threat emulation toolset Cobalt Strike.
To avoid analysis and detection by security solutions, the code employs obfuscation techniques. Popular endpoint security systems are attempted to be uninstalled or disabled using PowerShell scripts. The payload then executes, leaving users with a ransom message demanding payment within a three-day deadline to avoid their data being leaked online. If the criminals receive their money in the appointed time, the victims’ data gets fully decrypted.
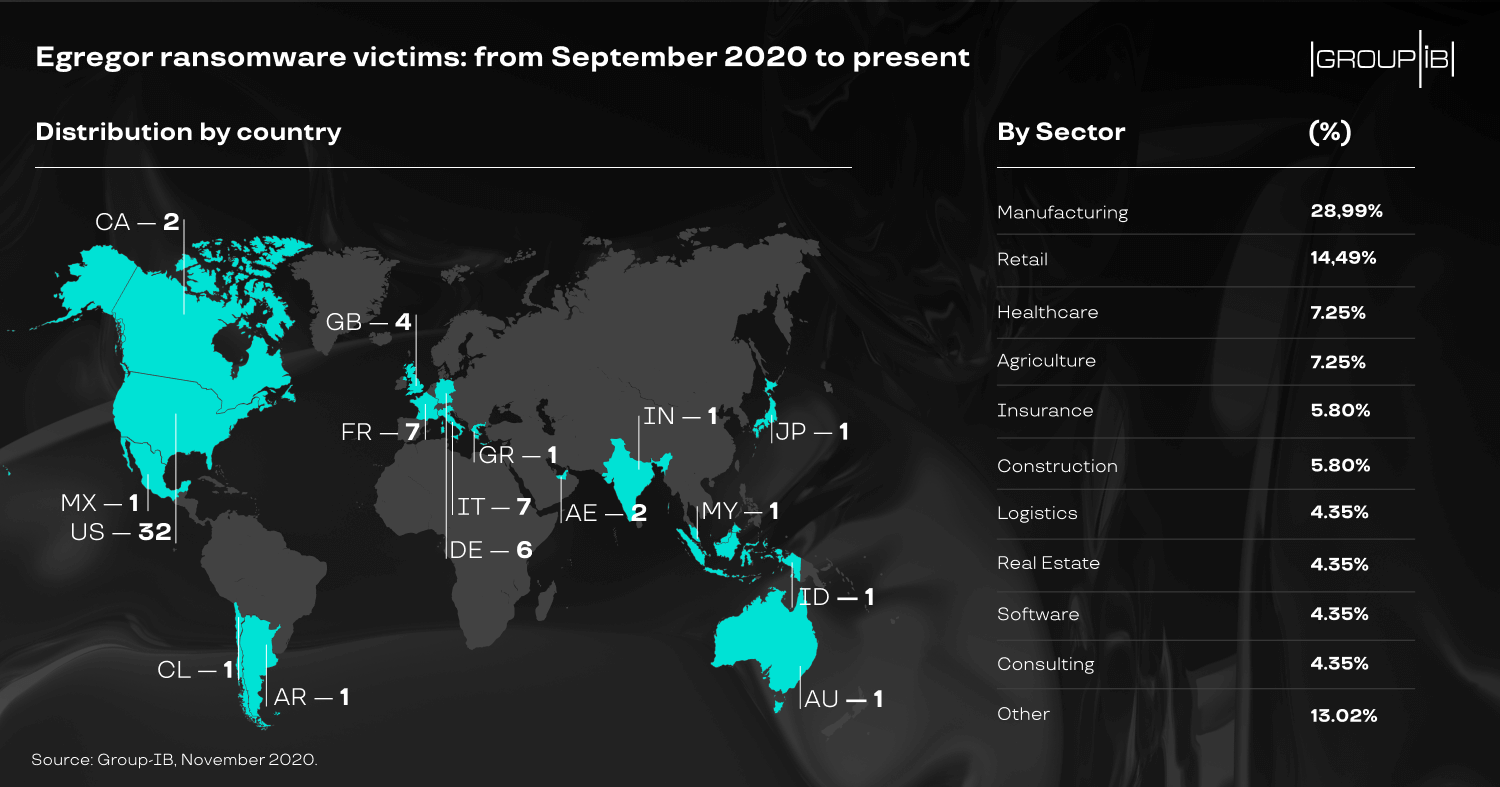
Demographically speaking, Egregor ransomware seems to target the same victims as Sekhmet and Maze.
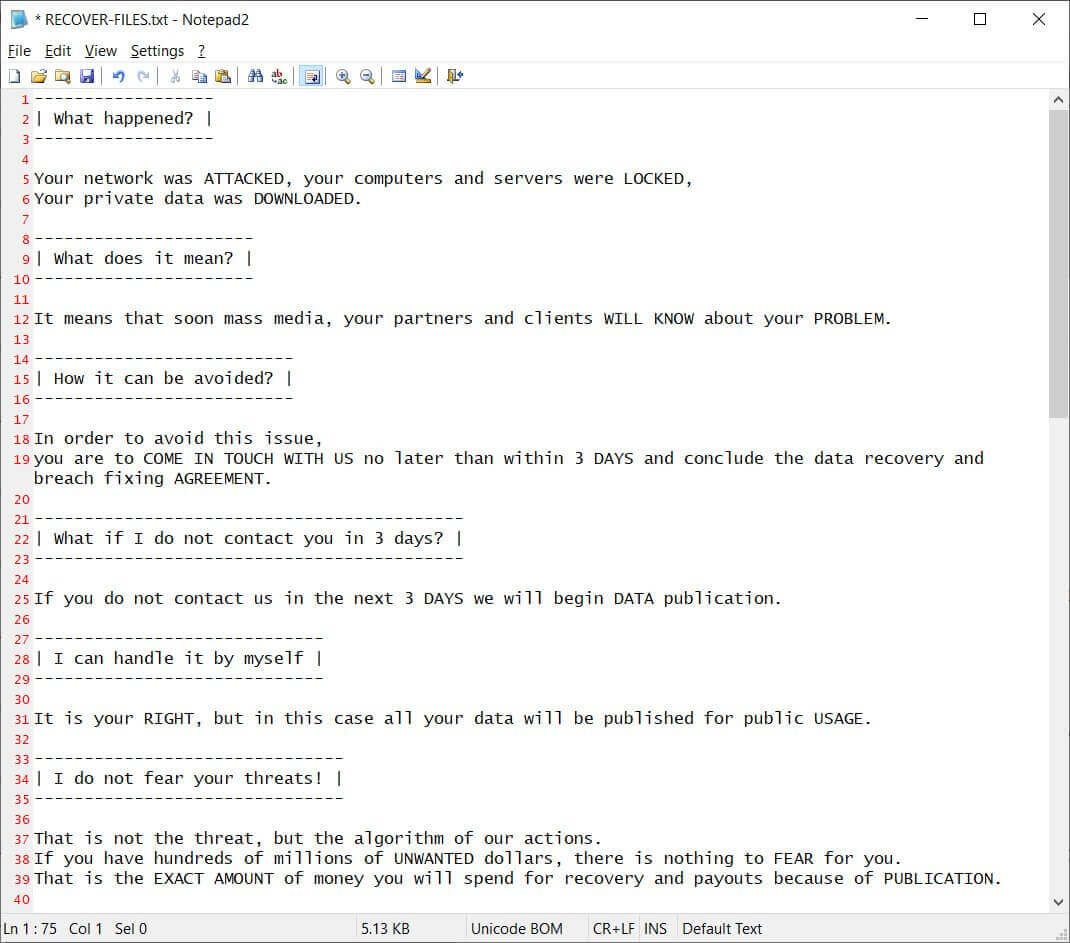
Egregor ransomware infection happens via a loader, then, in the victim’s firewall, it enables the Remote Desktop Protocol. After this part, the malware is free to move inside the victim’s network, identifying and disabling all the antivirus software it can find. The next step is the encryption of the data and the insertion of a ransom note named “RECOVER-FILES.txt” in all the compromised folders.
Afterward, the victims are told to download a dark web browser to communicate with the cybercriminals with the help of a dedicated landing page.
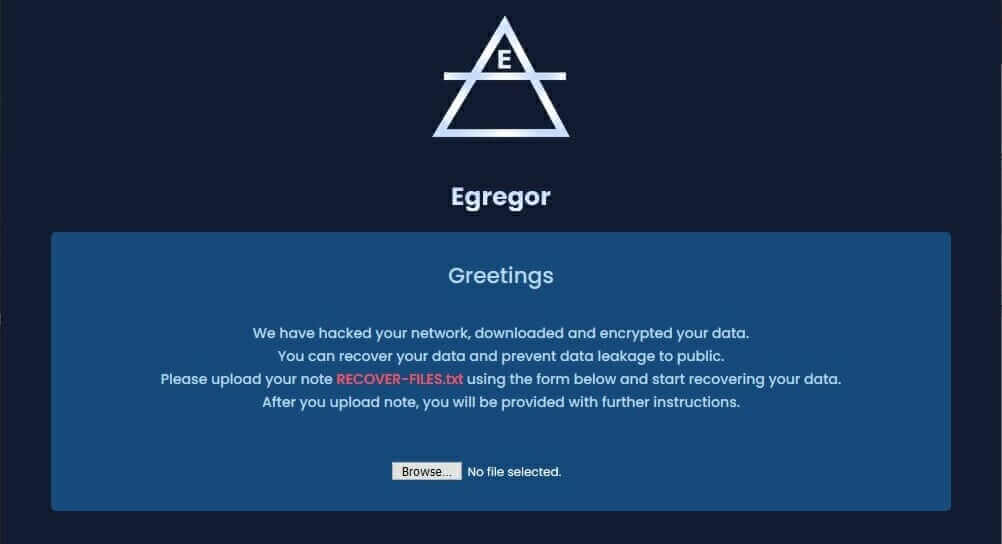
Egregor Ransomware landing page
Egregor Ransomware Attacks
Since September 2020, Egregor Ransomware has had an impressive number of victims. We’ll mention just a few:
October 2020
Barnes and Noble
In October 2020, Barnes and Noble, the world’s largest bookstore chain, became one of Egregor’s first high-profile victims. A cyber attack resulted in illegal and unlawful access to some Barnes & Noble business networks, according to a public statement released by the company.
Barnes and Noble warned that certain customers’ data may have been compromised because of an abundance of caution. Email addresses, shipping addresses, and phone numbers could all have been hacked. Shortly later, a message surfaced on Egregor’s dark web leak site, claiming to have proof of stolen data.
Crytek and Ubisoft
Video game developers Crytek and Ubisoft were two of Egregor’s first victims. Two posts containing supposed files and data exfiltrated from both firms’ IT systems emerged on Egregor’s dark web leak site at the same time.
The Ubisoft breach included source code for one of the company’s video games, while the Crytek leak included development materials for prospective projects. Egregor confirmed they had only stolen data from Ubisoft and that the ransomware had left the systems undisturbed and unencrypted. On the other hand, several of Crytek’s systems were entirely encrypted by the threat actors.
November 2020
Cencosud
Cencosud, a Chilean-based multinational retail company, was hit by Egregor Ransomware in November 2020. The attack impacted the services in their stores. With over 140,000 workers and $15 billion in sales for 2019 and stores like Easy home goods, Jumbo supermarkets, and Paris department stores, Cencosud is one of the biggest retail businesses in Latin America.
A good example of how Egregor ransomware affected Cencosud is what happened at an Easy store in Buenos Aires, where there was displayed a sign warning customers that because of technical issues, they do not accept the ‘Cencosud Card’ credit card, accept returns, or allow the pickup of web purchases.
December 2020
Kmart
A ransomware attack hit American department store chain Kmart’s back-end IT systems in early December 2020. Following the hack, the parent business Transformco’s human resources website went down.
For retailers, the holiday season is a very significant time of year. Successful attacks on shops’ IT systems done at the busiest period of the year have a higher possibility of resulting in rewards, according to threat actors. The Egregor organization was behind the attack, according to security researchers who saw the ransom note from the incident. The ransomware attack was never publicly acknowledged by Kmart, and the damage appears to have been limited to encrypted back-end systems and workstations.
In 2019, the company was bought by Transformco, which was also apparently affected. The internally used 88sears.com website was offline – workers confirmed that this happened due to the ransomware attack.
Translink
The Translink attack, which also occurred in early December 2020, impacted phone lines, web services, and payment systems. Customers were briefly unable to use credit or debit cards to pay for transportation services.
If Translink wished to avoid its data being released online, the ransom message demanded payment within three days. Egregor used an unusual technique of delivering the ransom note to Translink: the threat actors hijacked printers and printed the note repeatedly. This strategy was similar to Egregor’s attack on Cencosud, one month prior.
Randstad HR Firm
The Amsterdam-based company announced at the beginning of December 2020 that they were targeted by Egregor ransomware. As BleepingComputer noted, “Randstad is the world’s largest staffing agency with offices in 38 markets and the owner of the well-known employment website Monster.com. Randstad employs over 38,000 people and generated €23.7 billion in revenue for 2019.”
A 32.7MB archive with 184 files which included “accounting spreadsheets, financial reports, legal documents, and other miscellaneous business documents” got published by Egregor – they claimed that this represented only 1% of the exfiltrated data.
How to Stay Safe from Egregor Ransomware
The activities of the attackers behind Egregor ransomware have gotten the attention of the FBI: “All private sector organizations are being urged to be on the alert for potential malicious activities from the threat actors behind Egregor ransomware. The FBI alert warns the hacking group is actively targeting and exploiting a range of global businesses. […] The new FBI alert warns that Egregor has already claimed 150 victims worldwide since the group emerged in September.”
They have also stated again that “paying the ransom is not ideal or recommended as it further emboldens hackers to continue these targeted efforts. Victims should instead contact the FBI, which can assist in the prevention of further attacks.”
There were no decryption tools for Egregor ransomware strains available, therefore, only the threat actors responsible for the attacks have decryption software and keys to decrypt files that have been encrypted. Regardless, do not put your trust in cybercriminals or pay any ransoms.
Remember there are always a few aspects you can pay attention to if your goal is avoiding becoming a victim of ransomware attacks in the first place.
Educate your employees
All your employees should know about the dangers of phishing, which are a common vector for injecting ransomware. By definition, phishing is “a malicious technique used by cybercriminals to gather sensitive information (credit card data, usernames, and passwords, etc.) from users. The attackers pretend to be a trustworthy entity to bait the victims into trusting them and revealing their confidential data. The data gathered through phishing can be used for financial theft, identity theft, to gain unauthorized access to the victim’s accounts or to accounts they have access to, to blackmail the victim, and more.”
Employ Email Security solutions
Speaking of phishing, email security is one way of avoiding it. Our Heimdal™ Email Security solution is a revolutionary spam filter and malware protection system which packs more email security vectors than any other solution you can find. Heimdal™ Email Security will help you detect malware, stop spam, malicious URLs, and phishing with simple integration and highly customizable control.
Heimdal® Email Security
Make sure you have backups
Having backups (and even backups to backups, if possible) of your data is crucial for any company – and for every person. Anything can happen to anyone at any time, literally. As Health IT Security writes, “Backups should be secured, and administrators should ensure data is not accessible for modification or deletion from the system where the data resides.” The availability of backup files is a key factor for businesses looking to recover from a ransomware attack.
Install and update antimalware and antivirus software
A good antivirus solution can save you from many problems. Our Enterprise Endpoint Security is a multi-layered security suite that brings together threat hunting, prevention, and mitigation in one package, for the best endpoint protection. It combines the power of Heimdal™ Threat Prevention and Heimdal™ Next-Gen Antivirus & MDM, so you will enjoy both revolutionary technologies like Heimdal™ Patch & Asset Management, plus a powerful firewall and process behavior-based scanning. What’s more, solutions such as Heimdal™ Ransomware Encryption Protection can actively disrupt malicious encryption attempts.
Secure your endpoints with multifactor authentication
Multifactor authentication should be implemented on all remote access points in an enterprise network, with special attention paid to securing or disabling remote desktop protocol (RDP) access. Multiple ransomware attacks have been reported to take advantage of unsecured RDP connections to obtain initial access to a target network.
Multifactor authentication
To identify possible security incidents, employ user and entity behavior analytics
Assume a breach has occurred when the alert is triggered. Audit, monitor, and respond promptly to suspected privileged accounts and group abuse.
Prevent unauthorized data theft
Particularly when it comes to uploading huge amounts of data to lawful cloud storage systems that might be abused by threat actors. Consider limiting outbound traffic to cloud hosting services that aren’t approved.
The End of Egregor?
In what has been a busy year for Ukrainian law enforcement in breaking ransomware gangs, a joint operation with French police resulted in the arrest of many people linked to the Egregor ransomware gang. Egregor affiliates were detained in the February 2021 raid, carrying out hacks with the gang’s ransomware strain.
The dark web leak site run by Egregor had gone offline at the time of the arrests. It’s unclear whether the operation’s executives became alarmed, or whether the Ukrainian law enforcement sting was more extensive than initially disclosed. According to CSO, Egregor’s leader may have been apprehended as officials closed in.
On February 9, a joint operation by US, Ukrainian, and French authorities resulted in the arrest of gang members behind Egregor as well as associates who were part of their affiliate program. The leader of the Egregor group was reportedly among those arrested. The group’s website was also taken offline. It is too early to know whether this action has taken Egregor down permanently.
Source: CSO
Like in the cases of other ransomware families, there’s a chance Egregor will reappear under a different moniker, and that its current absence is just a pause. The alternative is that Egregor has been permanently disabled. Only time will tell if Egregor has a future or has been relegated to the past. Whatever the case, organizations must continue to be vigilant when it comes to combating ransomware attacks as new threat actors are continuously vying for a piece of what is a very huge pie.
Wrapping Up
Keep in mind that, if you ever become a ransomware attack victim, paying the ransom will only encourage cybercriminals, it will not help you. The best thing you can do for your company is to use prevention as a weapon.
Please remember that Heimdal™ Security always has your back and that our team is here to help you protect your home and your company and to create a cybersecurity culture to the benefit of anyone who wants to learn more about it.
If you enjoyed this article and want to keep up to date with everything cybersecurity, make sure you follow us on LinkedIn, Twitter, YouTube, Facebook, and Instagram.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











