Contents:
Coming back to your laptop only to find all your data encrypted and a defiant message on your screen asking you for money in return might probably be one of the scariest scenarios related to cyber-attacks. If you’re “lucky” enough to get targeted by cybercriminals, you might find out that Maze ransomware is even more frightening.
What Is Maze Ransomware?
If ransomware refers to a type of malware (malicious software) that encrypts all the data on a PC or mobile device, blocking the data owner’s access to it, as we explain in our Cybersecurity Glossary, Maze ransomware is an even more dangerous attack, as the criminals behind MAZE also have a public website where they post the stolen data of the victims who refuse to pay the extortion fee.
The particular Maze ransomware is nowadays so alarming because, even if you do manage to get access to your essential information through backups, the criminals would still have a copy, which could degenerate into a massive GDPR issue. You might be facing a combination of a ransomware attack and a data breach. As the criminals mention on their website, if the ransom is not paid, they will:
- inform the media and offer details about your security breach;
- sell the valuable stolen information on the dark market;
- inform the stock exchanges on which your company might be listed about the attack and the loss of sensitive information;
- inform your clients and partners that your company was attacked and use the stolen information to attack them as well.
After becoming one of the most dangerous types of ransomware and being taken as an example by other ransomware operators, Maze ransomware shut down in September 2020. The closing operation has been confirmed when a threat actor involved in the recent Barnes and Noble ransomware attack contacted a BleepingComputer journalist.
Apparently, Maze “had stopped encrypting new victims in September 2020, and are trying to squeeze the last ransom payments from victims. […] Maze has started to remove victims that they had listed on their data leak site. All that is left on the site are two victims and those who previously and had all of their data published. The cleaning up of the data leak site indicates that the ransomware operation’s shutdown is imminent.”
Maze Ransomware Operating Mode
The first known attacks of Maze ransomware took place in May 2019. The criminals initially distributed the ransomware via spam e-mail and exploit kits, but now they use a variety of tactics, techniques, and procedures. They might even hire actors to analyze their next victim’s organization and determine its annual revenue. The e-mails they were sending had “Missed package delivery” and “Your AT&T wireless bill is ready to view” at the subject line and were sent using several malicious domains with the registrant address abusereceive@hitler.rocks.
Once the Maze operators find a gap in a network, their next step is to obtain elevated privileges, conduct lateral movement and then begin to deploy file encryption across all drives, not before exfiltrating the data they discover. The data is encrypted using the ChaCha20 and RSA algorithms. After all the targeted files are encrypted, the malware will change the desktop image to something like:
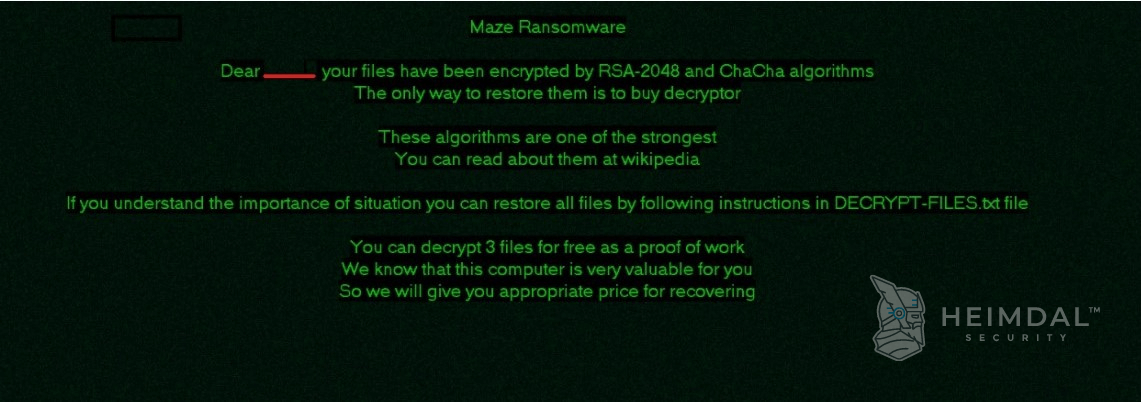
PCrisk explains:
Exploit kits are tools used to initiate ‘exploits’ against vulnerable (usually outdated) software or to inject malicious code into vulnerable websites. Other ways to proliferate ransomware-type programs (and other malware) are via emails, Trojans, untrustworthy software download channels, software ‘cracking’ tools, and fake updaters. Emails/spam campaigns can be used to infect computers through files that are attached to email messages. Typically, cybercriminals attach Microsoft Office documents, archive files (ZIP, RAR), executable files (.exe and other files of this kind), PDF documents, JavaScript files, etc. Their main goal is to trick recipients into opening the attachments. If opened, they infect systems with malware. Another way to proliferate infections is via Trojans, which are malicious programs. If already installed, they open backdoors for other malware. In this way, they cause chain infections. Examples of untrustworthy download sources are file hosting, freeware download websites, Peer-to-Peer (P2P) networks such as torrent clients, eMule, and other similar channels/tools. Cybercriminals use them to upload malicious files that are disguised as legitimate or harmless. By downloading and opening/installing them, many people install malicious programs inadvertently. Software ‘cracking’ tools are used by people (illegally) to avoid having to pay for activation of licensed software. In fact, these tools often install malware rather than activating any installed software free of charge. Fake (unofficial) software updating tools cause damage by exploiting bugs/flaws of outdated software that is already installed on the system, or simply by installing malicious programs rather than updates.
Following the notice informing you that your data have been hacked, you will be instructed to pay the ransom via a website URL that may be accessed via the Tor browser. Another option is to pay using a third-party website (the link is also included in the ransom note), which may be accessed through any browser. In any case, it is made plain that without the necessary tool/key, victims will be unable to decrypt their files. According to the Tor website, victims must pay $500 in Bitcoins using the specified BTC wallet address. The size of the ransom gets doubled unless victims pay the ransom within a certain time frame (a countdown timer is displayed at the top of the Tor web page). Three encrypted files can be decrypted for free using the same website. In general, cybercriminals provide free decryption to ‘show’ that they have decryption tools/keys.
Maze Ransomware Attack Examples
1. The Allied Universal Attack
No company is safe as long as the Maze group is out there. Allied Universal, a security staffing firm, learned this in November 2019. The Maze ransomware group published about 700 MB of stolen data after the ransom deadline they offered was surpassed. They said this only represented 10% of what they have stolen.
2. The Hammersmith Medicines Research Attack
On the 14th of March 2020, the IT staff of Hammersmith Medicines Research discovered a severe attack. The company, which at that time was on standby to carry out trials of a possible future vaccine for the Covid-19 coronavirus and have previously carried out tests to develop the Ebola vaccine and drugs to treat Alzheimer’s disease, was one of the many victims of the Maze cybercriminals. The medical company refused to pay the ransom, and personal details of former patients were published, although the Maze group had made a public promise not to attack medical research organizations during the coronavirus pandemic only a few days before.
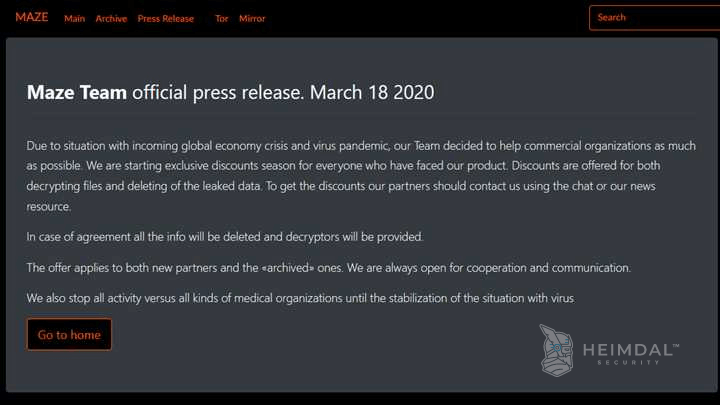
In regards to how the Maze group got into HMR, it would appear that the company used a Fortinet VPN Server that may have had a vulnerability.
3. The Xerox Attack
At the beginning of this year’s July, the Maze ransomware group claimed to have stolen more than 100 GB from Xerox, the giant printing company. As crn.com says, “the hackers appear to have stolen financial documents and databases possibly storing user information, according to SecurityWeek. The dates shown in the screenshots suggest that the ransomware started encrypting files on Xerox computers on June 24 […]”. As Microsoft says,
So far the attacks have affected aid organisations, medical billing companies, manufacturing, transport, government institutions, and educational software providers, showing that these ransomware groups give little regard to the critical services they impact, global crisis notwithstanding. These attacks, however, are not limited to critical services, so organisations should be vigilant for signs of compromise.
4. The Cognizant Attack
Cognizant, a Fortune 500 firm and one of the largest global providers of IT services, was hit by the Maze group in April 2020, resulting in widespread service outages.
Several Cognizant employees experienced communication difficulties as a result of the attack’s destruction of internal directories, and the sales staff was left with no method to interact with clients or vice versa. The corporation suffered significant financial losses as a result of the attack, with estimates ranging from $50 to $70 million in lost revenue.
5. The LG Electronics Attack
Maze did not use LG’s network to execute their ransomware; instead, they took the company’s sensitive data and chose to forgo the second phase of their extortion operations.
On the Maze ransomware leak site at the time, the operators only posted three screenshots as proof of the data breaches:
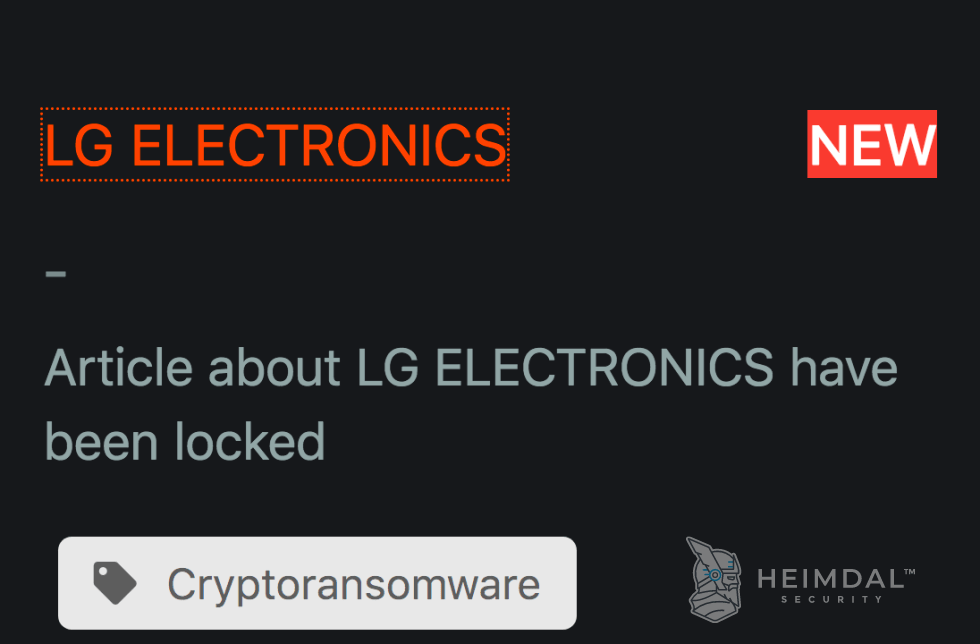
“We decided not to execute [the] Maze [ransomware] because their clients are socially significant and we do not want to create disruption for their operations, so we only have exfiltrated the data,” the Maze gang told ZDNet reporters via a contact form on their leak site.
Later, the hackers claimed to have stolen 50.2 GB from LG’s internal network and leaked it online.
How to Stay Safe from Maze Ransomware
There were no decryption tools for Maze ransomware strains available, therefore, in this case, prevention beats the cure. For online safety, we recommend you follow these anti-ransomware security measures that can significantly reduce the likelihood of a Maze ransomware attack:
1. Patch the OS and the software you use
The OS, security software (antivirus, firewall), and any other software (including Internet browsers) your company uses should always be updated and patched since cybercriminals can’t wait to find software vulnerabilities to use to their advantage. Our Heimdal™ Patch & Asset Management technology can help you achieve compliance, mitigate exploits, close vulnerabilities, deploy updates, and install software anywhere in the world, according to any schedule. Our tool covers both Windows and 3rd party application management and includes customizable set-and-forget settings for automatic deployment of software and updates. To better understand the concept, you can read more on patch management here.
2. Manage users and their privileges
The potential impact of a successful ransomware attack against your company can be minimized by good account management, based on the principle of least privileges and the zero trust model. If you want to automate the process, you can try our Privileged Access Management tool. Heimdal™ Privileged Access Management will help your system admins to approve or deny user requests from anywhere or set up an automated flow from the centralized dashboard, and all the activity will be logged for a full audit trail, so it will be crystal clear who did what and when.
When it comes to password management, you should set complex ones and change them frequently, enable multi-factor authentication and generally avoid browsing or opening documents if you are logged in as an administrator.
3. Disable Microsoft Office macros
Macros are small programs that perform particular tasks, and that can start when opening a Word or Excel document. Macros and the editing mode should not be enabled by default upon execution of a document, especially in the case of the ones received via e-mail. As we have mentioned before, the modus operandi of the Maze group heavily relied on e-mail compromise, so it’s a must to be extra careful.
4. Keep your antivirus updated
It goes without saying that your company’s cybersecurity is not complete without an antivirus solution which, obviously, must always be up to date if you want to be protected. Our Enterprise Endpoint Security is a multi-layered security suite that brings together threat hunting, prevention, and mitigation in one package, for the best endpoint protection. It combines the power of Heimdal™ Threat Prevention and Heimdal™ Next-Gen Antivirus & MDM, so you will enjoy both revolutionary technologies like Heimdal™ Patch & Asset Management, plus a powerful firewall and process behavior-based scanning. Additionally, solutions such as Heimdal™ Ransomware Encryption Protection can actively disrupt malicious encryption attempts.
5. Browse securely
To avoid becoming the next victim of Maze ransomware, always be careful when browsing. You should always update your browser, block ad pop-ups, avoid installing extensions you do not know much about, and don’t forget to verify if you’re visiting legitimate websites by checking the address bar (HTTPS is secure, HTTP not so much). Also, if you or your employees are keen on using web applications, don’t forget to learn more about what this means in terms of cybersecurity.
6. Backup your files
Backups are crucial if you want to be able to use your data in case of a Maze ransomware attack. You should enable automatic backups for your employees and protect them with unique complex passwords. It’s essential to use a combination of online and offline backups.
7. Use Email Security
Since Maze ransomware was first distributed via spam e-mails, it’s obvious why you must be extra careful with all the messages you receive. Firstly, you should enable multi-factor authentication to make sure that all logins are legitimate and set password expiration dates. Secondly, you should never open attachments or access links received from unknown, unexpected, or unwanted sources. You should also think about an e-mail protection solution, like our Heimdal™ Email Security.
8. Train your employees
Technology can help, but people are the ones who use it, for good or for bad – that’s why it’s so important that your employees know what’s safe and what’s not in terms of cybersecurity. User awareness is one of the most reliable methods to prevent an attack, so make sure you take the time to educate your employees and advise them to report to the security teams as soon as they notice something unusual.
9. Check for unusual behaviors
Checking for unusual behaviors and alerts should become a priority for any company. Microsoft advises paying attention to:
– Malicious PowerShell, Cobalt Strike, and other penetration-testing tools that can allow attacks to blend in as benign red team activities. – Credential theft activities, such as suspicious access to Local Security Authority Subsystem Service (LSASS) or suspicious registry modifications, which can indicate new attacker payloads and tools for stealing credentials. – Any tampering with a security event log, forensic artifact such as the USNJournal, or a security agent, which attackers do to evade detections and to erase chances of recovering data.
10. Investigate affected endpoints and credentials
If any of your endpoints got affected, identify all the credentials used on them and assume that all of them were available to and compromised by the attackers. You should check the Windows Event Log for post-compromise logons.
Heimdal™ Ransomware Encryption Protection
Should you consider paying the ransom if all these precautions ever fail?
Although this decision is entirely up to you, we would not recommend it. As the FBI says,
In some cases, victims who paid a ransom were never provided with decryption keys. In addition, due to flaws in the encryption algorithms of certain malware variants, victims may not be able to recover some or all of their data even with a valid decryption key. Paying ransoms emboldens criminals to target other organizations and provides an alluring and lucrative enterprise to other criminals. However, the FBI understands that when businesses are faced with an inability to function, executives will evaluate all options to protect their shareholders, employees, and customers. Regardless of whether you or your organisation have decided to pay the ransom, the FBI urges you to report ransomware incidents to law enforcement. Doing so provides investigators with the critical information they need to track ransomware attackers, hold them accountable […], and prevent future attacks.
Moreover, bear in mind that, even if you do pay the ransom, the security issues that allowed cybercriminals access to your company are still there and you still have to fix them. It’s better to adopt a prevention attitude from the start.
Conclusions
While waiting to see whether the Maze ransomware operators will release the master decryption keys, Maze affiliates switched to Egregor, a new ransomware that became very active in the same month Maze started shutting down.
As the Federal Bureau of Investigation mentions, “ransomware attacks are becoming more targeted, sophisticated, and costly […]”. Moreover, they represent a menace for a long time, since ransomware first appeared in 1989, when it was introduced into systems via floppy disks. You can find more information about this type of attack here, and, if you’re curious, details about the ransomware payouts from last year here.
If you enjoyed this article, make sure you follow us on LinkedIn, Twitter, YouTube, Facebook, and Instagram to keep up to date with everything cybersecurity.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











