Contents:
At the very least, the Pysa ransomware was first deployed in October 2018. The initial versions of the ransomware created encrypted files with the “.locked” extension, which is common among ransomware. A new version of Pysa has been detailed in open sources since December 2019. Pysa is the name given to this version since it creates encrypted files with the “.pysa” extension.
What is Pysa Ransomware?
PYSA is a form of ransomware that is increasingly being employed in “big game” assaults, in which attackers select their targets based on their projected ability to pay. PYSA is an acronym for “Protect Your System Amigo,” which is included in the ransom note left for the victim. According to cybersecurity analysts, Pysa is a variant of the Mespinoza ransomware family and has been active since at least October 2019.
The malicious software exfiltrates sensitive information before encryption and uses the stolen data to force the victim to pay a ransom in exchange for the files.
Pysa Ransomware Operation Mode
Pysa ransomware encrypts files and then leaves a Readme.README file on the user’s desktop and in numerous other Windows places. The attackers explain what happened to the victims’ PCs in the brief note, and that they must contact them by sending an email to certain email addresses.
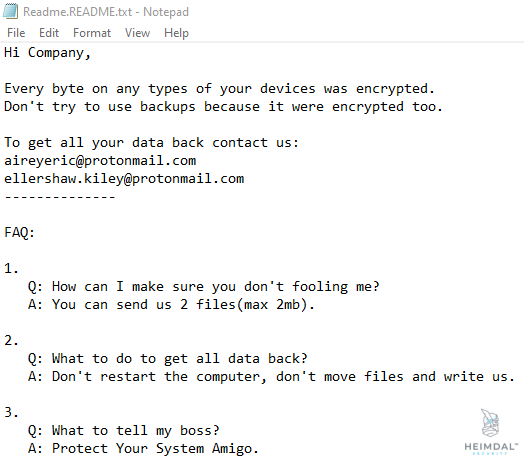
Pysa Ransomware Ransom Note
Once it’s delivered, the ransomware will try to exfiltrate sensitive information (usernames, passwords, databases, internal business files) before proceeding to encrypt all accessible non-system files via AES implementations. The Pysa ransomware will ensure a large variety of popular file types (.mp3, .mp4. .png, .jpg, .docx, .pptx, .xlsx, .rar) are encrypted.
The stolen data will eventually be used to extort affected parties into meeting the attackers’ ransom demands. Thus, victims cannot regain access to their files unless they decrypt them with a specific decryption tool or key. Organizations or individuals who do not give in to the hackers’ demands will have their information leaked on a website controlled by Pysa operators.
Sample #Mespinoza #Ransomware extension .pysa
Ransom note;Readme.README.txt
Sample https://t.co/Qe5jy87xe8https://t.co/SgR3bw4HnF pic.twitter.com/9CEZG12VPa— GrujaRS (@GrujaRS) January 5, 2021
Initially, this version was being used to target large organizations in an attempt to maximize the attackers’ skills, but alerts issued by the FBI, NHS, and CERTFR, warn that, similar to Ryuk and Maze, Pysa ransomware is targeting local government agencies, educational institutions, private companies, and the healthcare sector.
In a twofold extortion attempt, PYSA ransomware threat actors are now utilizing a RAT known as “ChaChi” to target educational institutions. While RATs are commonly used in ransomware operations, the combination of PYSA and ChaChi is concerning.
Created in 2019, the ChaChi RAT has since been enhanced to incorporate features such as port forwarding, DNS tunneling, and obfuscation. Using DNS and HTTP protocols, ChaChi delivers command-and-control (C2) capabilities to PYSA threat actors.
When PYSA acquires access to a victim’s network, it uses tools like Advanced Port Scanner and Advanced IP Scanner to do reconnaissance. Once the targeted network is compromised, attackers attempt to exfiltrate its accounts and passwords database. Operators also employed versions of PowerShell Empire, Koadic, and Mimikatz testing tools, to stop antivirus products. Before encrypting all Windows and Linux devices, the attackers utilize these tools to move laterally around the system, escalate privileges, and exfiltrate sensitive data.
Pysa Ransomware Distribution
Pysa has a strategy known as “big game hunting,” in which the ransomware gang focuses on high-value assets in companies that are most vulnerable to data loss or system failure. The theory is that victims, such as healthcare providers, government agencies, and MSPs, will be more likely to pay the ransom fast, regardless of the cost.
As opposed to more automated threats like WannaCry or Petya, Pysa is a human-operated ransomware. It’s usually spread through brute-force attacks on servers that have RDP or AD open to the Internet, but it’s also delivered in spam or through phishing email campaigns. The credentials database of the organization is then stolen by the threat actors. Antivirus solutions are attempted to be stopped — or even uninstalled — using PowerShell and Batch scripts. The Pysa ransomware has been documented to target 46 organizations, with victims in France, Australia, and the United States.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
How to Stay Safe from Pysa Ransomware
If a device on your network becomes infected with Pysa ransomware it will begin encrypting files, which may also include remote files on network locations. The latest Pysa ransomware strains do not have decryption tools available; therefore, in this case, prevention beats the cure. For online safety, I strongly advise you to follow the anti-ransomware security measures listed below.
#1. Provide proper training to all employees
It’s important to raise awareness and help your staff detect a phishing email, strengthening they should not open any attachments or web links within an alleged phishing email. In general, these emails are sent from unknown, suspicious addresses. Hackers usually mark their emails as “important” or “official” leading the victim into a false sense of security.
#2. Keep your software up to date
You should always use the functions and tools provided by official software developers, like automatic updates. Any software or files should only be downloaded from official and trustworthy sources, and through direct links. Never download updates using unofficial activation methods/tools as they can infect the systems in the activation process.
#3. Scan your operating system regularly
Your OS is the most important part of the software as its vulnerabilities affect the entire machine. Therefore, scanning and updating your OS is essential. You should do so by using a trustworthy antivirus or anti-spyware suite remembering to it up to date as well. What’s more, an operating system is a very complex program and due to this, it often has flaws that can turn into security threats. Updating your OS can help block these threats easily.
Additionally, for extra protection, you can:
- Make sure secure configurations are applied to all devices.
- Enable tamper protection settings in security products.
- Use multi-factor authentication (MFA) and lockout policies, especially for administrative accounts.
- Use administrative accounts only for necessary purposes.
- Use remote administration services with strongly encrypted protocols that only accept connections from authorized users or locations.
- Constantly monitor your systems for suspicious activity, so that a compromise of the network can be detected as early as possible.
Unfortunately, Pysa hasn’t got any security flaws in the implementation of the encryption algorithms so far. Pysa ransomware victims have been advised to report these incidents to their local FBI field office or the FBI’s Internet Crime Complaint Center (IC3).
How Can Heimdal™ Help
To keep track of your privileged accounts and easily manage admin rights requests, I recommend you use a Privileged Access Management tool. Heimdal™’s PAM solution not only lets you efficiently manage user rights but also allows users to safely install software themselves while providing logs and audit trails for data protection and compliance. What’s more, it is the only tool on the market that de-escalates users’ rights upon threat discovery (when used in tandem with our Threat Prevention or Endpoint Antivirus modules).
Staying secure from ransomware is easier with the correct knowledge and habits, as well as a trustworthy portfolio of solutions. As always, Heimdal Security is available to assist you with the latter. You can always contact us at sales.inquiries@heimdalsecurity.com or book a demo if you have any questions regarding which of our company’s products are most suited for your needs.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










