Contents:
OCD or just very fond of structure, I must confess that I like pretty much everything around me to be in (a specific) order. Due to this habit, I got used to working mostly with web applications, since I don’t like to have many windows opened on my taskbar and I prefer moving swiftly between my browser’s tabs. Recently, though, I’ve started to wonder: what does this mean in terms of web application security? To answer that question, let us start from the beginning and clarify what is a web application in the first place. According to SearchSoftwareQuality,
A Web application (Web app) is an application program that is stored on a remote server and delivered over the Internet through a browser interface. […] Web applications do not need to be downloaded since they are accessed through a network. Users can access a Web application through a web browser such as Google Chrome, Mozilla Firefox or Safari. For a web app to operate, it needs a Web server, application server, and a database. Web servers manage the requests that come from a client, while the application server completes the requested task. A database can be used to store any needed information.
 Among the benefits of web applications we list:
Among the benefits of web applications we list:
a. Easier installation and maintenance
It’s much easier to install, upgrade or maintain a web-based application than a standalone desktop application. Web applications are upgraded in the host servers, and every user can access the updated version as soon as the deployment had finished, without needing to update the application on their PCs.
b. No download hassles
From an end-user perspective, this is probably the greatest advantage – with web applications, you don’t have to download anything in order to use the service. A compatible browser with Internet access is usually all you need.
c. Use of less storage space
When using a web application, you don’t have to worry about how much space and memory it needs on your device. Moreover, they can be accessed from any place in the world where there is an active Internet connection.
d. Accessible on various platforms
It’s safe to say that nowadays mobility is a great asset and it sure helps a lot not to depend on a certain device in order to complete your tasks. Web applications can be used on any platform (desktop, laptop, phone, tablet), wherever you are.
Web applications may be:
a. Static web applications
These are the most basic type of web application, created using HTML and CSS. If you need to make any serious changes to it, it’s highly certain that you need to contact the ones who planned and designed it.
b. Dynamic web applications
Dynamic web applications can include databases or forums and have the constant ability to update or change the available information.
c. E-commerce applications
E-commerce apps are more complex than the other two mentioned before, since they need a way to collect electronic payment.
d. Portal web applications
Portal web applications include forums, chats, emails etc. and are characterized by many different sections or categories which are accessible by way of a home page.
e. Animated web applications
It’s mandatory for this kind of applications to use FLASH technology. Animated web applications do not work with SEO optimization or positioning, because search engines cannot read their information properly.
f. Content management systems
Content management systems offer interfaces that can be accessed and updated and are used for personal or corporate blogs, media sites and so on. If we want to talk about web application security, though, we must first specify that web applications are related to the supply chain topic, which we covered here. Unfortunately but not surprisingly, as third-parties in your business workflow, web applications can be attacked in various ways, from database manipulation to large-scale network disruption. According to DARKReading,
Positive Technologies’ analysis unearthed some 70 different types of vulnerabilities in total in Web apps. Security configuration errors—such as default settings, common passwords, full path disclosure, and other information-leak errors—were present in four out of five apps, making this class of vulnerability the most common. Cross-site scripting errors were present in 77% of applications; 74% had authentication-related issues, and more than half (53%) had access control flaws.
Here are the main web application security threats that you need to be aware of:
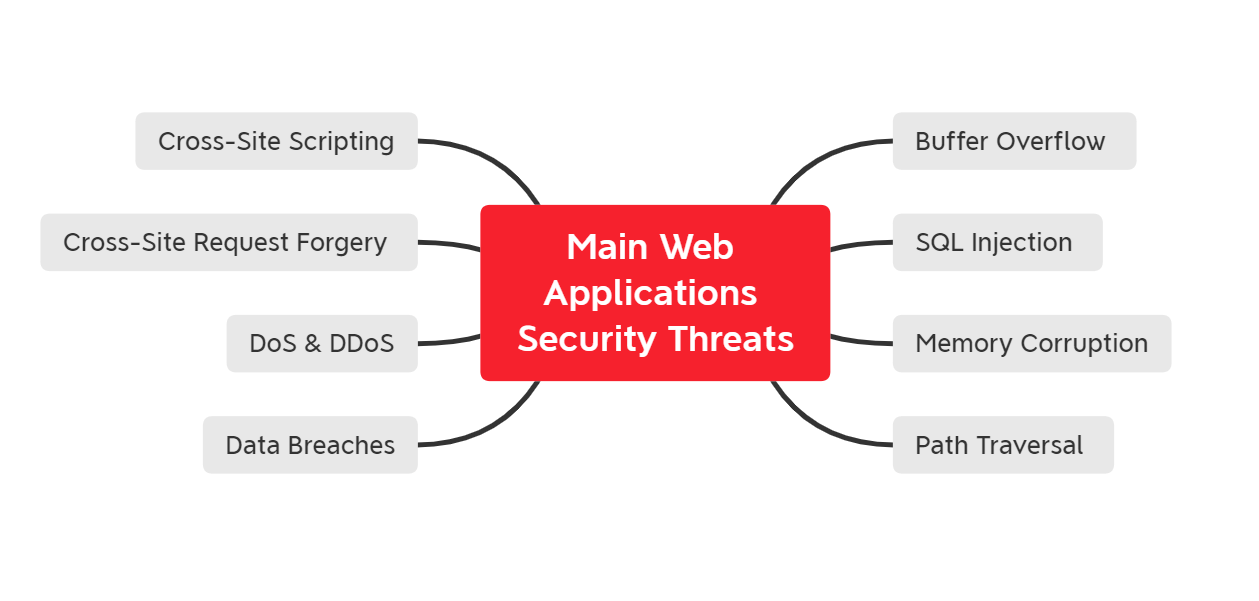
1. Cross-Site Scripting ( XSS)
In a cross-site scripting attack, hackers inject client-side scripts into webpages to get direct access to important information, to impersonate the user or to trick the user into disclosing sensitive data. If a visitor loads the compromised page, his/her browser may execute the malicious code. This kind of attack is not really the most sophisticated, but it is the most common.
2. Cross-site request forgery
This type of attack is a serious web application security vulnerability, involving tricking a user into making a request utilizing their authentication or authorization. By leveraging account privileges, attackers are able to send false requests. The common targets for cross-site request forgeries are the highly privileged accounts, like administrator or executive, which results in the exfiltration, destruction or modification of important information.
3. Denial-of-Service (DoS) & Distributed denial-of-service (DDoS) attacks
During a DoS or DDoS attack, hackers try to overload a targeted server or its surrounding infrastructure. When the server is no longer able to effectively process incoming requests, it will start to behave in an irregular manner, denying service to incoming requests from legitimate users.
4. Data breaches
Data breaches may occur through malicious actions or by mistake, but the consequence is the same: sensitive or confidential information gets leaked. Depending on the company who is unfortunate enough to experience a data breach, millions of user accounts can get exposed.
5. Buffer overflow
The term buffer refers to memory storage regions that temporarily hold data during its transfer from one location to another. A buffer overflow/overrun happens when the data volume is bigger than the storage capacity of the memory buffer, which results in adjacent memory locations being overwritten with data. By overwriting the memory of an application, the execution path of the program is changed, which triggers a response that compromises files or exposes sensitive information. Moreover, extra codes that send new instructions to the application may be introduced to get access to the IT systems.
6. SQL Injection (SQi)
Structured Query Language (SQL) represents a programming language typically used in relational databases or data stream management systems, being very effective in querying, manipulating, aggregating data and performing an impressive number of other functions. In a SQL Injection attack, the malicious players exploit vulnerabilities in the way a database executes search queries.
7. Memory corruption
Memory corruptions refer to that process in which a location in memory is unintentionally modified, possibly leading into unexpected behaviour. Hackers will try to exploit this by attempting code injections or buffer overflow attacks.
8. Path traversal
Path traversal attacks refer to the injection of “../” patterns in order to move up in the server directory hierarchy, for the purpose of accessing unauthorized files or directories outside the webroot folder. Successful path traversal attack might allow hackers access to user credentials, configuration files or even databases. All these sound pretty alarming, but, fortunately, there are many options you can choose when it comes to web application security and protecting your company by detecting, preventing and responding to attacks.
Here’s how you can enhance your company’s web application security:
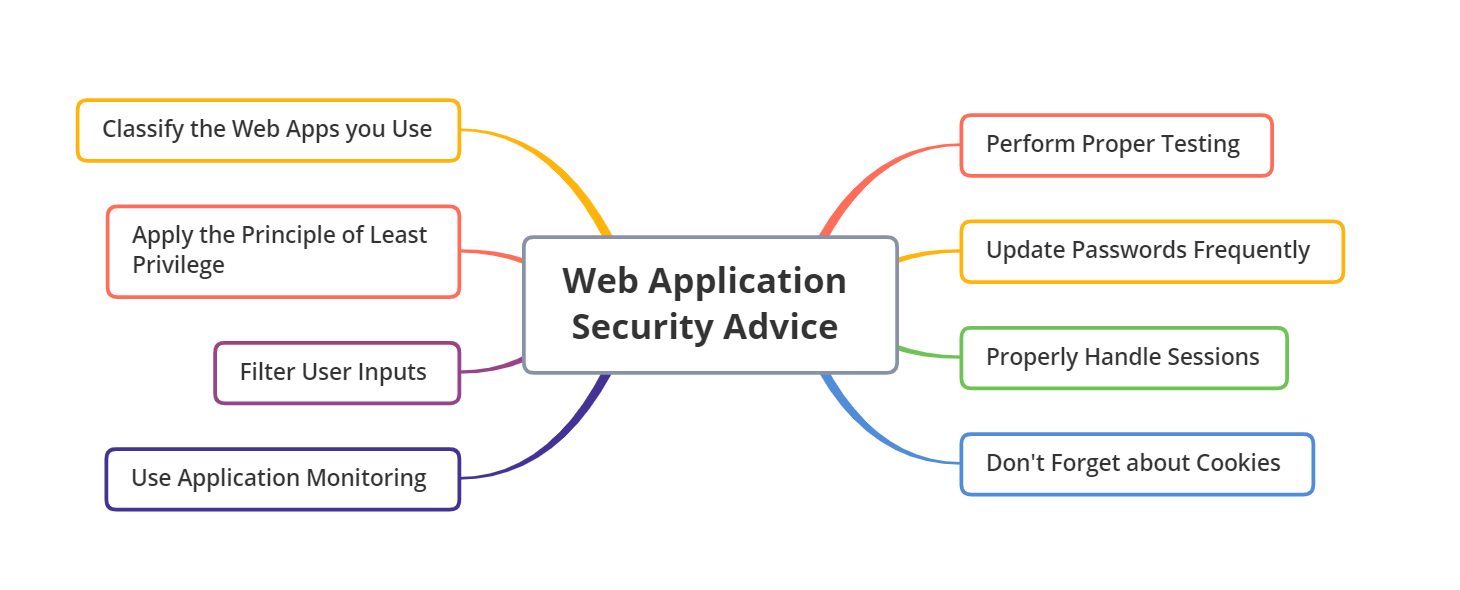
1. Classify Web Applications
The first thing to do if you want to avoid paying the fiddler is a matter of common sense – you must know the number of web applications your company uses and how are they being used. You cannot build a security system if you don’t know exactly what you need to protect. First step? Make a web applications inventory and try classifying them: very critical, critical, serious, normal.
2. Apply the Principle of Least Privilege
Access management can make or break web application security. Not all users will need the same set of rights and privileges, so make sure that you confine the higher privileges to only a few. Automated solutions can be of great help here. Our Heimdal™ Privileged Access Management, will make your life a lot easier if you decide to proactively manage, monitor, and control privileged account access. Heimdal® Privileged Access
Management
3. Filter User Inputs
Input fields can be found in almost every web application. These sections, where users introduce data (text, images, file attachments), are often attacked in the attempt to corrupt or take over the web application, so make sure that your company uses filters.
4. Use Application Monitoring
By monitoring applications with the help of a web application firewall, you will be able to get some insights regarding what type of traffic flows in, what vulnerabilities are being blocked, what kind of inputs and responses the application is receiving etc. Both of our Heimdal Next-Gen Antivirus & MDM and Endpoint Security Software include the firewall feature and can become your ally in your quest of implementing web application security.
5. Perform Proper Testing
Testing is a crucial aspect in cybersecurity. When it comes to the web applications your company uses, make sure your security experts perform penetration testing, in order to make sure that there are no logical flaws in the web applications you need to use.
6. Update the Passwords Frequently
This is another simple safety measure that every web application user can adopt. In order to stay safe is mandatory to use strong passwords that include special characters, numbers and letters. We wrote more about this topic here and here. In addition to strong passwords, a two-factor authentication method will make your accounts even more secure and will drastically reduce the cybercriminals’ chances to successfully attack your company.
7. Properly Handle Sessions
Web sessions consist of a series of HTTP requests and the responses of a user, in a certain period of time. Web application sessions are user-initiated and last till the end of the communication between two systems over a network. It’s important to properly handle these sessions if you want to avoid session hijackings, session sniffing, and cross-site scripting attacks.
8. Don’t Forget about Cookies
Cookies are crucial for web application security, and yet they are often overlooked. They provide excellent cyber attacks targets since they contain valuable information which helps users to be remembered by the sites they visit. To avoid any nuisances, try not to use cookies to store sensitive information or consider encrypting it and don’t forget to always monitor and control the cookies’ expiry dates.
Conclusion
As Dafydd Stuttard and Marcus Pinto say in their book, The Web Application Hacker’s Handbook,
There is no doubt that web application security is a current and very newsworthy subject. For all concerned, the stakes are high: for businesses that derive increasing revenue from Internet commerce, for users who trust web applications with sensitive information, and for criminals who can make big money by stealing payment details or compromising bank accounts.
Please remember that Heimdal™ Security always has your back and that our team is here to help you protect your home and your company and to create a cybersecurity culture to the benefit of anyone who wants to learn more about it. Drop a line below if you have any comments, questions or suggestions – we are all ears and can’t wait to hear your opinion!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











