Patch management helps you proactively eliminate potential vulnerabilities in your IT environment before they can cause financial or reputational damage.
In this blog, we explain what is patch management, the difference between patch & vulnerability management, benefits, risks & challenges, best practices, and more.
Why is Heimdal one of the best PATCH MANAGEMENT solutions?
LEARN MORE BY BOOKING A FREE TRIAL
What Is Patch Management?
Patch management is a systematic process to identify, acquire, test, deploy, and verify software updates.
The goal is to resolve specific threat vectors that a hacker might use to infiltrate your environment and access the sensitive information that lies within it.
While the theory might be comparatively simple, in practice it can be a complex topic to get right.
To understand the challenge in more detail, we need to understand the concept of technical vulnerabilities.
All software platforms have bugs, insecure code, or other vulnerabilities, both known and unknown, that hackers can use to gain access to an IT environment.
Once detected, these are published and made publicly-available through the common vulnerabilities and exposures database (CVE).
This allows vulnerability scanning tools and security teams to identify and remediate these issues, thus eliminating the risk of attack.
A patch is a software update that aims to resolve a specific known vulnerability.
Patch management, therefore, is the process of identifying which patches to apply and deciding the right order or priority in which to do it.
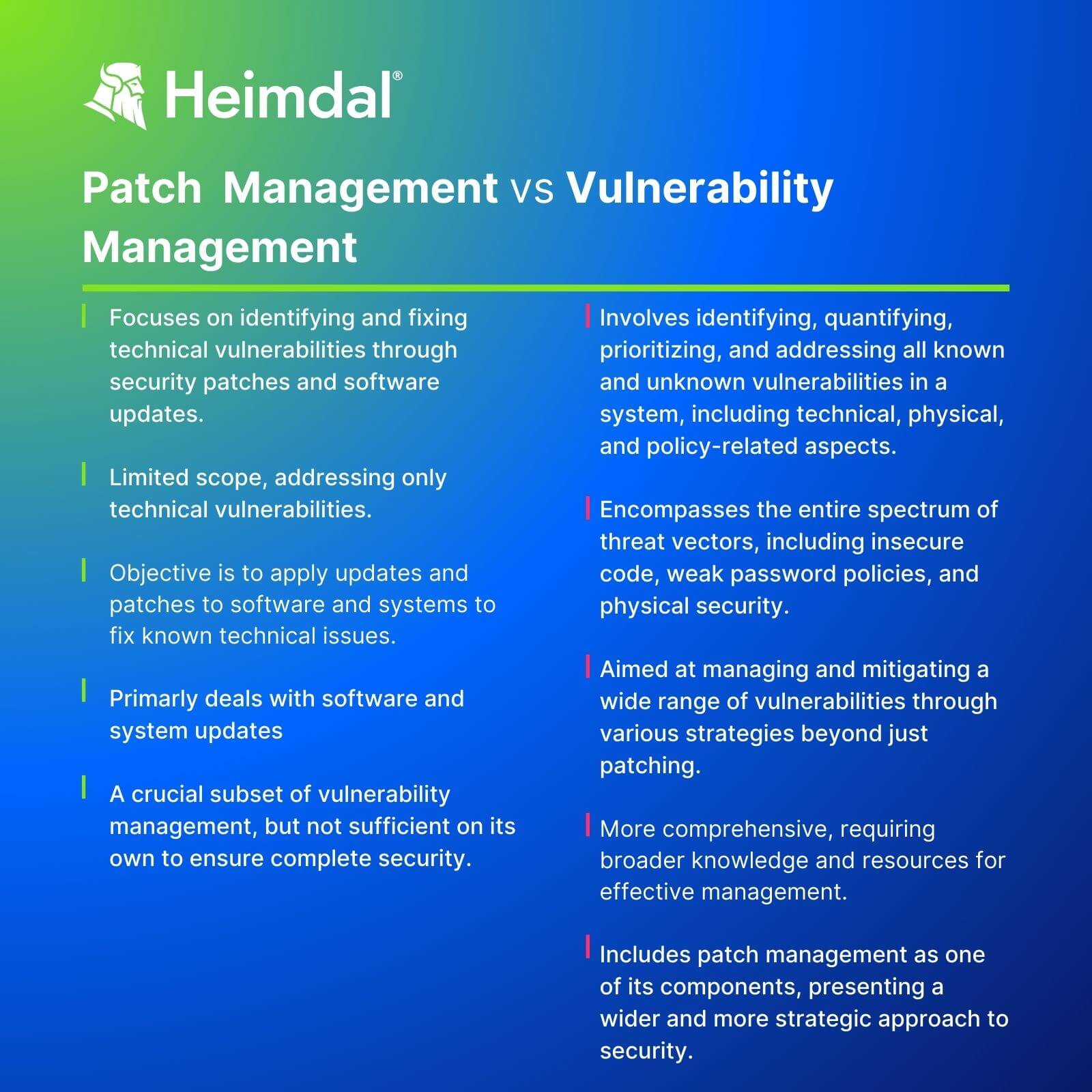
Patch vs. Vulnerability Management
Patch management and vulnerability management might be related concepts, but it’s important to understand the difference between them.
Essentially, patching is a type of vulnerability management – which refers to the wider strategy of identifying, quantifying, and prioritizing all known and unknown vulnerabilities.
The key difference is that vulnerability management should focus on the entire scope of threat vectors.
This applies to everything from insecure code to weak password policy, and the physical security of company buildings and computers.
Patch management, on the other hand, focuses only on technical vulnerabilities that can be resolved through security patches and software updates.
In reality, you need to consider them both as part of the same approach.
Patch management alone can’t keep your organization safe because it’s only focusing on one specific threat vector.
Benefits of Patch Management
The goal of an effective patch management process is to reduce the risk of attack to the lowest possible level.
But there are several ways a successful security attack can damage your organization, including:
Downtime
Successful attacks (such as ransomware or denial of service) can lead to your website, customer app, or internal tools being taken offline.
This can have a real impact on sales and productivity.
Reputational damage
If organizations gain a reputation for being insecure, it can be really difficult to shift.
Security-conscious customers can easily decide to take their business elsewhere – and regaining their trust can be a significant uphill battle.
Regulatory penalties
Information like customer names, addresses, banking details, and more are all protected by legislation such as the GDPR.
This means that it’s your responsibility to keep it safe and confidential. I
sensitive data is leaked, breached, or stolen, there’s a good chance you’ll be in for some regulatory fines.
Lost business
Downtime and reputational damage can all lead to customers deciding to take their money and data elsewhere.
The benefits of an effective patch management policy, therefore, are to avoid or eliminate these challenges from happening, wherever possible.
Patch Management Risks and Challenges
In theory, patch management should be a fairly simple job of identifying the highest-risk vulnerabilities and installing the relevant patch.
There are, however, a few factors that complicate the process.

1. Prioritization
As explained above, the hardest part of the process is simply deciding which vulnerabilities to patch and in which order.
2. Known vs. unknown threats
A vulnerability scanning tool can only detect publicly-known vulnerabilities.
Businesses can still be attacked through vulnerabilities that haven’t been detected.
These can’t generally be patched.
However, you can reduce their potential impact by tightening access controls, isolating sensitive assets, implementing multi-factor authentication and much more.
3. The limitations of patching
Not every security incident comes via technical vulnerabilities.
Employees accidentally leaking sensitive data in an email attachment can be just as much a security risk as suffering a malware or denial of service attack.
Patch management, therefore, needs to be treated as just one tool in a much wider security arsenal.
4. Compatibility
Patches can sometimes have unintended consequences after being installed.
You might find that tools and software don’t work in the same way afterwards.
This can create disruption when your processes, technology, and workflows are built around the way they used to be architected.
This can affect the speed and performance of digital services, break integrations between different types of software, create version conflicts, or a whole range of other issues.
It’s even possible to accidentally reintroduce a previously resolved vulnerability during a patch (regression bugs).
It’s important, therefore, to test the impact of proposed patches in a controlled environment.
This should help you proactively identify particular issues so you can mitigate them.
5. Potential downtime
One significant side effect of a security patch can be unwanted planned and unplanned.
New patches can change processes, workflows, or integrations.
This means it will need updating or fixing before the asset can work again.
This is an extreme example of the compatibility issue from the last point.
In this case, it’s therefore useful to test beforehand so you can identify and fix relevant workflows before the patch is installed.
Downtime can also be an expected necessity while the patch is being installed.
In this case, the system will return online after a reset.
Here, it can be useful to group together non-critical updates into scheduled maintenance periods, to reduce the cumulative downtime they cause.
6. Remote workforce
Having a remote workforce can also make patch management a challenge, because it often involves more IT assets, in different locations – which the security team may not have total visibility over.
To mitigate this challenge, ensure you use cloud-based vulnerability and asset scanning tools, as well as regularly installing vendor-issued software updates.
You should also invest in cybersecurity training, so employees can better identify the risk and warning signs of poor security – wherever they’re working from.
The Complete Patch Management Process
Now we’ve defined patch management and understand some of the challenges and limitations, we can discuss what an effective process looks like.
Depending on the framework being used, there may be varying stages to this – but the basic outline generally looks like this:
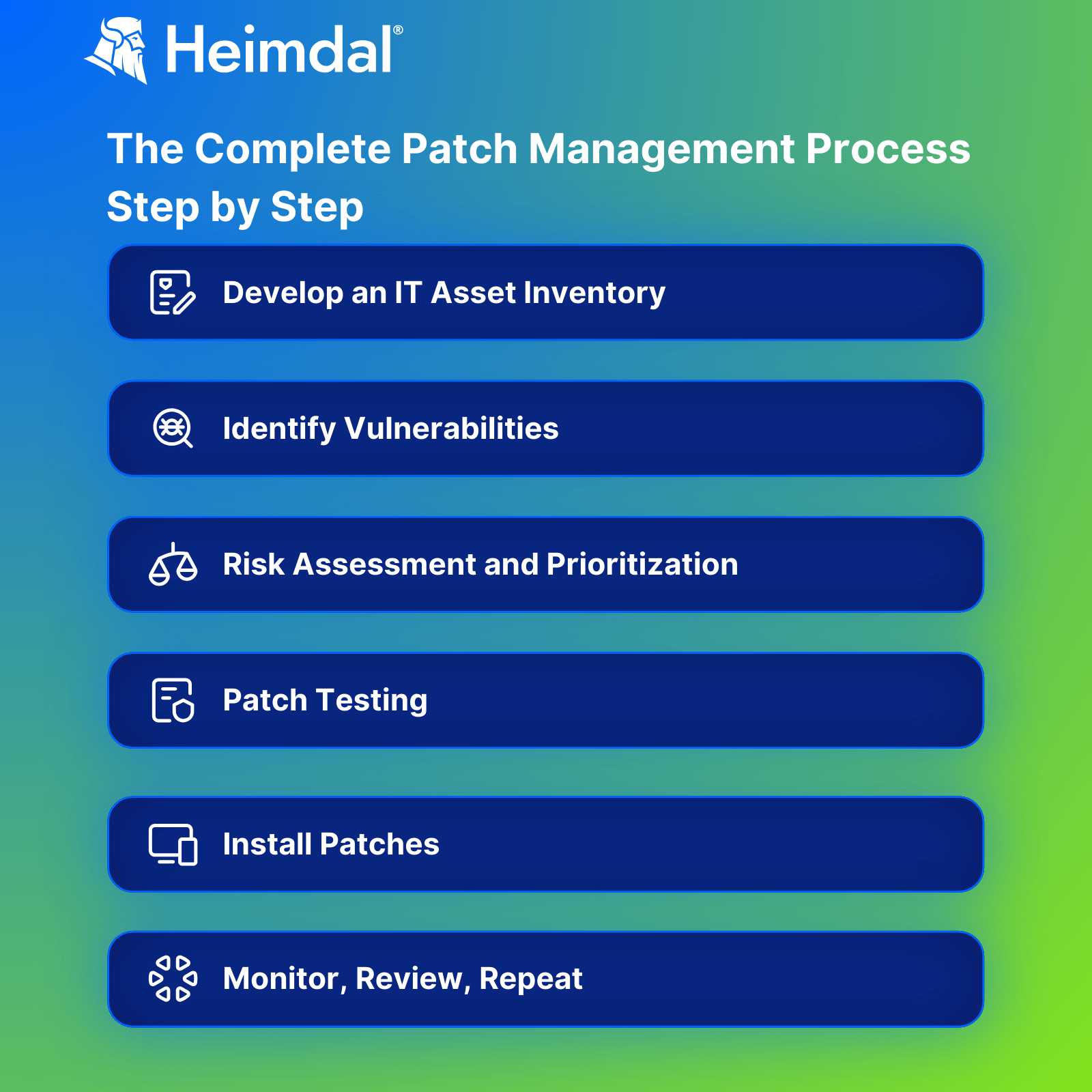
1. Develop an IT asset inventory
First, you need to understand what systems and assets exist within your IT environment and where risk lies.
The best place to start here is to run a scan using a cloud-native asset scanning tool.
From there, you should categorize specific systems and assets by their relevant risk profile.
Ultimately, the highest risk assets will be those that affect the uptime of critical systems or the security of sensitive data.
2. Identify vulnerabilities
The next stage is to identify specific vulnerabilities to be patched.
This can also be done using a vulnerability scanning tool, which will correlate the software and assets in your operating system and wider IT environment with a publicly-available list of vulnerabilities.
Based on the risks identified in the first stage, you may find that certain systems simply aren’t worth running the full vulnerability scan on.
In these cases, the risk and impact of a successful attack are so low that’s it’s simply not worth the effort.
3. Risk assessment and prioritization
You should now have a pretty comprehensive list of patches and updates that need to be installed.
The next job should be to prioritize which ones need remediating first, based on the resources you have and the perceived risk of the specific vulnerabilities.
To do this, you need to correlate the likelihood of the vulnerability being exploited against the perceived risk of the system or asset it’s targeting.
A useful tool here can be the common vulnerability scoring system (CVSS) which rates the relative risk of security vulnerabilities.
Check out our full guide to cybersecurity risk assessments to find out more.
4. Patch testing
To avoid downtime or other unintended consequences, it’s important to thoroughly test patches before installation.
One way to do this is to create a virtualized test environment (essentially a digital clone of your environment), through services like Microsoft Azure or Amazon Web Services (AWS).
You can also run smoke tests to identify any potential issues.
Another helpful trick here can be to ensure you’ve got comprehensive version rollback points for all your assets before installing patches.
This makes it easier to restore software or assets to their pre-installation state.
5. Install patches
Once you’ve decided which patches to deploy and tested for issues, it’s time to press install.
If you’ve followed the other steps in this blog, this should be fairly straightforward.
Much of this can be done automatically by specialist vulnerability management tools.
With the right tools, it’s also possible to create automated policies, so particular patches can be installed or scheduled based on their relative risk and the criticality of the assets they’re targeting.
As discussed above, downtime often occurs as a necessary consequence of installing patches.
Unless the vulnerability is critical, it’s probably going to be more helpful to schedule several installations into a single maintenance period, preferably scheduled when demand for apps or websites is particularly low.
6. Monitor, review, repeat
Effective patch management needs to be a constant, iterative process.
After all, new vulnerabilities are discovered all the time – and the longer they’re left unpatched, the higher your risk of being attacked through that vector.
Luckily, once you’ve done this once, it should be fairly simple to rinse and repeat.
It’s important to regularly scan both new assets in your environment and new known vulnerabilities – as both of these change constantly.
It’s vital to ensure your patching efforts are targeted towards the full scope of potential risks the organization may face.
Patch Management Best Practices
Here are some best practices to follow when implementing patch management:

- Asset Inventory: Document all systems and applications in your organization. Understanding your setup is key for identifying vulnerabilities and patches.
- Risk Assessment and Prioritization: Identify critical systems and prioritize patches based on risk. High-risk patches require immediate action.
- Effective Patch Policy: Develop a comprehensive policy for testing, deploying, and documenting patches. Refer to related articles for in-depth guidance.
- Patch Testing: Before applying patches, test them to avoid compatibility issues and potential system disruptions.
- Performance Monitoring: Keep track of system performance before and after patching. Have a rollback plan ready for quick resolution of patch-related problems.
- Patch Automation: Automate patching processes to increase efficiency and reduce errors. Focus on critical vulnerabilities to optimize resource use.
Patch Management Statistics 2024
- Breach Detection Time. Normally, detecting a breach takes 201 days. With effective patch management, this reduces to about 60 days.
- Data Breach Costs. The cost of a data breach in 2024 is estimated at $5 million per incident, up from $3.86 million in 2020.
- Prevention of Cyberattacks. Microsoft’s study shows that timely patching could prevent over 80% of successful cyberattacks.
- Perceived Vulnerability. About 75% of organizations feel at risk of cyberattacks due to their unpatched software.
- Patch Management Practices. Only 50% of organizations in 2024 have a documented process for patch management.
Automated Patch Management Benefits
Automated patch management systems bring a multitude of benefits, transforming the complex and often cumbersome process of patching into a streamlined, efficient, and less error-prone operation.
At the end of the day, the risk that many organizations face in their infrastructure and in their applications is ‘what if there’s a security vulnerability exploited before I have time to react?’
Aner Mazur, Chief Product Officer at Snyk
These systems leverage technology to automate the various stages of the patch management process, offering significant advantages to organizations of all sizes.
Consistency and Timeliness
Automated systems ensure that patches are applied consistently across all systems.
They eliminate the human error factor and ensure that patches are deployed promptly, reducing the window of vulnerability.
Resource Optimization
Manual patching is resource-intensive, requiring significant time and manpower.
Automation frees up IT staff to focus on more strategic tasks, improving overall productivity and efficiency.
Enhanced Security Posture
By ensuring that all systems are promptly and regularly updated, automated patch management significantly improves an organization’s security posture.
It minimizes the risk of cyberattacks exploiting unpatched vulnerabilities.
Compliance and Reporting
Automated systems provide detailed logs and reports, making it easier to demonstrate compliance with various regulatory standards.
This documentation is critical for audits and for maintaining transparency about the organization’s security practices.
Scalability
As organizations grow, so do their IT infrastructures.
Automated patch management systems scale to accommodate increasing numbers of devices and software, ensuring that the patching process remains efficient regardless of the size of the environment.
Reduced Downtime
By scheduling patches during off-hours and ensuring proper testing before deployment, automated systems reduce the likelihood of downtime caused by patch-related issues.
Continuous Improvement
Automated systems provide data and insights that can be used to continuously improve the patch management process.
This data-driven approach leads to better decision-making and more effective security practices over time.
How to Choose the Right Patch Management Software and Tools in 2024
As you might have already gathered, effective patch management is next-to-impossible without specialist patch management solutions.
The amount of known vulnerabilities and assets in your environment are simply too great to manually quantify and compare.
That’s why it’s so important to use the right software. Here’s how Heimdal® helps make patch management simple:
- Automated Patch Deployment. Heimdal®’s solution automates the process of deploying patches, reducing the manual workload and ensuring timely updates. This feature is crucial for businesses looking to maintain security without overburdening their IT staff.
- Broad Software Coverage. This ensures that not only popular applications but also niche or business-specific software receive timely updates, enhancing overall security. Heimdal®’s Patch & Asset Management software works with Windows, Linux, macOS, third-party apps, and even proprietary apps.
- Customizable Patching Policies. The ability to customize patching policies to fit specific business needs is a significant advantage. Businesses can prioritize patches based on severity, compatibility, or operational requirements, allowing for a more targeted approach to security.
- Security and Compliance. Emphasizes security and compliance, ensuring that businesses meet regulatory standards by keeping their software up-to-date. This is particularly important for companies in regulated industries.
- Reduced Vulnerabilities and Risks. By keeping software consistently updated our solution minimizes vulnerabilities, reducing the risk of cyber attacks and data breaches, a vital aspect for protecting business data and maintaining customer trust.
- Reporting and Analytics. Advanced reporting and analytics capabilities, offering insights into the patching process and helping businesses understand their security posture.
- Ease of Use and Support. User-friendly interfaces combined with professional support make the adoption and utilization of the patch management system smoother, ensuring businesses can leverage the full potential of the tool without extensive technical expertise.
Want to find out more? Check out our patch management solution.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










