In January 2024, the National Vulnerability Database received over 1,830 new CVEs. That added up to the other already registered 234,632.
Security Officers in charge of closing vulnerabilities need to focus on what to fix first and patching before hackers exploit them.
Let’s see how you can set up a smart and fast patch management process.
Key takeaways
- Patch management keeps hackers outside your system by closing known vulnerabilities.
- The 7 key steps of the patch management process are inventory, assess, prioritize, test, schedule, deploy, and monitor.
- Automated patch management software improves visibility and control, helps overcome talent shortages, and reduces the attack surface by patching third-party software.
- Heimdal Patch & Asset Management unifies patching for Windows, MacOS, and Linux.
The 7 key steps of the patch management process
To make patching an easier task for your security team, set a clear patch management policy.
Then create an effective patch management process.
Make it clear which member of the IT staff is responsible for which step of the process.

Asset inventory
Make sure you know what you need to protect before you get to work.
The first step of a successful patch management process is a thorough inventory of all potentially exposed assets.
The inventory list should include:
- Laptops, mobiles, printers
- Routers & servers.
- IoT devices.
- On-prem or Cloud databases.
- Operating systems.
- Third-party apps, etc.
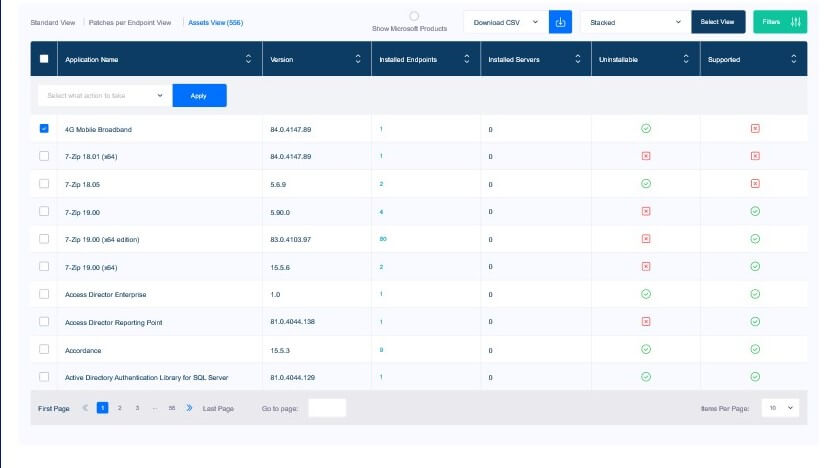
Asset inventory – See all software in the Heimdal Dashboard
Internet-facing assets pose the highest risk of becoming a target for hackers.
Now it’s the moment to create device groups based on operating systems and critical status.
Vulnerability assessment
All software has flaws.
Yes, even MacOS has exploitable vulnerabilities, so you should patch MacOS devices too.
Vendors like Microsoft, Apple, Adobe, Atlassian, etc. regularly release patches for known vulnerabilities.
Keep an eye on new releases and track the old known vulnerabilities.
Search for missing patches.
Use vulnerability management tools to detect vulnerabilities in your system.
Patch prioritization
Take your time to prioritize patches. Not all vulnerabilities are equally threatening and not all devices are equally exposed.
There are so many known flaws that there’s not enough time or workforce to patch everything.
You’ll have to choose. Here are three elements you should base your choice on:
- Company specifics and asset inventory.
- CVSS scores – can’t use those alone. According to the National Vulnerability Database dashboard, more than 60% of known vulnerabilities are of high or critical severity. You’re looking at more than 75,000 CVEs.
- EPSS scores – this is an instrument that predicts exploitability. It estimates how likely is it that hackers will use a certain vulnerability against their targets. The EPSS score is not a standalone tool either.
Patch testing
Get the patches you need from the vendor. Test them in a controlled environment before going live.
Document both the testing process and its results.
Check how your devices, software versions, and overall system will react to the updates.
Operating system or software updates can make them run slow, block, overlook safety measures, etc.
You should always have a backup to revert to in case things go wrong.
Testing can seem like a tedious task that slows down the patching process, but it pays off.
Here are some of the patch testing benefits.
Prevent disruption
Testing allows you to catch any issues that could interfere with the company’s workflow.
Make the adjustments you need to ensure business operations continue to run smoothly.
Ensure stability of the IT infrastructure
See if the patch conflicts with existing systems or applications.
Checking compatibility helps avoid slowdowns or outages in your critical systems.
Check quality
Patches are bits of software, and no software is flawless.
So, before installing patches, test them to see if they resolve the vulnerability without creating new bugs or security holes.
Scheduling
Keep workflow smooth by scheduling patch deployment at a convenient time for your organization.
Based on the company’s specific and day-to-day tasks, assess when the best time is to update software.
If your company activates in the educational sector, for example, the best time for patching might be in the evening or during weekends.
Take time to observe when the devices in your system are less used.
Communicate with the company’s employees so they understand why patching is important and should be a priority.
If your organization is medium to large, my recommendation is to go for an automated patch management tool.
Best patch management solutions come with the possibility to schedule patching at your own pace.
Deployment
Prepare the deployment package that will get the patch from the IT admin to the company’s computers.
This package is also known as a group policy object and includes:
- the tested patch.
- a script, which is a piece of code written by the IT admin. The script tells the device what to do with the patch.
Professional, automated patch management tools can also help with this step.
In a hybrid work environment, you need to be able to safely apply patches remotely.
If you patch manually, you’ll need to write scripts for the deployment package every time you patch.
Additionally, you’ll only be able to patch office-located devices.
You’ll have to postpone deploying patches on devices that belong to people who work remote or are on leave.
This is good news for the hackers since you’ll be slower to close a known vulnerability.
Monitoring results and reporting
The last step of the patch management process is to monitor, check the results, and document everything for the record:
- Were there any patch failures or rollbacks?
- What caused that?
- What was the impact of patch failures on the company’s operations?
Take the necessary steps to remediate the issue and apply patches.
Documenting how the patch deployment step succeeded or failed is useful intelligence for future diagnosis.
You can also use it in incident response, and compliance reports.
What makes the patch management process challenging?
Here are some aspects that will give you and your team a hard time if you patch manually.

Prioritizing patches
Deciding which patch to test and deploy first can be stressful.
Managing patches for different OSes
Lots of companies use different OSes for different departments.
IT teams could work on Linux, Accounts on Windows, and Marketing on MacOS, for example.
Maintaining visibility and control over assets
Moving to a hybrid or remote work environment brings a lack of visibility and control.
BYOD work policies also complicate endpoint security.
Patching third-party apps
Third-party software includes apps like Adobe, Google Chrome, Zoom, TeamViewer, etc.
Each third-party app you install on the company’s endpoints expands the overall attack surface.
Why? Because all software has vulnerabilities.
Talent shortage
People in the IT or Security teams are usually highly qualified.
Having enough hands on the deck to cover the patching process properly depends on the company’s budget and the available workforce.
Proper patch management is not enough to keep the IT infrastructure safe.
Integrating it with other tools, like Endpoint Detection and Response or DNS security, increases safety and incident response efficiency.
That’s why the trend in cybersecurity is to use unified platforms, that integrate and automate processes.
Heimdal’s MXDR suite, for example, comes with integrated vulnerability management, patching included.
Automate your patch management routine.
Heimdal Patch & Asset Management Software
How to keep patch management simple and effective
Patching is a tedious task, if done manually.
Additionally, things can easily go wrong if the ones in charge with patching don’t follow a clear policy.
You might overlook patching legacy software.
When in a rush, you might feel tempted to skip testing.
Not testing a patch or update before deployment can bring new bugs, impact performance and even data loss.
Also, check patch status after deployment.
Undetected patch failure leaves the system open to vulnerabilities and security risks.
Automating the patch management process solves most of the patching challenges.
It makes things happen clear and fast.
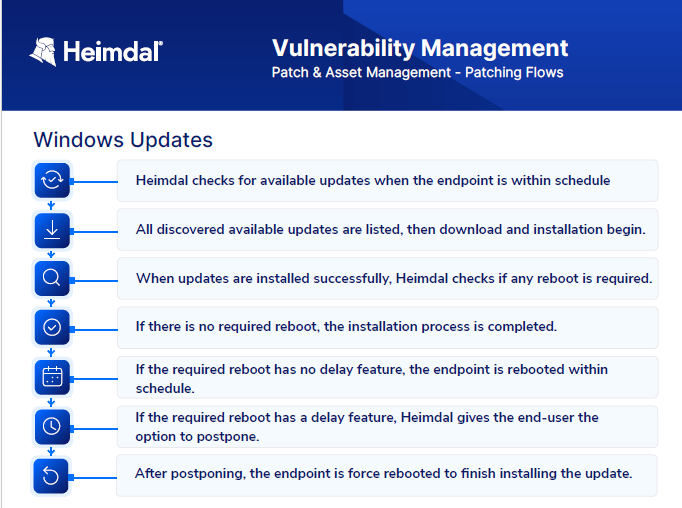
Heimdal’s patch management software helps the IT team keep it all on the green:
- enjoy total visibility over assets;
- assess;
- prioritize;
- test patches in a safe environment;
- schedule according to the business’s needs;
- deploy;
- monitor & report;
in a few clicks and remotely. Try it here, for free.
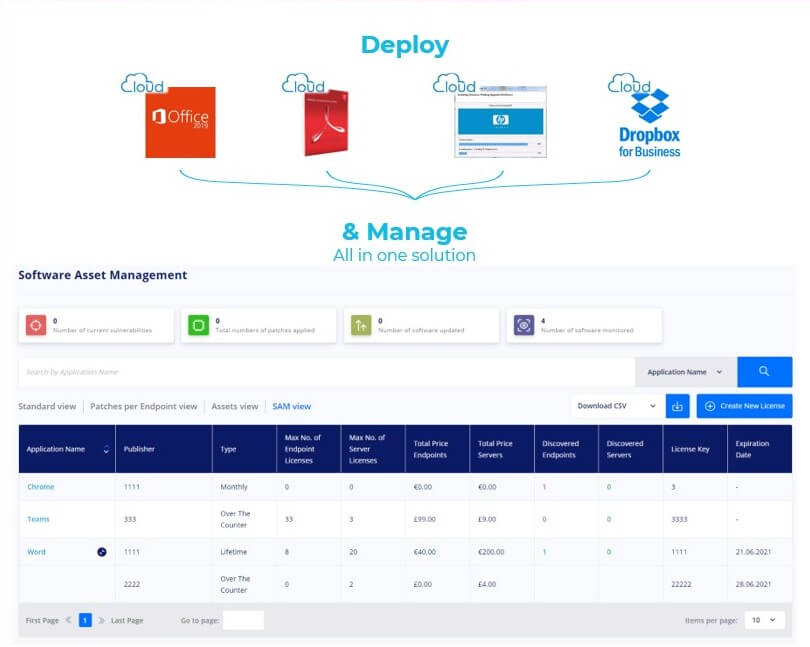
The tool solves patching for Windows, MacOS, and Linux.
All you need to do is set some operating system specific groups at the beginning and you’re good to go.
There’s no need to spend the budget on various tools to patch a diverse IT infrastructure.
Conclusion
As businesses develop, the need for using a variety of apps increases.
That grows exposure which can bring more opportunities for hackers, and more work for Security Officers.
Patching all critical assets to close high-severity vulnerabilities is possible.
Use an automated patch management solution that brings all OSs under the same umbrella.
Choose a tool that integrates into a unified security platform so you can view and control all processes from the same dashboard.
Automating redundant tasks and increasing visibility over all assets will take pressure off the security team and the budget.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








