Contents:
According to recent research into Raspberry Robin’s attack infrastructure, other threat actors may be able to repurpose the infections for their own malicious actions.
Raspberry Robin, also known as “QNAP worm”, and linked to the threat actor DEV-0856, is a malware that has increasingly been identified as being used in attacks on financial, government, insurance, and telecom entities.
It is thought to be a pay-per-install (PPI) botnet because it has been used by multiple threat actors to drop a wide range of payloads, such as SocGholish, Bumblebee, TrueBot, IcedID, and LockBit ransomware, explains The Hacker News.
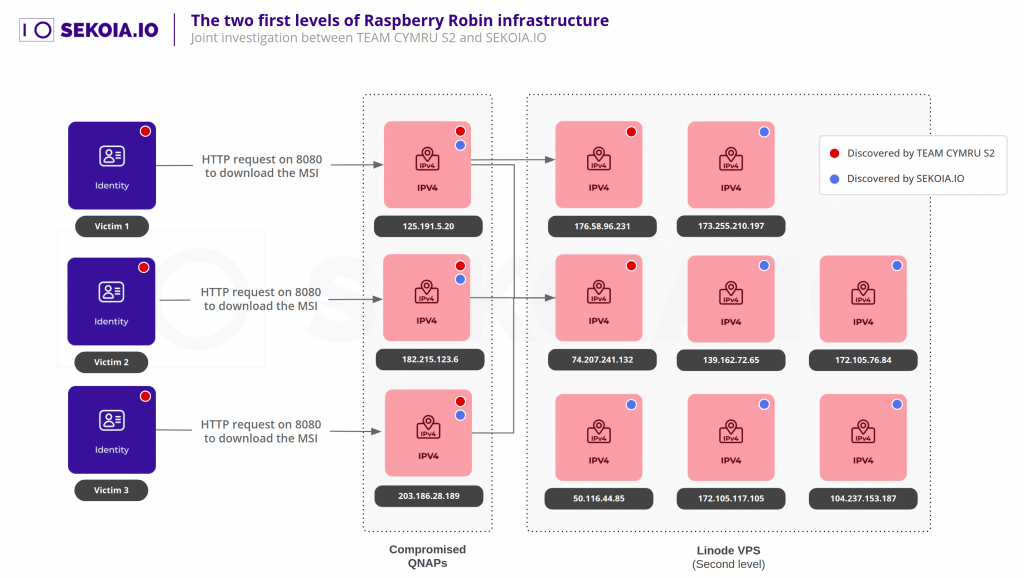
Raspberry Robin, in particular, uses infected USB drives as a dissemination vector and leverages breached QNAP network-attached storage (NAS) devices as first-level command-and-control (C2).
Cybersecurity researchers at SEKOIA discovered at least eight Linode-hosted virtual private servers (VPSs) that are part of a second C2 layer and presumably serve as forward proxies to a third, unknown tier.
The Attack Chain
What follows is a breakdown of the attack chain: the primary obfuscated Raspberry Robin payload is downloaded from the QNAP instance when a user inserts the USB drive and runs a Windows shortcut (.LNK) file.
As msiexec utility sends out HTTP requests to retrieve the malware, these requests can be spoofed to download another rogue MSI payload using DNS hijacking attacks or by repurchasing previously known domains after they expire.
This is one of the particularities of Raspberry Robin: the domain resolutions of its infrastructure are constantly changing, from a compromised QNAP to another. Dozens of new resolutions are made and new compromised QNAP are popping every day, limiting the risk of tapping or sinkholing it from an operator point of view.
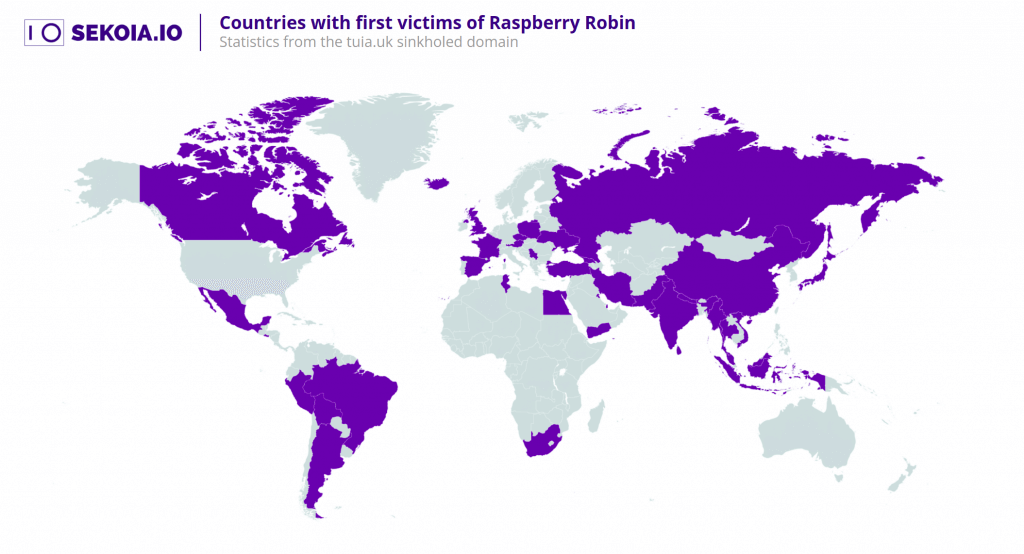
In the early stages of the campaign, in late July 2021, a domain name was registered and operated as a C2 between September 22, 2021, and November 30, 2022, when it was suspended by the.UK registry. This domain was tiua[.]uk.
It is presently uncertain where the initial wave of Raspberry Robin USB infections came from, however it is thought that the worm may have been spread via other malware.
This idea is supported by the presence of a.NET spreader module that is believed to be responsible for distributing Raspberry Robin .LNK files from infected hosts to USB drives. Using the same method, these .LNK files are then used to break into other computers.
This happened a few days after Google’s Mandiant team said that the Russia-linked Turla group used expired domains linked to the ANDROMEDA malware to send reconnaissance and backdoor tools to targets in Ukraine that were already infected by ANDROMEDA.
The full analysis published by SEKOIA’s research team is available here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








