Contents:
Security researchers recently noticed a surge in new devices infected with the Truebot malware downloader. This is created by a Russian-speaking hacking group known as Silence.
The Silence group is well-known for performing big heists against financial institutions. However, in recent years, they’ve shifted away from phishing as their initial compromise vector.
The threat actor has created a new custom data leakage tool called Teleport, and analysis of their attacks over the past months revealed they delivered Clop ransomware that is typically deployed by FIN11.
Truebot Infections: What You Need To Know
The Silence hackers planted their malware on over 1,500 systems worldwide to collect the hackers’ tools. These included Cobalt Strike beacons, Grace malware, Teleport exfiltration tool, and Clop ransomware.
Researchers at Cisco Talos examined the new campaigns and found that different attack vectors have been used since August 2020.
Over a short period in August and September, hackers exploited a severe vulnerability in Netwrix Auditor servers tracked as CVE-2022-31199. They used Truebot (Silence. Downloader) to infect systems with their code.
In October 2022, the gang switched their strategy and started training their mice to act as USB drives to deliver their malware payloads. The mice carried firmware developed for the Raspberry Robin worm, which often produced IcedID, Bumblebee, and Truebot viruses.
A new report from Microsoft has linked the WannaCry worm with ransomware attacks. Furthermore, the distribution of this malware has occurred in an overlapping time frame as that of DigitalPawan and Petya (known for distributing Clop ransomware variants).
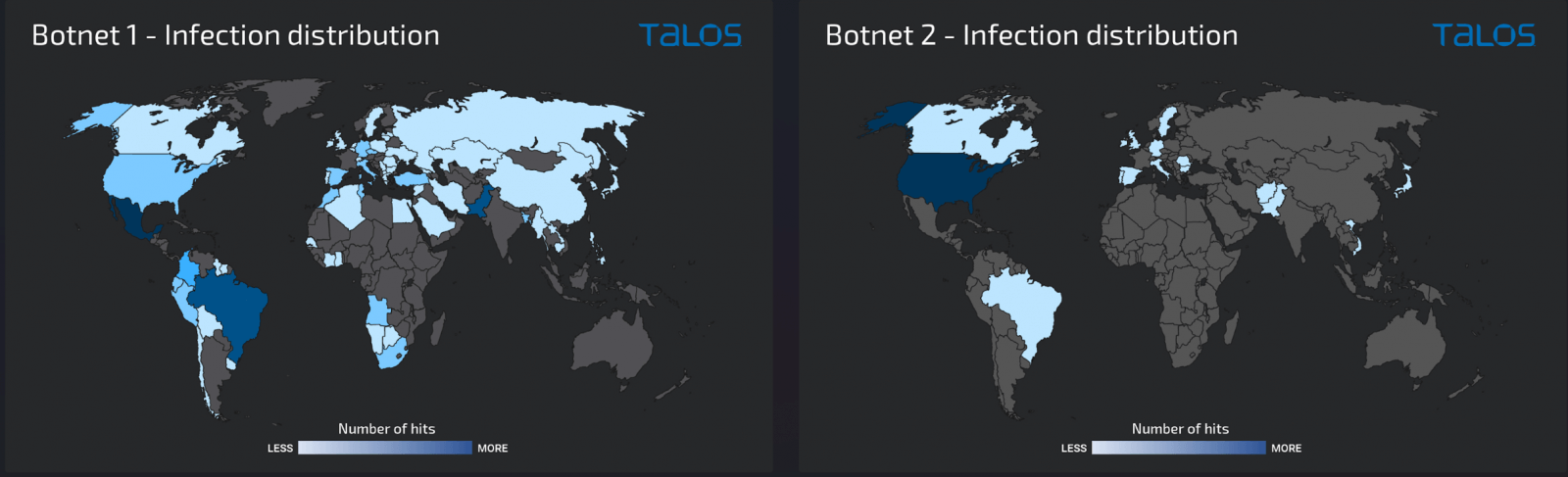
Cisco Talos notes that the Truebot gang used Raspberry Robin to infect more than 1,000 hosts. Many of these victims were desktops not accessible over the public web, mainly in Mexico, Brazil, and Pakistan.
Security researchers discovered hacking targeting Windows servers in November of this year, exposing a list of services on the public internet, including RDP, SMB, and WinRM. The research found that over 500 infections occurred, and about 75% were in the United States.
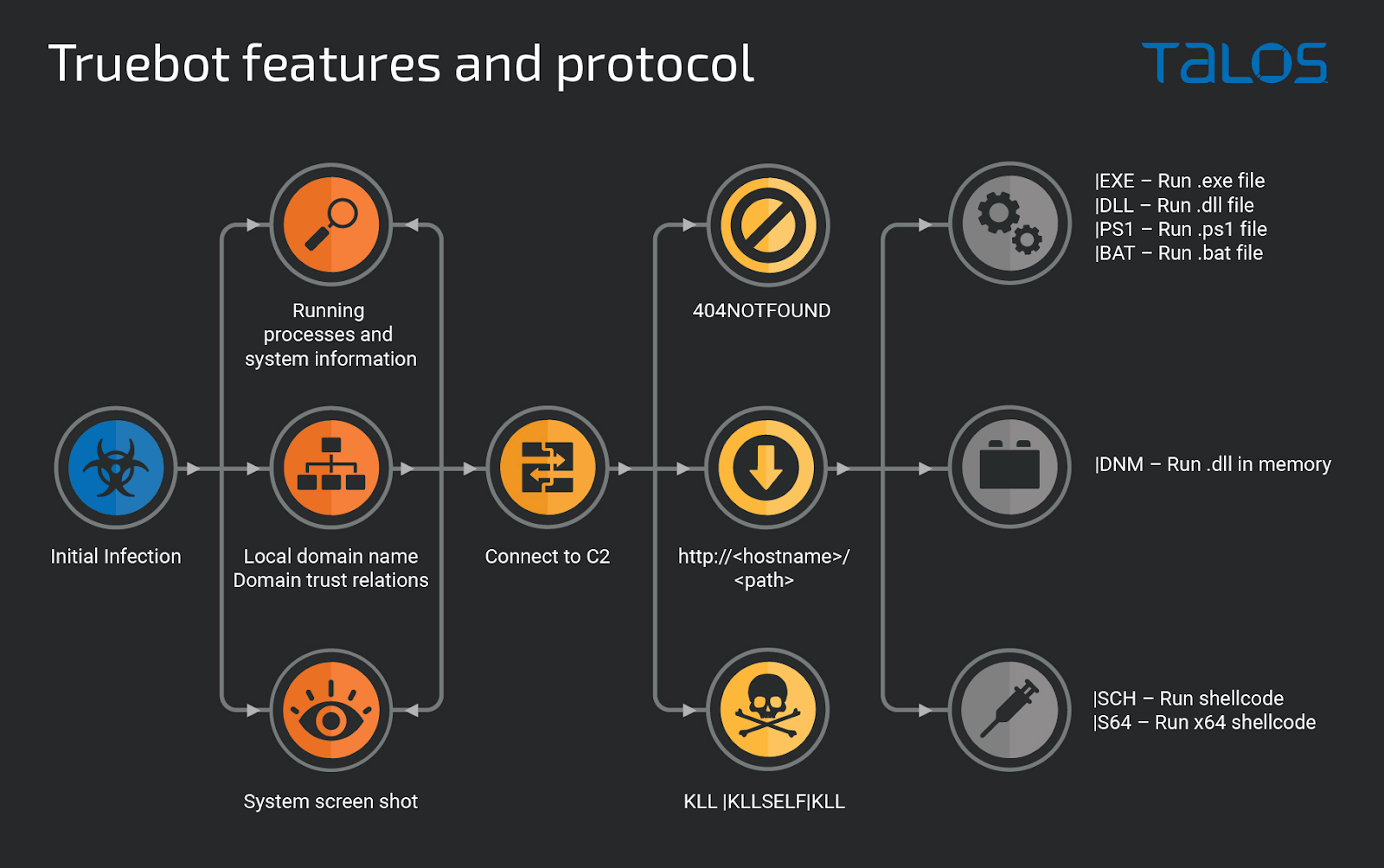
Truebot can collect basic information from an infected host computer, including screenshots and Active Directory trust relations. This is then sent to the threat actor for planning post-infection activity on a targeted machine.
Using the command and control (C2) server, Truebot can be instructed to install shellcodes, download files, and execute modules.
New Teleport Data Exfiltration Tool
Hackers use Truebot to drop Cobalt Strike beacons or the Grace malware (FlawedGrace, GraceWire), which the TA505 cybercriminal group created.
First, the intruders deployed Teleport. Cisco says this is a novel custom tool built in C++ to steal data without detection.
Teleport communicates with the C2 server over an encrypted channel. Operators can limit the upload speed and filter files by size to steal more. They can also delete the payload to stay under the radar on the victim machine.
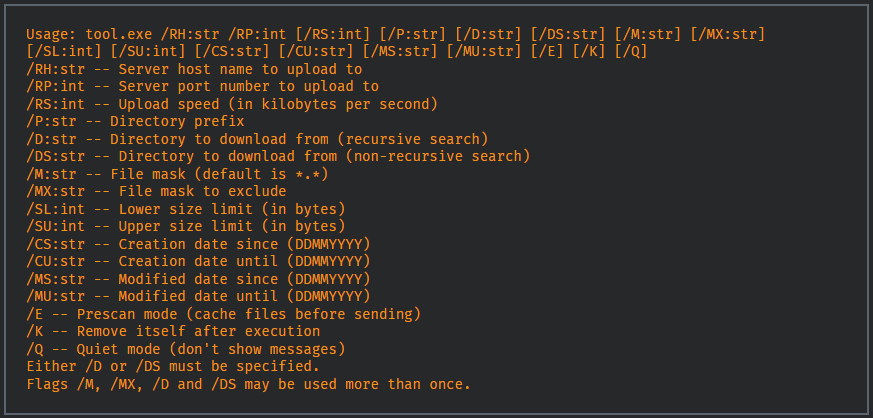
Teleport also features options to steal files from OneDrive folders, collect the victim’s Outlook emails, or target specific file extensions.
In some cases, the attackers deploy the Clop ransomware after moving laterally to as many systems as possible with the help of Cobalt Strike.
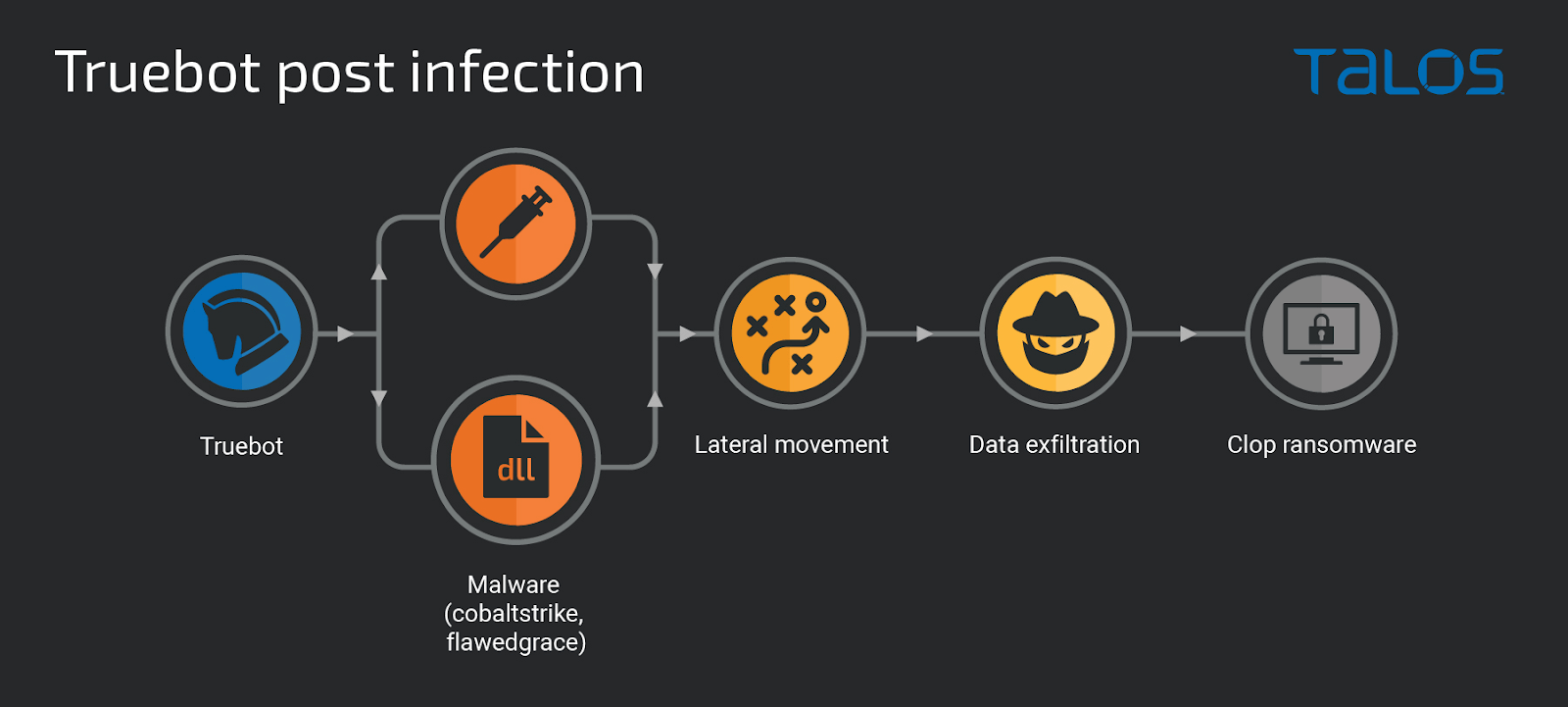
During the exploration and lateral movement phases, the attackers browsed key server and desktop file systems, connected to SQL databases, and collected data exfiltrated using the Teleport tool to an attacker-controlled server.
Once enough data had been collected, the attackers created scheduled tasks on many systems to start executing the Clop ransomware and encrypting as much data as possible.
Cisco Talos researchers explain.
Silence Gang: The Forgotten Minority
Security experts at Group-IB have been watching Silence/Truebot activity since 2016, when the hackers broke into a bank but failed to steal money because of an error with a payment order.
The attacker hit the same target again and started to monitor the bank operator’s activity by taking screenshots and streaming video from the infected system. After learning how the money transfer works, they could manipulate it to steal a large sum of money.
Based on Group-IB’s knowledge, they pulled their first successful robbery in 2017 by attacking ATM systems and stealing more than $100,000.
The Silence group has made $4.2 million from bank robberies in just three years, from 2016 to 2019, across all continents in the former Soviet Union, Europe, Latin America, and Asia.
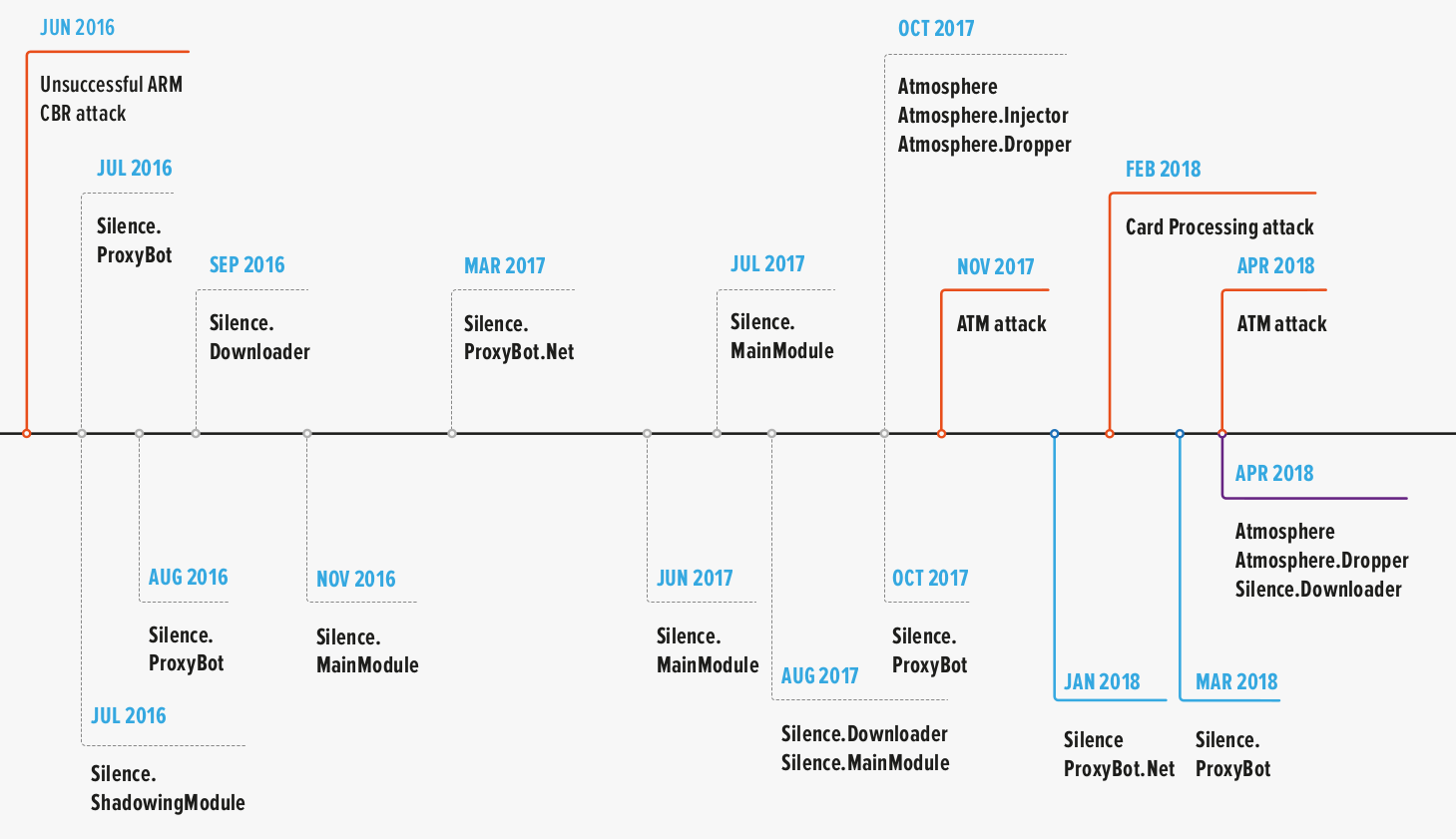
The Group-IB research team describes the Silence hackers as highly skilled. They can reverse engineer malware and alter it or adapt a nation-state group’s exploit. In addition, they’ve developed their own tools.
Initially, the attacker focused mainly on Russian industries, but they have since expanded their efforts to a global level.
How Can Heimdal® Protect You From Ransomware?
Heimdal® offers an outstanding cybersecurity suite, which includes the Ransomware Encryption Protection module. This module is compatible with any antivirus solution and makes detecting and remediating LockFile ransomware easy.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










