Contents:
SEO poisoning attacks have been on the rise in recent years, as more and more people are using search engines to find information online. Attackers are constantly coming up with new ways to exploit SEO vulnerabilities, so it’s important to be aware of the risks and take steps to protect yourself. In this article, I’ll explain what SEO poisoning is, how it works, the risks it poses, and how you can protect yourself from such attacks.
What Is SEO Poisoning?
Search engine optimization (SEO) poisoning is a malicious attack used by cybercriminals to take advantage of unsuspecting Internet users. By using specific keywords and phrases, attackers can make their malicious content appear more relevant and trustworthy to users than it actually is. The goal of SEO poisoning is to hijack the search engine results of popular websites and inject malicious links into them to boost their placement in search results. These links then lead unsuspecting users to phishing sites, malware downloads, and other cyber threats. These fake websites have a convincing appearance, are often exact replicas of real websites, and frequently rank for popular search terms.
How Does SEO Poisoning Work?
When a cyberattacker wants to harm a company or individual, they insert malicious code into a website that will redirect users who are searching for specific keywords to a different, harmful site. The objective of SEO poisoning is to damage the reputation of the targeted company or individual, infect users with malware to launch a ransomware attack, or access bank information to steal sensitive data from unsuspecting users.
This type of attack works by taking advantage of vulnerabilities in search engine algorithms. When a user types in a keyword or phrase into a search engine, the search engine scours the Internet for websites that match those keywords. The attacker will create a website with malicious code that includes the same keywords as the original site they want to target. Because the attacker’s website includes the same keywords, it will show up higher in the search results than the legitimate website. When the user clicks on the attacker’s site, they are redirected to a harmful one where their sensitive information may be stolen.
The five techniques listed below can be used by malicious sites to reach page #1 of the search results.
- Whitehat SEO strategies including generating lengthy, original material that is relevant to the topic and will draw readers and search engines.
- Blackhat SEO techniques including keyword stuffing, buying backlinks, cloaking, link schemes, and article spinning.
- Attacking all genuine sites that are currently ranked above them with “negative SEO” in an effort to have those sites tumble in the rankings.
- Paying the search engine provider to list the malicious website on the 1st page of search results.
- Using the scareware strategy which alerts website visitors that their computers are infected with viruses. They get a notification asking them to download an online antivirus program, which is in fact malware.
SEO poisoning can have devastating effects on companies and individuals alike. Not only can it damage their reputation, but it can also lead to loss of revenue and lawsuit. It is important for companies and individuals to be aware of this type of attack and take steps to protect themselves.
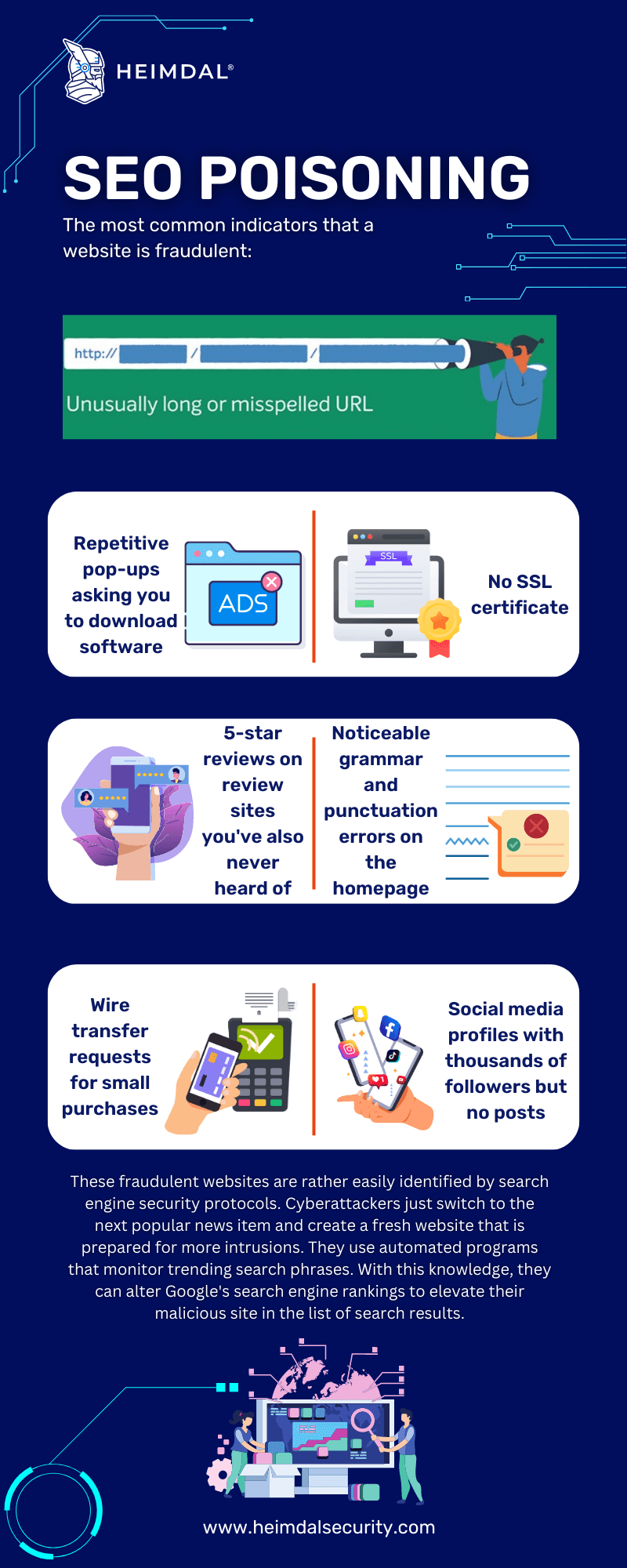
How to Spot Search Engine Poisoning Attacks
There are a few key symptoms of SEO poisoning that you should be aware of. First, if you notice a sudden drop in your website’s traffic or rankings, this could be a sign that your site has been poisoned. Secondly, if you start receiving more spammy or low-quality links to your site, this is another red flag. Finally, if you find that your site is being blocked by Google or other search engines, this is a clear sign that your site has been hit with this type of attack.
When looking for a hot issue or current event that has received a lot of media attention, your personnel should be warned that they may come across an SEO poisoning attack.
Staff members should proceed cautiously if they are unfamiliar with a website. Avoid any websites with too many pop-ups or Java since those are signs that the site is compromised. Pop-ups on any website are a warning sign.
Additionally, malicious websites frequently send users to “scareware portals”, where users are inundated with phony virus warnings that compel them to install malicious code posing as an antivirus product. Your personnel should be instructed to identify potentially dangerous websites and alert your IT department.
How to Avoid Getting SEO Poisoned
Often, prevention is preferable to remedy. I recommend the following best practices for guarding against SEO poisoning attacks:
1. Security Awareness Among Staff
Be sure to maintain the antivirus software on BYOD and office devices up to date to protect yourself and your staff against search poisoning attempts. The best course of action is to instruct personnel on how to avoid clicking any suspicious-looking links in the first place. They must also comprehend that if they are doubtful about a website, they should never give out any personal information.
Make sure your staff is aware of the risks involved with visiting an untrusted website. In search engine results, they should pay close attention to the URL and stay away from any that seem untrustworthy. Additionally, making sure all of your staff members have access to IT security training will greatly lessen the likelihood that your company will fall victim to malware, ransomware, or data theft.
2. Web Security, Malware & Virus Protection
Make sure your IT employees are maintaining up-to-date end-user security programs that block harmful websites from a central location. Routing all users through a secure web proxy is one technique to achieve this goal. You can also lessen your risk by using the most recent anti-malware and antivirus software on email servers and user computers.
3. Website Safety
Your IT department should make sure that there are no web vulnerabilities on your company’s website. Applying the most recent WordPress updates is a wonderful place to start, and best practices also call for adding firewall security, anti-spam detection, and plugin upgrades.
Although some attempts cause users to be diverted from your website to one that is malicious, another risk involves hackers adding pointless meta tags and keywords to the pages of your website. This suggests that your business uses unethical blackhat SEO techniques. As was previously indicated, that might result in penalties from Google and other search engines. In the process, they lower your search engine optimization and degrade your search page rating.
4. Abnormal SEO Results Disclosure
Report the suspicious site to the search engine if you think it’s trying to harm your SEO position in order to get the result removed. For instance, you can file a DMCA complaint with Google so they can investigate the website in question.
What is more, there are a few extra things you can do to avoid getting SEO poisoned:
- Keep your keywords relevant to your topic. If your keywords are too general, you run the risk of your content being lost in a sea of other articles that cover the same topic. Be specific and focus on long-tail keywords that are less competitive.
- Don’t keyword stuff. This is when you cram as many keywords into your content as possible in an attempt to game the system. Not only will this make your content difficult to read, but it will also result in search engines penalizing your site.
- Do your research. Before you publish any piece of content, make sure to do a thorough check for any potential red flags that could get your site flagged for SEO poisoning. A simple Google search should suffice.
- Stay up-to-date with the latest algorithm changes. Google’s algorithms are constantly changing, so it’s important to stay on top of any updates that could affect your site’s ranking. A good way to do this is to subscribe to an SEO newsletter or blog.
Mitigation Strategies
SEO poisoning is a serious issue that can have a negative impact on your website’s ranking in search results. There are a few key things you can do to mitigate it:
- Audit your website regularly for signs of poisoning. This includes keeping an eye out for unusual or suspicious activity, such as sudden changes in traffic or rankings, strange new backlinks, or keywords that seem out of place.
- If you suspect that your website has been poisoned, take immediate action to clean up the affected pages and improve your site’s security. This may involve deleting spammy or malicious content, disavowing harmful backlinks, and changing your password and security settings.
- Stay up-to-date on the latest trends and changes in SEO so that you can better protect your website from future attacks. This includes keeping an eye out for new types of SEO poisoning and knowing how to quickly identify and fix them.
The best way to defend against these attacks is to avoid downloading cracked software from any source. Make sure you always check the source domain of every download to assure that the files are legitimate and to keep your anti-malware and other security solutions up to date.
New types of malware are designed to evade traditional file-based antivirus detection. For this reason, you will need to install a more robust piece of software that can keep up with and protect your organization against evolved threats.
Our Heimdal Next-Gen Antivirus & MDM is a next-generation antivirus solution with four state-of-the-art malware detection layers and live process monitoring. In addition to this, it runs in the background without slowing the machines in your network down, which is always a plus. As the counterpart of Heimdal Threat Prevention – Endpoint, it combines the techniques known by both traditional and Next-gen Antivirus engines to offer market-leading mitigation with EDR and Firewall functionalities.

Heimdal® Next-Gen Endpoint Antivirus
- Multiple layers of detection.
- Enhanced Brute-Force Protection.
- Remote device control with MDM.
Conclusion
As you can see, SEO poisoning is a serious security threat with potentially devastating consequences.
In order to further their goals, cybercriminals have learned how to manipulate SEO strategies, discovering ways to drive legitimate websites down the ranks while elevating their own websites to the top.
Users can make way for harmful viruses onto your network by downloading free software or clicking on internal links. Companies must be vigilant in order to safeguard their computer systems from intrusion and prevent their corporate websites from ending up among the websites that attackers have compromised. It’s important to take steps to protect yourself and your organization from this type of attack, including using complex passwords and avoiding clicking links or downloading files from unknown sources.
As always, implementing effective anti-malware, antivirus, and web browser protection as well as educating yourself and your staff about the risks of a search engine poisoning attack may significantly reduce the likelihood of becoming a target.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










