Contents:
Threat actors started using fake malware to confuse researchers and avoid being analyzed by detection systems. The new technique involves dropping a fake payload when the malware senses it`s being run into a sandbox and analyzed. If the analysis doesn`t seem to take place, real Raspberry Robin malware is launched.
What Is Raspberry Robin
Ransomware threat groups use worm-like malware Raspberry Robin to gain initial access to compromised networks.
FIN11 and Clop ransomware gangs were previously associated with Raspberry Robin and so were TrueBot, Bumblebee, and IcedID payload distribution.
Researchers noticed lately that cybercriminals tend to use Raspberry Robin against telecommunication service providers and government systems.
How Does Raspberry Robin Operate?
First malicious USB drives infect the machine with malware after they are inserted and the included LNK file is clicked on. As soon as the shortcut is used, it gets the legitimate ‘MSIExec.exe’ Windows executable to download a malicious MSI installer that sets the Raspberry Robin payloads.
Researchers noticed that:
The malware is heavily obfuscated to hide its code from antivirus programs and security researchers, featuring multiple layers containing hard-coded values for decrypting the next one.
However, to make it even harder for security researchers to analyze the malware, Raspberry Robin has begun to drop two different payloads depending on how it is being run on a device.
When the malware is run inside a sandbox, which is a clear signal that it is being analyzed, the loader drops a fake payload.
The fake payload has two additional layers:
- a shellcode that has an embedded PE file
- a PE file that had the MZ header and PE signature removed.
During the execution, it tries to read the Windows registry, searching for infection markers. After that, it starts collecting basic system information.
The next step is the fake payload`s trying to download and execute the ”BrowserAssistant” adware, which is supposed to delude the analyzing system that it had reached the final payload.
If none of that happens, the actual Raspberry Robin malware is on from the start.
Apart from the payload stunt, the actual payload uses ten layers of obfuscation, so it is extremely hard to analyze.
Right after being launched, if the user doesn`t have admin rights, it gains administrative privileges through a privilege escalation method called ”ucmDccwCOMMethod in UACMe”.
Raspberry Robin also changes the registry for endurance between reboots.
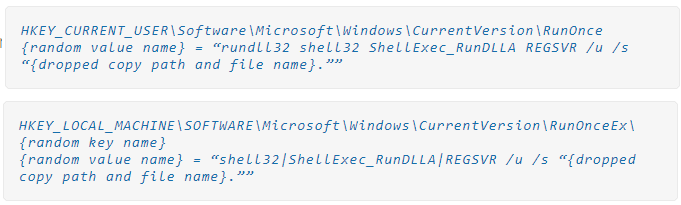
When everything is ready, the malware tries to establish a connection to the hard-coded Tor addresses and starts exchanging information with its operators.
Another notable feature of the Raspberry Robin infection process is that it also copies itself to other USB drives attached to the endpoint so it can continue to infect other systems too.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









