Contents:
Turla Russian espionage group delivers KOPILUWAK reconnaissance utility and QUIETCANARY backdoor to ANDROMEDA malware victims in Ukraine. Cyber researchers track the operation as UNC4210.
Turla is also known as Iron Hunter, Krypton, Uroburos, Venomous Bear, or Waterbug and is thought to be sponsored by the Russian state. The malicious group`s principal targets are governmental, diplomatic, and military institutions. It has been connected to a number of credential phishing and reconnaissance operations targeted at organizations in Ukraine since Russia’s military invasion.
Cyber researchers say it is unusual for hacking groups to target victims of other malware campaigns to launch their own attacks on and warn that:
As older ANDROMEDA malware continues to spread from compromised USB devices, these re-registered domains pose a risk as new threat actors can take control and deliver new malware to victims.
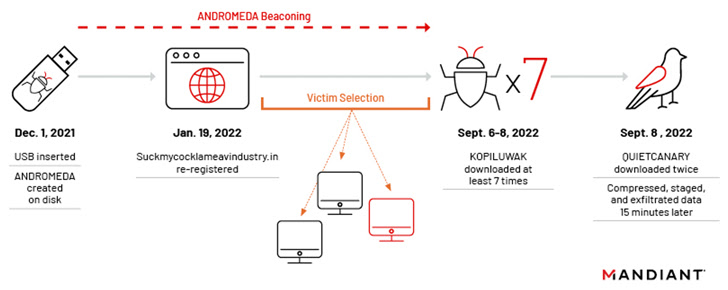
The Timeline of the Discovered Attack
December 2021 – an infected USB stick is inserted at a Ukrainian organization`s endpoint and a legacy ANDROMEDA artifact is deployed, after a malicious link (.LNK) file disguised as a folder within the USB drive is double-clicked.
January 19th, 2022 – one of ANDROMEDA`s C2 domains was discovered to be freshly re-registered. The domain was used by UNC4210 to outline interesting potential victims
September 6th, 2022 – UNC4210 downloads and deploys KOPILUWAK, a JavaScript-based reconnaissance tool, to the victim machine. The tool is used for streamlining C2 conversations and victim profiling.
September 8th, 2022 – On the final phase of the attack, threat actors downloaded the QUIETCANARY .NET backdoor on the victim and used it for data exfiltration of files that were created after January 1, 2021.
Russian State-Sponsored Threat Groups Extremely Active
Another series of Russian adversary groups` attacks on public institutions was recently reported by cyber researchers. At the beginning of 2022, COLDRIVER launched cyberattacks on three nuclear research labs in the U.S.
Threat actors attempted to trick nuclear scientists into revealing their passwords, by spoofing login pages for Brookhaven, Argonne, and Lawrence Livermore National Labs.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









